Credential Manager is where Windows stores passwords and other login information. What is Credential Manager
Windows StorageAt the top of the window is the Windows Vault icon, which by default stores all credentials. In fact, "vault" is just a more readable name for the "Credentials" folder. On computers connected to the domain, it is located at " C:\Users\Username\AppData\Roaming\Microsoft"(in the English version - " C:\Users\Username\AppData\Roaming\Microsoft»).
On computers in a peer-to-peer network, the address is different - “ C:\Users\Username\AppData\Local\Microsoft"((in the English version - " C:\Users\Username\AppData\Local\Microsoft"). The files in this folder are, of course, encrypted.
Backing up and restoring Windows Vault
Under the Windows Vault icon there are two links: Back Up Vault and Restore Vault. Archiving not only allows you to have a backup copy in case the storage is deleted or damaged, but also makes it easier to transfer credentials from one computer to another.
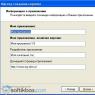
The Archive Vault link launches a multi-step archiving wizard (Figure D), including accessing the Secure Desktop via ++ to create a password for backup copy storages. This is necessary even if the secure desktop is normally disabled.
Figure D: During backup, you must gain access to the secure desktop and set a password for the vault backup.
When restoring storage from a backup (Figure E), you also need access to the secure desktop to enter the password.
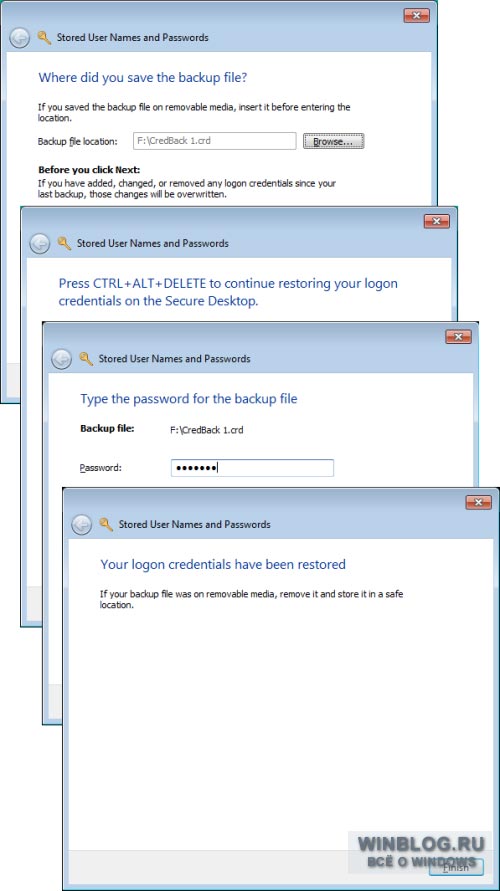
Figure E: To restore your vault from a backup, you must access the secure desktop and enter your password.
Credential Types
In the Credential Manager, all data is grouped into three categories: “Credential Windows data"(Windows Credentials), "Certificate-Based Credentials" and "Generic Credentials".
Windows credentials are names and passwords that are used to access shared network folders, websites that use Windows Integrated Authentication, and when connecting to a remote desktop.
Certificate-based credentials are designed for smart cards and other such devices.
Shared credentials are used third party applications, which require separate authorization with credentials different from those used to log in to the system. This section can store almost any credentials that comply with Microsoft standards.
It is worth considering that Credential Manager is not responsible for all the data used to log into websites. Most credentials in Internet Explorer, for example, is handled using the AutoComplete function.
Credential Manager, or Credential Manager, is a mechanism that allows you to manage user credentials (login and password) to access network resources, as well as certificates and credentials for various applications (Email, web services, etc.).
For example, we want to access a folder located on another computer and remote computer asks for our credentials. Enter your login and password and check the “Remember credentials” checkbox. Or, when connecting to a remote desktop, we allow saving credentials so as not to enter them every time.
Strictly speaking, websites are a different story. The Credential Manager is not responsible for all the data used to access Internet resources. Most of this data is processed and stored in the Internet Explorer web browser itself, which has for this purpose special function autocomplete (AutoComplete).
