What is spam in mail? SMS messages can also be spam. Block spam using mail settings
Modern look banks
The word "SPAM" originally appeared in the city. It stood for SPiced hAM (spicy ham) and was a trademark for Hormel Foods canned meat, a spicy ground pork sausage. The term SPAM gained worldwide fame when applied to annoying advertising thanks to the famous sketch of the same name from the famous show “Monty Python's Flying Circus” (1969) by the comic group Monty Python. The point of the sketch is that in one cafe all the dishes on the menu contain “SPAM”, some even several times. When the main character of the sketch, who came to this cafe with his wife, asks to bring him a dish without “SPAM”, the waitress offers him a dish with “ a small amount SPAM." The customer is outraged, and a choir of Vikings sitting at nearby tables begins to sing a song of praise to “SPAM”, after which the sketch plunges into chaos. At the end of the sketch, the hero's wife exclaims: I don't like SPAM! (English) “I don’t like spam!”). The word “SPAM” was also added to the names of the characters in the credits. IN total this word is mentioned more than a hundred times in the sketch.
The most common types of spam
Advertising
Some legitimate businesses advertise their products or services using spam. They can distribute it themselves, but more often they order it from those companies (or individuals) that specialize in this. The appeal of such advertising lies in its relatively low cost and (presumably) large reach potential clients. Such unsolicited advertising may also have the opposite effect of alienating recipients and may even become synonymous with intrusive advertising, as happened with ham, they can actually increase sales without causing much trouble to the recipients. The main conditions of mutual benefit for the recipient and the mailing organizer are:
- combining the roles of mailing list organizer and email service provider;
- quality improvement target audience each specific promotional mailing letter;
- warning clients by the provider that he will send promotional letters;
- provision convenient means to block unwanted emails.
Advertising illegal products
Spam is often used to advertise products that cannot be communicated in other ways - for example, pornography, counterfeit (counterfeit) goods, medicines with restrictions on circulation, illegally obtained classified information(databases), counterfeit software.
Anti-advertising
"Nigerian Letters"
Sometimes spam is used to lure money from the recipient of the letter. The most common method is called "Nigerian letters" because a large number of such letters came from Nigeria. Such a letter contains a message that the recipient of the letter can receive in some way a large amount money, and the sender can help him with this. Then the sender of the letter asks to transfer him some money under the pretext of, for example, completing documents or opening an account. Extorting this amount is the goal of the scammers.
A narrower name for this type of fraud is scam or scam 419(by article number in the Nigerian Criminal Code).
Phishing
Distribution methods

Spam folder in an email client window
The largest flow of spam is distributed through electronic mail (e-mail). Currently, the share of viruses and spam in total email traffic ranges from 70 to 95 percent, according to various estimates. The most common spam content is advertising of unpopular products: Viagra, etc. .
Fighting spam
Ideology
It is obvious that spam brings economic benefits to its customers. This means that users, despite their dislike of spam, still use the services advertised through spam. As long as the return on spam exceeds the cost of defeating the defense, spam will not go away. Thus, the most reliable way to combat this is to refuse services advertised through spam. There are proposals to use public condemnation, up to the cessation of communication, against persons who buy goods and services advertised by spam.
Other methods are aimed at making it difficult for spammers to access users.
Preventive protection measures
The most reliable way to fight spam is to not let spammers find out email address. This is a difficult task, but some precautions can be taken.
All address hiding methods have a fundamental drawback: they create inconvenience not only for alleged spammers, but also for real recipients. In addition, it is often necessary to publish the address - for example, if it is the contact address of a company.
Filtration
Since promotional emails tend to be very different from regular mail, a common method of dealing with them has become to filter them out of the incoming mail stream. Currently, this method is the main and most widely used.
Automatic filtering
There is software for automatic detection spam (so-called spam filters). It may be intended for end users or for use on servers. This software uses two main approaches.
The first is that the content of the letter is analyzed and a conclusion is made whether it is spam or not. A letter classified as spam is separated from other correspondence: it can be marked, moved to another folder, or deleted. Such software can run both on the server and on the client’s computer. In the latter case, the user does not see filtered spam, but continues to bear the costs associated with receiving it, since the filtering software receives each letter and only then decides whether to show it or not. On the other hand, if the software runs on a server, the user does not incur the cost of transferring it to his computer.
