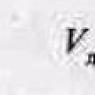How to prevent files from being deleted. Prohibiting the installation of applications using the Group Policy Editor. Using static routes
Video version
Text version
Mobile subscriptions– this is a special type of service that, as a rule, provides content or access to a website for a daily subscription fee of approximately 5 to 50 rubles.
A small lyrical digression. Megafon, in my opinion, is one of the most greedy in terms of money from scammers (from people/companies that organize mobile subscriptions). The fact is that at one time on a separate web resource I helped people find ways to disable subscriptions. There is, of course, a banal option with a personal account, but it was not always suitable. But let’s be honest, I even came across the moy-m-portal mailing list once – “ free access for 5 days, go to Personal Area"and clap... minus 150 rubles. Technical support said that it was my own fault for clicking on the link. God bless you, operator. I wrote a complaint on a special page of Megafon, which is dedicated to scammers - they didn’t call me back, didn’t answer by mail, didn’t return the money.
Well, now to the point - how to ban subscriptions on Megafon in order to protect yourself from unwanted debits from your balance. There are two ways.
Megafon content account
Content account– this is an additional account (balance). When connected, all infotainment services, that is, subscriptions, will be able to withdraw money exclusively from there. If there is no money in the content account, it will not be debited.
We could also talk about this method of protection against subscriptions, but it is unlikely that many subscribers will like it, since it requires going to a Megafon salon and writing an application there to create a content account. This is the only way to connect.
Prohibition of paid content short numbers
But this is what I love. One USSD request and that’s it – no need to go anywhere. This service does not create a separate content account from which subscribers will unsuccessfully try to withdraw money, but simply blocks them. Prohibition of paid content short numbers limits access to paid entertaining SMS,USSD, voice services content providers, as well as to the numbers of the “Mood” service.
You can activate or deactivate the “Banning of paid content short numbers” service using a simple USSD request on your phone: *526# 📞
What to choose?
Megafon's content account protects the main balance from mobile subscriptions. This may come in handy if you really want to use some mobile subscriptions. Well, you never know. If you want to completely protect yourself from mobile subscriptions, then I recommend the second option - Ban paid content short numbers.
It is impossible to imagine the number of sites located in wide open spaces world wide web. Naturally, the topics of information resources are the most diverse, because everything that takes place in real life, is reflected on web pages.
There are issues that are inappropriate, indecent or illegal to discuss, just as there are sites that viewing is undesirable or prohibited:
The forbidden fruit is always sweet, but its consumption leads to disastrous consequences. The restrictions do not always have to be the same for everyone, because the same information may be perceived differently by different visitors. That is why the question of how to block a site for a certain group of users comes up head on.
But decisions to restrict access to information resources are made by people, and their opinions do not always fully coincide with common sense. Therefore, the question of how to access blocked sites is no less pressing. All this will be discussed in this article.
Who should be blocked?
Limitation is a rather relative concept. Access to some resources is blocked only for a certain group of people or certain time. To deal with this, it is necessary to identify categories of people for whom prohibitions can be introduced. It is also worth mentioning those who introduce these restrictions.
- He is his own director. Everyone understands that it is necessary to achieve self-discipline, but few know how. Blocking access to a site whose constant visits interfere with productive activities is a radical, but correct decision. People who learn to say “no” to themselves usually achieve what they set out to achieve;
- Children don't care about everything in the world. Wise parents will worry about how to block unwanted sites for their child. Prohibited topics are an individual choice for everyone. Some people don’t want their child to get involved in online games, while others are against fighting without rules. But, as a rule, the restriction only applies to adult sites with known content;
- IN work time do business. There are, of course, boss animals who demand absolute silence and hands folded on the table. But in most cases, restrictions begin to be introduced after regularly observing the following picture: employees with all their appearance demonstrate hard work, but instead there is intense correspondence or viewing of entertainment sites on the computer;
- To all the inhabitants of this country. There are such information resources, the content of which forces domestic government bodies introduce bans. These blocked sites are not available in Russia, but may be officially allowed in other countries.
The state is on alert
In our country, Roskomnadzor is responsible for online censorship, and weekly updates the list of blocked sites. If a resource is related to one of the following topics, then it has an excellent chance of being among the prohibited.
- Promotion of drug use. The population must be healthy, so the state carefully monitors any attempts to encourage terrible addiction;
- Racism and extremism. If information resource incites hostility and stimulates aggression, he must be included in the register of prohibited persons;
- Pornographic materials in the creation of which minors participated. Children should not take part in the operation of the adult industry;
- Suicides. Materials that develop suicidal tendencies in people with unstable psyches are, of course, included in the list of unacceptable;
- Information published without copyright. At one time, some people took care to legally record their own achievements, and the law should apply everywhere, including on the Internet;
- Topics that are prohibited due to government policy. Intrigues on top level– this is a topic that can hardly be discussed within the framework of this article, so the only thing that can be done is to accept everything as it is.
The list of sites blocked by Roskomnadzor can be viewed by entering the appropriate query in a search engine:

You can also use official resource at: eais.rkn.gov.ru:

Familiarization with the list of prohibited resources will help prevent the use of unwanted phrases on your web pages. When viewing the registry, you should pay attention to why the site’s content is blocked, because very often one of the topics described above is mentioned accidentally or in a figurative sense.
If the owners of the web resource eliminate the misunderstanding, the site is removed from the list of prohibited sites without any consequences. It is important to learn from the mistakes of others, which predecessors made in huge numbers.
How to block access?
As has already become clear, access restrictions are introduced for various quantities of people ( from one to all). That is why various locking mechanisms are used, and some of them are given below.
- Block access to unwanted site(s) on a specific computer. There are many ways to restrict access for one user. You can use the browser's capabilities or slightly edit the contents of the hosts file in the etc folder. How to get there and what to do next will be described in more detail below;
- Blocking unwanted IP addresses on the Internet gateway. Using this method, you can deny access to sites for many users at once;
- Changing proxy server settings. You can prohibit the use of certain words in site names, thus covering a wide range of unwanted resources;
How to block a website on your computer
Let’s imagine that you are terrified of annoying VKontakte, which prevents you from doing really important and useful things. So you decided to cut him out of your life. The impulse is worthy of respect, you just need to know how to act correctly.
If you enter in address bar browser magic vk.com, we will see the usual picture:

In order to block a site on your computer, you need to know how to log in as an administrator. To do this in Windows 7, you need to go to the “Start” menu, right-click on “Computer” and go to “Management”. The following window will open:

Let's move on to " Local users " - "Users" - right-click on "Administrator" and select "Properties":

In the window that opens, uncheck the “ Disable account "and close all windows.
Go to “Start”, look for “ Shutdown" and click " Change user" Having logged in as an administrator, go to drive C, look for the Windows folder there, go to system32, find drivers folder, and in it select the etc directory. We need a hosts file:

Open it in notepad:

In order to block access to a site, enter its domain name and write the following construction in front of it:

Now an attempt to kill time will be met with an obstacle in the form of white screen. You can, of course, go around the rules and set all the settings to the initial state, but here we should hope for all-conquering laziness.
How to access a blocked site
There are people who come up with and establish prohibitions, and there are those who violate these prohibitions. Restrictions are not always fair, and very often users quite reasonably want to be able to access one or another prohibited site.
To open blocked sites, you can file a lawsuit, but if access is required immediately, other methods and means are used. Below are just a few of them.
- Turbo mode. To enable you to view prohibited pages, Opera offers a faster loading mode for pages. This feature is also present in Yandex.Browser;
- Installation of special plugins. For Google users Chrome has a Stealthy plugin, which allows you to connect as if from another country. Available for Firefox similar plugin for those who do not know how to open a blocked site in this browser;
- Proxy servers that mask the real IP address;
- Tor. Using Tor browser it is impossible to determine where the Internet resource is being accessed from.
Thus, it is necessary to block visits to certain sites, as there are inappropriate topics and criminal activities. Access to some Internet resources can be restricted both on one computer and for all users in the country.
A component of security in the operating system is to ensure that deletion of files or directories is prohibited. These measures involve hiding, prohibiting editing, viewing, or adding permissions to process file objects.
Created big number software products, designed to organize the protection of files and folders, but more often they solve the problem of deleting files in a comprehensive manner, making them hidden or denying access.
All directories, files, processes in Windows are created specific user. Creators of Windows We tried to develop such a protection system that each user has a very specific case of rights. This case contains options of a prohibiting or allowing nature for manipulating processes and file objects.
It is possible to implement a ban at the account level. By creating, for example, a directory or file in an administrator account while simultaneously opening access at the guest account level, leaving them with write, read, and move rights. However, more often you need to make a ban at the level of the current (own) account.
We need to contact the system Windows security. This method assumes that the file system of the object location disk is initially NTFS. It provides a mechanism for distributing prohibiting and allowing options for all users. FAT systems cannot offer such distinctions.
Moreover, the restrictions imposed do not concern the object itself, but its location. If its location is changed, then access will resume. You must also understand that prohibitive options have highest priority in comparison with permissive ones, so if selected same settings permission and prohibition, then the rights of prohibition are executed first.
First, let’s prohibit deletion for a specific user.
However, such a restriction will be wider, since it will be necessary to limit full access.

First of all, let's open context menu selected file and find the properties item in it.
In the window that opens, go to the “Security” tab.

In the groups and users field, select the desired user.

Click the “Change” button and, in the window that appears, in the list of group permissions, check the boxes for prohibiting settings.

Now let's save the changes we made.

Let's continue the operation

Now we see that we have checkboxes for the prohibitive options

So, we will set restrictions on full access, which also include a prohibition on deleting the object.

An attempt was made to open an image file from a prohibited location. Now let's try to remove it.

We agree with the warning

However, the following window pops up. Click “Continue”.

The system still does not allow you to delete the object.

We prohibit deleting a large number of objects
The same restriction mechanism can be applied to a large number of objects located in a single directory. In this case, a ban can be imposed on all users of the system. This kind of restriction (for everyone) can be done for a single file. In this case, we will need to add a new user group (“Everyone”). Then, you will need to check the restrictive options boxes.

Go back to the security tab

Click the “Advanced” button to open the advanced settings window.

Then select “Change permissions”:

In this window you need to select “Add”.

In the window for selecting groups and users, write a new category “Everyone” and check the names.

After this procedure, the system will show the placement for which this moment restrictions are met. Next, you just need to click “Ok” and agree to the pop-up warnings.

We agree to continue the operation

As you can see, we have a new group with special rights.

These special rights are also visible here.

Let's try to remove something from this directory.

We agree to move it to the trash.

However, we see a familiar window requiring elevation of rights.

The system thinks a little...

However, it then reports that there is no option to delete the file from this location.

Brief summary
Many created software tools to restrict user access to file system objects. However, Windows has its own built-in tools. File NTFS system allows you to set restrictive settings for the location of a specific user or for all locations at once. Moreover, such restrictions may prohibit full access or only the deletion of one or many directories and files.
The Internet is fraught with a lot of dangers, especially for the fragile minds of the younger generation. But few parents manage to protect their child from harmful information through prohibitions and admonitions. 90% of schoolchildren easily deceive their mother and father and continue to visit non-children’s resources.
Adults also “sin” by using the Internet for inappropriate purposes. Mistakes made by office workers often arise because 50% of the time they are busy not with business, but with social networks.
Only one remedy can radically solve the problem - blocking unwanted resources. Read how to block a website from children and careless adults using eight proven methods.
Method of blocking web resources through Hosts - local database IP addresses and domain names associated with them, designed for the most inexperienced. Since today they even know about Hosts junior schoolchildren, for many it will not be difficult to reset the setting and reduce your efforts to nothing. Therefore, you should take measures to protect it. For example:
- Create an account for the user you are going to block access to unwanted sites with limited rights. Then he will not be able to correct anything in the Hosts file even if he wants to.
- Use tricks to hide blocking records.
The blocking technology itself is very simple:
- Log in to Windows using an administrator account.
- Go to the folder %Windir%\System32\drivers\etc, find a file without an extension with the name “Hosts” and open it using Notepad or a program that replaces it. To avoid problems with saving changes, you can do this: run Windows Notepad(file notepad.exe, located in Windows folder) with administrator rights, through the “File” - “Open” menu, go to Hosts and load it into the program.
- To any place in the file with new line add an entry 127.0.0.1 site, where instead of “site” we write the address of the blocked resource.

