Security of third-party email clients on Mac: what data do you voluntarily give and to whom? HTTP services for those who do not understand anything about the WEB
At the beginning of December, the long-awaited release of the desktop version of the Spark email client for macOS took place. This application is popular on iPhone and iPad due to its attractive design, all the necessary (but not redundant) functionality, and large quantity popular fastening type options important letters, smart inbox, read receipts, and so on. Apple Company quickly added Spark for macOS to the list best apps year in Mac App Store, which only added to the popularity of this email client. Personally, I use Spark on iPhone, iPad Pro, and since the start of beta testing of the desktop version, he has abandoned the “heavy” AirMail on Mac. However, the free email client with user-friendly interface and still has excellent functionality underwater rocks. Developer Vladimir Shabanov on Facebook drew users' attention to Spark's privacy policy.
Why free unofficial ones are dangerous email applications like Spark? Because they get access to all your letters outside of your laptop, iPhone and gmail on their server - and when it is hacked, most of your accounts in stores, social networks, payment systems, dating, bookings, steam and dropboxes will also be hacked. And the companies that develop these apps have no incentive to invest in security because they don't charge you for the app.
In order not to copy too much large text with background, tips and conclusions, we recommend read about Spark in the publication of Vladimir Shabanov. And at iG, we asked ourselves: what is the actual situation with the collection and storage of user data when using third-party mail clients? To do this, we looked into the “Privacy Policy” sections that are unpopular among most users and selected from there the main facts that you need to know when using third-party email clients on Mac. Briefly we're talking about that almost all applications send user data, including addresses, to developer servers Email, in some cases, passwords, email texts, contact lists, calendar data and various anonymized data. And some applications even collect device information, phone numbers, location, or completely copy all data available in the email account to the server. We also asked Yandex and Mail.ru regarding the collection of user data and letters when working with accounts third party services and a mechanism for sending push notifications about new letters, however, company representatives were unable to promptly respond to the editor’s request.
Of course, every developer claims that user information stored on reliable servers like Amazon Web Services, and they all take some additional protective measures. However, is it necessary to say that we are not talking about one hundred percent security? While the largest and most reliable Internet companies sometimes leak user data, relying on the protection of small startups would be reckless. On the one hand, you can brush off all threats under the pretext that there is no secret data in your mail, but do not forget that even in the most boring mailbox there is a lot of interesting things for attackers. Nowadays, the email address serves as a key identifier to which accounts of payment systems, social networks, various sites and services are linked, and in some cases the email password matches other accounts, which increases the possible damage from hacking. Simply put, you cannot be careless when choosing an email client, and when using third party software It is imperative to understand exactly what data you are transmitting to developers.
Spark

1. In addition to impersonal statistical information When using the application, you may be asked to provide some personal information.
2. The first email address that is added is used as the username. It may send you emails with information about new features, updates, announcements, and requests to provide feedback on your use.
3. Spark servers are used only to deliver push notifications and in some cases send emails.
4. Accounts are added using OAuth authentication if possible. Otherwise, addresses and passwords are stored on a cloud server Amazon Web Services.
5. In addition to Amazon Web Services security policies, Spark uses a number of measures to prevent third parties from accessing data, as well as HTTPS protocol and asymmetric encryption of account data.
6. Spark uploads the subject and part of the email to the server to send the push notification and deletes this data immediately after the notification is delivered. Messages are stored encrypted on the server.

1. The mail client may request the voluntary transfer of data such as name, email address, phone number and bank card.
2. Polymail collects and stores data about usage scenarios of the application and its functions, as well as mobile devices on which it runs, including: operating system, smartphone or tablet model, unique identifiers devices, information mobile communications and phone number.
3. When using Polymail, developers can collect information about the user's location, IP addresses, GPS data, as well as information from other sensors of the mobile device.
4. Polymail collects and stores information about the contacts of users with whom you exchange letters. This data is used to improve the service.
5. Polymail collects and stores information about sent emails (subject and attachments) to provide read receipt functionality.
6. To improve the Polymail service, we index letters: the date the message was received, folders and sender names.
7. Cookies and other anonymous identifiers are collected and stored by Polymail and its partners.

