We are learning ways to unlock Windows XP. Final work and actions in case of failure
Surely, every fourth user of a personal computer has encountered various scams on the Internet. One type of deception is a banner that blocks the operation of Windows and requires you to send an SMS to paid number or requires cryptocurrency. Essentially it's just a virus.
To fight banner ransomware, you need to understand what it is and how it penetrates your computer. Typically a banner looks like this:

But there may be all sorts of other variations, but the essence is the same - scammers want to make money from you.
Ways a virus gets into a computer
The first variant of “infection” is pirated apps, utilities, games. Of course, Internet users are accustomed to getting most of what they want online “for free,” but when downloading pirated software, games, various activators, and other things from suspicious sites, we risk becoming infected with viruses. In this situation it usually helps.
Windows may be blocked due to a downloaded file with the extension " .exe" This does not mean that you should refuse to download files with this extension. Just remember that " .exe"may only apply to games and programs. If you download a video, song, document or picture, and its name has “.exe” at the end, then the chance of a ransomware banner appearing increases sharply to 99.999%!
There is another tricky move with the supposed need for updating Flash player a or browser. It may happen that you will work on the Internet, move from page to page, and one day you will find an inscription that “your Flash player is out of date, please update.” If you click on this banner and it does not lead you to the official adobe.com website, then it is 100% a virus. Therefore, check before clicking the “Update” button. The best option such messages will be ignored altogether.
And lastly, outdated Windows updates weaken the system's security. To keep your computer protected, try to install updates on time. This feature can be configured in “Control Panels -> Windows Update” to automatic mode so as not to be distracted.
How to unlock Windows 7/8/10
One of simple options remove the ransomware banner - this is . It helps 100%, but reinstalling Windows makes sense when you don’t have important data on the C drive that you didn’t have time to save. When you reinstall the system, all files will be deleted from system disk. Therefore, if you do not want to reinstall software and games, then you can use other methods.
After treatment and successful launch of the system without the ransomware banner, you need to carry out additional actions, otherwise the virus may resurface, or there will simply be some problems in the operation of the system. All this is at the end of the article. All information has been verified by me personally! So, let's begin!
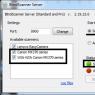
Kaspersky Rescue Disk + WindowsUnlocker will help us!
We will use a specially developed operating system. The whole difficulty is that you need to download the image on your work computer and or (scroll through the articles, it’s there).
When this is ready, you need. At the moment of startup, a small message will appear, such as “Press any key to boot from CD or DVD.” Here you need to press any button on the keyboard, otherwise the infected Windows will start.
When loading, press any button, then select the language - “Russian”, accept license agreement using the “1” button and use the launch mode – “Graphic”. After starting the Kaspersky operating system, we do not pay attention to the automatically launched scanner, but go to the “Start” menu and launch “Terminal”

A black window will open, where we write the command:
windowsunlocker
A small menu will open:

Select “Unlock Windows” with the “1” button. The program itself will check and correct everything. Now you can close the window and check the entire computer with the scanner already running. In the window, put a checkmark on the disk with Windows OS and click “Run object scan”

We wait for the check to finish (it can take a long time) and finally reboot.
If you have a laptop without a mouse and the touchpad does not work, then I suggest using the text mode of the Kaspersky disk. In this case, after starting the operating system, you must first close the menu that opens with the “F10” button, then enter command line still the same command: windowsunlocker
Unlocking in safe mode, without special images
Today, viruses like Winlocker have become smarter and block Windows from loading. safe mode, so most likely you won’t succeed, but if there is no image, then try. Viruses are different and can work for everyone different ways, but the principle is the same.
Reboot the computer. During boot, you need to press the F8 key until the menu appears additional options start Windows. We need to use the down arrows to select from the list an item called "Safe Mode with Command Line Support".
This is where we need to go and select the desired line:

Next, if everything goes well, the computer will boot and we will see the desktop. Great! But this does not mean that everything is working now. If you don't remove the virus and just reboot into normal mode, then the banner will pop up again!
We are treated using Windows
You need to restore the system when the blocker banner did not yet exist. Read the article carefully and do everything that is written there. There is a video below the article.
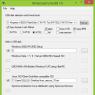
If it doesn’t help, then press the “Win + R” buttons and write the command in the window to open the registry editor:
regedit
If instead of the desktop a black command line is launched, then simply enter the command “regedit” and press “Enter”. We have to check some sections of the registry for the presence of viruses, or, to be more precise, malicious code. To start this operation, go to this path:
HKEY_LOCAL_MACHINE\Software\Microsoft\WinNT\CurrentVersion\Winlogon
Now we check the following values in order:
- Shell – “explorer.exe” must be written here, there should be no other options
- Userinit – here the text should be “C:\Windows\system32\userinit.exe,”
If the OS is installed on a different drive other than C:, then the letter there will be different. in order to change incorrect values, press right click mouse over the line you want to edit and select “edit”:

Then we check:
HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon
There should be no Shell and Userinit keys here at all; if there are, delete them.
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
And also be sure to:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
If you are not sure whether you need to delete the key, you can simply add a “1” to the parameter first. The path will be incorrect, and the program will simply not start. Then you can return it to how it was.
Now you need to run the built-in system cleaning utility, we do it in the same way as we launched the “regedit” registry editor, but we write:
cleanmgr
Select the disk with operating system(by default C:) and after scanning, check all the boxes except “Files backup copy update package"

And click “OK”. With this action, we may have disabled the autorun of the virus, and then we need to clean up traces of its presence in the system, and read about this at the end of the article.
AVZ utility
The idea is that in safe mode we will launch the known antivirus utility AVZ. In addition to scanning for viruses, the program has just a lot of functions for fixing system problems. This method repeats the steps to close holes in the system after the virus has worked, incl. To get acquainted with it, move on to the next point.
Fixing problems after removing ransomware
Congratulations! If you are reading this, it means the system started without a banner. Now they need to check the entire system. If you used life-saving disk Kaspersky and checked there, then you can skip this point.
There may also be one more problem associated with the activities of the villain - the virus can encrypt your files. And even after completely deleting it, you simply will not be able to use your files. To decrypt them you need to use programs from the Kaspersky website: XoristDecryptor and RectorDecryptor. There are also instructions for use there.
But that's not all, because... Winlocker has most likely played a dirty trick on the system, and various glitches and problems will be observed. For example, the Registry Editor and Task Manager will not start. To treat the system we will use the AVZ program.
When booting from using Google Chrome may have a problem because... This browser considers the program malicious and does not allow you to download it! This question has already been raised on the official Google forum, and at the time of writing this article everything it's already normal.
To still download the archive with the program, you need to go to “Downloads” and click “Download” malicious file“Yes, I understand that this looks a little stupid, but apparently Chrome believes that the program can harm the average user. And this is true, if you poke it anywhere! Therefore, we strictly follow the instructions!
We unpack the archive with the program, write it to external media and run it on the infected computer. Let's go to the menu "File -> System Restore", check the boxes as in the picture and perform the operations:

Now we go along the following path: "File -> Troubleshooting Wizard", then go to « System problems-> All problems" and click on the “Start” button. The program will scan the system, and then in the window that appears, check all the boxes except “Disable operating system updates in automatic mode” and those that begin with the phrase “Autostart is allowed from...”.

Click on the “Fix noted problems” button. After successful completion, go to: “Browser settings and tweaks -> All problems”, here we check all the boxes and click on the “Fix marked problems” button in the same way.
We do the same with “Privacy”, but here do not check the boxes that are responsible for cleaning bookmarks in browsers and whatever else you think is necessary. We complete the check in the “System Cleaning” and “Adware/Toolbar/Browser Hijacker Removal” sections.
Finally, close the window without leaving the AVZ. In the program we find “Tools -> Explorer Extension Editor” and uncheck those items that are marked in black. Now let's move on to: “Service -> Extension Manager Internet Explorer» and completely erase all the lines in the window that appears.
I already said above that this section of the article is also one of the ways Windows treatment from a ransomware banner. So, in this case, you need to download the program on your work computer and then write it to a flash drive or disk. We carry out all actions in a safe mode. But there is another option to launch AVZ, even if safe mode is not working. You need to start from the same menu when the system boots, in the “Troubleshoot your computer” mode

