Safe Internet for children: offers from MTS, MegaFon and Beeline
With development mobile networks develops and Mobile Internet. Everyone is used to regular Internet: twisted pair, Ethernet, TCP/IP. What does the mobile internet hide? Let's try to find out! In our study we will touch upon general principles how the mobile Internet works, take a closer look at the GPRS Tunneling Protocol, talk about the GRX network and discuss some practical approaches to the security of the mobile packet network.
How do each of us connect to the mobile Internet? In principle, you only need to know three parameters: APN, login and password. APN is an access point through which a subscriber can connect to the service he needs (WAP, MMS, Internet); for our operators it usually looks like internet.
Now that we know required parameters, we can connect to the mobile Internet! How does this mysterious procedure happen? It happens in two stages:
- GPRS Attach
- PDP Context Activation.
Let's take a closer look at each of them.
GPRSAttach
In the GPRS Attach procedure, the phone begins to “communicate” with the operator’s packet network. Authentication and authorization of user equipment occurs according to the following parameters:
- IMSI ( International Mobile Subscriber Identity individual number subscriber) - to identify the subscriber;
- keys stored on SIM card– for subscriber authentication;
- examination available to the subscriber services (Internet, MMS, WAP) according to an entry in the subscriber database.
IMEI (International Mobile Equipment Identity) can also be checked. This identifier can be used to check against lists of stolen equipment, and if a specific IMEI is on the list of stolen equipment, then access to the network may be denied, or even reported “where it should be” :)
After successful completion of the GPRS Attach procedure, the PDP (Packet Data Protocol) Context Activation procedure begins. To understand this procedure, let's digress and define some concepts.
SGSN (Serving GPRS Support Node, GPRS subscriber service node) is a device that implements the basic functions of processing packet data in a mobile network.
GGSN (GPRS Gateway Service Node, GPRS gateway node) - a device that provides data transfer from the operator’s network to external networks(for example, on the Internet). In fact, it can be a regular router with support for some specific functions.
GTP (GPRS Tunneling Protocol) is a protocol stack used in GPRS, UMTS and LTE networks.
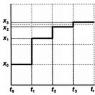
So, PDP Context Activation (the diagram is greatly simplified).

What happens when this scheme is implemented?
- The phone sends a context activation request to the SGSN, which contains, among other things, the username, password and APN.
- The SGSN, having received the APN, attempts to resolve it on the internal DNS server. The server resolves the provided APN and returns the address of the GGSN responsible for this APN.
- The SGSN sends a request to create a PDP context to this address.
- GGSN checks the provided login and password on the RADIUS server.
- Then gets IP address for our phone.
- And all the information necessary to activate the PDP context is sent back to the SGSN.
- The SGSN completes the activation procedure by sending the data necessary to establish the connection to the phone.
Essentially, the PDP Context Activation procedure is the creation of a tunnel between the phone and the gateway in the operator's network.
And now we can go to our favorite sites and read mail.
Roaming
The question immediately arises: how does this all work in roaming? It turns out that there is a special network: GRX (Global Roaming Exchange) - a network for exchanging packet data among roaming subscribers of mobile networks. All our traffic “runs” through it. Something like this:
- Having successfully arrived in warmer climes, we decided to download our favorite series. We turned on the phone and started connecting to the Internet (send login, password, APN).
- The foreign SGSN is trying to resolve the APN we provided on its DNS server.
- The DNS server, not finding similar records, turns to the root DNS server, which is located on the GRX network.
- Root DNS- the server sends a request to the DNS server on the network of our home operator.
- He, in turn, responds to him with the address of our GGSN.
- The root DNS reports this address to the DNS server of the foreign operator.
- Which in turn communicates this address to the foreign SGSN.
- The SGSN, knowing the GGSN address, sends it a request to activate the PDP context.
- GGSN, if all conditions are met (there is money in the account, the correct login and password are indicated, etc.), sends a confirmation, SGSN accepts it and sends confirmation to our phone for Internet access.
What do we see? We see that packages with our favorite TV series are running halfway around the world from our operator to an operator in a warm country. They run along special network, wrapped in GTP protocol. And all negotiations between the operators’ special hardware are conducted using the same GTP.
And then an idea comes: shouldn’t we try to figure out something similar in a laboratory setting? Build your SGSN and GGSN. How can we come to incredible discoveries?
SGSN + GGSN on the knee

After a long search, the following was discovered.
There is software special purpose, which implements some SGSN functions. It looks like a Linux script that can emulate everything necessary procedures(GPRS Attach and PDP Context Activation) and eventually produce a ready-made interface for accessing the Internet, as if we had plugged in a 3G modem. Having learned about this, we immediately rushed to look for a device ready to shoulder the functions of GGSN. It turned out that popular Cisco router 7200 is quite suitable.
After some manipulations, settings and tests, success awaited us.