The second approach is to use various methods, identify the sender as a spammer without looking at the text of the letter. This software can only run on a server that directly receives letters. With this approach additional traffic is spent only by the server on communicating with spam mail programs (i.e., refusing to accept letters) and contacting other servers (if any are needed) during verification.
There are also specialized online services, for example, Kaspersky Lab (Kaspersky Hosted Security service), Outcom (SPAMOREZ), INKAP (Antispam-Post), which provide paid anti-spam protection. Changing the MX record in a business domain name (see.
Another problem with automatic filtering is that it may mistakenly mark you as spam. useful messages. Therefore, many email services and programs, at the user’s request, may not delete those messages that the filter considers spam, but place them in a separate folder.
Automatic filtering methods
Automatic filtering programs use statistical analysis content of the letter to decide whether it is spam. The greatest success has been achieved using algorithms based on Bayes' theorem. For these methods to work, it is necessary to pre-train the filters by sending them manually sorted letters to identify statistical features of normal letters and spam.
The method works very well when sorting text messages(including the sample manages to cut off up to 95-97% of spam. To bypass such filters, spammers sometimes place the content in a picture attached to the letter, but the text is either missing or random, which does not allow the filter to compile statistics for recognizing such letters In this case, you need to use text recognition programs (most modern email programs do not support this), or use other methods.
Pledge reliable operation Bayesian method - constant additional training of the filter and pointing out errors to it. For this purpose, mail programs introduce the ability to manually mark messages as “spam/not-spam”, and in mail services on the Internet, a “report spam” button is introduced.
Manual filtering
Many programs and email services on the Internet allow the user to set their own filters. Such filters may consist of words or, less commonly, regular expressions, depending on the presence or absence of which a message does or does not end up in the trash bin. However, such filtering is labor-intensive and inflexible, and also requires the user to have a certain degree of familiarity with computers. On the other hand, it allows you to effectively filter out some of the spam, and the user knows exactly which messages will be filtered out and why.
Blacklists
Ownership, use, effectiveness
These include:
- lists of IP addresses of computers that are known to send spam.
- (widely used) lists of computers that can be used for mailing - “open relays” and “open proxies”, as well as lists of “dialups” - client addresses that cannot have mail servers
- (possible use) local list or a list maintained by someone else.
- (widespread due to ease of implementation) blacklists, queried through the DNSBL service ( DNS B lack L ist). Currently this method is not very effective. Spammers find new computers for their purposes faster than they can be blacklisted. In addition, a few computers sending spam could compromise an entire email domain or subnet, and thousands of legitimate users on indefinite time will be unable to send mail to servers using such a blacklist.
- (there are) lists of people preaching rather radical theories (for example, equating viral messages with malicious spam, etc.).
Misuse
Often irresponsible and incorrect use of blacklists by resource administrators, leading to blocking large number innocent users.
Example: the use of lists without precise representations of which addresses are included in it and how, the use of email blacklists for web resources, etc.
Irresponsible use
Example: failure to provide the user (or administrator) of a blocked address with information about the list (since there are a great many of them) or guided in their actions by the principle of presumption of guilt.
Racket by blacklist administrators
IN Lately There are more and more complaints online about blacklist administrators who blackmail Internet providers and hosting providers by refusing to remove IP addresses from which spam may have once been sent (addresses end up on blacklists by anonymous complaints, which are often impossible to verify). In addition, many require “donations” from IP address owners to remove entries from blacklists.
Authorization of mail servers
Were suggested various ways to confirm that the computer sending the letter really has the right to do so (Sender ID, SPF, Caller ID, Yahoo DomainKeys, MessageLevel), but they are not yet widely used. In addition, these technologies limit some common types of functionality of mail servers: it becomes impossible to automatically redirect correspondence from one mail server to another (
It is a common policy among providers that clients are only allowed to establish SMTP connections with the provider's servers. In this case, it becomes impossible to use some of the authorization mechanisms.
Gray lists
Method greylisting is based on the fact that the “behavior” of software designed to send spam differs from the behavior of regular mail servers, namely, spam programs do not try to resend the letter when a temporary error occurs, as required by the protocol The simplest version of greylisting works as follows. All previously unknown SMTP servers are considered to be on the gray list. Mail from such servers is not accepted, but is not rejected at all - they are returned a temporary error code (“come back later”). If the sending server tries again after at least some time t g(this time is called delay), the server is whitelisted and the mail is accepted. Therefore, regular letters (not spam) are not lost, but their delivery is only delayed (they remain in a queue on the sender's server and are delivered after one or more unsuccessful attempts). Spammer programs either do not know how to resend letters, or the servers they use manage to get blacklisted during the delay on the computer from which the letter is sent, etc. Using these measures, only the most primitive spam is eliminated - a small number of messages. However, it is not zero, so their use still makes sense.