If you have it installed, it will be displayed at the very top of the menu. If it’s not there, then try starting Windows until the banner appears and unplugging the computer. Then turn it on - it may be offered new mode launch.
Running from the Windows installation disc
Another the right way- this is to boot from any installation Windows disk 7-10 and select there not “Install”, but "System Restore". When the troubleshooter is running:
- You need to select “Command Line” there
- In the black window that appears, write: “notepad”, i.e. launch a regular notepad. We will use it as a mini conductor
- Go to the menu “File -> Open”, select the file type “All files”
- Next, find the folder with the AVZ program, right-click on the file to be launched “avz.exe” and launch the utility using the “Open” menu item (not the “Select” item!).
If all else fails
Refers to cases when, for some reason, you cannot boot from a flash drive with a recorded Kaspersky image or the AVZ program. All you have to do is get it out of your computer HDD and connect it with a second disk to your work computer. Then boot from an UNINFECTED hard drive and scan YOUR drive with a Kaspersky scanner.
Never send SMS messages that scammers ask for. Whatever the text, do not send messages! Try to avoid suspicious sites and files, and generally read. Follow the instructions, and then your computer will be safe. And don’t forget about antivirus and regular operating system updates!
Here is a video where you can see everything with an example. The playlist consists of three lessons:
PS: which method helped you? Write about it in the comments below.
Just like today people just don’t try to earn money, and even more, forgetting the humanity that the Lord put into us. It's amazing how much people lose by deceiving and stealing from others. After all, the Law of our world, which says: “Whatever a man sows, that he will also reap” has not yet been canceled. And after some time the questions arise: “Why?”
In this article, dear readers, I will tell you about one of fraudulent activities, aimed at picking your pockets - when your computer is attacked by a virus released by “smart” people that blocks the Windows OS, and it doesn’t matter what version of your operating system you have - XP, 7, 8, 10 or others. Surely you know what I mean, don’t you, at least I think that many of you have encountered a similar problem? Yes, yes, I say about the ransomware banner, which appears immediately after turning on the computer and blocks Windows. This banner may say that you watched some prohibited video, and now you need to urgently send someone money, for example through Webmoney, and receive an SMS in return with an operating system unlock code.

Don’t even think about paying anyone anything, because... They will not send you any SMS with an unlock code. Let the Lord deal better with these attackers, and in the meantime I will try to help you unlock your computer.
How does a ransomware banner get onto a computer?
1. The Banner Ransomware virus can get onto your computer along with free programs or games downloaded from dubious sources.
2. If you download photos, music, videos, etc. from the Internet, and these files have the extension .exe (file name.exe), instead of the corresponding .jpg, .mp3, .avi, .mkv (file name .jpg).
3. If on some sites you see a banner that says that you need to update or reinstall something, and by clicking on which you go not to the official sites of your programs, but to their clones.
4. If there is no antivirus installed on your computer/laptop, then the virus can enter your computer simply from the pages of various sites.

Unlock Windows, i.e. You can remove the ransomware banner that is blocking your computer in the following ways:
1. Reinstall Windows.
2. Clean the Windows registry, i.e. remove the banner from the system startup.
3. Using a boot disk with special anti-virus software (programs) to remove viruses from the system.
In today’s post we will talk about the second method – removing the ransomware banner from the startup of the operating system.
Method No. 1: How to unlock Windows by cleaning the system registry
No matter how complicated it may sound, it's actually simple. Just follow the instructions below and be careful.
1. Enter safe mode Windows operation. To do this, after turning on the PC, while loading the operating system, press the key "F8". A black screen should appear allowing you to select system boot options. Choose "Safe mode".

2. When Windows boots, press the keyboard shortcut "Win+R". Or "Start - Run".
3. In the window that appears, enter: regedit

Important! If the ransomware banner also appears in “Safe Mode,” then restart the PC again and through “F8”, select “Safe Mode with Command Line Support” from the menu. When the PC boots and a black screen with a blinking cursor appears, also type “regedit” and press “Enter”. The same window with the registry will appear.
4. Go to the address: HKEY_LOCAL_MACHINE\Software\Microsoft\WinNT\CurrentVersion\Winlogon, and check that the following values have the following settings:
Shell– on the contrary there should be only “explorer.exe”.
Userinit– on the contrary there should be only “C:\Windows\system32\userinit.exe,”. If Windows is not installed on the C: drive, then the letter here will be different.

