How does VPN work? What is a VPN or how to protect your network. What types of VPN are there?
In this article we will answer the most FAQ what is a VPN server, we will tell you whether a VPN can increase your security, whether you need to use Double VPN and how to check whether the VPN service keeps logs, as well as what modern technologies exist to protect personal information.
VPN is virtual private network, which provides encryption between the client and the VPN server.
The main purpose of a VPN is to encrypt traffic and change the IP address.
Let's figure out why and when this is needed.
Why do you need a VPN?
All Internet providers log the activities of their clients on the Internet. That is, the Internet provider knows which sites you visited. This is necessary in order to provide all information about the violator in case of requests from the police, and also to relieve oneself of all legal responsibility for the user’s actions.
There are many situations when a user needs to protect his personal data on the Internet and gain freedom of communication.
Example 1. There is a business and it is necessary to transmit confidential data over the Internet so that no one can intercept it. Most companies use VPN technology to transfer information between company branches.
Example 2. Many services on the Internet operate on a geo-referenced basis and prohibit access to users from other countries.
For example, the Yandex Music service only works for IP addresses from Russia and other countries former CIS. Accordingly, the entire Russian-speaking population living in other countries does not have access to this service.
Example 3. Blocking certain sites in the office and in the country. Offices often block access to social networks so that employees do not spend work time for communication.
For example, in China many are blocked Google services. If a Chinese resident works with a company from Europe, then there is a need to use services such as Google Disk.
Example 4: Hide visited sites from your ISP. There are times when you need to hide the list of visited sites from your Internet provider. All traffic will be encrypted.
By encrypting your traffic, your ISP won't know what sites you've visited on the Internet. In this case, your IP address on the Internet will belong to VPN country server.
When you connect to a VPN, a secure channel is created between your computer and the VPN server. All data in this channel is encrypted.

With a VPN, you will have freedom of communication and protect your personal data.
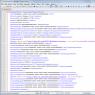
In the logs of the Internet provider there will be a set different characters. The picture below shows an analysis of the data obtained by a special program.
The HTTP header immediately shows which site you are connecting to. This data is recorded by Internet service providers.

The following picture shows the HTTP header when using a VPN. The data is encrypted and it is impossible to find out which sites you visited.

How to connect to a VPN
There are several ways to connect to a VPN network.
- PPTP is an obsolete protocol. Most modern operating systems have excluded it from the list of supported ones. Disadvantages of PPTP - low connection stability. The connection may fail and unprotected data may leak onto the Internet.
- L2TP (IPSec) connection is more reliable. Also built into most operating systems (Windows, Mac OS, Linux, iOS, Android, Windows Phone and others). Is different better reliability unlike PPTP connections.
- SSTP connection was developed relatively recently. It is only supported on Windows, so it is not widely used.
- IKEv2 is a modern protocol based on IPSec. This protocol has replaced the PPTP protocol and is supported by all popular operating systems.
- OpenVPN connection is considered the most reliable. This technology can be flexibly adjusted even in case of a fall. OpenVPN connections blocks sending unprotected data to the Internet.
There are 2 data transfer protocols for OpenVPN technology:
- UDP protocol – is fast (recommended for use) VoiP telephony, Skype, online games)
- TCP protocol – characterized by the reliability of transmitted data (requires confirmation of receipt of the packet). Slightly slower than UDP.
How to set up a VPN
Settings VPN connections takes a few minutes and differs in the VPN connection method.
On our service we use PPTP and OpenVPN connections.
Security of working with a VPN program
We will always talk about integrated approach to safety. User security consists of more than just the VPN connection itself. It is important what program you use to connect to the VPN server.
Currently, services offer convenient VPN clients - these are programs that make it easier to set up a VPN connection. We ourselves offer a convenient VPN client. Thanks to such programs, setting up a VPN connection takes no more than 1 minute.

