Optimal settings for Comodo Internet Security. Installing Comodo Antivirus Free
The products boast such a wide range of computer protection tools as Comodo Internet Security. This free, powerful, convenient, complex antivirus with a pleasant interface would be good for everyone, if not for its settings, which often confuse a novice (and not only) user.
To be honest, the frequently asked question of how to properly configure Comodo Internet Security seems to us to be posed incorrectly, because it all depends on how exactly you are going to use this program, and what is your priority in protection. That is why we decided to pay attention only to the most important issues that concern the majority of users about setting up this antivirus.
Basic installation settings
But before we begin to consider them, let’s say a few words about some of the settings that the user has to deal with when installing the program. First of all, pay attention to the Setup Wizard’s suggestion “Get additional security by switching to a COMODO SecureDNS server.” This checkbox is desirable if it is checked, of course. If you leave it, all your connections will go through special server Comodo, where they will be analyzed and checked for threats; This will also replace your ISP's DNS addresses with Comodo's DNS addresses, which in turn can cause problems with the Internet in general.

You can use this option only after consulting with your provider. In addition, some of the sites that you previously visited may be blocked if Comodo suddenly considers them potentially dangerous.
The second item “Analysis of application behavior” can be left untouched. The third checkbox can be unchecked or left as desired. After installation is complete, the program will prompt you to select the network type. Please note that Home and Working network are internal and therefore, if you plan to work on the Internet, you must select the “Zone” network public access” boldly ignoring all notes.

Okay, okay. Let's move on to general settings. The advanced settings module is divided into two blocks: general settings and security settings. First, let's look at the general settings.


Interface
You don't have to change anything here. The “password settings” option is useful only if other people actively use your computer. You can also leave the update and logging settings unchanged.

Configuration
If real-time system protection is a priority for you, we recommend changing the configuration to proactive Security. If the main emphasis is on protecting your computer while surfing the Internet, you should leave Internet configuration Security.
It is also possible to exclude programs ( executable files) and processes. Please note that this setting (exceptions) applies to all types of scans, including real-time protection.


Defense+. HIPS Settings
So, HIPS or host intrusion protection. Using this technology will increase the level of system security. Without going into details, HIPS can be defined as a technology that allows you to create rules that regulate the behavior and determine the rights of any applications.
And HIPS technology can also be compared with controlling network access. HIPS works based on proactive protection. It means that this technology does not use virus databases, it either prohibits something or allows it.
If you decide to use host intrusion protection, we recommend that you first switch the program to training mode. As you work on your computer, the program will ask you various security-related questions, and you will answer them. Thus, the program will learn how to properly respond to certain actions. If you are absolutely sure that your computer is clean, you can set the “Clean PC” mode. In this case, monitoring will only occur if there are any subsequent changes to the system.

If you suspect the presence of malicious objects in the system, you can switch to safe mode. When switching to paranoid mode, almost all changes on the computer will be monitored. You can clarify what exactly will be monitored by clicking on the “Monitoring Settings” link. We also recommend checking the boxes as shown in the screenshot above.


HIPS Rules
This subsection lists all the rules installed by default in Comodo Internet Security. It is not necessary to change these settings. The same applies to the “Rule Sets” subsection.



Protect files, registry and COM interfaces
All files that are protected by default are listed here, important keys registry, as well as COM interfaces. In most cases none additional actions on the user side is not required here. However, if desired or necessary, you can add selected files, groups of files, folders, processes, as well as hives (or individual keys) of the system registry.



Behavioral analysis
This feature is designed to protect your computer from possible infection at startup suspicious programs. This means that a program identified by Comodo Internet Security as suspicious or unknown will automatically run in the sandbox. The default mode for processing unverified applications is “Partially Restricted”. It is not necessary to change it. Also pay attention to the “Do not block files from this list” option. Here you can set exceptions for trusted files and processes.



Sandbox
But here it’s the other way around, you can forcefully specify which applications should be launched in virtual environment. At the same time, it is also possible to set the restriction level for the application (restricted, untrusted, suspicious, etc.), as well as the size of memory allocated to the application and its operating time. The remaining settings can be left unchanged. We set the password for the virtual kiosk as desired.



