Encryption wep wpa wpa2. WPA2-PSK - what is it? Security type WPA2-PSK. How to choose the encryption type and set the WPA key on the WiFi router
To protect your Wi-Fi network and set a password, you must select the type of wireless network security and encryption method. And on at this stage Many people have a question: which one to choose? WEP, WPA, or WPA2? Personal or Enterprise? AES or TKIP? What security settings will best protect your Wi-Fi network? I will try to answer all these questions within the framework of this article. Let's consider everything possible methods authentication and encryption. Let's find out what parameters Wi-Fi security It is better to set the network in the router settings.
Please note that security type, or authentication, network authentication, security, authentication method are all the same thing.
Authentication type and encryption are the main wireless security settings. Wi-Fi networks. I think that first we need to figure out what they are, what versions there are, their capabilities, etc. After which we will find out what type of protection and encryption to choose. I’ll show you using the example of several popular routers.
I highly recommend setting up a password and protecting your wireless network. Install maximum level protection. If you leave the network open, without protection, then anyone can connect to it. This is primarily unsafe. And also an extra load on your router, a drop in connection speed and all sorts of problems with connecting different devices.
Wi-Fi network protection: WEP, WPA, WPA2
There are three protection options. Of course, not counting "Open" (No protection).
- WEP(Wired Equivalent Privacy) is an outdated and insecure authentication method. This is the first and not very successful method of protection. Attackers can easily access wireless networks that are protected using WEP. There is no need to set this mode in the settings of your router, although it is present there (not always).
- WPA(Wi-Fi Protected Access) – reliable and modern type security. Maximum compatibility with all devices and operating systems.
- WPA2– a new, improved and more reliable version of WPA. There is support for AES CCMP encryption. On this moment, This The best way Wi-Fi network protection. This is what I recommend using.
WPA/WPA2 can be of two types:
- WPA/WPA2 - Personal (PSK)- This the usual way authentication. When you only need to set a password (key) and then use it to connect to a Wi-Fi network. The same password is used for all devices. The password itself is stored on the devices. Where you can view it or change it if necessary. It is recommended to use this option.
- WPA/WPA2 - Enterprise– more complex method, which is mainly used to protect wireless networks in offices and various establishments. Allows for a higher level of protection. Used only when a RADIUS server is installed to authorize devices (which gives out passwords).
I think we have figured out the authentication method. The best thing to use is WPA2 - Personal (PSK). For better compatibility, so that there are no problems connecting older devices, you can set the WPA/WPA2 mixed mode. This is the default setting on many routers. Or marked as "Recommended".
Wireless Network Encryption
There are two ways TKIP And AES.
It is recommended to use AES. If you have older devices on your network that do not support AES encryption (but only TKIP) and there will be problems connecting them to the wireless network, then set it to "Auto". Type TKIP encryption not supported in 802.11n mode.
In any case, if you install strictly WPA2 - Personal (recommended), then only AES encryption will be available.
What protection should I install on my Wi-Fi router?
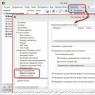
Use WPA2 - Personal with AES encryption. To date, this is the best and most safe way. This is what the wireless network security settings look like on ASUS routers:

And this is what these security settings look like on routers from TP-Link (with old firmware).

More detailed instructions for TP-Link you can look.
Instructions for other routers:
If you don’t know where to find all these settings on your router, then write in the comments, I’ll try to tell you. Just don't forget to specify the model.
Since WPA2 - Personal (AES) older devices ( Wi-Fi adapters, phones, tablets, etc.) may not support it, then in case of connection problems, set the mixed mode (Auto).
I often notice that after changing the password or other security settings, devices do not want to connect to the network. Computers may receive the error "The network settings saved on this computer do not meet the requirements of this network." Try deleting (forgetting) the network on the device and connecting again. I wrote how to do this on Windows 7. But in Windows 10 you need .
Password (key) WPA PSK
Whatever type of security and encryption method you choose, you must set a password. He's the same WPA key, Wireless Password, Wi-Fi Network Security Key, etc.
Password length is from 8 to 32 characters. You can use letters of the Latin alphabet and numbers. Also special signs: - @ $ # ! etc. No spaces! The password is case sensitive! This means that "z" and "Z" are different characters.
