Yandex password protection against phishing. Protect technology in Yandex Browser - description of capabilities. How to disable Yandex Protect technology
![]() Protection against phishing (a type of fraud whose goal is to obtain passwords, banking information and other personal information of the user) is present in most popular web browsers. Yandex.Browser is no exception; such protection, using Safe Browsing technologies (essentially a blacklist of unreliable websites), has been working in the browser since its inception.
Protection against phishing (a type of fraud whose goal is to obtain passwords, banking information and other personal information of the user) is present in most popular web browsers. Yandex.Browser is no exception; such protection, using Safe Browsing technologies (essentially a blacklist of unreliable websites), has been working in the browser since its inception.
Protection using blacklists (be it Safe Browsing of Yandex, Google or other analogues) has long remained the only solution. The problem is that, today, the creation of fake sites, their publication, sending spam through social media. networks and so on happens so quickly, due to the automation of these processes, that a new phishing page manages to do enough damage before it ends up in the list of bad sites and is blocked by the browser.
The new anti-phishing algorithm used in Yandex Browser has now become even more effective. In addition to Safe Browsing and password protection, which has been working in Yandex Browser for a year now, a new version browser received technology that protects bank card numbers. This technology is based on Yandex’s developments in the field of machine learning and computer vision.
You can find out in more detail how Yandex.Browser protects against phishing on the company’s official blog on Habrahabr.
The latest version of Yandex.Browser is available.
Browser team Google Chrome encourages all users of this browser to update to the latest version as soon as possible. Yes, let me tell you...
ECS (Elitegroup Computer Systems) introduced the Liva Q2 mini-PC. The dimensions of the new product are only: 70 x 70 x 33.4 mm, weight – 260 grams. A...
In the latest test build of Windows 10 with index 18836 appeared new opportunity, which allows you to interact with Linux subsystem files directly...
Firefox contains built-in Phishing and Malware Protection to help keep you safe online. These features will warn you when a page you visit has been reported as a Deceptive Site (sometimes called “phishing” pages), as a source of Unwanted Software or as an Attack Site designed to harm your computer (otherwise known as malware). This feature also warns you if you download files that are detected as malware.
Table of Contents
What are Deceptive/Phishing, Attack Sites, Unwanted Software and Malware?
Deceptive Site (also known as "Phishing")
Attack Sites
Attack Sites are websites that try to infect your computer with malware when you visit. These attacks can be very difficult to detect; even a site that looks safe may be secretly trying to attack you. Sometimes even the website’s owner doesn’t realize that the site has become an Attack Site.
Malware
Malware is software designed to infect your computer without your knowledge. Malware is most often used to steal personal information, send junk email (spam), or spread more malware.
You can learn more about malware and Attack Sites from StopBadware, a non-profit organization that works with partners like Mozilla to protect users from malware and other dangerous software.
Unwanted Software
Unwanted Software sites are websites that try to trick you into installing programs that harm your browsing experience (for example, by changing your homepage or showing extra ads on sites you visit). You can learn more about such software on the Google Unwanted Software Policy.
How does Phishing and Malware Protection work in Firefox?
Phishing and Malware Protection works by checking the sites that you visit against lists of reported phishing, unwanted software and malware sites. These lists are automatically downloaded and updated every 30 minutes or so when the Phishing and Malware Protection features are enabled.
When you download an application file, Firefox checks the site hosting it against a list of sites known to contain "malware". If the site is found on that list, Firefox blocks the file immediately, otherwise it asks Google’s Safe Browsing service if the software is safe by sending it some of the download’s metadata.*
*Windows users: This online check will only be performed in Firefox on Windows for those downloaded files that don’t have a known good publisher. Most of the common and safe software for Windows is signed and so this final check won’t always need to happen.
How do I use the Phishing and Malware Protection features?
These features are turned on by default so, unless your security settings have been changed, you are likely already using them. Phishing and Malware Protection options preferences can be found on the Security panelPrivacy & Security panel:
To turn these features off, follow the preceding steps to return to the Security panel and remove the check marks.
To turn these features off, follow the preceding steps to return to the Privacy & Security panel and remove the check marks.
To see if Phishing Protection is active, visit our phishing test site. Likewise, you can visit our malware test site to confirm that Firefox is blocking Attack Sites as well as our unwanted software test site. With Phishing and Malware Protection turned on, all these sites should be blocked from loading.
What happens when a page or file is blocked?
Firefox will block the page from loading and display a Receptive Site warning for phishing sites, Reported Unwanted Software Page for unwanted software sites and Reported Attack Page for malware sites.
If you download malware or spyware, Firefox displays a message about the file in the Downloads panel.
Unblock.
If you download malware or other software that is potentially unwanted or uncommon, Firefox displays a message about the file in the Downloads panel.
To ignore the warning and download such a file, right-click on it in the Downloads panel and select Allow Download.
What information is sent to Mozilla or its partners when Phishing and Malware Protection are enabled?
There are two times when Firefox will communicate with Mozilla’s partners while using Phishing and Malware Protection for sites. The first is during the regular updates to the lists of reporting phishing and malware sites. No information about you or the sites you visit is communicated during list updates. The second is in the event that you encounter a reported phishing or malware site. Before blocking the site, Firefox will request a double-check to ensure that the reported site has not been removed from the list since your last update. This request does not include the address of the visited site, it only contains partial information derived from the address.
In addition to the regular list of updates mentioned above, when using Malware Protection to protect downloaded files, Firefox may communicate with Mozilla's partners to verify the safety of certain executable files. In these cases, Firefox will submit some information about the file, including the name, origin, size and a cryptographic hash of the contents, to the Google Safe Browsing service which helps Firefox determine whether or not the file should be blocked.
The Mozilla Privacy Policy describes what data Firefox and Mozilla each receive and how it"s handled. The Google Privacy Policy explains how Google handles collected data.
I’ve confirmed that my site is safe, how do I get it removed from the lists?
If you own a site that was attacked and you have since repaired it, or if you feel that your site was reported in error, you can request that it be removed from the lists. We encourage site owners to investigate any such report thoroughly, though; a site can often be turned into an attack site without any visible change.
Attentive users Yandex.Browser we immediately noticed that the browser received a new, slightly modified logo, but this is not the most important thing - the key innovation in the latest version of the browser from Yandex is the active protection technology called Protect. And browser users are already looking for instructions not only on how to enable, but also how to disable Protect in the Yandex browser.
Protect technology consists of several protective components:
- password protection;
- protection in public network Wi-Fi;
- blocking suspicious fraudulent resources;
- checking all downloaded files.
Protect browser protection
Protect provides users with timely protection, which practically does not need to be managed - Yandex browser will do everything itself. The main goal development is to prevent the occurrence of threats, and not to eliminate their consequences: 

