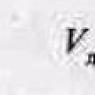Firewall (Firewall, firewall). What is Windows Firewall - its settings and use
Network or firewall is a set of software and hardware that provides information protection to one part of a computer network from another by analyzing the traffic passing between them.
There are other terms for firewalls that well reflect the functional purpose of this type of protection:
- Firewall - this word came into the Russian language from German many years ago. Initially, it designated a partition on a train, separating the firebox area of the locomotive from the passenger compartment.
- Firewall and other transliterations of the English word firewall, although not officially accepted, can be found in literature quite often. The original meaning of this term is a structural element of a house, namely a wall made of fire-resistant material that prevents the spread of fire between parts of the house (usually belonging to different owners).
For a firewall, one part of the network is internal, the other is external (Fig. 1). A firewall protects an internal network (for example, an enterprise's local network or, as a degenerate case, a user's individual computer) from threats emanating from an external network (we will, as a rule, mean the Internet by such a network).
Protection of the boundaries between enterprise local networks and the Internet is provided by corporate firewalls; the same functions, but at the border between the home computer and the Internet, are performed by personal firewalls.
For a firewall to effectively perform its main function - protection - it is necessary that all traffic exchanged between nodes of the protected part of the network and Internet nodes pass through it.
This arrangement allows the firewall to fully control (prohibit, restrict, or log) external user access to internal network resources. A firewall protects the network not only from unauthorized access by external intruders, but also from erroneous actions of users of the protected network, such as transferring confidential information to an external network.
Rice. 1. A firewall protects the internal network from threats emanating from the external network
To implement access control, the firewall must be able to perform the following functions:
- analyze, monitor and regulate traffic (filtering function);
- play the role of a logical intermediary between internal clients and external servers (proxy server function);
- record all security-related events (audit function).
Along with these basic functions, the firewall can also be assigned other auxiliary protection functions, in particular:
- antivirus protection;
- traffic encryption;
- filter messages by content, including types of files transferred, DNS names and keywords;
- prevention and detection of intrusions and network attacks;
- VPN functions;
- network address translation.
As you can see, most of the listed functions are implemented as separate products or as part of other types of protection systems. Thus, packet filtering functions are built into almost all routers, the task of detecting viruses is solved by many different programs, traffic encryption is an integral element of secure channel technologies, etc., etc. Proxy servers are often supplied as applications, moreover, they themselves often integrate many of the functions inherent in firewalls, such as authentication, network address translation, or content filtering.
This is where difficulties arise when defining the concept of “firewall”. For example, it is quite common to think that a firewall is an edge device that performs packet filtering (that is, a router), and a proxy server is a completely different security tool from a firewall. Others insist that a proxy server is an indispensable and integral attribute of a firewall. Still others believe that a firewall can only be called a software or hardware device that is capable of monitoring the state of the packet flow within a connection. In this book, we will adhere to the widely accepted point of view that a firewall is a software and hardware complex that performs a variety of functions to protect the internal network, the set of which may vary depending on the type, model and specific configuration of the firewall.
How to open a firewall and what to do next
Before setting up the firewall, you need to go into it and open it. In Windows, this is done through the Control Panel, which can be accessed through the Start menu; the firewall can be easily found by the globe icon behind the brick wall. In Kaspersky Anti-Virus, you can access the firewall settings using this path: Settings (at the bottom of the screen, just to the right of the center) - Protection Center (left) - Firewall (right). If the firewall is a stand-alone program, it can be opened by double-clicking, like all programs. So, how to open a firewall depends on whether it is a separate program or a component of a more complex system.
When the firewall window is open, you can enable or disable it and configure it. If the firewall, also known as the firewall, is disabled, the issue of settings is removed. But you should disable it only if a more powerful firewall is installed and used; quite often this is done with the standard Windows firewall to avoid conflict with another firewall. If the firewall is turned on, you can go to settings that differ from program to program.
Protecting your computer Yaremchuk Sergey Akimovich
Firewall settings settings
To activate the firewall, just click the link Turn on on the corresponding tab. The parameter settings window can be called up by pressing the button Settings at the bottom of the window and selecting the appropriate item or from the appropriate menu item Protection. Clicking the link View current network activity, you will display the number of active applications using the network, as well as the number of open connections and ports.
There are several areas available in the module settings window, in each of which you can enable/disable by checking the appropriate box Firewall completely or one of its components - a filtering system, an intrusion detection system, Anti-Advertising or Anti-Banner(Fig. 5.2). In the firewall settings area there is a slider, using which you can set one of five levels of protection:
Allow everything– any network activity is allowed without restrictions, corresponding to disabling the firewall;
Minimum protection– all network connections are allowed, except those prohibited by the rules;
Training mode– the user independently decides what network activity to allow or prohibit; when trying to access the network of an application for which a rule has not been created, the user is asked for confirmation and a new rule is created based on the response;
Maximum protection– all unresolved connections are blocked;
Block everything– all connections are blocked, access to the local network and the Internet is prohibited; must be used in case of detection of network attacks or when working in a dangerous network.
Rice. 5.2. Firewall module settings
During installation, rules are created for all applications, but they are not always optimal for a particular system, so it is recommended to change the protection level from the default minimum to training. You should switch to maximum protection mode only if you are sure that all allowing rules have been created. However, after installing new software, you should return to training protection mode again. When the system is operating in training mode, the user is notified (Fig. 5.3).