Free (installer). First of all, you need to decide for what purposes you will use this program. If Comodo Internet Security rus will be used as an antivirus at the same time, then both programs that previously performed these functions for you should be removed. Before deleting, be sure to disconnect from the Internet. It is also better to disable the standard Windows Firewall. Double click on the installer cispremium_installer.exe to start the installation.
The program will automatically select the Russian language, if this suits you, then click OK.
In the next window you can leave everything as is.
 But, it’s better to activate the checkbox in the first line before Change DNS settings servers... Click on Installation options. Uncheck the box before Install COMODO GeekBuddy. If you already have good antivirus, and Comodo Internet Security will only be used as a firewall, then you should uncheck the Install COMODO antivirus.
But, it’s better to activate the checkbox in the first line before Change DNS settings servers... Click on Installation options. Uncheck the box before Install COMODO GeekBuddy. If you already have good antivirus, and Comodo Internet Security will only be used as a firewall, then you should uncheck the Install COMODO antivirus.

Click Back, and in the previous window click on Agree, Install.
After installation you will be prompted to reboot.

We humbly agree.
After reboot, if you see a window like

don’t be alarmed, you’re just disconnected from the Internet and the program, having encountered an unfamiliar application, cannot request the “cloud” (database on remote server) about the trustworthiness of this application. With an Internet connection, such questions will be asked relatively rarely. Therefore, immediately connect to the network, check the box in front of Send files for recognition to COMODO, uncheck Remember my choice and click on Block(this should always be done when you are not sure that you are dealing with a good program, in in this case this is ToolbarUpdaterServicek.exe). Even if you make a mistake, everything can be corrected later. After connecting to the Internet, the update will start immediately antivirus databases, after which you will be prompted to scan your computer. If you have used antivirus programs before, then understanding the antivirus functions will not be difficult. Comodo Internet Security starts working normally already with settings, set by default. If you do not have sufficient experience, then it is better not to change anything. Newcomers are often confused by firewall messages like:

It doesn't matter if you don't know what to do. In such cases, our favorite method of scientific poking comes to the rescue. If you have the slightest doubt, be sure to click on Block and don't put a checkmark in front of Remember my choice. If we made a mistake, we will immediately understand by the result. In this case, the criterion for an erroneous decision would be to stop downloading the file through the torrent client (uTorrent). If there is an error, go to settings. In the lower right corner of the screen in the tray next to the clock we find the Comodo icon (red shield with the letter C)
![]()
Double-click on the icon, the program control panel will appear

Let's go to the tab Firewall


Find the blocked application (C:\Program Files\uTorrent.exe) and double-click on it

In line Action change Blocked b on Allow,click on Apply,we get

Click OK and see if everything works well. If you suddenly get confused with some program, then by clicking on the button Delete(pic above), you can delete the rule for this program and Comodo will start asking its questions again.
When you get a little familiar with the program, I recommend (two clicks on the Comodo icon in the tray? Firewall ?Firewall Settings ? General Tinctures):

Check the box before Create rules for secure applications and uncheck the box before Do not show pop-up notifications.
Don't be afraid of firewall alerts. At first, you can simply ignore them (or even turn them off) if you don’t know what to do. But it is important to start learning how to work with a firewall. Without it, your computer will be dominated by malicious programs controlled by bad people.
This program has such a very useful feature, How . You can get acquainted with a detailed similar program.
More detailed instructions information on working with Comodo Internet Security rus can be found on the page
If you have any questions, please contact us. Good luck in mastering information security!
This lesson is a continuation of the article: Firewall.
So, we found and downloaded latest version Comodo Firewall. Only one firewall can be installed on a computer. Therefore, in order to avoid inter-program conflicts, the built-in Windows firewall must be disabled. You can see how to turn off the firewall in Windows XP and Wiindows 7 in previous lessons: and. But when we install Comodo Firewall, this is not necessary. The Firewall Setup Wizard will automatically disable the built-in Windows firewall.
A firewall controls attempts by applications to communicate on the network. The illustration shows how the firewall intercepted the attempt software Nokia phone to go online. This the right application, so click the "Allow" button:

One of the first to allow connections system components"Windows alg.exe" and "svchost.exe". They are needed to connect to the network. Once installed, Comodo Firewall will issue alerts again and again for various programs. If the application is known to us, we allow the connection request. If there is any doubt and the program seems suspicious, click the “Block” button. By checking the “Remember my choice” checkbox, we confirm our choice for this application. And the next time you connect, the notification window for this program will not appear. You need to act carefully. Only programs known to us can allow connections and secure selections. If you click on the application name, the program properties window will open.
Also, the firewall notifies about incoming connections:

The following illustration shows how Comodo Firewall intercepted incoming package for a popular peer-to-peer client:

At first, the firewall notifications are a bit annoying. But we make our choice and over time there are fewer and fewer of them.
Malicious programs can disguise themselves as harmless software in order to deceive the firewall and gain permission to connect. Therefore, you need to regularly scan your machine with an antivirus program. You can read more about choosing and working an antivirus.
Let's move on now to the firewall settings.
Open Comodo Firewall like any other application, double click by desktop icon or notification area icon. The main program window appears with open tab"Summary":

This displays traffic information and system status. By clicking on the connection numbers, you can view details of active network connections. Clicking the "Stop all connections" button will stop all network activity. This function can be used in case of inappropriate system behavior - suspicion of interference with the operation of programs. For example, the system freezes for a long time and does not respond. This may be a consequence of the network activity of some malicious application. By blocking traffic, you can find out the reason and identify the program that poses a threat. All connections are turned on by clicking the same “Restore all connections” button.
The firewall operating mode can be changed by opening the drop-down list with the " Safe mode".
"Block all" is a mode that does not allow any network activity - the equivalent of the "Stop all connections" button.
"User Policy" is hard mode, in which firewall will display an alert for each program connecting to the Internet. Here, you need to create program policies yourself - clearly understand which applications can be allowed to connect.
"Safe Mode" is installed by default and is universal. The firewall applies user policies - it carries out user settings for individual programs, and also allows network traffic to applications that it considers safe. There will be few notifications and the firewall will not be too distracting.
We assign “training mode” when you need to observe various applications without interfering with their work. Here, Comodo Firewall independently determines program policies without displaying any alerts.
In Inactive mode, the firewall is disabled. You have to turn off the firewall in case of an obvious inter-program conflict, for example, with an anti-virus program or another firewall.
On next tab"Firewall" contains firewall settings. "Firewall Event Log" - the "log" reflects all events - the firewall's reactions to the network activity of various programs.
"Add trusted application" allows you to select the desired application and add it to the allowed ones.
“Add blocked application”, on the contrary, makes it possible to add the selected application to those blocked for connections.
Section "Policies" network security" opens a window where you can select one of the predefined application policies or create your own.
In the "Active" window network connections"programs showing in this moment network activity.
"Master of Hidden Ports" - with these settings you can hide specific ports and make the computer invisible on selected networks.
"Firewall Settings" is a window for selecting an operating mode, duplicating the drop-down list on the "Summary" tab. Also, set the “Safe Mode” slider and check the “Create rules for safe applications” checkbox:

The next tab, "Protection +", contains functions for managing proactive protection. When installing a firewall, proactive protection is enabled by default. Proactive protection is another layer of protection that controls the behavior of programs and prevents infection of the system. Proactive protection settings are basically similar to firewall settings.
The "Run program in Sandbox" item allows you to run dubious application in a kind of “sandbox”. Working in isolation in this protected area, malware cannot harm the system:

The "Proactive Defense Settings" item opens a window of proactive defense operating modes. And, briefly, let's go through these settings.
The "Paranoid" mode implies a paranoid suspicion of protection towards any network activity. Proactive protection will issue an alert every time any application attempts to establish a connection.
In safe mode, protection applies policies user installed, and also allows applications that it considers safe to be active.
In Clean PC mode, protection unconditionally trusts all programs installed on the computer and requests connection permissions only for newly installed applications.
"Training mode". In this mode, the protection does not issue alerts and performs monitoring independently.
"Protection disabled." In this mode, proactive protection is disabled. There is no need to disable protection. The optimal solution protection will be set to safe mode.
On the "Miscellaneous" tab there are additional settings firewall. You can watch them yourself. The review turned out to be voluminous. The main thing is that Comodo Firewall is a very reliable, flexible, Russian-language and free firewall. Comodo Firewall combined with a good antivirus program will provide comfortable and safe work online.
In detail, about work and choice antivirus program read .
Getting to the settings is quite problematic, since there is no button of the same name. However, on the menu Tasks did you see the button Advanced settings(Sandbox Tasks and Advanced Tasks), by clicking which you can get to the parameters window (Fig. 4.99).
Rice. 4.99. Advanced settings
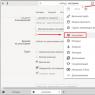
The window is divided into two parts: on the left are settings categories, on the right are changeable parameters. There are only two categories: General settings And Security Settings(Fig. 4.100).