- Save the file in its original location. So that the notebook is not attributed to him txt extension, the name “hosts”, we write in quotes, and from the file types we select “all files”.

After this, the site will no longer open in browsers, since the computer will look for it not on the Internet, but on itself.
Tricks that will prevent a user from deleting your entry in Hosts
The first option is to hide the entry itself in the file. It is impossible to make it invisible, but between comments (lines starting with #) and it you can insert 2-3 hundred empty lines. The user, when opening a file, most likely will not pay attention to the scroll bar of the document and will not see your entry, since it will be far down.
The second option is to move Hosts file to another, more secluded place. Decide for yourself where to place it, but to prevent the system from losing it, you will have to make a small edit to the registry. Open in RegEdit editor branch HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters and in the parameter value DataBasePath write down new way to Hosts.

Via DNS
Traffic from a computer connected to the Internet passes through DNS server(which, like hosts, map website names to their IP addresses). In addition to the DNS provided by the provider, you can use others, for example, free public ones.
Some public DNS They have a content filtering system, that is, they do not load sites with certain content onto the computer.
Unfortunately, you can't block resources of your choice using DNS, but if you want to block access to adult content or potentially malicious websites, the method is very effective. To use it, you just need to specify the required DNS addresses in the connection and protocol properties of the IPv4 version.

This example uses Yandex public DNS with an adult content filter.
There are other blocking options:
- Yandex: 77.88.8.88 (main) and 77.88.8.2 (alternative) - filtering phishing and fraudulent resources.
- Norton ConnectSafe (Symantec): 198.153.192.40 (primary) and 198.153.194.40 (alternate) - filters phishing, fraud, malware.
- Norton ConnectSafe: 198.153.192.50 and 198.153.194.50 - the same plus an adult content filter.
- Norton ConnectSafe: 198.153.192.60 and 198.153.194.60 - the same plus blocking of any “inappropriate” topics.
In browsers
Modern browsers contain a lot of useful things, but most of them do not have functions for blocking sites of the user's choosing. It remains, perhaps, only in Internet Explorer.
To make the ability to block sites appear in your favorite browser, just install a special extension in it, for example, Block Site. This link takes you to the Chrome store, where you can download such a plugin (not just one, but three with the same name) for Google Chrome and Yandex.Browser.
The principle of operation of such extensions is very simple. They add a blocking feature to the context menu. By right-clicking on any link (including a file download link) and selecting the “Block” command, you will blacklist the site. And the whole thing, and not a separate page.

Some of the presented extensions also allow you to manually add to the blacklist and create custom filters for blocking by content.

Plugins with web resource block functions are produced not only for Chrome, but also for Opera, Mozilla Firefox and other less popular browsers.
Using Windows Firewall or a third-party firewall
Windows Firewall can only block websites based on IP addresses. This is not the most The best way, since one IP is sometimes shared by several resources, and large portals such as VKontakte and Odnoklassniki occupy entire ranges of addresses. Third-party firewalls can be configured more flexibly - they allow you to block access to even a single page. To do this, it is enough to indicate its URL in the program, not its IP, which is much more convenient for the user.
Since each firewall is configured in its own way, and we cannot consider them all, let’s study the configuration principle universal remedy — Windows Firewall 10.
To create a blocking rule, we first determine the site's IP. To do this it is convenient to use the command ping_URL(for example, “ping ya.ru”) or whois services.