When we first started providing VPN services in 2006, all of our users set up the official OpenVPN application. It has an open source. Of course, setting up the official OpenVPN client takes longer. But let's figure out what is better to use in terms of anonymity.
VPN client anonymity
We see danger in using similar programs. The thing is that the source code of such programs is the property of the company and in order to preserve the uniqueness of its program, no one publishes it.
Users cannot find out what data the program collects about you in the absence of open source code.
VPN programs and can identify you as a specific user even when the logs on the server are turned off.
Any program can have the functionality to record the sites you have visited and your real IP address. And since you enter your login into the program yourself, it is impossible to talk about any anonymity in using the program at all.
If your activity needs high level anonymity, we recommend that you abandon such VPN programs and use the official open source OpenVPN release.
At first you will find this inconvenient. But over time, you will get used to it if the factor of security and anonymity comes first for you.
We guarantee that Secure Kit does not store any data about you. But we must warn you that such programs can spy on you.
Another idea on how to increase your security came from the point of view of the geographical location of servers. On the Internet it is called an offshore VPN.
What is an offshore VPN
Different countries have different levels legislation. There are strong states with strong laws. And there are small countries whose level of development does not allow information security data in your country.
Initially, the concept of offshore was used to designate a country in which tax policy was relaxed. Such countries have very low business taxes. Global companies have become interested in legal tax avoidance in their country, and offshore bank accounts in the Cayman Islands have become very popular.
Currently, many countries around the world already have bans on the use of bank accounts in offshore countries.
Most offshore countries are small states located in remote corners of the planet. Servers in such countries are more difficult to find and are more expensive due to the lack of developed Internet infrastructure. VPN servers in such countries began to be called offshore.
It turns out that the word offshore VPN does not mean anonymous VPN, but only speaks of territorial affiliation with an offshore state.
Should you use an offshore VPN?
Offshore VPN presents additional benefits from an anonymity point of view.
Do you think it’s much easier to write an official request:
- to a police department in Germany
- or to the Islands Police Department in Antigua Barbuda
Offshore VPN is an additional layer of protection. An offshore server is good to use as part of a Double VPN chain.
There is no need to use only 1 offshore VPN server and think that this is complete security. You need to approach your security and anonymity on the Internet from different angles.
Use an offshore VPN as a link to your anonymity.
And it's time to answer the most frequently asked question. Can an anonymous VPN service keep logs? And how to determine whether the service keeps logs?
Anonymous VPN service and logs. What should I do?
An anonymous VPN service should not keep logs. Otherwise, it can no longer be called anonymous.
We have compiled a list of questions, thanks to which you can accurately determine whether the service keeps logs.
Now you have full information about VPN connections. This knowledge is enough to make yourself anonymous on the Internet and make safe transfer personal data.
New VPN technologies
Are there any new trends in the VPN space?
We have already talked about the pros and cons of sequential cascading VPN servers(Double, Triple, Quad VPN).
To avoid the disadvantages of Double VPN technology, you can make a parallel cascade of chains. We called it Parallel VPN.
What is Parallel VPN
The essence of Parallel VPN is to direct traffic to a parallel data channel.
The disadvantage of sequential cascading technology (Double, Triple, Quad VPN) is that on each server the channel is decrypted and encrypted into the next channel. Data is consistently encrypted.
There is no such problem with Parallel VPN technology, since all data undergoes double parallel encryption. That is, imagine an onion that has several peels. In the same way, data passes through a channel that is double encrypted.