Hello, dear readers of the blog site. You've probably already encountered spam, even if you didn't know exactly what this outrage is called. And for this it is not even necessary. Spam also pours into a regular mailbox with enviable regularity - these are the same countless advertising brochures, which are slipped to you in the hope that you will order or buy something.
So, spam is just that, an annoying one, creeping in from all sides advertising(but not only advertising - there are worse things). You didn’t order it, you don’t need it, but he rushes and rushes from every corner. The information you need can easily get lost in this heap and you have to spend a lot of time sifting through it.
In our computer age, the main source of spam. And besides advertising spam mailings can also be dangerous both for your wallet (phishing, social engineering, scams) and for your computer (viruses, worms, Trojans).
What does the word Spam mean, what does it look like and how can you fight it, you will find out by looking at this short article. I hope it will be interesting (well, certainly useful - I promise you that).
Spam - what is it?
What does the word SPAM mean?
Self word Spam comes from the name of canned meat, which was vigorously advertised after the end of the Second World War (obviously, it was necessary to urgently sell out the soldiers' meat rations).

The advertising was so aggressive, comprehensive and ubiquitous that this word (and the “sediment” associated with it) was remembered, but only because of the intrusive advertising that appeared along with it in conferences (then still on the Fidonet, if anyone remembers).
The word stuck, especially since intrusive advertising did not become less, but rather the opposite. When email gained popularity, unauthorized mass advertising and malicious mailings became commonplace. Such mailings were profitable for spammers, because without any special costs necessary information reached a large number of people.
But It's not limited to email. They spam in private messages on social networks, on forums, in instant messengers instant messages, on message boards, in comments to blogs, open for editing and adding text by anyone. They will also spam your phone, for example with advertising calls or mailings. promotional SMS messages.
Where can you find him on the Internet?
- Email- it's just a Klondike for spammers. With the help of mass mailings you can sell anything, you can deceive and rob, you can infect computers and send worms. Databases for mass mailings are collected independently (with the help of programs), or purchased from those who do this professionally.
- Forums, comments blogs, wiki sites and message boards - here, essentially, everyone is allowed to leave messages and spammers find it difficult to resist spamming. This is not always advertising - often this is how webmasters try to get a free link to their site so that it ranks higher in search results Yandex or Google for various requests. This brings them traffic and money.
- Social media and dating sites are among those coming personal messages Spam is very common. It is also available in the comments to messages.
- Messengers (like ) are also susceptible to this scourge.
- SMS-messages from unknown people of an advertising nature. Probably everyone is familiar with it.
- Search spam- a rather specific thing, but familiar to everyone. Have you ever had a situation where you enter a query into Yandex (Google), and the responses are entirely sites with some kind of bullshit that have nothing to do with the matter. These are so-called doorways (sites with automatically generated useless texts). They spam search engine results, but they make money from visitors visiting them (in different ways).

Those. all letters in your mailbox (or forum messages, blog comments, personal messages) of an advertising or other nature from a sender unknown to you - this is spam. True, the newsletters you have subscribed to can also be intrusive, but you can still unsubscribe from them (refuse to receive them further).
Spam itself is annoying and annoying, because it litters where it appears. Most often, this is your inbox, and it can be quite difficult to separate the wheat from the chaff when there are too many unwanted messages. But spam can also pose a real danger to both you and your computer. Let's figure this out.
Understanding the types of spam (harmless and dangerous)
From now on I will mainly talk about spam messages arriving by email, because it is this channel that is considered especially susceptible to this phenomenon. Everything else is not as neglected and is not so actively used by spammers, and this does not apply to all network users. But the problem of protecting them from unwanted messages is acute.
Types of harmless spam
- Advertising of legal goods and services- in this case, the business owner simply chose spam mailings as one of the channels for attracting clients and customers, because it is not expensive, fast and brings results. Naturally, he doesn’t think much about the moral (or rather immoral) side of this matter.