Rice. 4.100. General settings
IN General settings there are four subcategories.
Interface. In this subcategory you can change the program language, as well as configure visual and sound parameters. To do this, check the boxes next to the appropriate parameters. The more of them are enabled, the more often the program reminds you of its presence on the computer. Separately, it should be noted that you can block access to program settings using a password. To do this, check the Protect settings with a password checkbox, click on the Set password link and enter your password in the window that appears.
Updates. It's about about updating both the anti-virus databases and the program itself. This is where you can configure the frequency of checking for updates (Fig. 4.101).
Journaling. You can disable logging or, conversely, enable it.
Configuration. The subcategory is responsible for protection priorities. By default, COMODO is selected - Internet Security, which is sensitive to threats from the Internet. If you spend a lot of time on the Internet, then don't change anything. COMODO - Proactive Security focuses on protecting from within. Select it if your computer had a large number of viruses. COMODO - Firewall Security only conducts network protection(firewall). To change the configuration, double-click on the required item (Fig. 4.102).

Rice. 4.101. Setting Up Updates

Rice. 4.101. Setting Configuration
The default security settings are set to very high level(Fig. 4.103). The only thing you can do is lower the protection and exclude it from scanning separate files. These settings are unlikely to be useful to the average user, so we will not dwell on them in detail.

Rice. 4.103. Security Settings
CHECKING YOUR COMPUTER
You can start scanning in the main window using the button Scan. You can also use the button Tasks ( General tasks Scan). In the window that opens, select the scan type (Fig. 4.104):
Quick scan - checks areas of the computer that are susceptible to infection;
Full scan - scans all files on the computer;
Custom Scan - scan individual files or folders ( Custom Scan Scan Folder or Scan file)(Fig. 4.106).

rice. 4.104. Scan profiles


Rice. 4.106. Custom Scan
In addition, you have the opportunity to create your own profile. To do this in the menu Custom Scan click the button Other options, in the window that opens, click the button Add(Fig. 4.107).

Rice. 4.107. Creating a Scan Profile
In the next window (Fig. 4.108), give the profile a name and add scan objects: individual files and entire areas (tab Objects). On the tab Options select the thoroughness of the check. The more checkboxes you check, the more thorough the check will be. In the tab Schedule set the time and frequency of this type of scanning. Click OK.

Rice. 4.108. Setting up a scan profile
Now in the window Scanning(see Fig. 4.104) the created object scanning profile will appear. Check the box to activate it, and the antivirus will begin scanning at the scheduled time.
To summarize, it should be noted that COMODO Antivirus is highly effective. He copes well with the task assigned to him. The disadvantages include a not very clear interface.
As they say, the flight is normal, only the product is paid and after 30 days it will stop working and ask for money. Tell me, is there any free firewall of the same quality?
Hello friends! Today's article is about popular and free Comodo firewall Firewall.
Security software from the developer company Comodo Group has gained popularity in the software market due to the presence of software products three important components - a popular field of application, simplicity and convenience of the interface, as well as free distribution. It is especially worth noting the flexibility of the developers’ approach. So, software package to protect your computer, consisting of an antivirus, firewall, Sandbox and other modules can be installed either entirely or selectively, installing only individual modules either Comodo AntiVirus or Comodo Firewall. It is the latter that will be discussed in more detail below. Let's look at the features of the Comodo Firewall, how to install this program and how to configure it.
Tasks and features of Comodo Firewall
Comodo Firewall, despite the fact that the product is free, provides full protection computer from network threats. Moreover, he has more than once become the winner of various tests conducted by Internet software resources in order to identify the best software solution class "Firewall". Comodo Firewall is able to protect against attacks from hackers and malware spreading over the network at the same level as paid advanced firewalls such as Outpost Firewall Pro. To put it simply, you won’t find software of the same quality and especially free on the market..
Comodo Firewall analyzes suspicious activity of programs on your computer and checks all their active components, blocking the launch of anything that could harm your computer. Thanks to the Stealth program mode Mode computer is made invisible to port scanning by malware. Comodo Firewall automatically detects the trusted zones of your computer, that is, those folders and files that are authorized to be shared over a home or local network.
Unlike its counterpart, which does not work well with every antivirus on the same system, Comodo Firewall is more loyal in this regard. Even if you do not like the specificity or effectiveness of the Comodo AntiVirus antivirus module, you can install any other antivirus, since Comodo Firewall, as a rule, does not conflict with third-party security software.
Several operating modes and flexible settings Comodo Firewall will allow you to configure the desired firewall behavior for both beginners and more experienced users.
Installing Comodo Firewall
Run the downloaded installer Comodo programs Firewall.