I don't recommend betting simple passwords. It is better to create a strong password that no one can guess, even if they try hard.

It is unlikely that you will be able to remember such a complex password. It would be nice to write it down somewhere. It’s not uncommon for Wi-Fi passwords to be simply forgotten. I wrote in the article what to do in such situations: .
If you need even more security, you can use MAC address binding. True, I don’t see the need for this. WPA2 - Personal paired with AES and complex password- quite enough.
How do you protect your Wi-Fi network? Write in the comments. Well, ask questions :)
A major concern for all wireless LANs (and all wired LANs, for that matter) is security. Security is just as important here as for any Internet user. Security is a complex issue and requires constant attention. Enormous harm can be caused to the user due to the fact that he uses random hot-spots or open points WI-FI access home or office and does not use encryption or VPN (Virtual Private Network) private network). This is dangerous because the user enters his personal or professional data, and the network is not protected from outside intrusion.
WEP
Initially, it was difficult to provide adequate security for wireless LANs.
Hackers easily connected to almost any WiFi networks by breaking initial versions of security systems such as Wired Equivalent Privacy (WEP). These events left their mark, and for a long time, some companies were reluctant or did not implement wireless networks at all, fearing that data transferred between wireless WiFi devices and Wi-Fi hotspots access can be intercepted and decrypted. Thus, this security model slowed down the integration of wireless networks into businesses and made people using WiFi networks at home nervous. Then the IEEE Institute created working group 802.11i, which worked to create a comprehensive security model to provide 128-bit AES encryption and authentication to protect data. The Wi-Fi Alliance introduced its own intermediate version of this 802.11i security specification: Wi-Fi Protected Access (WPA). The WPA module combines several technologies to solve the vulnerabilities of the 802.11 WEP system. Thus, WPA provides strong authentication users using the 802.1x standard (mutual authentication and encapsulation of data transmitted between wireless client devices, access points and server) and Extensible Authentication Protocol (EAP).
The operating principle of security systems is shown schematically in Fig. 1
Also, WPA is equipped with a temporary module for WEP encryption-engine through 128-bit key encryption and uses the Temporal Key Integrity Protocol (TKIP). And with the help checksum message (MIC) prevents data packets from being modified or formatted. This combination of technologies protects the confidentiality and integrity of data transmission and ensures security by controlling access so that only authorized users have access to the network.
WPA
Further enhancing WPA security and access control is the creation of a new unique key master for interaction between each user wireless equipment and access points and providing authentication sessions. And also, in creating a random key generator and in the process of generating a key for each package.
The IEEE ratified the 802.11i standard in June 2004, significantly expanding many capabilities thanks to WPA technology. The Wi-Fi Alliance has strengthened its security module in the WPA2 program. Thus, the level of transmission security WiFi data 802.11 standard has reached the required level for implementation wireless solutions and technologies in enterprises. One of the significant changes from 802.11i (WPA2) to WPA is the use of 128-bit Advanced Encryption Standard (AES). WPA2 AES uses anti-CBC-MAC mode (a mode of operation for a cipher block that allows a single key to be used for both encryption and authentication) to provide data confidentiality, authentication, integrity and replay protection. The 802.11i standard also offers key caching and pre-authentication to organize users across access points.
WPA2
With the 802.11i standard, the entire security module chain (login, credential exchange, authentication and data encryption) becomes more secure and effective protection from undirected and targeted attacks. The WPA2 system allows the Wi-Fi network administrator to switch from security issues to managing operations and devices.
The 802.11r standard is a modification of the 802.11i standard. This standard was ratified in July 2008. The standard's technology more quickly and reliably transfers key hierarchies based on Handoff technology as the user moves between access points. The 802.11r standard is fully compatible with the 802.11a/b/g/n WiFi standards.
There is also the 802.11w standard, which is intended to improve upon the security mechanism based on the 802.11i standard. This standard is designed to protect control packets.
802.11i and 802.11w standards - protection mechanisms WiFi networks 802.11n standard.
Encrypting files and folders in Windows 7
The encryption feature allows you to encrypt files and folders that will subsequently be impossible to read on another device without a special key. This feature is present in versions of Windows 7 such as Professional, Enterprise or Ultimate. The following will cover ways to enable encryption of files and folders.