This issue was fixed in Windows 8, where Credential Manager has a separate section called “Internet Credentials.” And if you specify to save, for example, the password for Yandex mail, then it will be saved here. However, this feature only works with Internet Explorer; other browsers do not use it and continue to store all the data themselves.
All credentials saved in this way end up in the so-called Windows Vault, which is where all credentials are stored by default. In fact, vault is just a more descriptive name for the Credentials folder. For domain users, this folder is located at:
C:\Users\Username\AppData\Roaming\Microsoft
(in the English version C:\Users\Username\AppData\Roaming\Microsoft),
for local - C:\Users\Username\AppData\Local\Microsoft
(in the English version C:\Users\Username\AppData\Local\Microsoft).
All files in this folder are, of course, encrypted, and access to them is carried out using the Credential Manager.
You can open it through the Control Panel, or simply by typing Credentials Manager in the search bar (Credentials Manager for the English version).
All data in Credential Manager is grouped into three categories:
Windows Credentials(Windows Credentials) are names and passwords that are used to access network shares, websites that use Windows Integrated Authentication, and when connecting to a remote desktop;
Certificate-based credentials(Certificate-Based Credentials) - designed for authentication using smart cards;
General credentials(Generic Credentials) - used by third-party applications that require separate authorization with credentials different from those used to log in. This section can store almost any credentials that comply with Microsoft standards.
Credential Manager in Windows 7
Credential Manager, or Credential Manager, is a mechanism that allows you to manage user credentials (login and password) for accessing network resources, as well as certificates and credentials for various applications (email, web services, etc.) .
For example, we want to access a folder located on another computer, and the remote computer asks for our credentials. Enter your login and password and check the “Remember credentials” checkbox.
Or, when connecting to a remote desktop, we allow saving credentials so as not to enter them every time.
All credentials saved in this way end up in the so-called Windows Vault, which is where all credentials are stored by default. In fact, vault is just a more descriptive name for the Credentials folder. For domain users, this folder is located at: C:\Users\Username\AppData\Roaming\Microsoft (in the English version C:\Users\Username\AppData\Roaming\Microsoft), for local users - C:\Users\Username\ AppData\Local\Microsoft (in the English version C:\Users\Username\AppData\Local\Microsoft). All files in this folder are, of course, encrypted, and access to them is carried out using the Credential Manager.
You can open it through the Control Panel, or simply by typing Credentials Manager in the search bar (Credentials Manager for the English version).
This is what Credential Manager looks like. All data in it is grouped into three categories:
Windows Credentials(Windows Credentials) are names and passwords that are used to access network shares, websites that use Windows Integrated Authentication, and when connecting to a remote desktop;
Certificate-based credentials(Certificate-Based Credentials) - designed for authentication using smart cards;
General credentials(Generic Credentials) - used by third-party applications that require separate authorization with credentials different from those used to log in. This section can store almost any credentials that comply with Microsoft standards.
All credentials can be expanded and viewed in detail, and, if desired, edited.
Credentials can not only be saved during the connection process, but also entered directly in the manager. To do this, select a section and click on the “Add credentials” link. As an example, let's add the credentials to connect to the private website http://contoso.com in the General Credentials section.
Now the data is saved in the storage, and when connecting to this resource you won't need to enter them.
Strictly speaking, websites are a different story. The Credential Manager is not responsible for all the data used to access Internet resources. Most of this data is processed and stored in the browser itself. Internet Explorer, for example, has a special autocomplete function for this (AutoComplete).
They tried to fix this flaw in Windows 8, where there is a separate section in the Credential Manager called “Internet Credentials”. And if you specify to save, for example, the password for Yandex mail, then it will be saved here. However, this feature only works with Internet Explorer; other browsers do not use it and continue to store all the data themselves.
Archiving and recovery
Directly below the Windows Storage icon are two links: Archive Storage and Restore Storage. This way, credentials can be backed up in case the storage is deleted or damaged, or transferred from one computer to another.