- Let's open the firewall. In the left panel, select “Outgoing Connection Rules”, and in the “Actions” list, select “Create Rule”.

- In the next window, check “All programs” (if the site should be blocked in all browsers) or “Program path” (if in one). When choosing the second option, indicate the path to executable file browser.

- We'll skip the next window. After it, we have to indicate the IP to be blocked. At the bottom of the “Area” window, select the “Specified IP addresses” item and click “Add”. Top margin We do not touch it, since it is intended for creating rules in local networks.

- Enter the IP address or range of website addresses and click OK.

- Next, select “Block connection”.

- Let's mark the network profiles for which we are going to use the rule.

- AND last step Let's give the rule a name.

After clicking “Finish” the rule will take effect.
On the router
Access control settings on routers different models are not the same, but their algorithm is largely similar. Let's figure out how to block access to unwanted sites using TP-Link as an example.
Control TP-Link access(and not only) works in black and white list mode. In the first case, access is allowed to any web resources except those specified. In the second, it is prohibited to apply to everyone, except, again, those indicated. Let's consider creating a blacklist as an example, since it is used more often.
- Go to the admin panel, open the “Access Control” section and click “Setup Wizard”.

- In the new window, select the “IP address” mode, indicate the name of the host for which we are creating a rule, and enter its IP or address range.

- Next, select the mode “ Domain name", write an arbitrary name of the target (for which the rule is created) and list the prohibited sites.

- The next step is to create a blocking schedule.

- Then we set the name of the rule, check all the parameters and click “Finish”.

- The last step is to select a filtering mode (in our case, block packets with specified domains pass through the router) and save the rule. Also, don’t forget to check “Enable Internet access control management.”

This completes the setup.
Parental controls
Parental controls are now being built in wherever possible. It is available in many routers antivirus programs and even in themselves operating systems. Before Windows release 7 parental control was separate system function. In Windows 10 it became " family security with settings via the Microsoft website,” but its essence has not changed. Parents still have the opportunity to use it to limit their child’s access to network resources.
However, what are we all about Windows and about Windows? Let's look at how parental control works in Kaspersky Internet Security.
- Restrictions are configured through a specially designated section.

- The first thing you have to do after entering it is to set a password to disable the function and change the settings.
- Next, you will see a list of user accounts for which you can enable parental controls. Click “Set up restrictions” next to the selected account.

- Restrictions on access to web content are set in the “Internet” section. There are 2 blocking modes: sites for adults (black list) and all sites except permitted ones (white list).

- When you select blacklist mode, you can specify categories of content to be blocked, but without specifying specific sites. When selecting a mode whitelist allowed sites must be added to exceptions. Everything else will be blocked.

The control on/off slider is located at the top of the settings window in the user list.
Using static routes
Static (permanent) route is tough given path following packets from one network node to another. For example, from your computer to the server that hosts the website. Having registered in Windows registry or in the router settings there is a false route to an Internet resource (more precisely, to its IP address), you will make sure that it does not open.
How to do it:
- Define using the command ping_URL IP address of the desired site.
- Without closing the command line (it must be launched as administrator), run one more instruction: route -p add destination_site_IP mask 255.255.255.0 192.168.1.0 metric 1.

The answer “Ok” means that the route to the site 213.180.193.3 has been created. Now ya.ru will not open on this computer.
In the Windows registry, all static routes are located in the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\PersistentRoutes section.

