Full memory dump what. What is a memory dump and how to close it. See what “Dump” is in other dictionaries
Hello friends, today we will discuss an interesting topic that will help you in the future when a blue screen of death (BSoD) appears.
Like me, many other users had to observe the appearance of a screen with a blue background on which something was written (white on blue). This phenomenon indicates a critical problem, both in software, for example, a driver conflict, and in a physical malfunction of some computer component.
I recently got a blue screen issue in Windows 10 again, but I quickly got rid of it and will tell you about it soon.
So, most of the users are not aware that BSoD can be analyzed to later understand the critical error issues. For such cases, Windows creates special files on the disk, and we will analyze them.
There are three types of memory dump:
Full memory dump– this function allows you to completely save the contents of RAM. It is rarely used, because imagine that you have 32 GB of RAM, with a full dump, all this volume will be stored on disk.
Core dump– saves kernel mode information.
Small memory dump– saves a small amount of error information and loaded components that were present at the time the system malfunction occurred. We will use this type of dump because it will give us enough information about the BSoD.
The location of both the small and full dump is different, for example, the small dump is located in the following path: %systemroot%\minidump.
The full dump is here: %systemroot%.
There are various programs for analyzing memory dumps, but we will use two. The first is Microsoft Kernel Debuggers, as the name suggests, a utility from Microsoft. You can download it from the official website. The second program is BlueScreenView, a free program, download from here.
Analyzing a Memory Dump Using Microsoft Kernel Debuggers
For different versions of systems you need to download a different type of utility. For example, for a 64-bit operating system, a 64-bit program is needed, for a 32-bit operating system, a 32-bit version is needed.
That's not all, you need to download and install the package of debugging symbols needed for the program. It's called Debugging Symbols. Each version of this package is also downloaded under a specific OS, first find out what system you have, and then download. So that you don’t have to look for these symbols anywhere, here is the download link. The installation should preferably be done in this path: %systemroot%\symbols.
Now you can launch our debugger, the window of which will look like this:
Before analyzing the dumps, we will configure something in the utility. First, we need to tell the program where we installed the debugging symbols. To do this, click on the “File” button and select the “Symbol File Path” item, then specify the path to the symbols.

The program allows you to extract symbols directly from the web, so you don't even have to download them (sorry to those who have already downloaded them). They will be taken from a Microsoft server, so everything is secure. So, you need to open “File” again, then “Symbol File Path” and enter the following command:
SRV*%systemroot%\symbols*http://msdl.microsoft.com/download/symbols

Thus, we indicated to the program that the symbols should be taken from the network. Once we have done this, click “File” and select “Save Workspace”, then click OK.
That's all. We have configured the program in the right way, now we begin to analyze memory dumps. In the program, press the button "File", Then "Open Crash Dump" and select the desired file.
Kernel Debuggers will begin analyzing the file and then output a result about the cause of the error.

In the window that appears, you can enter commands. If we enter !analyze –v, then we will get more information.
That's all with this program. To stop the debugger, select "Debug" and the "Stop Debugging" item.
Analyzing a memory dump using BlueScreenView
The BlueScreenView program is also suitable for analyzing various errors and BSoDs; it has a simple interface, so there should be no problems with mastering it.Download the program from the link above and install. After launching the utility, you need to configure it. Go to the parameters: “Settings” - “Advanced settings”. A small window will open with a couple of items. In the first paragraph, you need to indicate the location of the memory dumps. They are usually located in the path C:\WINDOWS\Minidump. Then just click the "Default" button.

What can you see in the program? We have menu items, part of the window with the names of the dump files, and the second part of the window – the contents of the memory dumps.

As I said at the beginning of the article, dumps can store drivers, the screenshot of the “screen of death” itself, and other useful information that may be useful to us.
So, in the first part of the window, where the dump files are, select the memory dump we need. In the next part of the window we look at the contents. Drivers located in the memory stack are marked in reddish color. They are precisely the cause of the blue screen of death.
On the Internet you can find everything about the error code and driver that may be to blame for BSoD. To do this, click “File”, and then “Find error code + Driver in Google”.

You can display only the drivers that were present at the time the error occurred. To do this, click “Settings” - “Bottom window mode” - “Only drivers found in the crash stack”. Or press the F7 key.