Rice. 5.3. Network Activity Notification
It contains a description of the activity and information necessary to make a decision: type of connection (incoming, outgoing), protocol, application, remote IP address and port, local port. Based on the received data, you can select the desired action by clicking the corresponding button - Allow or Prohibit. Selecting an option Disable training mode will disable this mode of operation of the module.
If the checkbox is checked Create a rule, then a new rule is generated based on the selected response, and during subsequent network activity of this application, if the request parameters match, the program will not bother the user. In the drop-down list, you must select the activity type to which the selected action applies. Several options are available:
Any activity– any network activity of this application;
Selectively– a specific activity that should be specified in the rule creation window;
This address– activity of an application whose remote network connection address matches the specified one; can be useful if you want to limit the network activity for a selected application to specified addresses.
You can also select one of the presets that describe the nature of the application: Mail program, Browser, Download Manager, FTP client, Telnet client or Clock synchronizer.
Component Intrusion Detection Module Firewall responds to activity typical of network attacks. If an attempt to attack a computer is detected, a corresponding notification will appear on the screen indicating information about the attacking computer: type of attack, IP address of the attacker, protocol and service that was attacked, date and time. In this case, the system blocks the IP address of the attacking computer for one hour. You can change the blocking time in the area Intrusion detection system in the field next to the checkbox Add the attacking computer to the blocking list on.
From the book Business Way: Yahoo! Secrets of the world's most popular Internet company by Vlamis Anthony From the book Computer 100. Starting with Windows Vista author Zozulya YuriPage Setup Settings Before you print a document, you should set the optimal page settings for it. To configure these parameters, use the Page Options and Page Background command groups on the Page Layout tab (Fig. 5.55). In the group
From the book Adobe InDesign CS3 author Zavgorodniy VladimirSettings for working with files The File Handling section (Fig. 7.16) contains some settings for saving files and using the clipboard when working with several programs at the same time. Rice. 7.16. InDesign File Handling SettingsDocument Recovery Data Area
From the book AutoCAD 2009 for students. Self-instruction manual author Sokolova Tatyana YurievnaSettings for working with the clipboard The Clipboard Handling section (Fig. 7.17) allows you to set settings for working with the Windows clipboard; Depending on these settings, Adobe InDesign will interact better with other Adobe programs (with a focus on
From the book Setting up Windows 7 with your own hands. How to make work easy and convenient author Gladky Alexey Anatolievich From the book Self-instruction manual for working on Macintosh author Sofia SkrylinaSetting screen parameters Using the link Optimizing the image on the screen (see Fig. 2.47), you can switch to the mode of additional adjustment of screen parameters for people with disabilities (Fig. 2.49). Rice. 2.49. Setting up additional
From the book Linux: The Complete Guide author Kolisnichenko Denis Nikolaevich3.3. How to change screen settings? To change the resolution, brightness, number of colors, select a profile and calibrate the monitor, use the Color LCD dialog box, which is called up by clicking on the Displays mini-utility icon located in
From the book Linux author Stakhnov Alexey Alexandrovich6.2.4. Checking the operation of the network interface If you did not raise (activate) the interface during the graphical configuration process, do it now. Go to a text console or open a terminal window and run ifup eth0 (you can deactivate the interface
From the book AutoCAD 2009. Training course author Sokolova Tatyana Yurievna19.3.3. Viewing network device parameters The ip link show command is best viewed through examples. To obtain information about the status of the eth0 device, enter the command:# ip link ls dev eth0eth0: mtu 1500 qdisc cbq qlen 100link/ether 00:44:67:91:31:1d brd ff:ff:ff:ff:ff:ffGet device statistics eth0 is possible
From the book AutoCAD 2008 for students: a popular tutorial author Sokolova Tatyana YurievnaAppendix 4 Kernel Configuration Tree This appendix shows the Linux kernel configuration tree with the default settings in the Red Hat Linux 7.2 distribution. Conventions used: [*] – compiled into the kernel; – does not compile;
Setting the home screen options On the Display tab of the Options dialog box, shown in Fig. 3.2, you can configure the parameters of the AutoCAD work screen. Rice. 3.2. Dialog box for setting up working screen parameters In the Elements area of the window, Window Elements are configured
