What is keygen and where to find it. There are no files to install the program for free. Examining the contents of the folder with the installation file
How to use keygen, crack, patchIntroduction
It's no secret that in our country 90% of installed programs on computers are not licensed. The programs are already hacked, but installing them requires some skills. The article discusses the most common installation methods pirated programs. How to use keygen? How to use crack? What is request code? How to use patch?
Required knowledge
Program installation process
I advise you to study before
How to download a program from the Internet
How to download via torrent
We study the contents of the folder with installation file
Open the folder with the program installation files and examine its contents. Perhaps you will find a crack folder in it, then open it. Here possible options what you can find.
Text file (.txt)
File with instructions (readme, instructions, ...)
File with serial number(serial, key, ...)
Application file (.exe). Let's open it.
It generates a serial number (keygen, crack, ...)
It has a Request code field and another field (keygen, crack, ...)
There are no fields for the serial number. There is a Patch, Apply patch or Crack button (patch, keygen, crack, ...)
There is nothing in the folder except the installation file
Searching for a solution on the Internet
1. Installation instructions in a text file
The first thing you need to pay attention to is whether there is a “readme.txt” or “read me.txt” file in this folder (there may be other names). Very often it contains instructions for correct installation programs. If there is a file with instructions, then feel free to open it and follow the instructions. If there is no file, then the situation becomes a little more complicated.
2. Serial number in a text file
A serial number is sometimes required to verify ownership of a program. Having it, you can install the program for free.
The serial number may be required either when installing the program, or when launching it for the first time after installation. You cannot skip this step; the program will not proceed further until you enter the serial number (Fig. 1).
free installation of the program - serial number
Fig.1
Prompt to enter serial number
Example serial number: ADE-R119-F196-k9BA-17CD
In the folder with the program (in the same folder as the installation file) there may be a file with a serial number. Most often it is called “Serial number”, “Serial number”, “Key”, “key”, “crack”. Open this file, copy the serial number and paste it in the right place.
Open text file, copy serial number (Cntr+C)
All
3. How to use keygen
The program folder may contain a program file (keygen, crack, ...).
Here is an example of such a program, if you run it (Fig. 2) 
How to use crack
Fig.2 Serial number generator
Click on the “Generate” button (Fig. 3)
how to use keygen
Fig.3 
Serial number generator with key
Copy the serial number, paste it in the right place and you're done. We continue the installation, or click “Ok” (possibly “Finish”, “next” ...) if the installation is already completed.
Sequencing:
Start installing the program until it asks for a serial number
Open Keygen file
Generate serial number and copy (Cntr+C)
Paste it where required (Cntr+V)
All
4.Gaining access using the "Request code"
Another option. During installation of the program or after launch installed program, a registration window appears on the screen. There should be keygen.exe, crack.exe or something else in the folder with the installation file.
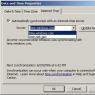
Example of a registration window (Fig. 4)

Fig.4 Start of registration with "Request code"
Sometimes you need to select a registration mode, for example, select “enter serial number”. A window for entering the serial number appears on the screen. (Fig.5)
IN in this case:
- Get an activation code - get an activation code
- Enter an activation code - enter the activation code (the option we need)
Request code
Fig.5 
Open the file keygen.exe (crack.exe, ...) from the folder with the program installation (Fig. 6).
Request code
Fig.6 
Now we need to copy the “Request code” from the window in Fig. 4 (Fig. 5) and paste it into the window in Fig. 6. Select Request code and press Cntr+C ( hotkey copy).
Paste the copied code into the last window (Cntr+V).
Note!!!
The code was not copied completely, but only the first line. The second line of code needs to be copied separately, in the window in Fig. 6 you need to put a space, copy and paste the remaining part of the “Request code”. It should look like this (Fig. 7) 
Request code
Fig.7
Generator after inserting "Request code"
After this, in the program in Fig. 7, click the “Calculate” button (sometimes called Generate). It should look like this (Fig. 8):
free installation of the program - Request code
Fig.8 
We copy the "Auth code" from the program in Fig. 7 into the window in Fig. 5 and get this (Fig. 9): 
Free installation of the program - Request code
Fig.9http://posthelper.ru/images/articles/23/071.png
Click Next or Ok. We should be informed that the registration was successful. Now the program can be used for free.
This situation occurs quite often. The main thing is not to forget that the Request code consists of two lines.
Sequencing:
Install the program
Run the program
Select serial number entry mode (Enter...)
Open keygen
Copy "Request code" from the program to "keygen" (both lines)
In "keygen" click the generate button
Copy the code received in "keygen"
Paste it into the required place in the program (Cntr+V)
Click done
All
5. How to use patch
Sometimes for free installation programs cannot simply generate a serial number. In such cases use special programs, which change files so that the program does not require money. In the folder with the program installer there should be a file "Patch" (it can be called - patch, keygen, crack, ...). This is a program, also called a patch.
The first thing we have to do is install the program (the one we want to make free). After installation, you do not need to open the program.
Next, we need to rewrite patch (or another patch file) to the folder in which we installed the program. Most likely this is drive C, folder Program files, folder with the program name (C:/Program files/“program name”).
Here is an example of a patch.exe file (Fig. 10):
how to use patch
Fig.10