How to disable Yandex Protect technology
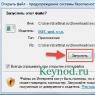
Yandex's Protect technology has just been introduced into the browser, and the developers have already promised that new mechanisms will be introduced in the future that will combat other threats. But despite its benefits, users also noticed that the browser often blocks sites that do not pose threats. Not everyone is happy with this state of affairs, so I decided to try disabling protection Protect Yandex. To turn off the Protect technology, first you need to find the icon in the form of three stripes, and then select “Settings”.

After opening the settings, scroll to the bottom of the page and look for the “Show” button additional settings" Now go to the “Personal Data Protection” settings block and uncheck the “Enable protection against malware", that is, disable Protect protection against malware.

The article talks about what password phishing is, how it is carried out, why it is used by attackers, and how to protect yourself from it.
Start
Just 15 years ago, not everyone could boast of having home computer, and one could only dream of fast and unlimited Internet. Fortunately, they are developing similar technologies very quickly, and nowadays you won’t surprise anyone with having a PC or access to the Internet. From year to year digital technologies are becoming more accessible, simple and attractive. Almost all enterprises, institutions and organizations have switched to electronic document management, and the range of services provided via the Internet is constantly growing and expanding.
All this leads to the fact that more and more important personal or classified information. For example, data electronic wallets, passwords for them, etc. Naturally, all this attracts attackers, and for a long time no one will be surprised by stories about how hackers are hired to “take down” a competitor’s website or obtain compromising information.
In addition to the listed values and information, attackers are also interested in its intangible component. K and password to the account of some online game, paid service etc. And often, in addition to the usual virus attack, they use a method such as phishing. So what is password phishing and how can you protect yourself from it? We'll figure this out.
Definition