Previously, the state had a rather mediocre understanding of the Internet, so it did not legally interfere with users. Today, while walking on the World Wide Web, you can increasingly come across the phrase: “This site is included in the register of prohibited sites” or “Your ISP has blocked access.”
So, if you want to regain complete freedom of action on the Internet and acquire another level of protection, then you definitely need to familiarize yourself with the technology of virtual private networks - VPN.
VPN: term and principle of operation
Virtual Private Network (VPN) is the name of a technology that allows the creation and overlay of one or more networks on top of any other user network.
Now, how exactly does a VPN work? Your computer has a specific IP address that blocks access to certain sites. You enable VPN technology through some program or extension. VPN changes your address to an address from a server in another country (for example, Holland or Germany).
Next, a security connection is created, which cannot be blocked by the provider. As a result, you get a secure protocol through which you can freely visit any Internet site, and completely anonymously.
Structure and types of technology
The whole technology works in two layers. The first is an internal network, the second is an external one. When you connect to the technology, the system identifies your network and then sends an authentication request. This technology very similar to authorization in some social network, only here everything is carried out through secure protocols and without the participation of the provider.
Virtual networks themselves are also divided into several categories. The main classification is based on the degree of protection, that is, the user can use both paid VPNs, and free.
The difference between them is the secure connection. For example, subscription systems will give you secure protocols such as PPTP, IPSec and others. While free VPNs often provide only “trusted” channels. That is, your network itself must be highly protected, and a VPN will only enhance the level of protection.
To be honest, the biggest disadvantage of free VPN services not even security, but stability and connection speed. Through free VPN The Internet will most likely work very slowly, and not always stable.
A subscription to paid VPNs does not exceed $10 per month, but not every user needs it. For ordinary tasks, there is no point in purchasing Premium accounts; standard capabilities are sufficient.
Reasons to use a VPN
Every user needs to use VPN technology, and here's why:
- Data protection. Especially suitable for those users who like to connect to a neighbor’s “free” Wi-Fi connection, and then discover that their card data has been stolen. Such situations include gatherings in cafes and generally in any places with free Wi-Fi.
- Complete anonymity. When you open new tab with the site - this action will be displayed on the provider’s server, so that your journey on the Internet can be tracked by any employee of the company. By turning on a VPN, you will hide your browsing history because you are using a different IP address.
- The ability to surf the Internet without obstacles. Bookmakers, online casinos, torrents, forums, sites for adults - all the “underground” of the Internet is again available to you, everything is like in the old days.
- Use of foreign resources. It is, of course, unlikely that you will use English-language services such as hulu.com, but still, you are provided with full access to all popular sites around the world.
How to use VPN on a computer?
Let's consider a situation where we use a regular browser and want to visit blocked sites. In this situation, you can go two ways:
- install the VPN client (program) on your PC;
- add a browser extension via Webstore.
Both the first and second options are easy to implement, but for the full picture, let’s consider both.
You can also use the free one.
To install a VPN client, you need to download a program on the Internet, for example, “Betternet”. Let's launch installation file and install the client. We launch it, click: “Connect” and that’s it. The problem is that the program automatically gives us a random IP address, and we cannot select a country, but by pressing just one button we are already using a VPN. And one more disadvantage is the need to constantly launch the program, however, some clients have the ability to launch it simultaneously with the OS.
The second way is to add an extension. The downside here is that, most often, registration is required to use it, plus the extensions have the ability to crash. But the extension is much easier to use - click on the icon in the browser, select the country and profit. On this moment There are thousands of similar programs, you can choose any of them, for example, “ Hotspot Shield" Add the extension to your browser, register and no more technical points will not be.
For example, this is how it works ZenMate extension VPN in browser:

ABOUT VPN extensions For different browsers we wrote in the article: .
How to use VPN on mobile devices?
We will look at those devices that have popular operating systems on board, for example, iOS or Android.
Using a VPN on smartphones or tablets is also quite simple, namely through mobile applications. The problem is that some programs require root rights, and these are additional hassles, plus the possibility of turning the phone into a “brick”. So look for programs that do not require you to have root rights. On Android, for example, it is OpenVPN, and on iOS it is Cloak. You can also use the free and proven one on iPhone and iPad. I use it myself sometimes, it works great.