1. Postal Airmail client does not collect or store emails on cloud servers. When using options such as Snooze Sync, all necessary data is synchronized directly between devices.
2. Airmail collects and stores data such as Cookies, anonymized information about application usage scenarios and email addresses.
3. Cookies are collected and used only for the purpose of identifying the user to save settings and to provide the services required by the user.
4. In some cases, access to data collected and stored on servers may be provided to certain employees associated with the work of Airmail: administrators, sales specialists, marketers, lawyers.
5. User data is collected to operate Airmail, as well as for the following purposes: interaction with third party social networks and platforms, managing contacts and sending messages, analytics, remarketing, behavioral targeting, for commercial purposes, for payment processing, interaction with the service technical support and feedback.

1. If the account does not support OAuth authentication, the login and password are stored on the AWS cloud server.
2. On cloud servers emails are downloaded to send push notifications.
3. Emails are downloaded within the last 14 days on mobile devices and 60 days on Mac.
4. Newton receives and stores information from our partners about users who send you email.
5. To use the Read Mark feature, Newton collects and stores data about sent emails.
6. Newton promises that it will not sell or transfer to third parties. personal information, and also uses the HTTPS protocol and additional security tools when transferring data to AWS servers.

1. Using the Canary email client does not provide access to users’ personal data and transfer it to cloud servers.

1. When creating an account, Nylas N1 collects and stores personal data, such as email address, first and last name, which can be used for identification.
2. When using the application, Nylas N1 collects and stores data account and associated passwords.
3. By entering your email account information you agree to grant Nylas N1 the rights to make a copy of all content mailbox, calendar and contact list.
4. Nylas N1 also uses automated data collection tools such as Cookies and Web Beacons.

1. Mail, calendars, files, contacts, settings and other data from it will be automatically synchronized with the device via a cloud server.
2. Outlook stores data on Microsoft servers for support additional features, such as quick search, personalized filtering of less important mail and adding attachments from linked storage providers.

1. On the official website of the application, the information in the “Privacy Policy” section applies only to the operation of the Unibox website itself. There is no information about the collection and storage of personal and anonymized data when using the Unibox email client.
Let me start with the fact that I was once forced to deal with Web services on my own. Then somehow, little by little, I managed to master this matter and understand what and where to press for everything to work. Fortunately, the configuration we had to work with was already stuffed It was possible to look at it using Web services and do it by analogy, and on the Internet I was able to find enough articles on this matter. And so, using examples (for me it’s The best way study), I have mastered this matter, and now they no longer scare me.
SO. The main task of any integration, be it CD, Web services or HTTP services, is to transfer something from somewhere, do something with it, and return a response. This is the format in which we will consider the new technology.
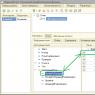
In the metadata tree, HTTP services are located in the General branch:
Added new HTTP service just like any other metadata object. Name and synonym as you wish. Only the “Root URL” is important here - this is, in fact, the identifier HTTP service in this database, i.e. exactly what you write in this property is what you will pass to a third party developer(or for yourself) as a link to the service.

I don’t know if it’s possible to write here in Cyrillic, but so as not to be laughed at in the progressive world, write in Latin).

The Template property itself is important here:

Using a template, you can later refer to the data that was transferred to you. SO: all the data that you want to receive from the outside can be divided into 2 blocks - mandatory and optional.
Required data/parameters we push it into the template, thus if the person accessing the service does not fill them out, then the service will a priori generate an error, and when developing the text of the handler module, you will be sure that this data is there. How this is done: in the line Pattern in curly brackets “()”, alternating with the “/” sign, we write the names of the variables. For example, we definitely need an article - then we write /(artikul). If we need to get the article, name and username, the template string will look like this: /(artikul) /(name)/(user), etc. Each of these parameters in the text of the handler module can be obtained like this: Request.ParametersURL["<имя параметра>"]. If there are no required ones, then the template looks like this: /*.
Optional data, which we want to receive through the service, are NOT described in the template. When building a link to access a service, they are described at the end of the link after the "?" sign, separated by the ampersand character "&" and have the structure<имя параметра>=<значение параметра>. In the text of the handler module, they can be accessed with the following construct: Request.RequestParameters.Get("<имя параметра>"). BUT: it is important to remember that since they are not required, they may not exist; accordingly, we check the value for Undefined.
Next we add new method for our template. The HTTP method property is important here. There are them here great amount, BUT we will not go into all the details. To implement any of your tasks you only need 2: GET And POST.