The stand easily raised tunnels through which the real Internet was “visible.”
We immediately began to look at what packets were passing between our mighty SGSN and GGSN. Do they look like the real thing? With bated breath we open the dump - and yes! the packages look like real ones.

Similar packets can travel on the GRX network, and they may well be overheard by an evil hacker. What will he see there? Let's try to find out.
Security questions
The GTP protocol comes in several types: GTP-U is used for direct packaging and transmission of user data, GTP-C for session management (it is used to carry out the PDP Context Activation procedure and other service procedures); There is also GTP’ (GTP Prime) - it is used to transmit billing information. GTP does not support peer authentication and encryption, it works on top of UDP. What's so interesting about all this? Almost everything here is interesting!
Let's take GTP-U and see what a tunnel with user data looks like. The tunnels are separated by the TEID (Tunnel Endpoint Identifier) parameter.

Upon further study, it turned out that, if desired, the field with TEID can be replaced, and by sending a packet with a substituted tunnel identifier, you can unexpectedly break into someone else’s session.
And here is GTP-C. Having been surprised to discover the absence of any authentication or hints of encryption of the transmitted data, you can try not only listening, but also, excuse me, sending something. For example, “left” requests to establish or terminate a session.
Let's try to outline the vectors of possible attacks in this way and take a closer look at them.

For example, DNS attack flood. The attacker sends a large number of requests for APN permission from our operator. All these packets will bombard the poor operator's DNS, which will not withstand the heat and generally refuse to transfer the GGSN address to anyone, causing global DoS for subscribers.

Or the attacker will start sending personally crafted requests to create a PDP context. GGSN, seeing such pressure, may well think, or even freeze. Which will again lead to denial of service to subscribers.
What if you try sending session break requests instead of creation requests? For example, like this:

An evil hacker, substituting a foreign SGSN address, will send requests to terminate the connection. GGSN, thinking that the subscriber has finished downloading his favorite series and wants to end the Internet session, deletes this tunnel, breaking the connection.
Having sketched a few vectors, let’s turn our gaze to real objects to “touch” it all. Let's type the request “GGSN” in shodan. Here is a snippet of the returned results.