Data archiving is carried out by a special master. The procedure is simple - we indicate where to save the archive (recommended for removable media), then set a password to access it. The password must be set using a secure desktop (Secure Desktop). This is necessary even if the secure desktop is disabled.
Recovery follows a similar scenario - we indicate the location of the archive and enter the password, also on Secure Desktop.
The Credential Manager is especially convenient when there is no domain, when all permissions to network resources are registered locally. In this case, the credential archive can be used to automate the process of assigning rights. However, the Credential Manager can also be used in a domain to access external resources. In general, a useful thing, special settings does not require, saves data. True, sometimes individual credentials can unexpectedly disappear, so it’s still worth making an archive.
Windows stores passwords in a reversible form not only in LSA secrets, but also in other places.
Network Service Accounts
Windows stores passwords in a reversible form not only in LSA secrets, but also in other places.When you access a network resource, such as a shared folder, a proxy server with NTLM authentication, a DBMS, mail server etc., then you can often save your password by simply checking the “Remember password” box.
In fact, in such Windows cases saves usernames and passwords in Credential Manager(Credential Manager). Storing credentials allows Windows to use the single sign-on (SSO) technology introduced in Windows XP. With SSO, every time a user needs to authenticate to a network resource, they do not have to re-enter their credentials.
Passwords in Credential Manager are encrypted using the DPAPI subsystem and can be obtained from unencrypted.
In Credential Manager you can also view, edit and add information. On Windows systems Vista and higher manager is available in Control Panel\User Accounts and Family Safety\Credential Manager or Control Panel\User Accounts and Family Safety\User Accounts\\Manage your credentials.
For similar purposes in Windows there is Secure storage(Protected Storage). Applications like Internet Explorer and Outlook Express store passwords for email accounts in a secure storage; mail passwords are encrypted using CryptoAPI, and the encryption key is generated from the user password, therefore, mail passwords can also be obtained in unencrypted.
Third-party programs (Chrome, RealVNC Client, Thunderbird, etc.) save passwords from websites different ways: some in the registry, others with using Windows APIs store them in an account manager or secure storage, while others store passwords in files. But regardless of which method is used by the program, passwords are stored in a reversible form, and, therefore, we have the opportunity to obtain unencrypted passwords from sites.
Getting information from Account Manager
Ways to interact with Credential Manager documented Microsoft and are used in some utilities that allow you to drain information from the manager.Can also successfully drain information from Credential Manager. The only problem is that the utility only works locally, so if target system you do not have the rights to install the software, better utility do not use.
The post-exploit module should not be used windows/gather/credentials/enum_cred_store from the Metasploit framework, since the module always crashes, regardless of the Windows version.
Retrieving information from secure storage
I give first place to (pspv) from NirSoft. The utility works stably and is a stand-alone EXE file.And here is the utility in in this case It is ineffective and I do not recommend using it.
Obtaining credentials from third-party programs
NirSoft offers a wide range of utilities for obtaining credentials from a third party software. Many of these utilities are combined into a separate EXE file, carrot.Also, if you managed to run Meterpreter on the target system, then the Metasploit framework will be very useful to you: the framework has several post-exploit modules specifically for such purposes. Some of the modules work stably, while others are still beta versions and often crash.
What threats does obtaining network service accounts pose?
When analyzing internal network infrastructure, you will most likely first capture a simple workstation rather than a server.An important step towards compromising the entire network is obtaining information about what role exactly the machine you captured plays. If a workstation is used daily, then chances are high that the user of this workstation has access to corporate mail, internal websites, corporate proxy server and other services. And, what is even more likely, the user has chosen “Remember password” everywhere.
“Free” access to such corporate services even with low-privileged user rights is actually invaluable. Automatic input credentials will help you expand control over the network, and also show the customer that the protection of even the most insignificant workstation remote from the demilitarized zone must be approached with special care.
Very often, users to access mail, shared folders and other network resources use the same passwords (sometimes even the password is the same as the password account domain user), so getting accounts network services makes a huge difference during a penetration test.
I added the utilities described in this article to table. I will be glad to see your feedback and suggestions!