From the book Undocumented and Little-Known Features of Windows XP author Klimenko Roman AlexandrovichSetting the home screen options On the Display tab of the Options dialog box, shown in Fig. 3.2, you can configure the parameters of the AutoCAD work screen. Rice. 3.2. Dialog box for setting up desktop screen settings In the Elements area of the Window Elements window
From the book Linux through the eyes of a hacker author Flenov Mikhail EvgenievichNetwork Connection Security Many messages between a client and a server carry information that can be quite easily obtained by someone eavesdropping on network communications. For example, an encrypted password can be obtained and used to
From the author's bookStoring console settings Another thing worth mentioning is storing console settings. If you think that console settings are stored in the registry, then this is not true. In fact, all console settings are contained in the console files themselves. This is easy to understand using the console example,
From the author's book3.6.3. Changing network connection settings Using ifconfig, you can not only view network connection settings, but also change them. To do this, you need to specify two parameters:? network interface whose parameters need to be changed;? parameters. General view of the command
From the author's book4.13.2. Bypassing a firewall A firewall cannot provide absolute security because its operating algorithm is imperfect. There is nothing flawless or 100% reliable in our world, otherwise life would be boring and uninteresting. How a Firewall protects your computer
What is a firewall? This is the name for applications designed to protect a computer from unwanted traffic and malware from entering the network. This is a protective system, like a wall, standing between the network adapter and the operating system. Therefore, these programs are often called firewalls or firewalls. In its original meaning, a firewall is a wall that separates and protects an adjacent building from the spread of fire. Any network packet is checked by a firewall before being processed by the operating system. And any outgoing data packet must pass its control. This means that a firewall is not a solid wall, but a specially configured program that filters incoming and outgoing traffic.
When we work online, we use various applications. Each application needs access to a certain type of traffic. For example, browsers require port 80 for the outgoing TCP connection and port 53 for the DNS server. ICQ clients need port 5190 for outgoing TCP connections. If we close port 44583, we will not be able to use Skype. It is precisely the firewall that controls these and all other computer ports for incoming and outgoing traffic. That is, it opens the corresponding ports only to applications allowed by the rules. And we can set these rules ourselves when we set up a firewall. Let's assume we have allowed the Opera program to work. This means that incoming and outgoing traffic for this application will be allowed through the firewall. If, however, network packets come from a program that we have not given permission to operate, the connection will be blocked. When you first launch any application that requires access to the network, the firewall displays a request dialog box. And here, we ourselves decide to give access or not.
Firewall is the first and main means of protecting your computer from network intrusions. And it must be configured accordingly.
If we work in an office and are connected to the company's local network, we have nothing to worry about. The system administrator will provide reliable protection and there is no need to configure a personal firewall on your machine. It’s another matter when we directly access the global network. In this case, a firewall must be installed. And it must be enabled and configured.
The operating system of a completely unprotected computer can be completely disabled in just a few hours of active Internet surfing. Such experiments were also carried out. The firewall will stop some intrusions - it blocks unauthorized connections.
A proprietary firewall is built into Microsoft Windows systems starting from Windows XP SP2 and higher. Let's read the lesson: Windows XP firewall and see how to enable it and configure it.
Using examples of built-in Windows protection tools, we became familiar with the principles of operation of firewalls - firewalls. A reliable firewall controls more than just incoming network packets. It should also record all outgoing traffic. And block packets emanating from malicious programs, if such programs have nevertheless penetrated the computer and are trying to send stolen information. For example, the Windows XP firewall does not work on outgoing connections. Here, you should consider installing a third-party firewall. What can you recommend?
According to the results of tests by authoritative independent laboratories dealing with the problems of protecting personal computers, Comodo is recognized as the best firewall. Comodo Firewall is a free personal firewall from the American developer Comodo Group for Windows XP, Vista, Windows 7 and 8. You can download the latest version of the firewall from the developer’s official website.
Let's move on to the lesson: setting up Comodo Firewall and see how to install and work with this firewall.