How to choose: If what we described in the previous two paragraphs is enough for your work, i.e. You can get all the data you need using the mandatory and optional parameters of the request itself, then we take GET. In this case, in any browser, if you enter correctly address bar, you will see the result of your HTTP service - PROFIT! If suddenly your service requires data in more complex form(xml for example, or something else), what cannot be stuffed into a simple address bar, then we take POST. On the downside, such an easy check through the browser address bar, as with GET, will not work, but on the Internet you can easily find some sites where you can check services using the POST method (for example, the site https://www.hurl.it) . If the method is selected POST, then the request besides URL (addresses) a body appears into which you can stuff anything, and in the method handler access it through the Request.GetBodyAsString() construct. Any template can have both a GET and a POST method. They will have correspondingly different handlers, and 1C, depending on how the request was sent, will choose one method or another.
An HTTP service handler is a function that always returns a value of type HTTPServiceResponse, which is built by the constructor New HTTPServiceResponse(<КодСостояния>). <КодСостояния>- this is a number, so as not to have to worry about choosing what to write, we write: 200 - if everything is fine and you return some logical value, 400 - if there is an error and you return a description of the error. U of this type There is various methods(you can read it in the syntax assistant, everything is clearly written there). Again, you can always return everything you need as a string - the SetBodyFromString() method. (one little trick: if you return html and want the browser to display it beautifully on the screen when you enter the address of your service in the address bar, in the response Headers property write: Answer.Headers.Insert("Content-Type","text/html; charset=utf- 8") - thereby you indicate that this is not just a set of characters, but HTML and it must be shown accordingly)
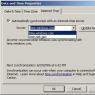
After you've done everything, the HTTP service needs to be published. This is done on a computer with a web server installed (I won’t write about the settings, there are plenty of articles) through the menu:
Administration - Publishing on a web server.

There is a HTTP Services tab. Check the boxes and click "Publish"

So, we received a ready-made HTTP service. HOW to contact him? If we use the GET method, then in the address bar of the browser we write: http://<имя веб сервера>/<имя базы>/hs/<корневой URL>/<обязательный параметр1>/<обязательный параметр2> <имя не обязательного параметра 1>=<значение не обязательного параметра 1>&<имя не обязательного параметра 2> =<значение не обязательного параметра 2> .
And finally, once again in pictures))):