- Prohibited advertising— there are goods and services that are prohibited by law from advertising, and for them spam mailings can be the main channel for attracting customers. By the way, spammers also advertise their services through mass mailings, since this activity is prohibited by law. This also includes advertising that discredits competitors, since this is also prohibited by law (praise yourself, but don’t scold others).
- Impact on public opinion- very often spam becomes a good choice for those who are trying to manipulate public opinion in the desired direction. This could be politics, as well as commerce. Letters in general can be sent supposedly from some person in order to compromise him, change his opinion about him, or use his authority for profit. But this does not pose a danger to you personally.
- Letters that ask to be forwarded to others- these can be varieties of so-called “letters of happiness” (send it to 10 friends and you will be happy), or asking to send information to friends for some other reason. Often such letters are used by spammers to collect or replenish already existing base Emails for subsequent mass mailings.
High-risk spam - what it can be

If ordinary (harmless) spam can only slightly affect your peace of mind and mental health, then the examples below can be very dangerous for your wallet or computer. And this is no joke.
I myself (the one who teaches and trains everyone) a couple of years ago “bought” a similar type of letter (phishing) and parted with several thousand rubles (read “”). I just got wrapped up and did everything “automatically” just to get behind, well, when I realized it, it was too late.
- - Very effective method deceiving not only gullible people, but also simply busy or inattentive people (there is a hook for everyone). They send you a letter supposedly from your bank or service electronic money or from somewhere else. In this letter, you will definitely be taken aback by something (unsettled) and asked to log in to the site to solve the problem. You log in, but the site will be fake (although it looks exactly like the real one) and the data you provided will be immediately used to steal all your money.
- Nigerian letters- you find out that you can get a large amount of money (various pretexts - from an unexpected inheritance to helping a prince in exile). You don’t believe it for a long time, but they convince you. When you believe it, you will be asked to transfer some money for “related expenses.” You translate and no one will bother you anymore.
- Viruses, worms, Trojans— the letter may contain an attached file with malware(or a link leading to a site with a virus). She can immediately cause problems with the operation of the computer, or she will sit quietly in a corner and carefully write down all the passwords, logins and other useful household things you enter. Worms, among other things, can also send themselves to your friends using the email addresses found in your contacts (as they will call you later...).
Spam protection
Where do spammers get databases with email addresses?
- Spammers (those who send mass mailings) collect email addresses from all available sources. These could be forums guest books, chats, social media and other sites where postal addresses may be publicly available.
- Hackers manage to get to some databases of addresses stored on websites.
- Emails are collected in most cases programmatic method(using search bots - harvesters) and this is not required special effort(only time and not very much). Moreover, similar spam email databases You don’t have to collect them, but buy them from those who specialize in this matter ().
- There are billions of email addresses registered all over the world, and therefore you can simply try to generate Emails using special programs using appropriate dictionaries. With a high degree of probability, many of them will actually exist. Read below about how spammers check the reality of addresses.
- There are special worms (viruses) that can send themselves to a database of addresses found on the victim’s computer. The database collected in this way will already be cleared of non-working mailboxes.
How do spammers clean databases of inactive email addresses?
Those who collect a database of addresses essentially don’t care who owns this or that address - they send letters to everyone, because there will still be someone who will respond to them (as they say - they hit the squares).
But still, in order to optimize costs and increase the return on mailings, it is beneficial for them to clear the databases of non-existent addresses. How do they do it? Let's get a look.
- The simplest thing is to place a picture in the letter (maybe not even visible - one pixel in size), which will be loaded from the site owned by the spammer when the user opens the letter. If the picture is loaded, it means the letter was opened and the email is valid.
- Many email clients (programs for working with email) automatically send a message that the letter has been read, which again plays into the hands of spammers.
- The letter may contain a link urging you to go somewhere, promising mountains of gold. We've moved on - consider that your Email will now be marked as valid. The most unpleasant thing is that such a link can be disguised as an unsubscribe button, which will actually lead to the opposite effect.
How to reduce the likelihood of your email getting into the spam database?

In general, as soon as your mailbox is “verified,” spammers won’t just leave you. It is important to understand that no one is immune from spam. But it is possible significantly reduce the likelihood of getting into such a spam database if you take the following precautions:
- You can, of course, not publish your Email anywhere at all and not tell it to anyone. But in most cases this is difficult to do, so I advise except the main drawer have one or two minor ones that you will use to register on forums, etc. Often they can also come in handy, which can be obtained without registration at all.