Enabling file encryption:
Start -> Computer (select the file to encrypt) -> right button mouse over the file->Properties->Advanced (General tab)->Additional attributes->Place a checkmark in the item Encrypt content to protect data->Ok->Apply->Ok (Select apply only to file)->
Enabling folder encryption:
Start -> Computer (select the folder to encrypt) -> right mouse button on the folder -> Properties -> Advanced (General tab) -> Additional attributes -> Check the box Encrypt contents to protect data -> Ok -> Apply -> Ok (Select apply only to the file) -> Close the Properties dialog (Click Ok or Close).
WPA2 (Wireless Protected Access ver. 2.0) is the second version of a set of algorithms and protocols that provide data protection in Wi-Fi wireless networks. As expected, WPA2 should significantly improve the security of Wi-Fi wireless networks compared to previous technologies. New standard provides, in particular, for the mandatory use of the more powerful AES encryption algorithm ( Advanced Encryption Standard) and 802.1X authentication.
Today, to ensure a reliable security mechanism in a corporate wireless network, it is necessary (and mandatory) to use devices and software with WPA2 support. Previous generations of protocols - WEP and WPA - contain elements with insufficiently strong security and encryption algorithms. Moreover, programs and techniques have already been developed to hack WEP-based networks that can be easily downloaded from the Internet and successfully used even by untrained novice hackers.
WPA2 protocols operate in two authentication modes: personal (Personal) and corporate (Enterprise). In WPA2-Personal mode from the entered in clear text passphrase a 256-bit PSK (PreShared Key) key is generated. The PSK key together with the SSID (Service Set Identifier) are used to generate PTK (Pairwise Transient Key) temporary session keys for the interaction of wireless devices. Like the static WEP protocol, the WPA2-Personal protocol has certain problems associated with the need to distribute and maintain keys across wireless devices networks, making it more suitable for use in small networks from a dozen devices, while WPA2-Enterprise is optimal for corporate networks.
WPA2-Enterprise mode solves static key distribution and management issues and integrates with most corporate services authentication provides account-based access control. This mode requires login information such as a user name and password, a security certificate, or one-time password, authentication is carried out between workstation and a central authentication server. The access point or wireless controller monitors connections and forwards authentication requests to the appropriate authentication server (typically a RADIUS server such as Cisco ACS). WPA2-Enterprise mode is based on the 802.1X standard, which supports user and device authentication suitable for both wired switches and wireless points access.
Unlike WPA, the stronger AES encryption algorithm is used. Similar to WPA, WPA2 is also divided into two types: WPA2-PSK and WPA2-802.1x.
Provides new, more reliable mechanisms for ensuring data integrity and confidentiality:
CCMP (Counter-Mode-CBC-MAC Protocol), based on the Counter Cipher-Block Chaining Mode (CCM) of the Advanced Encryption Standard (AES) encryption algorithm. CCM combines two mechanisms: Counter (CTR) for confidentiality and Cipher Block Chaining Message Authentication Code (CBC-MAC) for authentication.
WRAP (Wireless Robust Authentication Protocol), based on the Offset Codebook (OCB) mode of the AES encryption algorithm.
TKIP protocol for backward compatibility with legacy equipment. Mutual authentication and key delivery based on IEEE 802.1x/EAP protocols. Secure Independent Basic Service Set (IBSS) to enhance security in Ad-Hoc networks. Roaming support.
Contribution to the security of wireless networks is the CCMP mechanism and the IEEE 802.11i standard. The latter introduces the concept of a secure network (Robust Security Network, RSN) and a secure network connection (Robust Security Network Association, RSNA), after which it divides all algorithms into:
RSNA algorithms (for creating and using RSNA);
Pre-RSNA algorithms.
Pre-RSNA algorithms include:
existing IEEE 802.11 authentication (referring to the authentication defined in the 1999 edition of the standard).
That is, these types of algorithms include authentication Open System with or without WEP encryption (more precisely, no authentication) and Shared Key.
RSNA algorithms include:
TKIP; CCMP; RSNA establishment and termination procedure (including the use of IEEE 802.1x authentication); key exchange procedure.