All this looks like real GGSN posted on the Internet.
Or let’s try to write a script that sends GTP-echo requests, and let it circulate on the Internet: maybe someone will respond. And those who respond are:
Sometimes even with open telnet.
The new generation standard, codenamed LTE, still uses the GTP protocol, and therefore all of the above is relevant and will be relevant in the foreseeable future.
That's all for today. See you again!
To use the Internet using mobile phone passed most comfortably, it is important to know a few simple rules and recommendations on how to correctly use wireless (mobile) Internet. The “Safe Mobile Internet” section will help you with this.
what to do:
1) check the remaining traffic;
2) disable automatic application updates in the settings of your smartphone/tablet;
3) turn off data transfer when using Wi-Fi (if, when using Wi-Fi, the signal level decreases or disappears, then the point may be automatically replaced in the smartphone/tablet Wi-Fi access to the Mobile Internet service access point);
4) disable the “Data transfer while roaming” option on your smartphone/tablet if you do not plan to use the Mobile Internet service while roaming;
5) remember that in the settings of a number of smartphones/tablets there are counters for used data, where you can:
- view the amount of traffic consumed on various applications;
- set restrictions on the use of mobile Internet depending on the planned volume (in this case, the amount of data recorded by the phone meter may differ from the data of the operator’s switching equipment).
If you use the services of several Internet providers on your computer, a mistake in choosing a connection can lead to unexpected traffic consumption and the formation of debt.
what to do:
In case of use various options connections on one computer must be monitored network settings computer, operating system, software or remove the modem after completing work with the Mobile Internet service to prevent errors when choosing a connection.
Additional control over the volume of Internet traffic using special functions Modem software. Incorrect termination device operation is the main reason for the loss of statistics and the fact that an entry in the connection log is not generated.
what to do:
Rules for correctly removing a USB modem and shutting down the control program (using the example of Windows XP).
- Before removing the modem, you must close the management program
- Double-click the icon in the taskbar icon area, the interface “ Safe removal devices"
- Select the equipment to be turned off and click “Stop”
- When the "Hardware may be removed" message appears, remove the modem.
description:
RootSmart is malicious application, which, when it gets into a smartphone (especially common on the Android operating system), automatically starts downloading viruses to mobile device. Initially, the application does not contain a virus, but after a while it begins to introduce dangerous code. The download process is often hidden behind standard communication operations on the device. RootSmart can penetrate your smartphone through downloaded applications from unofficial Internet portals, such as those dedicated to the Android OS. After downloading or installing regular application(games, translator, multimedia player, wallpaper collection, etc.) Internet access is provided. After some time, a virus is downloaded, with the help of which SMS sending begins, as well as phone calls on paid numbers without the subscriber's knowledge.
Android.Gongfu is distributed through unofficial software collection sites. The Android.Gongfu malware is distinguished by its ability to install another application on the infected mobile device, which is added to the infected system as a background service. Installed by a virus the service starts automatically without user intervention and collects data about the device, including operating system version, phone model, name mobile operator, IMEI number And phone number user. Subsequently, all this information is “transmitted” to the attackers. In addition, Android.Gongfu can execute commands received from scammers.
what to do:
Be careful when downloading and installing apps on your smartphone. Carefully study the conditions for downloading and operating applications. Pay attention to user reviews about the operation of a particular application. Use applications downloaded only from official “markets”. Also don't forget about antivirus protection your his mobile gadget!
description:
For Internet users, blockers are another pressing and serious problem. They are programs that partially or completely paralyze the operation of a computer system or cause damage to its operating system.
Encryption programs also cause significant damage to your computer, requiring payment for unzipping files by sending SMS. Such pest programs are installed when clicking on pop-up windows, when downloading content of dubious origin (videos, music, games, etc.), as well as when launching unknown files.
what to do:
description:
what to do:
To provide normal operation on the Internet and timely monitoring of Internet traffic, we recommend that you:
install up-to-date antivirus software software, and special programs, which help to record and control Internet traffic
use information caching, that is, saving already visited pages in the computer memory or viewing them offline
use download managers to download and save required files from the Internet
discard the function automatic update software for your computer, laptop, smartphone
description:
WI-FI– technology for transmitting data using a wireless connection.
How easy and correct to use:
1. Install an antivirus on your laptop, netbook or smartphone to protect against virus invasions
2. Do not connect to networks with suspicious names. Be careful when choosing connection points, choose the names of networks that are consonant with the place where you want to connect (name of a cafe, building, gallery).
3. Use a secure connection that requires you to enter a password. If you are in a cafe, the service staff will tell you both the name of the network and the required password and connection conditions
4. Use encrypted data storage to help protect your personal files. So your photos, documents, videos will be safe from hacking and unauthorized entry
5. Properly turn off WI-FI after finishing work
6. And finally: do not leave your smartphone, laptop or netbook unattended
With the development of mobile networks, the mobile Internet is also developing. Everyone is used to the regular Internet: twisted pair, Ethernet, TCP/IP. What does the mobile internet hide? Let's try to find out! In our study, we will touch on the general principles of the mobile Internet, take a closer look at the GPRS Tunneling Protocol, talk about the GRX network and discuss some practical approaches to the security of a mobile packet network.
How do each of us connect to the mobile Internet? In principle, you only need to know three parameters: APN, login and password. APN is an access point through which a subscriber can connect to the service he needs (WAP, MMS, Internet); for our operators it usually looks like internet.
Now that we know the necessary parameters, we can connect to the mobile Internet! How does this mysterious procedure happen? It happens in two stages:
- GPRS Attach
- PDP Context Activation.
Let's take a closer look at each of them.
GPRS Attach
In the GPRS Attach procedure, the phone begins to “communicate” with the operator’s packet network. Authentication and authorization of user equipment occurs according to the following parameters:
IMSI (International Mobile Subscriber Identity, individual subscriber number) - for identification
- subscriber;
- keys stored on the SIM card - for subscriber authentication;
- checking the services available to the subscriber (Internet, MMS, WAP) based on entries in the subscriber database
.
IMEI (International Mobile Equipment Identity) can also be checked. This identifier can be used to check against lists of stolen equipment, and if a specific IMEI is on the list of stolen equipment, then access to the network may be denied, or even reported “where it should be” :)
After successful completion of the GPRS Attach procedure, the PDP (Packet Data Protocol) Context Activation procedure begins. To understand this procedure, let's digress and define some concepts.
SGSN (Serving GPRS Support Node, GPRS subscriber service node) is a device that implements the basic functions of processing packet data in a mobile network.
GGSN (GPRS Gateway Service Node, GPRS gateway node) is a device that provides data transfer from the operator’s network to external networks (for example, to the Internet). In fact, it can be a regular router with support for some specific functions.
GTP (GPRS Tunneling Protocol) is a protocol stack used in GPRS, UMTS and LTE networks.
So, PDP Context Activation (the diagram is greatly simplified).
What happens when this scheme is implemented?
- The phone sends a context activation request to the SGSN, which contains, among other things, the username, password and APN.
- The SGSN, having received the APN, attempts to resolve it on the internal DNS server. The server resolves the provided APN and returns the address of the GGSN responsible for this APN.
- The SGSN sends a request to create a PDP context to this address.
- GGSN checks the provided login and password on the RADIUS server.
- Then it gets the IP address for our phone.
- And all the information necessary to activate the PDP context is sent back to the SGSN.
- The SGSN completes the activation procedure by sending the data necessary to establish the connection to the phone.
Essentially, the PDP Context Activation procedure is the creation of a tunnel between the phone and the gateway in the operator's network. And now we can go to our favorite sites and read mail.
Roaming
The question immediately arises: how does this all work in roaming? It turns out that there is a special network: GRX (Global Roaming Exchange) - a network for exchanging packet data among roaming subscribers of mobile networks. All our traffic “runs” through it. Something like this:

- Having successfully arrived in warmer climes, we decided to download our favorite series. We turned on the phone and started connecting to the Internet (send login, password, APN).
- The foreign SGSN tries to resolve the APN we provide on its DNS server.
- The DNS server, not finding such records, turns to the root DNS server, which is located in the GRX network.
- The root DNS server forwards the request to a DNS server on our home carrier's network.
- He, in turn, responds to him with the address of our GGSN.
- The root DNS reports this address to the DNS server of the foreign operator.
- Which in turn communicates this address to the foreign SGSN.
- The SGSN, knowing the GGSN address, sends it a request to activate the PDP context.
- GGSN, if all conditions are met (there is money in the account, the correct login and password are indicated, etc.), sends a confirmation, SGSN accepts it and sends confirmation to our phone for Internet access.
What do we see? We see that packages with our favorite TV series are running halfway around the world from our operator to an operator in a warm country. They run over a special network, wrapped in the GTP protocol. And all negotiations between the operators’ special hardware are conducted using the same GTP.
And then an idea comes: shouldn’t we try to figure out something similar in a laboratory setting? Build your SGSN and GGSN. How can we come to incredible discoveries?
SGSN + GGSN on the knee

After a long search, the following was discovered.
There is special purpose software that implements some of the SGSN functions. It looks like a Linux script that can emulate all the necessary procedures (GPRS Attach and PDP Context Activation) and ultimately produce a ready-made interface for accessing the Internet, as if we had plugged in a 3G modem. Having learned about this, we immediately rushed to look for a device ready to shoulder the functions of GGSN. It turned out that the popular Cisco 7200 router was quite suitable.
After some manipulations, settings and tests, success awaited us.

The stand easily raised tunnels through which the real Internet was “visible.” We immediately began to look at what packets were passing between our mighty SGSN and GGSN. Do they look like the real thing? With bated breath we open the dump - and yes! the packages look like real ones.