Patch program
Most often there is only one button in this file. In this case it is the Apply patch button. In some cases it may be called Crack. Click on this button and you can use the program for free.
Sequencing:
Install the program
Copy Patch.exe to the folder where you installed the program
Open Patch.exe
Press the only button in the "Patch" program
Run the program
All
6. There are no files to install the program for free
It may also be that you downloaded the program without a pirated “medicine”. That is, without ready-made serial numbers, keygens or patches. Then the task becomes more complicated. It is better, of course, to download programs with ready-made “medicines”. But what if such a problem still arises?
Sequencing:
Installing the program
Let's find out full version programs. (For example, Daemon Tools Lite 4.35.6)
Most often, the name of the installation file contains the full name. If the program is already installed, then in the “Help” menu item there is a line “About the program”. There you can also find out the full version of the program. If you can’t find the full name, enter the incomplete name into the search.
If during installation or after it requires a serial number, then in the search, for example yandex.ru, enter: serial number for “full name of the program” If other types of registration are required, then in the search line, for example yandex.ru, enter: crack for “full the name of the program"
We go through all kinds of links until we download the appropriate medicine or serial number
Conclusion
It is possible to combine several registration methods. For example, in the folder with the installation file there may be a serial number in text document, as well as Patch. In this case, during installation, enter the serial number, and after installation, use Patch. But for this you need to know how to use keygen, crack, patch, serial number separately.
I warn you that the material in this article is for informational purposes only. Using programs without a license entails criminal liability.
Http://posthelper.ru/page.php?staty_g=23 source
It's no secret that in our country 90% of installed programs on computers are not licensed. The programs are already hacked, but installing them requires some skills. The article discusses the most common methods of installing pirated programs. How to use keygen? How to use crack? What is request code? How to use patch?
- Required knowledge
- Program installation process
- I advise you to study before
- How to download a program from the Internet
- How to download via torrent
Examining the contents of the folder with the installation file
Open the folder with the program installation files and examine its contents. Perhaps you will find a crack folder in it, then open it. Here are the possible options that you can find.
1. Installation instructions in a text file
The first thing you need to pay attention to is whether there is a “readme.txt” or “read me.txt” file in this folder (there may be other names). Very often it contains instructions for correctly installing the program. If there is a file with instructions, then feel free to open it and follow the instructions. If there is no file, then the situation becomes a little more complicated.
2. Serial number in a text file
A serial number is sometimes required to verify ownership of a program. Having it, you can install the program for free.
The serial number may be required either when installing the program, or when launching it for the first time after installation. You cannot skip this step; the program will not proceed further until you enter the serial number (Fig. 1).
Serial number example: ADE-R119-F196-k9BA-17CD
In the folder with the program (in the same folder as the installation file) there may be a file with a serial number. Most often it is called “Serial number”, “Serial number”, “Key”, “key”, “crack”. Open this file, copy the serial number and paste it in the right place.
- Open a text file, copy the serial number (Cntr+C)
3. How to use keygen
The program folder may contain a program file (keygen, crack, ...).
Here is an example of such a program, if you run it (Fig. 2):