If the values are different, then correct it so that it turns out as I wrote above. To do this, click right key to the line where you want to change the value and select "Change".
5. Go to the address: HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon. Make sure there are no “Shell” and “Userinit” entries here. If there are, delete them.
6. We check the following addresses for the presence of suspicious records, such as - fgkthsinlr.exe that need to be removed:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
If you are not sure that the entry you found is a virus, then right-click on it and select “Edit”. Set the value to “1”. This way, you will disable this recording, and if something goes wrong, you can fix it.
7. Reboot the computer and rejoice! Windows should already be unlocked.
Method No. 2: How to unlock Windows using utilities (antivirus software) 
If it was difficult for you to figure out how to unlock your computer by cleaning the system Windows registry, then you can try using special anti-virus utilities (programs), with which you can do this in just a few clicks.
Windows unlock programs
— AntiWinLocker LiveCD http://www.antiwinlocker.ru/download.html
— Kaspersky Rescue Disk
: You can download from this link: http://sms.kaspersky.ru/
— Dr.Web LiveDisk http://www.freedrweb.com/livedisk/
- utility AVZ. You can download from this link: http://www.z-oleg.com/secur/avz/download.php
Basically, the procedure for unlocking a computer using utilities comes down to recording their images on a flash drive ( USB drive), enable the computer to boot from USB, and in the pop-up windows just click “Start”, “Anti SMS”, “Clear”, etc.
I will write more about these programs later, but that’s all for today. If something doesn’t work out for you, write in the comments, we’ll try to figure it out together.
If you run once unknown program, your computer stops responding to commands, and the desktop takes on the characteristic appearance:



This means that you have become another victim of Trojan.WinLock, or simply a ransomware Trojan that forces you to pay the attacker a certain amount of money for the opportunity to use your PC. The situation is not uncommon, although the peak of the Windows blocker epidemic has already passed. During the existence of this method of extortion, considerable experience has been accumulated in identifying and “treating” infections of this kind, but, nevertheless, attackers are still improving methods for blocking Windows.
It must be said that despite the threats of data destruction on the PC in case of non-payment of the “fine”, nothing like this ever happens. And with a skillful approach, any blocking can be removed quite quickly without resorting to reinstalling the system. Therefore, when you see the menacing “Computer is blocked” banner on the screen, do not rush to transfer money to the cyber criminal - you will not receive any unlock code.
So that you don't feel helpless in similar situation, we have prepared for you a description of the operating methods of ransomware Trojans and several ways to combat them.
Types of system blocking
We list the methods by which a computer is usually blocked under Windows control XP.
- Modification of the main boot entry(MBR), which, if you remember, occupies the first sector hard drive. In this case, the boot code is overwritten or moved to another location, and instead, almost immediately after turning on the PC, the malicious program takes control. This type of ransomware is called Trojan.MBRlock.
- Locking the desktop by modifying the system registry, or more precisely, its areas responsible for starting Windows and automatically starting applications. In this case, either instead of system files or along with them, a Trojan program is launched.
- Rewriting (patching) files critical for Windows boot. With this blocking method, there is not even a need to modify the registry, because malicious code written into system files will gain control in any case, and it will be much more difficult to detect the blocker. Typically, Userinit.exe, Explorer.exe, LogonUI.exe, Taskmgr.exe, and sometimes some others are targeted.
- There is also a way to block Windows by preventing you from launching any program or performing any actions on your computer other than reading a message with the ransomware’s demands. In this case, you can freely close the message, but you still cannot work on a PC - attempts to do anything will be “prohibited by the administrator.” Windows is blocked through group policies. The Trojan-Ransom.Win32.Krotten ransomware (according to the Kaspersky Lab classification) works on this principle.

In addition to the “pure” types of blocking listed above, there are also more sophisticated ones that combine several methods of autorunning Trojan code. For example, changes in the registry and patching of system files, as well as placing several copies of the Trojan on the hard drive that can restore each other.
The favorite locations for Trojan files in Windows XP are these directories:
C:\Documents and Settings\Current User\Local Settings\Application Data
C:\Documents and Settings\All Users\Local Settings\Application Data
C:\Documents and Settings\Current User\Local Settings\Temporary Internet Files
C:\Documents and Settings\All Users\Local Settings\Temporary Internet Files
C:\Documents and Settings\Current User\Local Settings\Temp
C:\Documents and Settings\All Users\Local Settings\Temp
C:\Windows
C:\Windows\Temp
C:\Windows\System32
C:\Documents and Settings\Current User\Main Menu\Programs\Startup
C:\Documents and Settings\All Users\Main Menu\Programs\Startup
And autorun is usually carried out using entries in the following registry sections:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnceEx
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServices
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
Parameters: Userinit, UIHost, Shell.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\userinit.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\explorer.exe
Debugger parameter
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows
AppInit_DLLs parameter
What to do if Windows XP is locked?
Most blockers work not only in normal mode, but also in safe mode, and in some cases they simply disable the ability to load safe mode by deleting the registry keys responsible for this. Therefore, if your Windows XP is blocked, you will have to solve the problem using alternative bootable media– so-called “live” disks (Live CD) with their own operating system. By booting your computer from such media, you will be able to access hard drive, which turned out to be blocked. Next we will look at how to work with Live CD, but for now we will try more simple ways, which, although not always, help out in many cases.
The easiest method to unlock your computer
This method was discovered by users experimentally. In cases complex blocking it’s unlikely to help, but it’s still worth a try, especially since all the steps will take you no more than 5 minutes.
- When you see the “Windows locked” banner on the screen, restart your computer and go to the BIOS Setup before starting the system. On the first tab “Main” (in Avard BIOS – menu item “Standard CMOS Feature”) translate system date 2 - 3 years forward or backward. To exit and save the settings, press F10 and “Y”.