Similar packets can travel on the GRX network, and they may well be overheard by an evil hacker. What will he see there? Let's try to find out.
Security questions
The GTP protocol comes in several types: GTP-U is used for direct packaging and transmission of user data, GTP-C for session management (it is used to carry out the PDP Context Activation procedure and other service procedures); There is also GTP’ (GTP Prime) - it is used to transmit billing information. GTP does not support peer authentication and encryption, it works on top of UDP. What's so interesting about all this? Almost everything here is interesting!
Let's take GTP-U and see what a tunnel with user data looks like. The tunnels are separated by the TEID (Tunnel Endpoint Identifier) parameter.

Upon further study, it turned out that, if desired, the field with TEID can be replaced, and by sending a packet with a substituted tunnel identifier, you can unexpectedly break into someone else’s session.
And here is GTP-C. Having been surprised to discover the absence of any authentication or hints of encryption of the transmitted data, you can try not only listening, but also, excuse me, sending something. For example, “left” requests to establish or terminate a session.
Let's try to outline the vectors of possible attacks in this way and take a closer look at them.

Here, for example, is a DNS flood attack. The attacker sends a large number of requests to resolve our operator's APN. All these packets will bombard the poor operator's DNS, which will not withstand the heat and generally refuse to transfer the GGSN address to anyone, causing global DoS for subscribers.

Or the attacker will start sending personally crafted requests to create a PDP context. GGSN, seeing such pressure, may well think, or even freeze. Which will again lead to denial of service to subscribers.
What if you try sending session break requests instead of creation requests?
For example, like this:

An evil hacker, substituting a foreign SGSN address, will send requests to terminate the connection. GGSN, thinking that the subscriber has finished downloading his favorite series and wants to end the Internet session, deletes this tunnel, breaking the connection.
Having sketched a few vectors, let’s turn our gaze to real objects to “touch” it all. Let's type the request “GGSN” in shodan. Here is a snippet of the returned results.