Fig.2 Serial number generator
Click on the “Generate” button (Fig. 3)

Fig.3 Serial number generator with key
Copy the serial number, paste it in the right place and you're done. We continue the installation, or click “Ok” (possibly “Finish”, “next” ...) if the installation is already completed.
- Sequencing:
- Start installing the program until it asks for a serial number
- Open Keygen file
- Generate serial number and copy (Cntr+C)
- Paste it where required (Cntr+V)
4.Gaining access using the "Request code"
Another option. During installation of the program or after launching the installed program, a registration window appears on the screen. There should be keygen.exe, crack.exe or something else in the folder with the installation file.
Example of a registration window (Fig. 4):

Fig.4 Start of registration with "Request code"
Sometimes you need to select a registration mode, for example, select “enter serial number”. A window for entering the serial number appears on the screen. (Fig.5)
In this case:
- Get an activation code - get an activation code
- Enter an activation code - enter the activation code (the option we need)

Open the file keygen.exe (crack.exe, ...) from the folder with the program installation (Fig. 6).

Now we need to copy the “Request code” from the window in Fig. 4 (Fig. 5) and paste it into the window in Fig. 6. Select the Request code and press Cntr+C (copy hotkey).
Paste the copied code into the last window (Cntr+V).
Note!!!
The code was not copied completely, but only the first line. The second line of code needs to be copied separately, in the window in Fig. 6 you need to put a space, copy and paste the remaining part of the “Request code”. It should look like this (Fig. 7):

Fig.7 Generator after inserting "Request code"
After this, in the program in Fig. 7, click the “Calculate” button (sometimes called Generate). It should look like this (Fig. 8):

We copy the "Auth code" from the program in Fig. 7 into the window in Fig. 5 and get this (Fig. 9):

Click Next or Ok. We should be informed that the registration was successful. Now the program can be used for free.
This situation occurs quite often. The main thing is not to forget that the Request code consists of two lines.
- Sequencing:
- Install the program
- Run the program
- Select serial number entry mode (Enter...)
- Open keygen
- Copy "Request code" from the program to "keygen" (both lines)
- In "keygen" click the generate button
- Copy the code received in "keygen"
- Paste it into the required place in the program (Cntr+V)
- Click done
5. How to use patch
Sometimes you can't just generate a serial number to install a program for free. In such cases, special programs are used that change files so that the program does not require money. In the folder with the program installer there should be a file "Patch" (it can be called - patch, keygen, crack, ...). This is a program, also called a patch.
The first thing we have to do is install the program (the one we want to make free). After installation, you do not need to open the program.
Next, we need to rewrite patch (or another patch file) to the folder in which we installed the program. Most likely this is drive C, folder Program files, folder with the name of the program (C:/Program files/“program name”).
Here is an example of a patch.exe file (Fig. 10):

Fig.10 Patch program
Most often there is only one button in this file. In this case it is the Apply patch button. In some cases it may be called Crack. Click on this button and you can use the program for free.
- Sequencing:
- Install the program
- Copy Patch.exe to the folder where you installed the program
- Open Patch.exe
- Press the only button in the "Patch" program
- Run the program
6. There are no files to install the program for free
It may also be that you downloaded the program without a pirated “medicine”. That is, without ready-made serial numbers, keygens or patches. Then the task becomes more complicated. It is better, of course, to download programs with ready-made “medicines”. But what if such a problem still arises?
- Sequencing:
- Installing the program
- Let's find out the full version of the program. (For example, Daemon Tools Lite 4.35.6)
Most often, the name of the installation file contains the full name. If the program is already installed, then in the “Help” menu item there is a line “About the program”. There you can also find out the full version of the program. If you can’t find the full name, enter the incomplete name into the search. - If during installation or after it requires a serial number, then in the search, for example yandex.ru, enter: serial number for "full program name" If other types of registration are required, then in the search bar, for example yandex.ru, enter: crack for "full program name"
- We go through all kinds of links until we download the appropriate medicine or serial number
Conclusion
It is possible to combine several registration methods. For example, in the folder with the installation file there may be a serial number in a text document, as well as Patch. In this case, during installation, enter the serial number, and after installation, use Patch. But for this you need to know how to use keygen, crack, patch, serial number separately.
5-10 years ago in order to purchase licensed program or a game, it was necessary to search original wheels. This, in turn, was quite difficult, because the market was filled with low-quality pirated products. With the spread of the Internet, everything has changed in better side. Now, to download licensed software, you just need to purchase a special key and enter it on the official website. After this, the system will perform an online key check and give you the opportunity to download the software.
Despite this availability of licensed software, many users still refuse to pay for it. Internet users use various programs designed to bypass the security system. One of these programs is keygen. What is it and what are the principles of its operation? You can learn about all this by reading this article.
Legality
But before we talk about the principles of keygen operation, it is worth considering the legal side of the issue. Since keygens can be classified as hacking programs, their use is illegal. There are several copyright laws that prohibit circumvention of technical protection measures. In the United States of America this law has existed since 1998 (described in digital age"), and in Russia a similar decree appeared in 2008 (documented in the Civil Code of the Russian Federation).
Now let’s talk in more detail about a type of program called “keygen”. What are they, how do they work, and what are they used for. You can find answers to these and other questions in this article.
Keygen: what is this?