- Boot Windows, if there is no banner on the desktop, download a free antivirus utility, for example, Kaspersky Virus Removal Tool or Dr.Web CureIt! and perform a scan. Why download these programs if you already have an antivirus? Then, due to the date change, it most likely does not work.
- After removing the Trojan, go to the BIOS settings again and return the previous date. All.
Online services of antivirus companies for unlocking Windows
If previous actions did not help you deal with the “Computer is blocked” banner, you can try to find an unlock code using the online services of antivirus companies. This option helps in 50 - 70% of cases, but it will only be useful to you when you have another PC (phone, tablet, etc.) with Internet access. Below are links and instructions for using these services.
Trojan.WinLosk deactivation service of Kaspersky Lab
- Rewrite the text of the ransomware message that you see on the screen and paste it into the appropriate field.
- In the adjacent field, enter the phone number specified in the message to which you are required to transfer money.
- Click the “Get unlock code” button and try to remove the banner using it.
- After logging into Windows, antivirus scanning PC, since the Trojan blocker file is still on the system and can block it again.
- Enter the phone number or wallet number of the ransomware in the appropriate field and click the “Search for codes” button.
- If nothing is offered, you can try to find a suitable code using appearance banner.
- After unlocking, scan your computer for viruses.
- Enter the text of the message from the “Windows blocked” banner and the phone number indicated there in the appropriate fields.
- Click the “Submit” button and try using the suggested codes.
- Once your computer is unlocked, scan it for viruses.
Automatic PC unlocking tools
If the previous measures did not have any effect and your PC is still blocked, you can remove the banner using specialized programs on boot disks (Live CD). Below are tools that allow you to automatically unlock Windows XP and eliminate Trojan horse.
AntiSMS
Fully automatic utility, which cures all known modifications of ransomware Trojans and restores standard settings system boot. Recommended for novice users inexperienced in PC administration. The program does all its work hidden, but it starts double click via a shortcut on the desktop of the bootable media.

Another boot disk, which can help if your Windows XP suddenly locks up. The utility will automatically find and remove the Trojan program, and also restore corrupted files And system registry. On a commercial basis, AntiWinLocker can also be used to protect Windows from blockers by installing it on your computer.
To remove a banner using this program, you will need a minimum of steps:
- boot from AntiWinLockerLiveCD, accept the license agreement and click the “Start” button;

- select “Automatic start” from the menu;

- agree to the offer to replace files (if any) by marking them in the list and clicking “Run”;

- After finishing the program, start the computer from the hard drive - the lock will be removed.
Another universal tool that can help not only in cases where the computer is locked, but also in any viral infections. Equipped with update function virus databases through the Internet.

To use it, just launch the scanner from your desktop, select the scan areas and click “Start scanning”.

No less easy to use tool than the previous ones. Also allows you to easily solve various virus problems on a PC, including when login to Windows XP was blocked. It has the ability to “smart scan”, useful for searching for unknown malicious objects.

Manually unlocking Windows XP when booting from a Live CD
Now let's consider manual methods removing malicious code that prevents Windows XP from loading. To use them you must be at least experienced user PC, otherwise there may be more problems after trying to remove the banner than there were initially. For the first method of treating a computer using a professional utility Universal Virus Sniffer(uVS) we will need any boot disk based on OS Windows. We will use Alkid Live CD.
Alkid Live CD and uVS
This method can be said to be the most labor-intensive, since all operations will have to be performed manually. However, in extreme situations, when native Windows XP is locked, there is no choice, and we will use what is at hand. So let's get started.
- Download the uVS program on another computer and extract it to a USB flash drive (if there is no other PC, this can also be done on an Alkid Live CD after setting up an Internet connection).
- Connect the flash drive to the locked computer.
- Download Alkid Live CD.
- Run the start.exe file from the uVS directory (which in our case is located at F:uvs).
- in the “Startup Mode” window, click the “Select Windows directory” button and navigate to Windows folder your locked system. Click “OK”.
- Click “Run as current user”.