- Do not click on links in spam emails (even if there is an “Unsubscribe” button - this is a trap) and, if possible, disable automatic download images in the email client program you are using. There is a chance that your Email will be counted as inactive and mass mailings will not arrive at hundreds per day.
- If you have not yet registered a mailbox or are planning to create a new one (for example, because the old one is completely clogged with spam), then do not proceed from the convenience and ease of remembering it, but on the contrary, make it longer and more complex. To your friends, you will still send it to in electronic format, but spam search programs are unlikely to guess it.
What to do if spam no longer lets you breathe?
It was all preventive measures combating spam (or rather reducing its quantity). But there is a possibility effective fight even in full neglected situation. In this case, it becomes extremely important.
The fact is that in such large services as or, there are powerful antispam filters.

They place all suspicious emails in a separate Spam folder, thereby freeing the Inbox from junk. Yes, there is no perfect spam cutter, and whenever possible, before cleaning, it would be better to view the contents of the Spam folder diagonally to see if it contains legitimate correspondence. But it’s still much easier than digging through all this garbage all the time.
If you have a mailbox on another service, where the spam cutting is poor (for example, as in), then you shouldn’t despair. Get yourself an Email on Gmail or Yandex, and then set up mail forwarding to it from your old mailbox. Moreover, these settings can be made as in the old mailbox (i.e. set up forwarding - shown in the screenshot):

Also, in the new mailbox, you can configure the collection of mail from your existing Emails (the screenshot shows the settings for collecting mail in Gmail):

The same can be said about programs mail clients . Most of them also have a built-in spam cutter.
But in this case we should not forget that on postal service will have its own spam folder. this can be corrected in the settings of the service or client program).
Good luck to you! See you soon on the pages of the blog site
You can watch more videos by going to");">

You might be interested
Account - what is it, how to create or delete it  Create an email - what is it, how and where to register and which email to choose (mailbox)
Create an email - what is it, how and where to register and which email to choose (mailbox)  What is Email (E-mail) and why is it called email
What is Email (E-mail) and why is it called email  How to restore a page in Contact (if access is lost, deleted or blocked)
How to restore a page in Contact (if access is lost, deleted or blocked)
Spam is the sending of advertising letters of a political or commercial nature to people who have not subscribed to it. Spam refers to emails, received by user's email, phone, social applications like whats app, skype and many others. Main topics letters can be different: from a visit to a resort to an offer to earn big money or receive a prize for some action that the user has never done.
The first episode of spamming took place in the nineteenth century. In 1864, British politicians received telegrams advertising dental services by telegraph. In the twentieth century, a similar term was used to designate the trademark of Hormel Foods Corporation. This there was an abbreviation SPAM stood for SPiced hAM, which translated meant “spicy ham.” After the war, advertisements about unconsumed canned food were broadcast at every turn - from the radio, newsstands, on trams and buses. There was a sketch on a television show in Britain called "SPAM". This is where the modern name comes from.
Sometimes spam turns from harmless letters into real black PR. For example, with its help, one company can denigrate another by sending Internet and telephone users some kind of defamatory information last message. With the help of such mailings, pornography, drugs and much more are advertised, which is prohibited by law.
Masked as spam money swindling. For example, a woman receives a message in the mail that her son was in an accident and asks to send money for a complex operation and the number where the savings should be sent. Those women who have never encountered such actions believe and send money. And then it turns out that the son is healthy and nothing happened to him. The types will be discussed in more detail below.
Types of spam
The most common type is advertising. With the help of advertising, companies sell services and offer goods. Such advertising is permitted at the legislative level. But many recipients are still wary.
Another type is " Nigerian letters" The name was formed due to the fact that a large number of similar messages were received in Nigeria. The recipient of such a letter is promised a large sum money, but you need to open an account, postage costs, which the scammer will supposedly pay only when the recipient sends the money to him.
Almost the same in appearance is " phishing" Allegedly, the bank administration will block the recipient's account if he does not send his details and does not confirm the data on the site under which the link to the spammers' site is hidden. This way, fraudsters will receive all the necessary data in order to transfer the money in the recipient’s account to themselves.