Firewall (Firewall)
Is antivirus software enough to protect you from bad guys and pests? No. There is a second line of defense - a firewall. Its main purpose is to limit the network activity of your computer and control the network connections being established.
A little theory.
Your computer has at least one network adapter through which you connect to the network (Internet, local network). We will call him network interface. One computer can have several network interfaces, not only physical, but also virtual. For example, when a VPN connection is established, the virtual private network adapter is activated.
In order for a computer to communicate with the world, it is necessary to determine the method of this communication - a protocol currently adopted on the Internet TCP/IP version 4, version 6 is coming. In version 4, the computer address is specified by twelve digits, which are usually arranged in groups of three (10.8.3.21 = 010.008.003.021). Each network interface corresponds to one network address (and an unlimited number of aliases/aliases). More than one network interface can be configured on one physical device.
Many programs and services are trying to use the network, and at the same time. To reduce the number of conflicts and collisions, a virtual device is organized on the network interface for each of them - a port through which this program communicates with other network partners. There are ports known, registered and dynamic. The known ones - the first thousand (1023) - are standard, each of them is assigned to a specific service by international agreement. The next 48 thousand (up to 49151) are also regulated by international agreements, but are assigned for private purposes. All ports with high numbers can be used by any programs and services. In general, all ports with a number greater than 1024 can be considered dynamic, since no one really monitors their use.
There are also two subtypes of IP protocols - UDP and TCP. The UDP protocol does not monitor the correctness of data transmission; it is used more often in the operation of services.
What happens when you try to visit a google.ru page? Your browser opens a dynamic port and sends a network packet from it requesting to establish a connection. The packet header contains Google's network address and the standard web server port - 209.85.229.104:80. Google's web server keeps port 80 open and listens on it. Your browser connects, and further exchange of network packets will occur between your dynamic and Google 80 ports.
Everything is very simple and reliable. In this example, we saw that a service (web server) can open and listen on ports. When the package is received, it takes effect. If this is an attacker's service (for example, a backdoor), someone can gain access to your computer. If this is a normal, regular service that has vulnerabilities, then using a specially configured request you can disrupt its operation or even gain control over your computer. We also saw that the program can open a dynamic port (or many dynamic ports) and establish a connection with some server/computer, which can also be triggered by an unknown bad guy. There is a need to control ports and programs accessing network interfaces. This is what firewalls are for.
Firewalls generally have a table of allowed ports and routes, for example:
| Network address (interface) | port | Remote IP/mask | Remote port | Description |
| 10.8.3.21 | 80 | 0.0.0.0/0 | * | You can connect to port 80 (web server) from any port and address |
| 10.8.3.21 | 21 | 10.8.3.0/24 | * | You can only connect to port 21 (ftp) from the local network |
| 10.8.3.21 | * | 10.8.3.29 | 22 | You can connect to port 22 (ssh) on a computer with the address 10.8.3.29 |
This is a simplified example; usually you also need to specify the protocol (udp /tcp). In addition, a good firewall has a proactive filter that controls whether programs open dynamic ports. In it you can specify, for example, that opera can connect to anything.
Each line in the table is a screen operation rule; all firewall operation is described by such rules. It is quite difficult to write all the rules manually; this requires a lot of patience and a solid amount of knowledge, which is why most firewalls have a training function. When a program tries to establish a connection, the firewall asks the user whether to allow such and such a program/service to connect to such and such an address on such and such a port. The user decides to allow or deny, and can also save his answer as a rule so that such questions do not arise again.
Enough theory, let's move on to practice. Let's start with the standard Windows Firewall (Windows Firewall). Many, or rather all seasoned networking gurus, grimaced with contempt when they heard this phrase. Their skepticism is well founded. The attacker, plotting, assumes that at least a built-in firewall will act against him, while providing ways to bypass it. Also, its functionality is no wider, and in some cases worse, than its free counterparts. However, it is better than nothing at all. So let's get started. Start-Control Panel-Windows Firewall.
Click the “Change settings” button