- After scanning, a list of suspicious files will open in front of you, and here it is in a prominent place - our ransomware Trojan.

- To study details about this file, double-click on it - a window will open where, among other things, the method for autorun will be indicated. In our case, this is the registry key that starts Windows Explorer(explorer.exe).

- Now let's move on to Trojan removal and recovery normal startup Windows. Close the properties window and right-click on the file. Select the “Delete all links along with the file” command in the context menu.

- Next, to restore the modified registry key, from top menu“Advanced” select the “Tweaks” command.

- Click “Reset Winlogon keys to initial state”.

- Close the program and boot your computer from your hard drive. You will no longer see the banner.
Important! If you are on the list of suspicious system file, especially Userinit.exe, LogonUI.exe, Explorer.exe or Taskmgr.exe, it is likely modified and contains blocker code. Such files must be replaced with their clean copies, which are stored in the C:WindowsSystem32dllcache folder.
ERD Commander 5.0
If you have this wonderful Windows XP recovery tool at hand, you can get rid of the “Computer is locked” banner much easier, for example, by using the System Restore function. To access it, boot your PC from the disk ERD Commander version 5.0 and proceed to the next steps.
- Press the “Start” button (analogous to start), select “System Tools” from the menu, and then “System Restore”.

- The familiar system recovery program will launch. Choose the right one control point and click “Next”. After the rollback procedure, boot from your hard drive. The “Windows blocked” banner will no longer annoy you.

Removing malicious code from the MBR
If immediately after turning on the PC, even before Windows XP started loading, the following picture appeared to your eyes:

This means that you have suffered from a ransomware Trojan that has entered the MBR. Not every one of the tools listed here can remove malicious code from there; this requires full-fledged antivirus products, which we will name below. Now let’s spend a couple of minutes on what you shouldn’t do in this case.
The Sure Way to Make Windows XP Unbootable
Many users know the purpose of the fixmbr console command - it is intended to overwrite the first hard sector disk. And, in an amicable way, it should restore the boot code, while simultaneously removing the Trojan sitting there. But it was not there. In the process of rewriting a non-standard MBR (and in the event of a Trojan infection it will be non-standard), the partition table, which is located on the hard drive immediately after the MBR boot code and is part of it, is often damaged.

If we ignore the recovery console warning and run fixmbr, instead of the message that the computer is locked, we will see the following:
which means the partition table is damaged. This means that we will not be able to load the system anymore.
Treating MBR using antivirus utilities
To restore the Master Boot Record correctly and safely, you can use:
- AntiSMS;
- Kaspersky Rescue Disk;
- Dr.Web Live CD;
- LiveCD ESET NOD32.
These tools are more than enough to remove any Windows XP lock, including this one.
How to avoid Windows blocking?
It’s unlikely that anyone would argue that preventing a computer from being infected by ransomware Trojans is much easier than fighting them later. And to prevent your PC from being “accidentally” blocked one day, follow these simple rules:
- install reliable antivirus and do not forget to update its database in a timely manner;
- before launch unknown file don’t be lazy to scan it for security;
- do not follow unknown links sent to you by mail and via instant messengers, even from your contacts;
- install Windows XP updates in a timely manner - this closes many loopholes through which the system is penetrated malware. And then, hopefully, you will never have to see “Windows is blocked” messages again, at least on your own computer.
The long-known Winlock blocker does not sleep, and has been “blackmailing” users for about seven years. To date, the representative of the Trojans has achieved clear success - evolution is evident. Users spend not only time to destroy the virus, but also quite often financial resources. But the good news is that there have already been many ways to help unlock the system without much difficulty. Read on to learn how to unlock Windows 7 yourself and absolutely free, and also pay attention to the possibility of preventing this unpleasant moment.
Where can you “pick up” a Trojan and how does it work?
In fact, any user can download a virus and even run it themselves. The Trojan can be in any picture or video file. If you download a file from an unfamiliar site, pay attention to the extension. Standard extension representative of the Winlock family of Trojans - .exe. When started, the active phase begins immediately windows infections. The user may not initially notice the changes, but the Trojan is immediately registered in startup and then limits the actions that the user can perform. A person can continue to “browse” pages on the Internet when a banner appears on the entire screen and completely blocks the work. It is not possible to close or collapse it. The image may be pornographic in nature, or it may use appeal, menacingly appealing to the law. And in mandatory will be asked to pay a fine or send paid message on specified number. Most likely, the Trojan will offer a fine and threaten any consequences for ignoring it. Of course, after payment you won’t get anything, and, naturally, you shouldn’t do this. First you need to pay attention to the number provided and find out the affiliation mobile operator, then contact his security service. There are times when the operator immediately dictates the unlock password, but it’s not always that simple.
To unlock the system, you need to remove the virus from startup and then delete it. There are several ways to do this.
Find out the unlock code
Some antivirus programs can actually provide a code to unlock Windows. After entering it into the appropriate field, the Trojan is nobly removed, and in the literal sense of the word. But not always, of course. You can find this code on antivirus websites. Everything is simple here - enter the wallet or phone number indicated on the banner, to which you are asked to send an SMS, and you will receive password combinations and further instructions. You can access sites from another PC or phone.
If you still manage to defeat the Trojan in this way, do not turn off your computer after work! Be sure to fully scan your windows for viruses.
We use improvised means
Don’t rush to connect complex utilities and call a wizard. Try another method. You must open the task manager by pressing CTRL, ALT, DEL or CTRL, SHIFT, ESC. If you managed to do this, then the problem is not that big. We are looking in the list active processes turn off this application. Finding it is not difficult - often the Winlock is suspiciously signed, and there is no description of the program at all. If in doubt, simply complete all incomprehensible applications in order until the banner disappears.