First, let's talk a little about terminology. The word “phishing” came to us from the English language (English fishing - fishing, fishing). As in the case of real fishing, the point of this action is to throw “bait” to the user and simply wait until the latter falls on the hook and “merges” passwords with logins. But what is password phishing and how is it technically implemented?
Unlike Trojans, keyloggers and backdoors, password phishing is implemented more simply, but at the same time more cunning, and often users do not notice the trick at all. So how is this method implemented?
It's actually quite simple. The attacker copies the source code of the page, for example, authorization postal service, and uploads it to his rented hosting, where he, of course, placed his fictitious data. Then it creates the address of this page very similar to the original one, for example, if the real address looks like e.mail./login?email, then the fake one looks like e..mail./login?email. As you can see, the difference is only in one point; you must admit, not everyone will notice it. Also, the fictitious page is configured so that after entering data (login and password), they are saved on the hacker’s website. So now we know what password phishing is.
Naturally, when authorizing, the user will receive an error, but in some cases, in order to further mislead, the attacker creates a script that will report that the login-password combination is incorrect, and the user will be redirected to this page authorization.
Password protection against phishing. What is this?

Now we come to how to protect ourselves from such theft. Firstly, you should never click on suspicious links, especially if these are authorization forms for some services or other services whose data is important to you. Especially if you were already logged in there and the session did not end. Secondly, always pay attention to the page address. Naturally, they make it as similar as possible, but differences still exist. And thirdly, it is important to remember that any device with Internet access that is frequently used must have an antivirus installed, be it a PC, tablet or smartphone. All modern versions can recognize fake pages.
Well, in addition: many services protect themselves from this; this is done with special page code and scripts, because of which their code cannot simply be copied and used as bait.
Mass distribution

This type of fraud became especially widespread about 10 years ago, at that time such a thing as a password phishing program appeared. The point of this software was that with its help anyone could easily and quickly create a copy of a phishing page. Fortunately, now similar programs are of little relevance, since the design of authorization forms and their code often changes to prevent the theft of passwords and logins.
The meaning of theft

Nowadays, the value of electronic data and other information is difficult to underestimate. Criminals also understand this, so they try to get them in every possible way. Moreover, they are interested not only in specific important data, for example, credit card number, passwords for accessing electronic wallets, but also access data to mail, social networks, etc.
So now we know what password protection against phishing means and how important it is.
For example, having gained access to a page on a social network, a fraudster can find out a lot of compromising information about a person and later begin to blackmail him. And the abundance of services for “hide and seek” on the Internet, anonymous payment systems, etc., only simplify this, and it is very, very difficult to catch such a hacker. Although in recent years this has been happening more and more often.
Conclusion
Also on everyone's lips is the popular Lately a type of “scam” when, having obtained the passwords, the hacker, on behalf of the victim, asks her friends to borrow money. So password protection against phishing is important aspect computer security. It is clearly not worth neglecting.
Attackers specializing in theft of passwords, bank card numbers and other personal information appeared in the last century and since then their number has only been growing. According to a report from Kaspersky Lab, between 9% and 13% of their users in Russia experience phishing. Globally, phishing and other forms of identity theft cause $5 billion in losses each year, according to Microsoft estimates. This generally corresponds to our observations and explains why in any more or less popular browser There is protection against phishing based on blacklists. Yandex Browser also has it. It would seem, why invent something else?
Safe Browsing
The most obvious solution to protect users is to use a ready-made database with a list of phishing sites. We check the pages you visit using the “black list” and warn you if a match is found. Protection using Safe Browsing technology, which has been working in Yandex Browser since its inception, is based on this idea.A little about how it works. The Browser regularly updates a list of bad sites weighing several megabytes. In fact, there are a lot of dangerous sites, and the degree of compression is limited, so instead of explicit addresses, we locally store only the prefixes (i.e., the initial part) of their hashes. We check the sites we visit using the local database. If a match is found, then we send the prefix to the server, in response we receive full hashes, we double-check, if there is a match here, then we show a warning. The chain looks long, but it works in a fraction of a second, does not produce requests and, most importantly, protects the user.