At the same time, the CCMP algorithm is mandatory, and TKIP is optional and is intended to ensure compatibility with older devices.
The standard provides two functional models: with IEEE 802.1x authentication, i.e. using the EAP protocol, and using a predefined key registered on the authenticator and the client (this mode is called Preshared Key, PSK). IN in this case The PSK key acts as a PMK key, and the further procedure for their authentication and generation is no different.
Since encryption algorithms using the TKIP procedure are already called WPA, and the CCMP procedure is WPA2, we can say that encryption methods that satisfy RSNA are: WPA-EAP (WPA-Enterprise), WPA-PSK (WPA-Preshared Key , WPA-Personal), WPA2-EAP (WPA2-Enterprise), WPA2-PSK (WPA2-Preshared Key, WPA2-Personal).
The connection establishment and key exchange procedure for the TKIP and CCMP algorithms is the same. CCMP itself (Counter mode (CTR) with CBC-MAC (Cipher-Block Chaining (CBC) with Message Authentication Code (MAC) Protocol), like TKIP, is designed to provide confidentiality, authentication, integrity and protection against replay attacks. This algorithm is based on the AES CCM encryption algorithm method, which is defined in the FIPS PUB 197 specification. All AES processes used in CCMP use AES with a 128-bit key and a 128-bit block size.
The latest innovation of the standard is support for fast roaming technology between access points using PMK key caching and pre-authentication.
The PMK caching procedure is that if a client has once passed full authentication when connecting to some access point, then it stores the PMK key received from it, and the next time it connects to this point, the client will send an earlier received PMK key. This will end the authentication, i.e. the 4-Way Handshake will not be performed.
The pre-authentication procedure is that after the client has connected and passed authentication on the access point, he can simultaneously (in advance) pass authentication on other access points (which he “hears”) with the same SSID, i.e. receive in advance their key is PMK. And if in the future the access point to which it is connected fails or its signal turns out to be weaker than some other point with the same network name, then the client will reconnect using a quick scheme with a cached PMK key.
The WEP2 specification, which appeared in 2001, which increased the key length to 104 bits, did not solve the problem, since the length of the initialization vector and the method for checking data integrity remained the same. Most types of attacks were implemented as simply as before.
Conclusion
In conclusion, I would like to summarize all the information and give recommendations for protecting wireless networks.
There are three mechanisms for securing a wireless network: configure the client and AP to use the same (non-default) SSID, allow the AP to communicate only with clients whose MAC addresses are known to the AP, and configure clients to authenticate to the AP and encrypt traffic. Most APs are configured to operate with a default SSID, no list of allowed client MAC addresses, and a known shared key for authentication and encryption (or no authentication or encryption at all). Typically these parameters are documented in the operational help system on the manufacturer's website. Thanks to these options inexperienced user can easily set up a wireless network and start working with it, but at the same time they make it easier for hackers to penetrate the network. The situation is aggravated by the fact that most access nodes are configured to broadcast the SSID. Therefore, a burglar can find vulnerable networks by standard SSID.
The first step to a secure wireless network is to change the default AP SSID. In addition, you should change this parameter on the client to enable communication with the AP. It is convenient to assign an SSID that makes sense to the administrator and users of the enterprise, but does not clearly identify this wireless network among other SSIDs that are intercepted by unauthorized persons.
Next step- if possible, block SSID broadcasting by the access node. As a result, it becomes more difficult (although still possible) for an attacker to detect the presence of a wireless network and SSID. In some APs, you cannot cancel the SSID broadcast. In such cases, you should increase the broadcast interval as much as possible. In addition, some clients can communicate only if the SSID is broadcast by the access node. Therefore, you may need to experiment with this setting to determine which mode is appropriate for your specific situation.
You can then allow access nodes to be accessed only from wireless clients with known MAC addresses. This may not be appropriate for a large organization, but for a small business with a small number of wireless clients, it is a reliable additional line of defense. Attackers will need to figure out the MAC addresses that are allowed to connect to the enterprise AP and replace the MAC address of their own wireless adapter with an authorized one (on some adapter models, the MAC address can be changed).