If the operation did not go as smoothly as we would like, and the task manager did not deign to please with his presence, we will make another attempt to call it. Use the Run command, which can be launched by pressing Win+R.
The usual location of the blocker is directories temporary files windows and browsers. However, the Trojan can also take care of copies, so a full system scan is still necessary.
Another way to remove a simple Trojan
You can get rid of a Trojan (advertising image, for example) by paying attention to the reaction of some programs. For example, when you notice a banner, open WordPad or notepad, hold down “win” - “r” at the same time and type “notepad”.
A new one will appear in front of you Text Document, enter some characters and turn off the computer using the power button. This action will cause all active tasks to terminate, just like the virus, but your PC will continue to work.
A window remains asking you to save or reject the changes. Now you have gotten rid of the banner in the current session, this makes it possible to thoroughly deal with the virus.
Removing more resistant variants of the Trojan
Some Trojans are more resistant to attempts to destroy it. The virus is persistent and blocks any actions, for example, the task manager does not start or important components in Windows are replaced. In this situation, all you have to do is restart your PC; hold “F8” while turning it on. A window will appear in front of you with suggested options for turning on the system; you need to select the line with . Then write “explorer”, confirm, this action will launch the explorer. Next, enter “regedit” and press “enter” again, you will notice a registry editor that will help you determine where the Trojan is hiding and where it comes from automatic start virus.

Most likely, you will be presented with entire paths to the virus in the roots “shell” and “userinit”. In the root “shell” the Trojan will be located in the line instead of explorer.exe, in “userinit” it will be listed after a comma. Having found the information, export the name of the virus to the clipboard, enter “del” in the command line, press the space bar and right-click to bring up the menu. Paste the selected information and press confirmation (enter). Then you remove one virus after another, and so on until victory.
The next logical action would be to check the registry for remaining viruses, start the search with the name of the Trojan. All suspicious files We’ll immediately liquidate it, then delete all copies of the created files and folders, and empty the trash.
As a precaution, use an antivirus and thoroughly check every loophole in your system. It is possible that the settings have been lost due to virus activity. network connection, you can restore them using the “Windows Sockets API” settings using the “AVZ” program.
Thorough infection of the system