Safe Browsing lists are replenished using Yandex search and anti-virus technologies, the details of which should not be disclosed for obvious reasons. However, third-party developers can also benefit from the results in their products (including browsers) using our Safe Browsing API.
Protection using lists of bad sites (be it Safe Browsing from Yandex, Google or other analogues) has long been the only method used in the browser industry. The problem is that modern phishers are not as slow as they used to be. Creating fake websites, publishing them, sending spam through social networks - all this has long been automated. By the time the new phishing page reaches the full database, and then the light local one, it may well have time to harm someone. We had to learn how to deal with the problem in the absence of accurate knowledge.
Password protection
Using phishing, attackers actively steal passwords from banks, payment systems, social networks, and even server management admin panels. How to protect them if the browser does not yet know whether the site is open in it is good or bad? Warn each time you enter a password and ask you to make sure that this is the same site? This is not only intrusive, but also useless in the long term. If a user confirms 100 times that this is a real Sberbank website and not a fake one, then the 101st time he simply will not check the site, which, according to the law of meanness, will certainly turn out to be fraudulent.By the way, there is a common misconception that two-factor authentication on banking websites will save you from money theft, even if a person falls for phishing. It will save, of course, but not always. In our practice, we have encountered examples of dangerous sites that, after entering a login and password, were able to initiate the sending of SMS by a real bank. The user entered the code from the SMS on an already open phishing page, and the attackers used it, receiving full access to your personal account. But we digress.
Initially the idea was quite simple. You need to keep an eye on passwords already saved in your browser. If a user enters a password on a site that clearly does not match the site from the password manager in the browser, then they need to be stopped and warned. The problem is that not everyone uses the built-in password manager. Even ordinary users who have never heard of LastPass, KeePass or 1Password are in no hurry to save their passwords, often preferring to enter them from memory or from a notepad (paper, not from Windows). Moreover, it is this category of users that is most vulnerable to phishing, which means that such a simple solution was not suitable.
There was no point in using already saved passwords, but instead of abandoning the whole idea, we taught the Browser to independently remember hashes of entered passwords. Why hashes? Because they are quite sufficient for comparing passwords, and storing hashes is still safer. Of course, we gave the option to disable the function for those who do not trust hashes. So, if the user logged in at least once, for example, to a real Alfa-Bank, then the Browser warned him when he tried to enter a password on phishing copies. It would seem that you could go drink champagne, but not everything is so simple.

Users' memory does not obey Moore's law, so many people prefer to come up with one password for all sites. This is terrible from a security point of view, but that's the reality. If we enabled password protection for all users on all sites, we would not only invent good protection from phishing, but also great way scare the audience. Therefore, by default, protection was enabled only for the sites most popular among scammers. For any other one, you can enable it manually.
This feature was introduced about a year ago, and all this time it not only protects against phishing, but also attracts people's attention to the topic of password security. But passwords are not the only type of confidential data that people like to steal.
Card protection
To steal money, it is not necessary to steal passwords from online banks and think through the logic of bypassing two-factor authentication. You can simply steal data bank card. There is also no need to remember about optional 3-D Secure - the user will not forget to enter the CVV code on the phishing page. After the card data is stolen, all that remains is to figure out how to take the money from there. There are different methods. For example, someone gives tourists tickets at a 50% discount, in fact buying them with a stolen card at full price. With varying success, such transactions can be challenged in a timely manner through your bank, but it is better not to let this happen and protect your bank card data.Unlike password protection, where password-site pairs could be uniquely controlled, bank cards can be used anywhere. We can control large sites, but we still won’t cover the long tail of online stores. And what does “control” even mean? Don't let me enter your card number? If you warn, then about what? Realizing that it is unlikely that it is possible to make an unambiguous conclusion at the Browser level about the bad intentions of the site, we looked at the situation from a different angle - from the point of view of encryption.
Availability of SSL certificate – required condition for any site that works with confidential user data, especially banking data. If a resource asks you to enter a card number, but does not support security and works via HTTP, then two different problems are possible. Firstly, someone can intercept your data along the way from open traffic. For example, through an unprotected Wi-Fi point in a cafe. Secondly, the owner of such a resource at least does not care about the safety of its visitors, and, perhaps, simply steals data. In any case, you should not enter your card number on such a site. If we somehow solve the problem with interception using the function, then encrypting the channel will not save you from a fraudster. More precisely, it will save data from fraudulent interceptors and deliver it intact to fraudulent phishers. And here something had to be done.
So, we have localized the problem. If a user visits an HTTP site that asks to enter a bank card number, then this is a reason to warn. But to show the message, you first need to recognize the card input. Special bank tag type input no one has yet come up with a relatively new attribute for browser autofill autocomplete=cc-number few people use it. The Chromium team, of course, is not giving up the idea of teaching the browser to substitute card numbers on its own and is even introducing heuristics that guess based on field names and some other data, but this does not work everywhere. In general, parsing input fields is not an option. But we can catch the input of numbers. For example, if the user entered 16 digits, then we can assume that this is a bank card. The problem is that this is not always the case. Fortunately, there is the Luhn algorithm.
I think many people know that the last digit in the card number is needed to verify the correctness of the entire number. And the check itself can be easily carried out using the Luhn algorithm. It's quite simple. In each pair of digits of the card number, we multiply the first number by 2. If after multiplication the number becomes greater than 9, then you need to add the composite numbers. And then put everything together. If the total amount is a multiple of 10, then we have the bank card number. With a 10% chance of error.