All this looks like real GGSN posted on the Internet.
Or let's try to write a script that sends GTP-echo requests, and let it go around the Internet: maybe someone will respond. And those who respond are:
Sometimes even with open telnet.
The new generation standard, codenamed LTE, still uses the GTP protocol, and therefore all of the above is relevant and will be relevant in the foreseeable future.
That's all for today. See you again!
I would like to express my gratitude to the Security Analysis Department network devices Positive Technologies for assistance in preparing the material.
Today, the mobile Internet is becoming increasingly popular and in its prevalence will soon overtake the traditional wired analogue. Data transfer rates are growing, communication technologies are developing and any modern gadget takes advantage of opportunities mobile connection in full. Mobile Internet - great helper business man on trips and business trips. A smartphone always travels with its owner and operational solution tasks such as working with by email, creating and editing documents, as well as surfing the web using a mobile device, are no longer something special.
However, the possibility wireless access to the World Wide Web from almost anywhere globe poses a number of specific dangers. Malicious programs, which are safely filtered by antiviruses on computers, fully manifest themselves on the mobile Internet, threatening the security of your device. Don't forget that balance personal account subscriber information is of great interest to unscrupulous content providers and various types of scammers.
Experts agree that the main threats in the field mobile fraud in 2012 will be associated with mobile banking. Mobile platforms do not have the same high level of security as Internet sites or ATMs, and are therefore more vulnerable to fraudsters. Attackers will try in every possible way to penetrate the browser and mobile applications user and take possession of his personal data in order to gain control over the account. In the near future, we should expect increased interest from scammers in p2p payments, which, according to experts, should soon become popular in our country.
In pursuit of personal data of smartphone owners, criminals often resort to social engineering methods - controlling user actions without help. technical means, manipulating exclusively human weaknesses. Thus, there is a well-known fraudulent scheme, which can roughly be called “a call from a technical support employee.” The caller introduces himself as a technical support employee mobile operator and informs about the need to reprogram the phone to new parameters in connection with the technical work. The owner of the device is asked to enter a combination of letters and numbers, after which funds are withdrawn from his account.
You can fall for scammers when visiting certain resources. Thus, while surfing the web, you can often come across offers to “update” software. Such notifications can be received, for example, when redirecting from other, safe sites. After interacting with such an information banner, a malicious program is downloaded, which automatically sends SMS messages to paid short numbers. With a problem automatic mailing SMS messages are also encountered by users who install software from numerous sites offering cracked versions of paid programs.
There is also such a scheme: the device receives a notification that for given number an MMS message has arrived. When you click on the link provided in the information letter, a malicious program is downloaded and SMS messages are subsequently sent to paid numbers. IN Lately For automatic download It is enough for malware to simply open such a message, especially if you have the option to automatically follow the received links enabled.
Particular vigilance should be exercised when using paid services, which provide various Internet resources. Sometimes they contain incorrect information and underestimate the cost of the content offered. Expecting to download the content as written large print amount, you may not pay attention to the subtle note at the bottom that the price is indicated for one day. In this case, you pay for a subscription for several months at once. Also, the site may not indicate the number of SMS messages that must be sent to make a purchase.
Particular attention should be paid to viruses that enter smartphones via MMS, the Internet and installed applications. After infection, the device begins to independently send SMS messages to paid short numbers of scammers. SMS sending or MMS without the user's knowledge can be carried out by Java applications, as a result of which numbers from the victim's contact list are also at risk, to which messages are also sent for further transmission of the virus. Indicators that you have become a victim of malware may include an unusually fast discharge of your battery and loss of funds from your personal account. You can also get a malicious Java application on your device by downloading and installing virus-infected games.
But you can lose funds not only due to the fault of scammers, but also due to your own negligence, for example as a result incorrect setting multimedia device. Any gadget, be it a smartphone or a laptop, increases its own Internet traffic consumption every year. For a mobile device, this may include various synchronization processes, downloading maps and other relevant information (for example, information about traffic jams, traffic incidents) when using a navigator. By default, the settings of such a device include many options related to data exchange functions. When working with a laptop, the Internet connection is used to automatically download various types of updates: both the OS itself and the installed software.
Operation of the device with default settings, without restrictions on Internet traffic consumption, in home region the user may be acceptable both for him and for the state of his subscriber account. This is explained low prices on traffic and the availability of various preferential packages. In roaming, when the price for 1 MB of mobile Internet increases sharply, the situation takes on a different character. And any regular update, constant loading of information, as well as other actions habitual for the subscriber can have a detrimental effect on the balance of his account.
Despite warnings about the high cost of using mobile Internet while traveling, as well as a large number of stories with our compatriots who, after downloading several episodes of their favorite TV series, ended up owing several million rubles to telecom operators, such cases still occur. Fortunately, in 2012 the situation with prices for mobile Internet in roaming is very different from what it was in the services market cellular communication a few years ago. Today operators big three offer special packages traffic and tariffs for trips and trips, which are designed to optimize the costs of mobile communications and the Internet outside home zone. Nevertheless, buying a local SIM card is still justified in some cases.
When installing any applications on your smartphone, it is recommended to read very carefully user agreements, and also view the list of options and processes that the program requests during installation. It would also be a good idea to read the comments on downloaded applications, since sometimes the information contained in the reviews of other consumers can help avoid adverse consequences installations. For those who receive applications only from official store Google Play Market (former Android Market), it is recommended to disable the ability to install applications from unreliable sources in the options of your smartphone.
If speak about Google Play, then, unlike Apple Store, this is the official repository of applications for the operating system Android systems until recently, it contained a large number of viruses and other programs that could damage devices. Later, moderation was strengthened, and downloaded software is now scanned by an antivirus. Thanks to these measures, a large number of malware and counterfeit programs were removed. In addition to disabling the above options in the smartphone settings, anti-virus protection tools also help combat such programs.
Another problem that owners of smartphones, laptops and tablets may encounter is the unintentional purchase of an application. The likelihood of such a situation is quite high, given the wide selection of programs presented in the Google Play Market and Apple Store. In this case, there is a procedure for returning spent Money. The time interval within which you can cancel a purchase is 24 hours for App Store and 15 minutes for Google Play ( Android Market).
Which mobile Internet is the most profitable? Understanding this issue is not as easy as it seems. After all, there are a lot of cellular operators in every city. And everywhere they offer their own conditions for connecting to the Internet. There are many factors to take into account. For example, how actively do you plan to use the Internet for “forays”. Sometimes it turns out that the most advantageous offer is the one with the least Internet traffic. What do they think about this issue subscribers? How do they connect their mobile Internet? Which operator performed best in this area?
Eternal competition
It is difficult to find an answer to all this. After all, everyone has their own requirements regarding the operation of the mobile virtual web. Therefore, the subscriber’s choice will depend on the requirements put forward.
Have you wondered which mobile Internet is the most profitable? Then pay attention to the most popular companies offering services mobile communications. They constantly compete with each other. This:
- "Megphone";
- "Beeline";
- "MTS";
- "Tele 2".
It is among these companies that a leader must be chosen. Be sure to answer a few questions for yourself:
- How often will you use the Internet?
- What do you do most often online?
- How active of a user do you consider yourself?
- What amount and traffic do you expect?
All this will help you make your choice. As practice shows, the ratio of price and offered Internet traffic plays a big role. But the quality of work of a particular operator also affects the choice of subscribers.