If Windows is seriously infected, it is almost useless to try to fix the problem. A more productive and efficient method is to run clean system and cure the underlying one. There are many options for carrying out this process, but one of the most current methods is to use a program that is based on Gentoo Linux. There are several basic file images that are created either by writing to disk or by creating boot file on a flash drive using the Kaspersky USB Rescue Disc Maker program.
When you turn on the infected PC, hold down the appropriate key to enter the BIOS, most often this button is “F2” or “Del”. In settings, select your file image and save by pressing the "F12" key. Modern versions BIOS give you the opportunity to select a boot device without visiting the main settings. Just press "F11" or "F12". Immediately after the reboot, Kaspersry Rescue Disc will launch. The operation involves automatic or manual treatment of your choice.
Removing a threat using the installation disc
Exists separate group Trojan that infects boot system"MBR", which you can find in the automatic launch slots. In the initial stage of recovery from the virus, it is necessary to recover the initial “MBR” password. For Windows XP this operation is performed using installation disk, by pressing the “R” key, call up the recovery menu and enter “fixmbr” in it, after which we agree using the “Y” button, rebooting. For Windows 7, the same process is performed using BOOTREC.EXE, enter bootrec.exe /Mbr. Thus, you start Windows and have the opportunity to find infected files using an antivirus.
Working with less powerful PCs
On low-end PCs and laptops the process windows recovery It takes a little longer and is more difficult. This is explained by a lack of power and difficulty in checking external drives. An effective solution It may be necessary to remove the infected hard drive and connect it to another, more powerful PC. It is recommended to use boxes with eSATA interface or USB3.0/2.0. To prevent the spread of the virus, it is best to disable automatic starting HDD, this can be done using the AVZ program. It is better to check using another program. Go to the “Troubleshooting Wizard” menu, select "system problems", "All" and click Start. Select an item “HDD autostart allowed” and correct everything noted. Before launching an infected media, you need to make sure that the entire anti-virus database works without failures or gaps; take this point seriously.
If disk partitions are not detected, then perform the following operation: “Start”, “Run”, write and confirm. After this, the partitions of the hard drive should be indicated by letters.

To avoid getting your system infected again, install a good antivirus that will perform regular scans. Basic safety rules include:
- Using a PC with limited rights
- You must use trusted browsers with good security systems
- Turn off Java script of unfamiliar sites
- Get rid of pop-up ads instantly
- Divide the disks into user files and systemic
- Disable autorun of flash drives.
In order to restore your PC in a short period of time, if necessary, it is recommended to use the following utilities: “Symantec Ghost”, “ Acronis True Image", "Paragon Backup and Recovery".
At the present time, with modern development technologies and high data transfer rates, users of personal computers, laptops, tablets and smartphones very often (even with installed antivirus protection) catch some kind of virus. Nowadays, programs that infect a device while blocking access to it with a banner on the desktop are very popular among hackers. How to unlock the computer in this case? How can I regain access to it?
What banners exist?
The most common are the following: Internet access is blocked, Windows is blocked, the rules for using the Internet have been violated, your account has been hacked and now spam is being sent from it, and so on. The computer owner is offered help in solving the problem. For this he is asked to send just one SMS via short number. By doing this, you will lose at least 250-300 rubles. And, accordingly, the banner in almost all cases does not go anywhere.
Basic ways to solve the problem
What to do? How to unlock your computer from a virus and continue to use your device? Exist various ways salvation. The main ones:
- Restoring the operating system.
- Removal virus program from OS startup.
- Application of special unlock codes from Dr.Web and Kaspersky websites.
- Using an antivirus.

It must be remembered that universal method There is no way to unlock your computer from a virus. Each of the above is only suitable for a specific situation. Now let's dwell on this a little.
Solving the problem via the Internet
This option is good for someone who has access to the network or has a connection with someone willing to help. The official websites of Kaspersky and Doctor Web have codes that can unlock your device. If they are not there, we go another way.
Removing the banner from startup
How to unlock your computer this way? This path is very simple. You need to boot your device in safe mode. To do this, press F8 when loading it. A menu with Windows boot options will appear in front of us. Choose the one you need. Then one of two things: the banner has not gone away, or the system will boot without the virus. In the latter case, click "Start" and enter msconfig in the command line. Go to startup, uncheck suspicious items there and reboot the PC.
Outdated unlocking method

If the banner has not disappeared anywhere, then you can try to unlock your computer from the virus using the outdated method, but sometimes effective method. To do this, we reboot it in safe mode, and set the clock forward about a week. This may help, but most likely not for long, since viruses are also updated regularly. System time It is possible to change it in the BIOS. It is also possible to perform a system restore.
Powerful professional way
If all the previous does not help resolve the issue of how to unlock your computer, we will fight the banner using an antivirus. If you can access the desktop in safe mode, then use Removal-tool Kaspersky or Cureit Doctors Web, the most famous of all. If this is not possible, we use LiveCD - a special boot disk that loads the antivirus without any problems and removes the banner. To do this, we write its image onto a flash drive or disc, then onto a computer, after which we scan the system for viruses. This option may be difficult for the average user to use, so it is recommended that you turn to a professional. So we figured out how to unlock your computer.