I already have it turned on, if you don’t, turn it on. If paranoia progresses, you can check the box “Block all incoming connections. This will not prevent you from visiting web pages. Let's go to the second tab "Exceptions".

In the picture you see a list of programs and ports that are allowed to work through the firewall. The problem is that we won't see whether incoming or outgoing connections are allowed. Only when opening a port can we be sure that it is open for incoming connections. What is allowed for programs is a great mystery. At least – outgoing connections. This list is available for editing by the administrator; you can completely remove an entry from the exclusion list, or you can temporarily disable it by unchecking the checkbox. For each exception, you can edit the scope, that is, the remote IP addresses.

But for normal network work there is no need to add exceptions. If the “Notify when the firewall blocks a program” checkbox is checked, you will receive messages about programs attempting to access the Internet and will be able to decide whether to allow it or not; if you indicate “Remember the rule” in the response, it will automatically be added to this list. Some programs add themselves to exceptions during installation. Therefore, a real paranoid person turns to this list only to remove checkmarks from suspicious entries.
Let's go to the "Advanced" tab.

Here we can check off those interfaces that need to be protected. By default, the firewall covers all interfaces.
So, the built-in Windows firewall has sufficient functionality, but the interface is not obvious (Windows 7 has an advanced firewall mode, which allows you to configure rules in more detail), which forces us to use other products. Naturally, only free solutions are accepted for consideration. The most common and characteristic representative of this series of products is ComodoFirewall.
Download and install. Decide for yourself whether to install it together with an antivirus.

After installation, make sure that the Windows Firewall is turned off.
When you start it for the first time, the question will arise whether we trust computers on the local network or not. This means that the computer will be visible in the network environment of other computers on the local network (a zone defined by the network address and mask) and will be able to share its folders and other resources. If you don't know what this means, don't check the box. In any case, we do not check the second box.

We also see Comodo Firewall questions about service activity. For reliable ones, check the box “Remember my answer” and click the allow button. Over time, there will be fewer and fewer such questions.
Let's go to settings. To do this, click the icon in the tray, or through the Start-Programs menu.

The first three points do not raise any questions. Let's look at the example of adding the Far application to the trusted ones for accessing the Internet. Click add a trusted application, find Far manager through the overview, click “Apply” - you’re done.
The fourth point is the master of hidden ports.

The first point allows you to define a trusted zone, that is, a subnet with which network traffic can easily pass through the firewall. The purpose of the second and third points is clear from the picture.
The next interesting item in the main menu is “My port sets”.

These port sets can be used in firewall rules to avoid creating multiple identical lines for different ports.
The “My network zones” item has the same purpose. In other words, these are groups of addresses to which the same rules apply.
The purpose of the last paragraph is clear from his signature.
Now click on the left (Firewall tasks) to the “Advanced” item.


This is the heart of the Chest of Drawers: rules for applications and global rules, that is, rules for everyone. Let's click on any application rule. If you assigned Far manager, as in my example, you will see the following picture:

We see that we have allowed all incoming and outgoing IP protocols from any source address to any destination address, any types of packets. Let’s leave it with only outgoing ones and click “Apply”. There is a wider choice on the global rules tab. Click the “Add” button and write a rule for uTorrent to accept incoming connections on port 51280.

The departure address is any computer on the Internet, the departure port is any, we don’t know from which port it will connect. But the destination address is our IP address on the interface that looks at the Internet (select a single IP and enter our address), the port number is 51280 (we took it from the settings of the uTorrent program). Click apply.
Let's take a closer look at some points. When assigning an IP address, we can select not only a specific range, but also zones that we described in “My network zones”, and when assigning ports - “My port sets” (see above).


The next menu item is Predefined Policies. Here you can specify sets of policies, which can then be applied to applications of the same type. For example, sets of policies for web browsers are already specified there, which will allow you to change only one line in the rules when changing browsers.
The remaining settings are not used so often, and those who are interested in them will figure it out without me.
Conclusion: Comodo Firewall allows you to perform all the filtering settings that interest us, and this does not require any special knowledge. And also, using his example, we examined the main ways to configure firewalls. Now you can close your network interfaces, protecting yourself from external attacks.
Remember, even if you have nothing, there will be people who don’t know it.