The installation process is somewhat different from the standard one, since it initially involves setting some parameters for the program. After selecting the program language, we will see the installation wizard window, where you need to select some options. It is not necessary to indicate your email.
You can leave all the preset options without changing anything only in the following cases:
When it comes to productive computer or laptop and high-speed Internet connection;
You fundamentally want to participate in the improvement of security software, in particular Comodo products, so that the company improves user protection;
You don't trust your ISP's DNS.

A window will open with options for installing the program, where the developer, hoping that you will quickly complete the installation and not delve into the installation settings, has prepared in addition to Comodo firewall Firewall automatic installation of two more programs - this is the client technical support from the developer Comodo GeekBuddy and a browser with enhanced protection for web surfing Comodo Dragon. There is no point in contacting the first program for those who do not know in English and is not going to finish free period pay for technical support from Comodo. Another program - Comodo browser Dragon on Chromium-based– you can download it for free on the Internet and install it at any other convenient time when the question arises about changing your browser.

Now you can safely press the “Forward” button.

In the next window, we are forced to install Yandex elements along the way and the omnipresence of this search engine in the browser. Let's refuse this service, since it can hardly be called a missed opportunity in life. Click the start installation button below.

The program will install. After launching it, we will see that the computer needs to be restarted. Click the “Fix” button.

Launching Comodo Firewall
The computer will reboot, and we will find a lot of Comodo Firewall windows on the desktop - information about Comodo technologies, a program gadget and a window presets firewall, where we need to indicate which network the computer is connected to - home, work or a network in public place, for example, with a Wi-Fi access point.

After this, Comodo Firewall will minimize to the system tray, from where the program interface can be called up at any time.

For any actions performed on the computer for which the firewall has not yet created a rule, you need to give it approval, unless, of course, we are talking about an unauthorized launch.

Approve every unknown Comodo to run on your computer Firewall programs This will have to happen until the firewall develops rules of behavior for each of the programs it runs. Of course, at first you will have to tinker, but this is actually small fee for the ability to control network connections.
Setting up Comodo Firewall
Comodo Firewall is designed for a wide range of users, including beginners, and the computer will be safe even with the settings preset by the developer. But more experienced users will probably find it interesting to use Comodo features Firewall for enhanced protection computer.
We launch the firewall using its shortcut in the system tray. In the main window that opens in front of us, we see the program status - the computer is protected. We also see the number of network intrusions, the number of blocked intrusions, and software updates.

Using the button on the left top corner We can switch to the program displaying a detailed summary. And then return to the summary view again.

In the main window of Comodo Firewall there is an option " Game Mode" Game mode is essentially full screen mode not only in games, but also when watching videos, as well as in any other applications that are displayed in full screen. When switching to this mode, the firewall will not bother us with its notifications and will make all decisions itself.

To open advanced firewall settings, in the main Comodo Firewall window with a detailed summary, click the “Firewall” link.

Will open detailed settings firewall, where you can change certain preset parameters.

You can, for example, at the top of the settings window change the preset “Safe Mode” of the firewall when it is allowed network activity programs that are in the list of trusted ones, and Comodo Firewall does not switch to other modes on every occasion. For example:
“Full blocking” - in this mode, any network activity is excluded. This mode is simply irreplaceable if your computer is infected with a virus.
“Custom set of rules” - as the name of the mode implies, it provides for strict control and user participation in decision-making for each network request for which there are no previously defined rules.
“Learning mode” - in this case, Comodo Firewall does not interfere with the activity of running programs, but only monitors events.