Since version 1.6 in Android there is a “service special features" It is not difficult to guess for what purpose it was created, but we, as people striving for unlimited possibilities, are interested in this service from a slightly different angle. Today we will write a program that will allow us to monitor input in other applications!
Why do you need an accessibility service?
It allows you to expand the interface regular applications to help users with disabilities or those who may be temporarily unable to fully interact with the device. For example, users driving a car, caring for a small child, or being at a very noisy party may require additional or alternative interfaces feedback.
Android has standard service special capabilities - TalkBack. If necessary, developers can implement their own. It has been possible to write such services since time immemorial (Android 1.6, API level 4), and with Android 4.0 (API level 14) they received significant improvements. Through the “support library”, these improvements are also implemented for devices with API versions lower than 14.
This service allows you to view a description of all windows, running applications and receive data entered by the user (except for entered passwords; agree that logins and text messages is also sufficient in many cases).
In this article I will tell you how to implement a service for intercepting keyboard input as simply as possible.
To do this you need to create an heir AccessibilityService. In the connection method onServiceConnected we need to set an event filter (class AccessibilityServiceInfo) that the service will listen to. And in the method onAccessibilityEvent process these events.
In the application manifest, you must add the following lines to describe the service:
If everything is done correctly, then in the log you can see something like this:
OnAccessibilityEvent: TYPE_VIEW_TEXT_CHANGED android.widget.EditText com.android.chrome 113326642 website
Class AccessibilityServiceInfo allows you to set filters for certain applications(who said “mobile banks” or “social network clients”?). We can take screenshots based on the event we need.
This is done quite simply on a rooted device, and if there is no root, then you need to look for third-party libraries to get screenshots from the service.
Example code for getting a screenshot from the service on a rooted device:
Continuation is available only to subscribers
Option 1. Subscribe to Hacker to read all materials on the site
Subscription will allow you to read EVERYTHING within the specified period paid materials site.
We accept payments by bank cards, electronic money and transfers from mobile operator accounts. Your actions on the computer are easy to track. As a result of activity in the request history, traces remain in the browser, which it is advisable to delete, since this is confidential information. In this article you will learn how to delete search history in popular browsers , clear information about search queries Google systems
, yandex, cookies. On the one hand, it is not necessary to hide information from each user, on the other hand, you are not immune from leakage confidential information . Once an attacker gains access to the history Google search
or user browser data - good luck.
What data is stored in browser history? In all popular browsers ( Google Chrome , Firefox, Opera, IE...) are all available necessary funds for thorough removal personal information
- . But first it is necessary to clarify what is “hidden” under this confidential information in the history of any browser:
- Cookies are a piece of text received by the browser from the server. Defines user settings on the site. Typically, cookies are used for authorization, tracking session status, or maintaining statistics about users.
- Saved form data, Search history - browsers have an auto-completion function, when when you enter a word or expression, the program suggests possible options previously entered data.
- Wand passwords - in Opera - passwords and logins for logging into websites. Works like auto-filling forms when you press the keyboard combinations Ctrl+Enter.
- Entered addresses - a list of addresses entered into the browser address bar.
- Cache - data saved on the hard drive from visited sites: HTML pages, images, flash, etc. The cache serves for more fast loading pages using previously saved files.
How can you delete all information from your browser without exception? Actually, how to delete browser history? Modern Internet browsers They brought this function to the forefront a long time ago, and clearing history is available in two clicks. In different ways, let's look at each specific case and browser.
How to delete browsing history for all browsers at once
I will tell you further about how to delete browser history and website visits through settings.
How to delete history in Opera
- browsing history in Opera
- download history
- Opera cookies, etc.
- cached images and files
- form autofill data
- data from third party services
Select the options you want and click the “Delete” button. You can also delete your browsing history for a specified period.
Privacy settings in Opera can be opened at the following address: menu “Tools - Settings”, tab “Security”, section “Privacy”.
To avoid deleting history, you can use private mode navigation in Opera using Ctrl combination+ Shift + N .
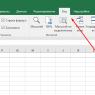
How to delete history in Chrome (Google Chrome)
You can delete history in Google Chrome at Settings and Google management Chrome (icon on the right top corner browser) - Additional tools- Deleting data about viewed pages - Ctrl + Shift + Del.
Available story elements:
- Download history
- Cookies browser
- Images and cache files