The download technology is very simple: download the application from Play Market or AppStore, install it on your device. Next, we activate the VPN, select a profile (from where we will get the IP address), then make a connection and that’s all. Now you are surfing the Internet through a VPN, which the application you are using will tell you about.
Now you understand how VPN connection technology is implemented, and now your online experience will become more secure, anonymous, and most importantly - accessible and unlimited.
The ability to connect remote company offices with each other via secure communication channels is one of the most common tasks when building a distributed network infrastructure for companies of any size. There are several solutions to this problem:
Renting channels from a provider: A common and reliable option. The provider leases dedicated physical or logical communication channels. Such channels are often called “point-to-point”
Advantages:
- Ease of connection and use - maintenance of equipment and channels is entirely the responsibility of the provider;
- Guaranteed channel width – data transfer speed always corresponds to that stated by the provider;
Flaws:
- Security and control – the company cannot control the equipment on the provider’s side.
Building your own (physical) communication lines: A reliable and cost-effective solution, since the construction of a physical communication channel is entirely the responsibility of the company. With this solution, the company fully controls and services the constructed channels.
Advantages:
- Flexibility – the ability to deploy channels that suit everyone necessary requirements;
- Security and Control – full control channel, since it belongs to the company;
Flaws:
- Deployment – Building such private channels is a labor-intensive and expensive solution. Laying kilometers of optics along poles can cost a fortune. Even if you don’t take into account obtaining permits from all state authorities. authorities;
- Maintenance – channel maintenance is entirely the responsibility of the company, so the staff must have highly qualified specialists to ensure its performance;
- Low fault tolerance - external optical lines communications are often subject to unintentional damage (construction equipment, utilities, etc.). It may take several weeks for an optical link to be detected and corrected.
- Limited to one location - laying external optical communication lines is only relevant if objects are located within several tens of kilometers. Extending communications to another city hundreds and thousands of kilometers is not possible for reasons of common sense.
Building a secure channel over the Internet (VPN): This solution is relatively inexpensive and flexible. To connect remote offices, an Internet connection and network equipment with the ability to create VPN connections are sufficient.
Advantages:
- Low cost – the company pays only for Internet access;
- Scalability – to connect a new office you need the Internet and a router;
Flaws:
- Channel capacity – data transfer speed may vary (there is no guaranteed bandwidth);
This article will take a closer look at the last point, namely, what benefits VPN technology provides to businesses.
Virtual private network (VPN) is a set of technologies that provide a secure connection (tunnel) of two or more remote local networks via public network(approx. Internet).
Unique advantages of geographically distributed VPN networks
Protection of transmitted traffic: it is safe to transmit traffic through the VPN tunnel using strong encryption protocols (3DES, AES). In addition to encryption, the integrity of the data and the authenticity of the sender are verified, eliminating the possibility of substitution of information and connection by an attacker.
Connection reliability: leading equipment manufacturers are improving VPN connection technologies, providing automatic recovery VPN tunnels in case of a short-term failure of the connection to the public network.
Mobility and ease of connection: you can connect to the company’s local network from anywhere in the world and from almost any modern device(smartphone, Tablet PC, laptop), and the connection will be secure. Most manufacturers multimedia devices added VPN support into your products.
Redundancy and load balancing: if you use two providers when connecting to the Internet (for balancing/failover), then it is possible to balance VPN tunnel traffic between providers. If one of the providers fails, the tunnel will use a backup connection.
Traffic prioritization: the ability to manage traffic using QoS - prioritization of voice, video traffic in case of high load to the tunnel.
VPN networks in business
Unified network
Consolidation of geographically distributed local networks of the company into single network(connecting branches to the main office) significantly simplifies interaction and data exchange within the company, reducing maintenance costs. Any corporate systems demand a single network space for employee work. This could be IP telephony, accounting and financial accounting, CRM, video conferencing, etc.
Mobile access
Regardless of the employee’s location, if he has the Internet and a laptop/smartphone/tablet, the employee can connect to the company’s internal resources. Thanks to this advantage, employees have the opportunity to perform work and quickly solve problems while outside the office.

Consolidation of networks of different companies
It is often necessary to combine networks of business partners, and such a union can be organized both with and without restricting access to the internal resources of each company. This association simplifies interaction between companies.

Remote management of IT infrastructure
Thanks to the protected remote access to the company's IT infrastructure equipment, the administrator is capable of as soon as possible solve problems and respond to problems that arise.

Quality of service
Traffic from video conferencing, IP telephony and some other applications requires a guaranteed channel width. Thanks to the use of QoS in VPN tunnels, for example, you can combine IP telephony of the company’s local network and a remote office.

Areas of application of distributed VPN networks and corporate data networks (CDNs)
Having analyzed the requirements and objectives of organizations various scales, we have compiled a general picture of solutions for each of them. Below is a description of typical implementations of VPN technology in a company's network infrastructure.
Solutions for small businesses. Often the requirements for such a solution are connectivity remote users(up to 10) to an internal network and/or combining networks of several offices. Such solutions are simple and quick to deploy. For such a network, it is recommended to have a backup channel with a speed lower or the same as the main one. The backup channel is passive and is used only if the main one is disconnected (the VPN tunnel is automatically built over the backup channel). Redundancy of edge equipment for such solutions is rarely used and often unjustified.
Traffic transmitted through the tunnel - traffic internal applications(mail, web, documents), voice traffic.
Requirement for channel reservation: average
Equipment redundancy requirement: low

Solutions for medium-sized businesses. Along with connecting remote employees(up to 100), network infrastructure must provide connection to several remote offices. For such solutions, Internet channel reservation is mandatory, and throughput The backup channel must be comparable to the speed of the main channel. In many cases, the backup channel is active (load balancing between channels is carried out). It is recommended to reserve equipment for critical network nodes (eg the border router of the central office). VPN network topology – star or partial mesh.
Requirement for equipment redundancy: average
.jpg)
Solutions for large businesses, distributed network of branches. Such networks on a fairly large scale are difficult to deploy and support. The topology of such a network from the point of view of organizing VPN tunnels can be: star, partial mesh, full mesh (the diagram shows the full mesh option). Channel reservation is mandatory (more than 2 providers are possible), as is the reservation of equipment of critical network nodes. All or several channels are active. Networks of this level often use leased lines or VPN provided by providers. In such a network, it is necessary to provide maximum reliability and fault tolerance in order to minimize business downtime. Equipment for such networks – flagship line enterprise class or provider equipment.
Traffic transmitted through the tunnel – traffic of internal applications (mail, web, documents), voice traffic, video conferencing traffic.
Requirement for channel reservation: high
Equipment redundancy requirement: high