Now there is a mass that is sometimes very difficult to understand. One of these terms is “keygen”. "What is it, where can I download it, how does it work?" — similar questions are often asked by users. This article aims to answer them. Want to learn more about copyright bypass software? Then this article is for you!
"Keygen" (short for English key generator, which translates as "key generator") are special programs that are capable of creating cryptographic keys for But most often, keygens are used to generate pseudo-authentic keys for activating licensed games, antiviruses and other software.
Work principles
In order to understand how keygens work, it is necessary to take a closer look at the key activation process. As a rule, the code is entered directly during installation. The installer (installer program) uses a special algebraic calculation in order to check its authenticity. For example, let's take a key that contains 5 numbers and 3 letters. First, the algorithm must determine the correctness of the entered numbers. To do this, the installer adds up the numbers. The sum of these 5 numbers must be equal to the value indicated in the algorithm. With letters everything is exactly the same. Letters have their numerical equivalents. The algorithm converts letters into numbers, then adds them and checks them for authenticity.

At first glance, this system seems impenetrable, like a medieval castle. But that's not true. It is very easy to find out the installer algorithm. This is what crackers (people who hack security systems) use. Using special programs called disassemblers, they view source installer. Having gained access to the source code, the cracker finds a function responsible for verifying the authenticity of the entered key. Having learned on what principle the function works, the cracker can special problems write an algorithm that will select working keys.
Keygens in the modern world
Previously, keygens were very often used to bypass the security system. Just remember the company Alawar, which suffered huge losses due to the fact that most users used keygens. Now the situation has completely changed. Key generators are no longer as relevant as they once were. The reason is that activation codes are now verified over the Internet and linked to user accounts.
Nobody wants to spend their hard-earned money on games. Because of this, many users are looking for a key generator for games from Steam and Origin. But we have to disappoint them: such keygens do not exist. The fact is that these services tie keys to accounts, which is why it will not be possible to activate codes twice. Also, for each game, Steam and Origin have their own function, which cannot be solved due to the closed program code.