- Passwords
- Autofill data
- Other Chrome History Elements
We tick the boxes that need to be deleted from the Google Chrome history and indicate the period: for all time, the past hour, etc.
How to delete history in Mozilla (Mozilla Firefox)
- Menu “Tools - Delete personal data”.
- Select the list items and click the “Delete Now” button.
- Privacy settings: menu “Tools - Settings”, sections “Privacy”, “Protection” and “Advanced”.
How to delete Google search history (Google.com search engine)
Based on the fact that Google is by far the most popular search engine in RuNet, using her example we will tell you how to delete the request history directly on the user account page in this service.
Actually, for those who would like to delete their Google search history, the search engine developers met halfway and put all the tools for “cleaning up” together.
Big brother Google is watching you: search history at a glance
In order to delete Google history without the possibility of recovery on all accounts, regardless of the device (PC, phone, tablet), do the following:
- We go to the page Google account My actions
- To delete actions for certain period
- In the “Delete by date” column, select a time interval, for example, All time
- We tick the necessary products - for example, Search - in order to completely erase the Google search history in the future
- Click the DELETE button to permanently delete your Google search history (after this you will not be able to restore it!)
How to delete history on your phone and tablet (Android)
The easiest way is to delete history from your phone in one fell swoop, using a specialized CCleaner utilities. mobile version The application completely removes data that could reveal your privacy by revealing your browsing habits.
The CCleaner utility allows you not only to completely delete browser history on Android, but also to optimize your phone by clearing the cache and other garbage. So its installation will be justified in any case.
How to delete history on Android:
- To delete history, go to the "Clear cache and memory" section
- Check the "Browsing History" option in CCleaner
- Click "Analyze" and "Clear" to complete removal stories
Removing sensitive operating system data
It turns out that there are countless hidden places on your computer where you can find out about your activities. It should be taken into account that more than one program may be involved in the work process. What to do in this case? Searching and deleting information that in one way or another concerns the user is a too long and routine process. Navigating through numerous menus (which for the most part cannot be remembered)… In general, carrying out daily cleaning is a waste of time.
Meanwhile, there are a lot of programs for deleting such information. There are “tweaker” programs where one or more sections serve exactly this purpose. But it is better to use one of the specialized utilities. Here is a list of some of them:
- NetConceal AntiHistory
- Privacy Eraser Pro
- Icesun System Cleaner
- Advanced System Cleaner
- Smart Data Scrubber
- East-Tec Eraser 2008
- Advanced Tracks Eraser
- Disk Cleaner Tool
- AbsoluteShield Internet Eraser Pro
One of the programs that should be on this list is Total Privacy 5. It is the most suitable option for our needs. You can download Total Privacy on the website in the “Download” section. The program is paid, but it works fully functionally in trial mode for 15 days. Unfortunately, it is only available in one language - English. This is a small drawback, given that we will be explaining almost every option in the program.
“Overview” section
By clicking on the “Wash My Computer” button, you will delete the data noted in the “Wash Setup” section from your computer. Therefore, we will return here later.
Wipe Method - method of erasing. This can be erasing in one or several passes (depending on which the chances of restoring the document change) or erasing according to standards (8 types of standards approved in different countries).
Selected Profile - settings saved in the “Profile” section.
Windows Tab
This section contains items related to Windows privacy in general. We will consider the contents of this tab in more detail, the rest - briefly.
“Start Menu” section
- Empty Recycle Bin- cleaning.
- Document History - recent list open documents in the Main Menu (see the “Recent Documents” section).
- Find Files or Folders History - clear Windows search bar history.
- Run History - clears the history of the “Run” dialog.
- Find Computer History - clearing the computer search history on the network.
- Start Menu Click History and Start Menu Order history - surprisingly, all clicks on the Start menu are recorded in the log. You can verify this by clicking on the “View Start Menu Click History” option.
“Browsers” tab
Removing personal information in popular browsers Internet Explorer Mozilla Mozilla Firefox, Opera, etc. We won’t dwell on this tab. Read more about this in the next chapter.
“Custom” tab
List of applications containing confidential information. Total Privacy pleases with a rich list of supported programs. For example, this includes the following popular apps like WinRar, Adobe Acrobat Reader, Winamp, Opera, etc. In order for Total Privacy to display a list of only programs available on your computer, check the box next to the “Show only detected programs” option.
“Wipe Free Space” tab
Whenever you delete a file (including deleting it from the Recycle Bin), it still remains on the hard drive - in whole or in part. At the same time, the area hard drive marked as “free to rewrite.” If desired, using recovery programs deleted files can be successfully restored. It depends on the time that has passed since the deletion. Erase (permanently delete) data regular means Windows is not possible. But you can do this using the “Wipe Free Space” tab. To erase, check the “Wipe the free space” option and select the disks to destroy information.