Selecting authentication and encryption options can be the most difficult part of securing a wireless network. Before you assign settings, you should inventory the access nodes and wireless adapters to determine the security protocols they support, especially if your wireless network is already configured with a variety of equipment from different vendors. Some devices, especially older APs and wireless adapters, may not be compatible with WPA, WPA2, or extended length WEP keys.
Another situation to be aware of is the need for user input on some older devices hexadecimal number, which represents the key, and other older APs and wireless adapters require you to enter a passphrase that converts to a key. As a result, it is difficult to ensure that one key is used by all equipment. Owners of such equipment can use resources such as WEP Key Generator to generate random WEP keys and convert passphrases to hexadecimal numbers.
In general, WEP should only be used when absolutely necessary. If using WEP is mandatory, you should choose keys of the maximum length and configure the network to Open mode instead of Shared. In Open mode on the network, no client authentication is performed, and anyone can establish a connection with access nodes. These preparatory connections partially load wireless channel communication, but attackers who established a connection to the AP will not be able to continue exchanging data because they do not know the WEP encryption key. You can even block pre-connections by configuring the AP to only accept connections from known MAC addresses. Unlike Open, in Shared mode the access node uses the WEP key to authenticate wireless clients in a challenge-response procedure, and an attacker can decrypt the sequence and determine the WEP encryption key.
If you can use WPA, you must choose between WPA, WPA2 and WPA-PSK. The main factor when choosing WPA or WPA2 on the one hand, and WPA-PSK on the other, is the ability to deploy the infrastructure necessary for WPA and WPA2 to authenticate users. WPA and WPA2 require the deployment of RADIUS servers and possibly Public Key Infrastructure (PKI). WPA-PSK, like WEP, works with a shared key that is known wireless client and AP. WPA-PSK You can safely use the WPA-PSK shared key for authentication and encryption, since it does not have the disadvantage of WEP.
Bibliography
1. Goralski V. xDSL technologies. M.: Lori, 2006, 296 p.
2. www.vesna.ug.com;
3. www.young.shop.narod.com;
7. www.opennet.ru
8. www.pulscen.ru
9. www.cisco.com
10. Baranovskaya T.P., Loiko V.I. Architecture of computer systems and networks. M.: Finance and Statistics, 2003, 256 p.
11. Mann S., Krell M. Linux. Administration of TCP/IP networks. M.: Binom-Press, 2004, 656 p.
12. Smith R. Network tools Linux. M.: Williams, 2003, 672 p.
13. Kulgin M. Computer networks. Construction practice. St. Petersburg: Peter, 2003, 464 p.
14. Tanenbaum E. Computer networks. St. Petersburg: Peter, 2005, 992 pp.
15. Olifer V.G., Olifer N.A. Basics of Data Networks. Lecture course. M.: Internet University of Information Technologies, 2003, 248 p.
16. Vishnevsky V.M. Theoretical basis design computer networks. M.: Tekhnosphere, 2003, 512 p.
WPA encryption involves using a secure Wi-Fi network. In general, WPA stands for Wi-Fi Protected Access, that is, protected.
Majority system administrators they know how to configure this protocol and know quite a lot about it.
But also ordinary people can learn a lot about what WPA is, how to configure it and how to use it.
True, on the Internet you can find many articles on this subject, from which it is impossible to understand anything. So today we will talk in simple language O difficult things.
A little theory
So, WPA is a protocol, technology, program that contains a set of certificates used during transmission.
To put it simply, this technology allows you to use various methods to protect your Wi-Fi network.
It could be electronic key, which is also a special certificate of the right to use this network (we’ll talk about this later).
In general, with the help of this program, only those who have the right to do so will be able to use the network and that’s all you need to know.
For reference: Authentication is a security tool that allows you to establish the identity of a person and his right to access the network by comparing his reported and expected data.
For example, a person can be authenticated when they attach their . If he simply enters his login and password, this is only authorization.
But a fingerprint allows you to check whether this person is really logging in, and not someone took his data and entered with their help.

Rice. 1. Fingerprint scanner on your smartphone
And also on the diagram there is a WLC - wireless controller local network. On the right is the authentication server.
All this is connected by a regular Switch (a device that simply connects different network devices). The key is sent from the controller to the authentication server and stored there.
When a client tries to connect to a network, it must transmit to the LAP a key that it knows. This key goes to the authentication server and is compared with with the right key.