If you managed to find a keygen for Steam or Origin, do not rejoice. Most likely, this is a hoax, and the so-called keygen is a regular stealer or a virus that will intercept your data. As a result, you may lose not only your Steam or Origin account, but also your page on in social networks. In order to protect yourself from this, simply do not download files from unverified and suspicious resources.
Less than ten years ago, without original discs it was almost impossible to purchase a licensed game or program. After all, at that time the market was overflowing with low-quality pirated products.
Now, with the advent of the Internet, things are completely different. To download licensed software, you need to purchase a so-called key and use it on the official website. After the key is verified online in the system, the user will be allowed to download the software.
Currently, licensed software has become available to everyone, but despite this, many do not want to pay for it. To bypass the security system, Internet users use various programs, one of which is keygen.
How does it work?
You will learn about this in this article. A few words about legality. It is impossible not to mention the legal side of the issue. After all, keygens are classified as hacking programs and are used illegally. There are copyrights that prohibit circumvention technical means protection. In America, a copyright law was passed in 1998. In Russia, such a decree was issued only in 2008.
A little more about kegen programs. How they work and how they are used.
Today there is a wide variety of difficult-to-understand computer terms. One of these is “keygen”. What is the principle of its operation and where can it be downloaded?
Translated from in English, the word - key generator sounds like “key generator”. Such programs create cryptographic keys to decrypt data. Very often, keygens are used to generate pseudo-authentic keys to activate antiviruses, licensed games and other software.
To understand how keygens work, you need to become more familiar with the key activation process. Usually the code is entered during installation. And to check it, they use the Installer - an installer program that performs an algebraic calculation. For example, we have a key consisting of 5 numbers and 3 letters. First, the algorithm determines whether the numbers are entered correctly. To do this, the installer adds numbers. In our case, their sum should be equal to the value indicated in the algorithm.
The same is done with letters that have their own numerical equivalents. Using an algorithm, letters are converted into numbers and added. This is how they are checked for authenticity. At first sight this system may seem impregnable and resemble a medieval castle. However, everything is much simpler, and the installer algorithm is very easy to recognize.
People who use these methods are called crackers. Using disassemblers (special programs) they find the source code. And having accessed it, they find a function that is responsible for verifying the authenticity of this key. Knowing how the function works, the cracker can write an algorithm that selects working keys.
In the recent past, keygens were used to bypass protective systems. Take Alawar as an example. At one time, she experienced huge losses. And all because many users resorted to keygens. Today the situation looks different. Now key generators are not relevant to the same extent as they were quite recently. Today, activation codes travel through the Internet and are attached to user accounts.
What is a keygen for games?
Many game lovers do not want to waste money on games, so they try to find a key generator for games from Steam and Origin. But, alas. This is not possible, since there are no such keygens. This is because these services tie keys to accounts. Therefore, codes cannot be activated twice.
In addition, each Steam game and Origin has its own function, which cannot be solved due to the fact that program code closed. If you nevertheless found a keygen for Origin and Steam, do not rush to rejoice. Most often this is a hoax, since in this case the keygen will be an ordinary stealer or virus that intercepts your data. And you will lose not only your Origin and Steam account, but also own page in social networks. To prevent this from happening to you, you should not download files from suspicious and unverified resources.
Disclaimer: everything written below is written solely for educational and research purposes, as well as for understanding the mechanisms of protection against hacking. The author under no circumstances recommends using this information for hacking programs.
In this article I want to talk about three and a half main ways to hack .NET programs. The goal I pursue is to help developers better understand the security mechanisms of their programs, i.e. identify the most obvious threats and take appropriate action (or not).
I won't go into detail or use complex hacking tools. Everything will be described “for dummies”, i.e. all tools will be simple, easily accessible and free. And the main one will be Reflector, a decompiler of programs for .NET
 As a guinea pig, I chose Expresso - an analyzer regular expressions. This program It’s free, the license doesn’t seem to say anything about hacking, but without registration it will only work for 60 days. In other words, the harm from hacking this program is minimal, and its internal structure is very well suited for training. I hope that the author of this program will not be offended by me.
As a guinea pig, I chose Expresso - an analyzer regular expressions. This program It’s free, the license doesn’t seem to say anything about hacking, but without registration it will only work for 60 days. In other words, the harm from hacking this program is minimal, and its internal structure is very well suited for training. I hope that the author of this program will not be offended by me.
To start brief educational program according to the structure of the .NET program, for those who are not familiar with development under given Framework: all code written in any .NET language (C#, Visual Basic, F#, Delphi.NET) is compiled into a special Intermediate Language, usually called IL or MSIL. This is something like an assembler, only very smart and with very powerful instructions. And this, in principle, is the same equal language as C#, only the syntax is worse (and there are more possibilities). In addition, the .NET program actively uses metadata, i.e. all information about classes, methods, properties, attributes and everything else is saved in the executable file.
Those. in fact, decompiling a program is not a very correct concept in this case. She's already all in open form lies, and tools in the form of Reflector are engaged in converting MSIL constructs to the corresponding constructs of C# or another language, increasing the readability of the code.
Let's move on to the actual hacking.
0. Trial reset
Actually, this is not even a hack, but a semi-legal way to extend the life of an inactivated program. It consists in the fact that there is a place where the date of the first launch is stored and changed/destroyed. After this, you can still use the program until the next deadline.Let's look at our test subject with a reflector:
After walking through the code a little, we find an interesting line in the MainForm constructor 
Open the registry editor, go to HKEY_CURRENT_USER\Software\Ultrapico\Expresso and see the following keys: 
We delete them and get another 60 days of work.
This option, of course, is simple and obvious, but even if it were more complicated, it would take a little more time in the reflector to find out all the places where information is written and clear them.
Advice to developers who will try to write data to a hidden place: write more carefully, otherwise everything can turn into problems ordinary users, who for some reason will not have this place, or there are not enough rights to it.
1. Writing keygen
The most terrible option for the developer, and the most pleasant for the end evil user. The program considers itself licensed, no scary gestures need to be made.We open the reflector and look for the code for classes containing License or Registration, we see: 
When you enter a name and code, a hash is calculated by name and compared with the code.