Section “Other Privacy Utilities”
“AutoStart programs” tab. Programs launched when booting Windows. If you do not know the purpose of a particular program, it is better to disable it (the “Disabled” button).
“IE Extensions” tab.
When installed, some programs are seamlessly integrated into Internet browser Explorer. Spyware can be disguised as an extension. Most reliable way- disable or remove all add-ons. Not only will this not stop the browser from working, but it will even load faster. If you know what's what, leave the most useful add-ons enabled.
“Internet Explorer” tab.
Browser settings that affect browser privacy: autocomplete, passwords, etc.
After you have marked the desired options, you need to go back to the top “Overview” section and click the “Wash My Computer” button to erase the marked personal data. The “Wash” tab displays the removal process.
Thus, almost all functions Total programs Privacy we have listed. The matter is up to you. Finally, you can go to the settings (“Settings” section) and set the program to autoload from Windows. Then the process of deleting confidential information will be automated.
In the last article I wrote about visiting blocked sites. I decided to continue a series of articles on browsers, and today I will write about how to clear history, cache, cookies and other information in the Opera browser. There seems to be nothing complicated there, but for many such instructions will be useful. I don't know about you, but I Opera browser I’ve been using it for a very long time, probably since I started using the Internet. Therefore, first I’ll tell you about solving various issues with this browser.
In the Opera browser, you can clear not only the history of visited sites, cache and cookies. There is also a download history, passwords, a history of auto-filling forms, and some data from third-party services. Let's first understand what it is and why clear this data in the browser.
- Visit history. Everything is very simple here. The browser always remembers the sites you visit. Every page. You can watch this story later. Sometimes this can be very useful. But, there are times when we need to clear history in Opera. For example, when we surf the Internet from someone else’s computer. I'll tell you a secret that in this case, it is better to use " Private browsing". "Menu" - "Create private window" In that Opera mode does not remember browsing history and other information.
- Download history. History of files that we downloaded from the Internet through a browser.
- Cache (cached images and files). These are different elements of websites that the browser saves so that the next time you visit the site it does not download these files again. And the site is already opening much faster. Clearing the cache can be useful in cases where, for example, the site is not displayed quite correctly. Or updated information is not displayed on the site. Sometimes, due to the saved cache, the router settings do not even open or are not displayed. In this case, you just need to delete the cache and the browser will reload up-to-date information from the site.
- Cookies. No, this is not a cat from the SlivkiShow channel :). IN browser cookies, this is a small piece of data that the browser receives from the site, stores it, and sends it back when visiting the site. Thanks to cookies, we don’t need to log in to sites every time or set any settings in different services And in social networks, re-add products to the cart in online stores, etc. Be careful, if you clear cookies in Opera, you will most likely have to log in to the sites again and set some settings.
- Passwords. Everything is very simple here. These are passwords from different sites to which you logged in using your data.
- Data for autofilling forms. When we fill out some forms, Opera remembers the information we enter, and when we fill out these forms again, it offers us the saved options. This is very convenient, I often use this feature myself. So, you can clear this information if necessary.
- Data from third party services. Many people advise clearing this data when problems appear in VPN work in Opera.
What we have figured out is that it’s time to move on to clearing the data we need in the Opera browser.
Opera: delete history, cache, cookies, passwords, form data and third-party services
Everything is very, very simple. Open Opera and click on the "Menu" button in the upper left corner. Hover your mouse over "Other elements" and select "Clear browsing history". Or press the keyboard shortcut Ctrl+Shift+Del.
A small window will immediately open. First of all, in the drop-down menu, select for what period you want to clear the data (behind last hour, day, week, 4 weeks, entire period). Then check the boxes that need to be cleared. Above I described each point in detail. And to clear it, click on the “Clear browsing history” button.

All data will be completely cleared.
Another way you can delete your browsing history in Opera
I don’t know if it will be useful to you, but you can clear your history using different programs to clean the system of debris. The most popular is probably CCleaner. On the "Applications" tab, you can select items that need to be cleared in the Opera browser.

There you can also clear history from other browsers, and clean Windows from unnecessary files. But watch carefully with this program. Especially with the "Registry Cleaner" section. Don't get too carried away.
These are the tips. I hope you found this article helpful. Best wishes!