If the keys match, the signal propagates freely to the client.

Rice. 2. Sample WPA scheme in Cisco Pocket Tracer
Components of WPA
As we said above, WPA uses special keys that are generated every time you try to start transmitting a signal, that is, turn on Wi-Fi, and also change every time.
WPA includes several technologies that help generate and transmit these same keys.
The figure below shows the general formula, which includes all the components of the technology under consideration.

Rice. 3. Formula with WPA ingredients
Now let's look at each of these components separately:
- 1X is a standard that is used to generate that same unique key, with the help of which authentication takes place in the future.
- EAP is the so-called Extensible Authentication Protocol. It is responsible for the format of messages with which keys are transmitted.
- TKIP is a protocol that made it possible to expand the key size to 128 bytes (previously, in WEP, it was only 40 bytes).
- MIC is a mechanism for checking messages (in particular, they are checked for integrity). If messages do not meet the criteria, they are sent back.
It is worth saying that now there is already WPA2, which, in addition to all of the above, also uses CCMP and AES encryption.
We won't talk about what it is now, but WPA2 is more secure than WPA. That's all you really need to know.
One more time from the very beginning
So, you have . Used on the network WPA technology.
To connect to Wi-Fi, each device must provide a user certificate, or, more simply, a special key issued by the authentication server.
Only then will he be able to use the network. That's all!
Now you know what WPA is. Now let's talk about what is good and what is bad about this technology.
Advantages and disadvantages of WPA encryption
The advantages of this technology would include the following:
- Enhanced data transmission security (compared to WEP, its predecessor, WPA).
- Tighter Wi-Fi access control.
- Compatible with big amount devices that are used to organize a wireless network.
- Centralized security management. The center in this case is the authentication server. Due to this, attackers are not able to gain access to hidden data.
- Enterprises can use their own security policies.
- Easy to set up and continue to use.
Of course, this technology also has disadvantages, and they are often quite significant. In particular, we're talking about here's what it's about:
- A TKIP key can be cracked in a maximum of 15 minutes. This was stated by a group of specialists in 2008 at the PacSec conference.
- In 2009, specialists from Hiroshima University developed a method for hacking any network that uses WPA in one minute.
- Using a vulnerability called Hole196 by experts, you can use WPA2 with your own key, and not with the one required by the authentication server.
- In most cases, any WPA can be cracked using a simple search of all possible options(brute force), as well as using the so-called dictionary attack. In the second case, the options are used not in a chaotic order, but according to the dictionary.
Of course, to take advantage of all these vulnerabilities and problems, you must have special knowledge in the field of building computer networks.
All this is inaccessible to most ordinary users. Therefore, you don’t have to worry too much about someone gaining access to your Wi-Fi.

Rice. 4. Burglar and computer
Hi all!
I analyzed a little of the comments that visitors leave on the site, checked the queries and realized that there is a very common problem with connecting to Wi-Fi, which I have not written about yet. But many comments were left on the site asking for help to solve this problem. I advised something there, but I don’t know if my advice helped you (rarely does anyone write about the results 🙁).
And yesterday, Roman (Thank you kind man :) I left a comment on the article in which I shared information on how he solved the problem “Saved, WPA\WPA2 protection”. This comment helped me understand the problem a little, and I decided to collect all the tips for solving this error in one article.
The essence of the problem
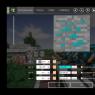
When connecting a phone or tablet (most likely on Android), To home network, or somewhere in a cafe, an inscription appears next to the name of the network “Saved, WPA\WPA2 protection”. And nothing else happens. If you click on this network and select To plug, then nothing will happen. You can see what this error looks like in the screenshot above.
I specifically provoked this problem on my Asus RT-N13U Wi-Fi router and tried to connect HTC phone One V (Android 4.0) . So I got this message “Saved, WPA\WPA2 protection”. Moreover, everything worked out the first time. How? Yes, very simple. In my router settings, “Wireless network mode” was set to Auto mode, and I set it to n Only. I saved the settings, disconnected the phone from Wi-Fi, but it was no longer possible to connect :)
The main causes of the error “Saved, WPA\WPA2 protection”
Friends, I cannot say exactly everything and give advice that will be one hundred percent working, I hope you understand. All devices are different, everyone has different settings and many other nuances.