The Luna algorithm reduces the likelihood of false positives significantly. But there is a cheap way to reduce the error a little more - control the first digits in the number. It is at the beginning of the number that the payment system that supports the card is encoded. If there is a 4 at the beginning, then it is VISA. Something in the 51-55 range is MasterCard. 34-37 is American Express. Likewise for some other systems. The probability of error, of course, always remains, but at an acceptable level.
We taught the Browser to recognize the input of a certain number of digits (from 15 to 19), check them using the Luna algorithm and for compliance with the codes of well-known payment systems. And all this works completely locally - the Browser does not send or store the card number anywhere. If all conditions are met, the user sees the following warning:

We show a similar message for a number of other dangerous situations. For example, if the site itself is protected by HTTPS, but the number is entered in an HTTP frame. Or if the site certificate is not valid.
There are situations for which, due to their widespread occurrence and relative safety, it is not worth displaying a warning, but it is still necessary to give users the opportunity to figure it out. For example, if the form for entering a card number is located in a frame on another domain (both the site and the frame are HTTPS). This happens all the time, because there are many online stores, but not all of them are able to develop their own payment module, preferring to embed frames of popular payment systems. Or another example. The site does not use encryption, but accepts the card via an HTTPS frame on its own domain. For such situations, the Browser does not show a warning, but adds a map icon to the address bar. If you click on it, you can find out who exactly you trust with your data.

All of our security described above revolves around having an SSL certificate. This is justified, because users for the most part are not yet accustomed to paying attention to the lock in address bar, and phishers have no incentive to use certificates. But gradually everything is changing. Install free certificate from the same Let's Encrypt is no longer a problem. This means that sooner or later we will again return to a situation where we need to protect somehow, but there is not enough data on the client. And in order not to lose to phishing sites in the future, we have already begun to prepare Now.
Machine learning
Any website on the Internet has a set of characteristics by which it can be assessed. For example, the size of the audience, lifetime, the presence of an SSL certificate, its reliability, or even the uniqueness of the address (phishers like to use addresses that are as similar as possible). And our trust in this or that site is largely determined by them. An experienced user, looking at an unknown site, can decide for himself whether this site is trustworthy. With a computer everything is more complicated. The task of determining “suspiciousness” is difficult to formalize and does not fit into simple algorithms. It is clear that a blunder in HTTPS is a strong criterion, but I am talking about much more unobvious cases. And here you can’t do without machine learning.Yandex has been using machine learning for several years. Our technologies are used not only within the company (Search, Music, Market), but are also available to external customers through Yandex Data Factory. It is machine learning that allows a computer to demonstrate behavior that was not explicitly designed into it. And for our task - to warn users when paying on suspicious sites - it is ideal.
To train a machine to look for suspicious sites, we must show it examples of obviously bad sites. We have no problems with this - thanks to Safe Browsing technology. On the other hand, we indicate to her the characteristics (factors) already mentioned above that are worth paying attention to. And then our Matrixnet machine learning method learns to derive patterns and build formulas that could be fed with a website address and get a verdict as a result. In the most simplified way possible, it looks like this.