Letters of happiness, common among schoolchildren and adults, are also one of the varieties in our country. They are based on the requirement to forward the message as soon as possible more friends. And in return, a miracle will happen in the life of the recipient in a few days. Sometimes such messages may contain negative content. For example, threaten heavenly punishment if a person does not forward a certain number of letters to friends.
All these are legitimate and misconduct committed by people called spammers. They could be mailing services, database collectors, software manufacturers, or even the average user. If a person wants to communicate something to many people without their request or consent, he automatically becomes a spammer.
This type of mailing brings benefits to the customers of letters. It is difficult to fight this species, but it is possible.
How to fight spam
You can deal with mailings yourself. If you often receive messages from a particular group or user, you can always add the person to black list and make sure that messages fall into a specially designated block. On the website mail.ru, or Yandex.Mail, it is called “Spam”.
For the user who wants to protect himself from spammers, Not recommended publish your mailing address on public sites. Or create a special box if you have to register in unreliable groups and communities. Not recommended respond to similar messages or follow the links in them. Perhaps the link already contains a script that will block your computer or phone best case scenario. At worst, he will gain access to your cards and bank accounts.
There are special software, which protects against annoying mailings. Typically, such antispam modules are built into the antivirus or installed separately. Kaspersky Lab, Antispam, Counterspam are the best of these programs.
It is recommended to blacklist such senders on phones. Letters will arrive in separate block called "Antispam" on the phone. And if the recipient wants, he can look, if not, he can put it on automatic removal after a certain number of days.
You can find examples in the pictures below. These are like this harmless mailings also called spam on the Internet.


These are examples of mailings from ordinary users. There are entire companies, for example, computer repair, window installation, that engage in similar mailings, inserting links to their pages in user names or words. Below is an example:


What to do with spam emails
Why spam is dangerous
First of all, it is dangerous because in the pile of the most different mailings you really have to search for a long time useful letter from a friend or at work. By opening a spam email and clicking on the link, you are exposing yourself and corporate network infection with various viruses. Thirdly, additional load on the network.
Every Internet user knows the word “spam” today. Moreover, he not only knows, but also often sees it in his email box. But not everyone knows that the word “spam” itself was once in no way associated with either the Internet or emails.
Spam is an acronym, a compound word. It was formed from the truncated “spiced ham” - “ham with spices”, “sausage with pepper”, “pepper ham”. Therefore, a direct translation of the English “spam” can be considered something like “spetchina” - “spices” plus “ham”.
The history of this “ham” is as follows: in 1937, the American company Hormel Foods produced minced sausage from the “illiquid” third-fresh meat that had accumulated at the factory. Americans did not buy the unappetizing product, so the owner of the corporation, Mr. Hormel, launched a large-scale marketing campaign, widely advertised his product and began supplying his canned food to the military departments and the navy.
In 1937, Hormel Foods fed American and Allied troops with its products. Even in post-war England, amidst the economic crisis, spam was a staple food for the British. The “pink pieces of meat” described by Orwell in 1984 were the spam of 1948. So the word acquired the meaning of something disgusting, but inevitable.
In December 1970, in the 25th episode of the theater group's sketch Monty Python's Flying Circus, diners find themselves in a restaurant where every dish contains Spam ham. The waitress describes the benefits of spam. A choir dressed as Vikings roars “Spam, spam, spam!” in the background, completely drowning out the conversations of the patrons. Thus, the term “spam” began to be associated with unwanted, annoying, redundant information that “jammes” even useful messages.
The term "spam" in a new meaning (obsessive email newsletter, mail junk) appeared in 1993.
The term “spam” in a new meaning (obsessive email, junk mail) appeared in 1993. Administrator computer network Usenet Richard Depew wrote a program whose error on March 31, 1993 caused two hundred identical messages to be sent to one of the conferences. His dissatisfied interlocutors quickly found appropriate name for intrusive messages - “spam”.
One can also note one of the earliest mass “spam mailings”: in April 1994, the law firm Canter & Siegel hired a programmer who wrote a simple program and advertised the office’s dubious services on the entire conference of the same Usenet network.
Today, the term “spam” (as well as its various derivatives - “spam”, “spammer”, etc.) has been completely reoriented towards e-mail and has come into widespread use, despite the fact that Hormel sausages with this name are produced in the USA still.
UCE and UBE
Before giving our definition of the term “spam,” we should say a few words about spam in general and how exactly it is understood in other countries.