To remove an entry from there that has become unnecessary and resume access to the site, right-click on the entry and select “Delete.” Or run in command line instructions route - f. Last method deletes all existing permanent routes. If you want to remove only one of them, run the command route delete target_node_ip, For example, route delete 213.180.193.3. After this, the ya.ru website will become accessible again.
Using local IP Security (IPSec) policies
Using IP Security Policy (IPSec) to restrict Internet access is a non-trivial method. Very few people know about the existence of such a possibility (unlike Hosts), and anyone for whom you block a certain web resource will never guess how you did it.
Using IPSec, you can block both an individual IP site and a pool of addresses. The only downside to this method is that not all have the policy management snap-in. editions of Windows. So, it is absent in home releases.
Creating an IP security policy may seem complicated, but only the first time. After several attempts, it will not take you more than 2-3 minutes. Moreover, every step of the setup is accompanied by a Wizard.
- So, to access the snap-in, open Administrative Tools in Control Panel, click Local Security Policy, and select Local PC IP Security Policies.
- Right-click on the empty area of the right half of the window " Local policies" and select "Create IP security policy". The first Setup Wizard will launch.

- In the window that opens, enter the name of the new policy and briefly describe its purpose. You can leave these fields as default, but it’s better to fill them out so you don’t get confused later.

- Then click “Next” without changing anything.

- Complete the Wizard by checking “Edit Properties” and clicking “Finish.”

- In the properties window for the future IPSec policy, click “Add”. This will launch the next Wizard - creating IP security rules.

- In the “Tunnel Endpoint” window, leave everything as is.

- Under Network Type, select All Connections.

- In the “List of IP filters” (they just need to be created), click “Add”. Next, give your list a name and click “Add” again. The third Wizard will start - IP filters.

- First of all, give the new filter a description (it’s most convenient to specify the URL of the site to be blocked).

- Specify “My IP address” as the traffic source.

- Destination: “Specific IP or subnet.” Below, write the address of the site or subnet to be blocked.

- In the “Protocol Type” section, check “Any”.

- The last step is to click “Edit Properties” and “Finish”. There is very little left.

- Confirm the new filter settings.

- If you want to create another one, click the Add button in the next window. Otherwise, click “OK”. This will launch the Filter Action Configuration Wizard.
 In the “List of IP filters”, mark the one you just created and click “Next”.
In the “List of IP filters”, mark the one you just created and click “Next”. 
- Give a name and description to what it will do (block the site).

- In the action parameters, specify “Block”.

- The final step of the stage is “Changing properties” and completing the wizard.

- Now check and confirm the setting again.

- The final push is to create safety rules. The fifth Master will do this.

- When it’s finished, change the properties again and click “Finish.”

- Review and confirm the parameters of the new rule.

- And finally - all the properties of the policy. It has been created and is displayed in the section list.

- All that remains is to put the policy into effect. Right-click on it and select “Assign”.
 In the “Properties” section you can later change any policy settings, and through the context menu you can disable, rename and delete.
In the “Properties” section you can later change any policy settings, and through the context menu you can disable, rename and delete.
Good afternoon
Yes, there is such a possibility. MegaFon has taken care of protecting its subscribers using the Stop Content service. This service is not advertised so as not to lose revenue from subscriptions and paid content, but it works great.
We set a ban on subscriptions on MegaFon
1. Type on the phone keypad *526# and click on the call button:
2. You will immediately receive a response from the MegaFon network:

The response may be “The Stop Content service is connected” or “The Stop Content service is already connected” if you have done this previously.
The Stop Content service does not have subscription fee, connection is also free. Unfortunately, using this wonderful service may cause you some inconvenience. You will also not be able to send SMS to useful and necessary short numbers. For example, you will not be able to pay for parking, participate in free sweepstakes or use mobile banking(only for some banks, for most there is an exception).
But, despite some inconveniences, the Stop Content service is necessary and useful, especially for people who cannot control their subscriptions (they don’t understand, pensioners).
In addition to subscriptions, money in the account may disappear due to paid services(often completely unnecessary). You can read about how to disable them in the article:
If you have any questions or need clarification, please, or leave a comment.