But I will try to collect the reasons known to me and ways to solve them, through which such a problem with connecting to a wireless network may arise.
If, when connecting to a wireless network, you see the message “Saved, WPA\WPA2 protected” on your phone (maybe a little different), then it’s worth checking these settings (I advise you to check in the same order):
To get started, simply reboot your router.
I have already noticed this problem several times: the Internet on the phone simply stops working, but there is a connection and the network is good. I turn Wi-Fi off and on on my phone, but it no longer connects to the network, it says “Saved, WPA2 protection.” Only rebooting the router helps.
- Set the correct region in the router settings
- Check whether the password for the Wi-Fi network is correct
- Check (change) the wireless network operating mode in the router settings
- Check (change) the encryption type and security type, change the password in the router settings
- Experiment with changing the channel on which your wireless network operates.
- Try changing the channel width.
And now in more detail on all points
Set the correct region in the router settings
Very often, this error occurs precisely because the Wi-Fi settings are set to the wrong region.
Using Tp-Link as an example, I will show you how to change the region. If you have a router from another company, then these settings are most likely changed on the same page where you set the name and other settings of the wireless network.
In Control Panel, go to the tab Wireless (Wireless mode) and opposite the point Region indicate the country you are in.
 Save the settings by clicking the button Save(Save) .
Save the settings by clicking the button Save(Save) .
Check your password and connect again
You may have simply entered your password incorrectly (however, then most likely there will be a constant connection, in a circle. But you need to check), and before getting into the router settings, I advise you to check this.
You may ask, how can I enter the password again, because the password request does not appear. You need to delete the connection. Just click on your network and select Delete.

Now, click on your network again and enter your Wi-Fi password. Just make sure it's correct. If you forgot, look at the password in the router settings, or on the connected computer (if there are any). Read more in the article.
Checking the wireless network operating mode
It seems to me that this main reason. Just your device (phone, tablet) may not support the operating mode in which the router operates.
The operating mode is those incomprehensible letters b/g/n, which you probably already noticed in the router settings. Try experimenting with changing modes. Don’t forget to restart the router after each change and turn off/on Wi-Fi on your phone (tablet).
So I installed n Only instead of Auto and an error popped up. And if, for example, you already have n Only in your settings? Here are your problems.
Changing the encryption/security type, password
It may be that your device simply does not like the type of security or encryption that the router uses. Or you don't like the password.
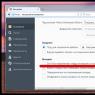
I advise you to set the following values:
WPA/WPA2 - Personal (Recommended)
Version: WPA-PSK
Encryption: AES
PSK Password (key) – at least eight characters and numbers only.
We save, reboot the router, delete the connection on the phone, and connect by entering a new password.
Attention! After changing the password or other security settings, problems may arise with connecting other devices that were already connected to this network (computers, laptops, TVs).
Experimenting with the channel on which the Wi-Fi network operates
It's unlikely, of course, but it could be. I wrote about what a wireless network channel is, how to change it and why in the article -.
Try experimenting and see if it helps.
Channel width
There is such a point in Wi-Fi settings router, like Channel width. If you have, for example, TP-Link and the menu is in English, then it is called Channel Width.
There you can select several options: Auto, 20MHz and 40MHz - depending on the router. Try installing first Auto(or in Asus 20MHz/40MHz), if that doesn’t help, then separately.
Where can I change the channel width?
Go to the router settings ( address 192.168.1.1, or 192.168.0.1, enter login/password - look at the bottom of the router).
Asus
Go to the tab Wireless network and change the value opposite Channel width.

TP-Link
Tab Wireless – Wireless Settings, paragraph Channel Width.

Don't forget to save the settings and reboot the router.
Afterword
I seem to have written everything I wanted. I really hope that my advice will help you. You will get rid of this problem and connect your phone or tablet with a Wi-Fi router :)
Perhaps you know other solutions to this problem, share them in the comments - I will be grateful!
Best wishes!
Also on the site:
The phone (tablet) does not connect to Wi-Fi, it says “Saved, WPA\WPA2 protected” updated: February 7, 2018 by: admin