Spam (unrequested information by the user), depending on the goals and objectives of the sender (spammer), may contain commercial information or have nothing to do with it. Thus, based on the content of the message, a distinction is made between “commercial” spam - “unsolicited commercial e-mail” (common abbreviation - UCE) and “non-commercial” - “unsolicited bulk e-mail” (UBE).
In the United States, each state's law often defines unsolicited (commercial) mail differently, and each state's legal status for spam has its own nuances. Most state laws limit the sending of unsolicited commercial emails only - UCE (unsolicited commercial email). However, in a number of states (for example, Connecticut, Delaware, Idaho, Iowa, Louisiana) restrictions were introduced for both UCE and UBE, i.e. for bulk mailings of any unsolicited emails, regardless of their nature.
From the point of view of organizing the text of an email, spam may contain information in the “Subject” field about what it is this message(for example, that it contains advertising information), and in the body of the letter - an indication of why the sender is contacting the recipient without prior consent, as well as information about what actions the recipient should take in order not to receive messages from sender, i.e., contain information about an email address, Internet resource or telephone number (usually a toll-free phone number), which are intended for unsubscribing (terminating subscription) from unsolicited information (“opt-out” function).
These signs (indication in the Subject field and the presence of an unsubscribe mechanism) indicate that the sender understands that the information he offers is being imposed on recipients, and that he is making a good faith attempt to reduce the possible negative impact on them. But very often, the spammer not only does not feel the desire to reduce the discomfort of spam, but also refuses responsibility for his actions by falsifying the sender's address, using a third party's address and falsifying message headers. All this is done in order to make it as difficult as possible to identify the sender and take appropriate measures against him.
Definition of spam
According to Kaspersky Lab's definition, spam is anonymous mass unsolicited mailing.
In this definition, every word included is important.
Anonymous: everyone suffers mainly from automatic mailings with a hidden or falsified return address.
Uninvited: Obviously, subscription mailing lists and conferences should not fall under our definition (although the anonymity condition largely guarantees this).
The definition of spam often includes the words “advertising” or “commercial offer.” This is not entirely true - a significant part of spam does not serve advertising or commercial purposes. There are political spam mailings, there are “charitable” spam letters, there are fraudulent (“Nigerian”, phishing), “chain letters” - letters with a request to forward to friends (horror stories, “chain letters”), viral and others that are not a commercial enterprise.
Thus, we divide all unsolicited proposals that fall into the box into:
- spam that has all the signs of anonymous mass mailing,
- targeted commercial offers.
The first ones need to be filtered and sometimes immediately deleted - according to company policy. The latter can also be filtered, but they need to be handled more carefully.
Surely each of us, when opening our mailbox, found colorful leaflets containing advertising information. There they offered you to visit some resort, earn a million, be cured of the evil eye, etc.
And only a few, having read these leaflets, found them useful for themselves. It is this kind of sending of information that is called unsolicited advertising, spam mailing or simply spam.
The term "spam" refers primarily to emails. Quite often, almost all email that the recipients have not requested is classified as spam. Recently, experts have studied all types of spam, as a result of which they concluded that if all unwanted or advertising letters are massively classified as spam, there is a danger of losing business mail.
To better understand what spam is, let's look at
Main types of spam
When you get to some sites, you can’t help but pay attention pop-up windows with advertisements of different nature. Such advertising windows generate income for the site author. To increase income, several of these pop-up windows are sometimes installed on the site.
The next type of spam is repeated sending of messages in newsletters (the so-called “ spam mailing"). Each such newsletter is usually devoted to a specific topic. The visitor subscribes to it in the hope of receiving information of interest to him. According to the rules of such mailings, advertising messages are allowed, but with certain restrictions(for example, no more than once a week).
However, those who send spam are of little interest to these rules. They send their advertisements daily to several mailing lists. At the same time, spammers do not pay any attention to the topic. A similar situation Spam mailings can be found in chat rooms, forums and various message boards.
Another type of spam - filling guest books with advertisements. Some resources may contain guest books so that visitors can leave their messages (wishes, comments, suggestions, etc.) in them. However, spammers manage to leave their mark here too. They are not at all interested in the content of sites; they simply find links to guest books and place their advertisements there.
A common type of spam is spam comments on articles on websites and blogs. Such comments, as a rule, do not correspond to the topic of the article on the site, but always contain links to external resources. Such links can be contained both in the text of the comment and in the name of the comment author.