Educational institutions. For educational institutions typical connection to the network control center. The traffic volume is most often not high. Reservation requirements are set in rare cases.
Medical institutions. For medical institutions There is an acute issue of reliability and high fault tolerance of communication channels and equipment. All branches of a geographically distributed network use redundant channel-forming equipment and several providers.
Solutions for retail (chain stores). Store chains are distinguished by their large number of locations (there can be thousands of stores) and relatively low traffic to the main office (data center). Reserving equipment in stores is most often not advisable. It is enough to reserve a connection to the provider (in the “second provider on hand” format). However, the requirements for the equipment located in the data center (head office) are high. Since this point terminates thousands of VPN tunnels. Constant monitoring of channels, reporting systems, compliance with security policies, etc. is required.
Implementation of distributed VPN networks and corporate data networks (CDNs)
Choice necessary equipment And correct implementation service is difficult task, requiring high expertise from the performer. The LanKey company has been carrying out complex projects for many years and has extensive experience in such projects.
Examples of some projects for the implementation of KSPD and VPN, implemented by LanKey
| Customer | Description of work performed |
|
|
Equipment Manufacturer: Juniper Solution: six remote branches of the company were connected to the main office using a star topology via secure communication channels. |
|
Solution: we connected to the Internet and built VPN tunnels in offices located in Moscow and Geneva. |
|
|
|
Equipment Manufacturer: Cisco Solution: Remote offices integrated over a secure channel with fault tolerance across providers. |
Soon there will be articles on the site talking about anonymity on the Internet with using VPN. We will set up a VPN on different devices. In order not to write every time in every article what a virtual private VPN network I decided to write this article.
If you are interested in issues of anonymity on the Internet, I advise you to read the article “” where we talked about proxy connections, why proxies are needed and what types there are.
In this article I will not dig deep. I will only tell you about the most important things that a person who is thinking about anonymity on the Internet needs to know.
Virtual private network Virtual Private Network (VPN) is a technology that provides the ability to provide one or more network connections over another network, such as the Internet.
This connection has the form of an encrypted tunnel that connects directly the user’s computer and remote server, which allows you not only but also to encrypt your traffic. In other words, this way you will be able to download anything from anywhere, and no one will know about it.
Types of VPN connections
You can set up the following types of VPN connections: As I said earlier, all information is reduced to the necessary minimum. Read more in specialized literature.
Virtual private network PPTP
RRTR- Point-toPoint Tunneling Protocol is a point-to-point tunnel protocol that will help establish a secure tunnel in an unsecured network. It is the most popular VPN connection method, but many Internet providers block such applications.
OpenVPN Virtual Private Network
OpenVPN- is a free implementation of this technology with the provision open source to create your own encrypted channels using the “point-to-point” or “server-client” types. The latter allows you to use another computer as a VPN server. However, setting up a tunnel requires installing a special software coupled with the knowledge to work with it.
L2TP Virtual Private Network
L2TP(Layer 2 Tunneling Protocol) is the most labor-intensive type of VPN tunnel to set up, but allows you to create it with specified access priorities, making it the most secure.
And although VPNs are not literally anonymizers, today most sites providing CGI-proximity services offer to purchase their own VPN channel. This technology is gaining momentum, so it is likely that soon the number of familiar anonymizers will be reduced to the required minimum.
They have become commonplace. True, no one really thinks about what is behind the concept like “VPN, setup, use, etc.” Most users prefer not to get into the weeds computer terminology and use standard templates. But in vain. From knowledge about such connections, you can derive a lot of benefits, for example, increase traffic or connection speed, etc. Let's look at what a connection to a virtual network actually is, using the example of interaction between operational Windows systems on a desktop computer terminal and Android on a mobile device.
What is VPN
Let's start with the fact that VPN setup is impossible without general principle understanding the essence of the connection being created or used.
If you explain in simple words, in such a network there is necessarily a so-called router (the same router), which provides computers or mobile devices trying to connect to existing network, standard additional IP addresses for access to LAN or the Internet.
At the same time, a virtual network in which there is activated setting VPN connections are accepted by any device connected to it and assigned a unique internal IP address. The range of such addresses is in usual standard from zero to value 255.
What’s most interesting is that even when accessing the Internet, the external IP address of the device from which the request is made is not so easy to determine. There are several reasons for this, which will be discussed below.
The simplest VPN setup for Android
Almost all virtual networks using wireless connection By Wi-Fi type They work on the same principle - assigning free IP addresses from the available range. It's no surprise that any mobile device can easily be connected to them (but only on condition that it supports the appropriate connection protocols).