This hash uses DES and all sorts of prefixes

Bytes are converted into a string using this method.
Now everything is clear, open the IDE and copy all the necessary pieces of code (or implement it yourself). All that remains is to find out what the values of Prefix, Suffix and MyDES implementation parameters are. I won’t give them, these are technical details.
As a result, we generate a key for any name and see: 
Bingo!
Protection against keygens is simple and obvious: use some form of asymmetric encryption. Those. make it so that it would be impossible to generate a code without knowing the private key, and given key is located in only one place - with the author of the program.
2. Using a wrapper
Checking the correctness of the license is quite a troublesome and slow task. Therefore, program developers usually check the license once, and then use the resulting flag - valid/invalid (as an option, how valid is it, if several types of licenses are allowed, differing in capabilities). Here you can play on this using the following algorithm:- Indicate to the program that the license has already been verified
- Indicate to the program that the license is correct


There is nothing interesting with the launch, but the check shows that if the program is already registered, then it thinks that everything is fine and does not do further work to determine the correctness of the license.
Let's use this:
Let's do it new project, add Reference to Expresso.exe and run it through ourselves: 
Let's see what happened: 
Well, who would doubt it.
In this case, everything turned out to be simple, but if the author of the program had replaced public properties with private ones, then he would only have had to use Reflection for access and everything would have come down to original problem.
I think it’s clear how you can try to protect yourself from this - check the license periodically, look at the environment from which the program is running, do impossible to install the desired variable.
But all these protections will lead to the attacker using
3. Physical hacking of the program
Everything is getting serious here. The entire program is decompiled into MSIL and then assembled back from it (remember, I wrote that MSIL is the same language as C#?). To decompile, we need a utility from the SDK called ildasm, and for compilation the compiler is from the .NET Framework ilasm.Launch ildasm, open Expresso.exe and save the dump to an .il file. We find the already discussed IsRegistered method and add a little of our code (without labels): 
Then we take ilasm and put everything back together (not forgetting to connect the resources).
What is he doing this code: sets desired name for registration (optional), and returns the status that everything is fine.
To make it clearer, this is how it looks in the reflector, in C# 
Those. It is quite obvious that now everything will be fine: 
A little about the code in MSIL: it is a stack-based machine that has no registers, all operations have the form: push onto the stack required quantity parameters, execute a function that will take the required number of parameters and put the result. Well, and vice versa: set the value of the variable to what is on the stack. To better understand how all this works, I recommend a simple technique: write a small program in a familiar language, compile it, see what happens in MSILe and understand the language constructs.
At the same time, some things in MSIL can be done very beautifully, for example, swapping two variables - 4 nice lines (less in C#, but ugly).
What the attacker sacrifices: the signature of the program, now it is no longer the author’s, but his. In some cases, this is a problem if the program uses many libraries. Then the evil hacker will have to disassemble them all and reassemble them again, but if he copes with this, then he will have “his own” signed version of the program his key.
There is actually little protection from all this disgrace: carry out obfuscation or move part of the logic/security checks into the native code.