The distinctive feature of such comments is that they carry general character and therefore suitable for any site. For example, "this interesting article” or “the article is useful, but the algorithm is too complex,” and a link to your spam page must be attached.
Some webmasters, in order to attract visitors to their site, try to deceive search engines. They fill the pages of their resource with invisible text that contains the most popular words(free, download, etc.). Invisible text has the same color as the main background of the site, so the site visitor cannot see it. The user types the phrase “download free music” into a search engine, ends up on a site with dubious content and, naturally, does not find anything he wants.
However, the most common type of spam remains the sending of advertising information via e-mail. If your email address is included in the “spam database”, then “write - it’s gone”, because unsubscribing from such mailings is often not so easy, and sometimes it is simply impossible.
How to fight spam?
How to unsubscribe from spam mailings? This is possible if there is a link at the end of the letter “ cancel subscription", or "unsubscribe". By clicking on this link, you can remove your e-mail from the spam database. Unfortunately, such a link may not be available, so let’s move on to the second option on how you can “break up” with spam mailings.
Comments on the site containing spam must be deleted by the site author manually or using a special plugin.
It is better not to visit sites of dubious content with a bunch of pop-up windows at all, in order to avoid the possibility of picking up viruses on your computer, which can be missed by any antivirus (“even an old woman can get screwed”).
How to fight spam in Mail.ru mail?
Before we start fighting spam, I want to emphasize that some important and necessary emails end up in Spam by mistake. Therefore, sometimes it is useful to look into the Spam folder, especially if you are waiting for some letter, but it still doesn’t come.
You can explain to your mail server at mail.ru that such letters should be sent to spam.
Let's figure it out
What does it mean to mark as spam?
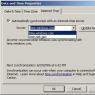
First, you need to select the letter by checking the box next to it (number 1 in Fig. 1, click on the picture to enlarge it):
 Rice. 1 Mark a letter as spam in Mail_ru mail
Rice. 1 Mark a letter as spam in Mail_ru mail Now click on the “Spam” command (number 2 in Fig. 1). This command will only act on letters that have a checkmark next to them (that is, on selected letters). As a result, the letter will be moved to the Spam folder, and mail server mail.ru will remember the sender as a spammer. This is how the manual “mark as spam” procedure works.
If you wish, you can delete a letter from the Spam folder by clicking on the “Clear” command (number 3 in Fig. 1), although after 30 days, letters from the Spam folder will be automatically deleted.
I would like to note that the procedure for sending a letter to Spam may have to be repeated several times. Because the mail server may not understand from the first (and even the second) time that you want to teach it to send letters from this sender directly to Spam. It’s not for nothing that they say that “repetition is the mother of learning”; this rule also applies to mail servers.
How to fight spam in Yandex.ru mail?
The exact same procedure as described above for Mail.ru to mark a letter as spam is suitable for mailbox Yandex.ru.
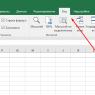
 Rice. 2 Mark the letter as spam in Yandex.ru mail
Rice. 2 Mark the letter as spam in Yandex.ru mail To mark a letter as Spam, you need to
- first check the box next to the letter (number 1 in Fig. 2),
- click on the “This is spam” button (number 2 in Fig. 2),
- Click on the brush to clear the Spam folder (number 3 in Fig. 2). But this is not necessary, because after 30 days such letters are automatically deleted from the Spam folder.
Should I mark a newsletter as Spam if it was previously useful?
There are newsletters that you yourself subscribed to. For some time, this newsletter was useful and interesting to you. Time has passed, the information from the newsletter has become boring, boring, uninteresting, etc. Should such mailings be marked as Spam?
By marking a mailing as Spam, you signal the mail server (on Yandex, Mail ru, etc.) to send letters from this author to Spam. Therefore, the mail server for ALL Internet users (not just you) will send letters from such an author to Spam.
This is NOT always fair to other Internet users who may need this information. In such cases, it will be fair and just unsubscribe from such mailings without marking them as Spam.
What can be concluded from the above?
Spam is information that we did not request, did not subscribe to, and is imposed on us.
However, let’s not forget that “when the forest is cut down, the chips fly.” Therefore, it is necessary to sometimes look into the Spam folder, because important letters may accidentally end up there.
We fight other spam to the best of our ability. It is often better to unsubscribe from a mailing that has become irrelevant than to mark it as spam.