However, today any smartphones or tablets based on the Android OS have in their functionality the option of connecting the same Wi-Fi. The network is detected automatically if the device is within its coverage area. The only thing you may need is to enter a password. The so-called “shared” ones do not require a password at all.

IN in this case You need to go to the main settings on your smartphone or tablet and activate Wi-Fi connection. The system itself will determine the presence of radio modules at a distance of 100-300 meters from the device (it all depends on the model of the distribution router). Once the network is identified, a menu will be displayed with all available connections and their blocking indication. If the network has a padlock icon, it is password protected (however, this will be indicated initially in the message). If you know the password, enter it.
In public networks, where login using a password is not provided, it is even simpler. Has the network been determined? All. Click on connection and use it. As is already clear, VPN configuration in this case is not required at all. Another thing is when to use Windows settings or another operating system (even mobile) to create a connection or assign computer terminal or laptop as a VPN server.
Creation on Windows
With operating systems of the Windows family, not everything is as simple as most users think. Of course, automatic recognition of a network or connection via Wi-Fi, ADSL or even direct connection via network Ethernet card they produce (subject to availability installed equipment). The question is different: if the distributor is not a router, but a laptop or desktop computer how to get out of this situation?
Main settings
Here you will have to delve into the VPN settings. Windows as an operating system is considered first.

First you need to pay attention not even to the settings of the system itself, but to its accompanying components. True, when creating a connection or using it to the maximum, you will have to configure some protocols such as TCP/IP (IPv4, IPv6).
If the provider does not provide such services in automatic mode, you will have to make settings indicating previously obtained parameters. For example, when connecting automatically, the fields in the Internet browser properties for filling will be inactive (there will be a dot on the item “Obtain an IP address automatically”). That is why you do not have to enter the values of the subnet mask, gateway, DNS or WINS servers manually (especially for proxy servers).
Router settings
Regardless of whether the VPN is configured on an ASUS laptop or terminal (or any other device), access to the network is still common.
To do it correctly, you need to go to its own menu. This can be done using any Internet browser, provided that the router is directly connected to a computer or laptop.

In the address field, enter the value 192.168.1.1 (this corresponds to most models), after which you should activate the enable function (using the router parameters in advanced mode). Typically this line looks like WLAN Connection Type.
Using VPN Clients
VPN clients are quite specific programs that work like anonymous proxy servers that hide the true IP address of the user's computer when accessing the Internet. local network or on the Internet.

Actually, the use of programs of this type is reduced to almost complete automation. The VPN setting in this case, in general, is not important, since the application itself redirects requests from one server (mirror) to another.
True, you will have to tinker a little with setting up such a client, especially if you want to make the most of your home virtual network available connections. Here you will have to choose between software products. And it should be noted that some applications, even the smallest in size, sometimes surpass the commercial products of many well-known brands, for which you also have to pay (by the way, a lot of money).
What about TCP/IP?
It goes without saying that almost all of the above settings affect the TCP/IP protocol to one degree or another. Today nothing better has been invented for comfort. Even remote ones anonymous proxy servers or local data stores still use these settings. But you need to be careful with him.

It is best to contact your provider or system administrator before changing settings. But one thing must be clearly remembered: even when setting the values manually, as a rule, the subnet mask has the sequence 255.255.255.0 (it can change), and all IP addresses begin with the values 192.168.0.X (the last letter can have from one to three characters ).
Conclusion
However, these are all subtleties computer technology. The same VPN client for Android can provide communication between several smart devices. But the biggest snag is whether it’s worth using such a connection on a mobile gadget.
If you notice, especially in technical details we didn't go into it. This is rather a descriptive instruction about general concepts. But even that simple example, I think, will help, so to speak, to understand the very essence of the issue. Moreover, with a clear understanding of it, the whole problem will be reduced only to the system settings, which will not affect a specific user in any way.
But here you need to be very careful. Actually, for those who don’t know what it is VPN connection, it won't do much. For more advanced users it is worth telling what to create virtual network using native Windows OS tools is not recommended. You can, of course, use initial parameters settings, however, as practice shows, it is better to have some kind of reserve additional client, which will always be like an ace in the hole.
.jpg)