"Megaphone"
Which mobile Internet is the most profitable? Perhaps some people note that Megafon offers very good conditions. But this company is not very famous for its stability. Most often, people indicate that while working with the network they experience various glitches and problems.
In addition, Megafon does not allow you to simply use the Internet throughout Russia. In order to have this opportunity, you will have to additionally activate the “Internet in Russia” service. Connection will cost 30 rubles, and subscription fee will range from 2 to 10.
In principle, not the worst option. "Megafon" is not very suitable active people(most operator offers). You can connect to one of the available mobile Internet packages (from XS to XL). Each offer has its own characteristics. Completely free Internet (mobile unlimited) is provided in the Internet XL package, which costs about 1,290 rubles per month. Traffic here is not limited, but the cost is quite high. Only very suitable active users.

"Beeline"
Are you wondering which mobile Internet is the most profitable? Many people offer Beeline. The company has long been famous for its reliability and quality of service. It is noted that communication services are provided without constant interruptions. But some tariff plans are overpriced. This can be off-putting.
Great attention should be paid to access speed World Wide Web. In large cities it will be very small. It is enough to work on the phone, but as soon as you insert the SIM card into the USB modem, you will feel that you will not be able to comfortably use the network services. But in small towns with little load on the network, you can really only rejoice at the speed of the Internet.
The “EVERYTHING!” line is extremely popular. from Beeline. Free Internet(mobile) is provided in fairly large volumes. For example, “ALL for 300” offers 3 GB of Internet. And additionally free minutes conversations with Beeline subscribers, as well as 100 SMS messages. Suitable for not very active users tariff plan"Vseshechka." 100 rubles per month - and 100 MB of Internet traffic. After spending the limit, you will pay a ruble for every 1 MB of information. Beeline has profitable offer, but most often they are used exclusively for mobile devices. The USB modem does not work very well with this operator.

"MTS"
MTS mobile internet is extremely popular. This operator offers quite profitable terms and good network performance. With its shortcomings - the company often experiences overload. And in forest areas it is not comfortable to work on the Internet with a USB modem. After all, the connection will be at low speed.
At prices, MTS offers the most humane offers. If we talk about a mobile phone, here you can use the tariff " Super BIT"for 150-250 rubles (depending on the region of your residence) and work comfortably throughout Russia with the Internet. A quota of 100 MB is given per day. As soon as you download more information than the limit, the network speed drops to 64 Kb/sec. Also It is possible to connect yourself to "BIT" for 150 rubles to work within your home region.
But MTS has completely different packages for USB modems. This mobile Internet pleases with its cost and speed. But, as already mentioned, either communication is often interrupted due to overload, or the network is very slow. This is how many people stop at this very proposal.
"Tele 2"
But in Moscow the best operator recognized by Tele2. This company appeared not as long ago as everyone else, but she has already won the hearts of many. Favorable rates and stable work networks are what the operator is famous for.
The "Internet for mobile" offer is suitable for mobile phones. It has a subscription fee, which is about 5.5 rubles per day. At the same time, the amount of data you download is not limited.

But for a USB modem there are completely different proposals. Tele2 offers a variety of tariffs. For example, "Internet Suitcase". With it you get 45 GB of Internet traffic for 400-500 rubles (the cost depends on your region of residence). Once the limit is reached, access to the network is terminated.
A true leader
So which operator is the most profitable for connecting to the Internet? It's hard to decide. It is noted that MTS and Tele2 are best suited for this moment for those who don't want to overpay.
How to set up mobile Internet? All operators now allow us not to think about this issue. You just need to save the settings that come to your mobile device. Or insert the SIM card into the USB modem. Everything is very easy and simple!