To show the BSoD screenshot, press F8.
To show all drivers and files, press F6.
Well, that's all. Now you know how to find out about the Blue Screen of Death problem, and if something happens, find a solution on the Internet or on this site. You can offer your error codes, and I will try to write for each article to solve the problem.
Also don't forget to ask questions in the comments.
In chapter A crash dump is defined by the following parameters:
– REG_DWORD-parameter AutoReboot with meaning 0x1(option Perform automatic reboot subwindow window Properties of the system);
– REG_DWORD-parameter CrashDumpEnabled with meaning 0x0, if a memory dump is not created; 0x1 – Full memory dump; 0x2 – Kernel memory dump; 0x3 – Small memory dump (64KB);
– REG_EXPAND_SZ-parameter DumpFile with meaning %SystemRoot%\MEMORY.DMP(dump file storage location);
– REG_DWORD-parameter LogEvent with meaning 0x1(option Log event window );
– REG_EXPAND_SZ-parameter MinidumpDir with meaning %SystemRoot%\Minidump(optional);
– REG_DWORD-parameter Overwrite with meaning 0x1(option Replace existing file window );
– REG_DWORD-parameter SendAlert with meaning 0x1(option Send an administrative alert window ).
How the system creates an emergency memory file
During boot, the operating system checks the emergency creation parameters in the registry section . If at least one parameter is specified, the system generates a map of disk blocks occupied on the boot volume and stores it in memory. The system also determines which disk device controls the boot volume and calculates checksums for the image in memory and for data structures that must be integer to be able to perform I/O operations.
After a failure, the system kernel checks the integrity of the page file map, disk file, and disk control structures.. If the integrity of these structures is not violated, then the system kernel calls special disk I/O functions , designed to save a memory image after a failure. These I/O functions are self-contained and do not rely on kernel services because the programs responsible for writing the crash dump cannot make any assumptions about which parts of the system kernel or devices were damaged when a crash occurred. The system kernel writes data from memory to the paging file sector map (it does not have to usefile system).
First, the system kernel checks the status of each component involved in the dump process. This is done so that when writing directly to disk sectors, the data located outside the file is not damaged. File size should be 1 MB is larger than the size of physical memory, because when information is written to, a header is created that contains the emergency signature and the values of several important system kernel variables. Title occupies less than 1 MB, but the operating system can increase (or decrease) the size of the paging file by at least 1 MB.
After system boot Session Manager (Windows NT Session Manager; disk address – \WINDOWS\system32\smss.exe) initializes system files, using its own function to create each file NtCreatePagingFile. NtCreatePagingFile determines whether the file being initialized exists, and if so, whether it has a header . If there is a title, then NtCreatePagingFile sends to Session Manager special code. After that Session Manager starts the process Winlogon (Windows NT Logon Program; disk address – \WINDOWS\system32\winlogon.exe), which is notified of the existence of an emergency . Winlogon starts the program SaveDump (Windows NT Memory Copy Program; disk address – \WINDOWS\system32\savedump.exe), which parses the header and determines further actions in an emergency.
If the title indicates the existence , That SaveDump copies data from a file to an emergency file whose name is specified REG_EXPAND_SZ-parameter DumpFile section . Bye SaveDump rewrites the file , the operating system does not use the part of the page file that contains the emergency . During this time, the amount of virtual memory available to the system and applications is reduced by (At the same time, messages may appear on the screen indicating a lack of virtual memory). Then SaveDump informs the memory manager that the save is complete , and he releases that part file in which it is stored , for general use.
Saving the file , program SaveDump records the creation of an emergency in the event log , for example: “The computer was rebooted after a critical error: 0x100000d1 (0xc84d90a6, 0x00000010, 0x00000000, 0xc84d90a6). Memory copy saved: C:\WINDOWS\Minidump\Mini060309-01.dmp" .
Full memory dump writes the entire contents of memory when a fatal error occurs. For this option, you must have a paging file on the boot volume, the size of which is equal to the amount of all physical RAM plus 1 MB. Default full memory is written to a file %SystemRoot%\Memory.dmp. If a new error occurs and a new complete file is created memory (or kernel memory) the previous file is replaced (overwritten). Parameter Full memory dump not available on systems running a 32-bit operating system and 2 or more RAM.
If a new error occurs and a new complete file is created memory the previous file is replaced.
Kernel memory dump writes only kernel memory, making the process of writing data to the log when the system suddenly stops proceeds faster. Depending on the amount of physical memoryin this case the page file requires 50 to 800 MB or one third of the physical memory on the boot volume. kernel memory is written to a file %SystemRoot%\Memory.dmp.
This does not include unallocated memory or memory allocated to mode programs. It only includes memory allocated to the kernel and hardware-specific layer ( HAL) V Windows 2000 and later versions of the system, as well as memory allocated for kernel mode and other kernel mode programs. In most cases this is the most preferred option. It takes up much less space compared to a full memory, while excluding only those memory sectors that are most likely not associated with the error.
When a new error occurs and a new file is created kernel memory the previous file is replaced.
Small memory dump records the smallest amount of useful information necessary to determine the cause of the problem. To create a small memory requires that the page file size be at least 2 MB on the boot volume.
Small files memory contains the following information:
– message about a fatal error, its parameters and other data;
– list of downloaded ;
– context ( PRCB) on which the failure occurred;
EPROCESS) for the process that caused the error;
– process information and kernel context ( ETHREAD) for the thread that caused the error;
– Kernel mode call stack for the thread that caused the error.
Small file memory is used when hard disk space is limited. However, due to the limited information it contains, analysis of this file may not always detect errors that were not directly caused by the thread running at the time the error occurred.
If the following error occurs and a second small file is created memory, the previous file is retained. Each additional file is given a unique name. The date is encoded in the file name. For example, Mini051509-01.dmp- this is the first file memory, created on May 15, 2009 List of all small files memory is stored in a folder %SystemRoot%\Minidump.
operating system , undoubtedly, much more reliable than previous versions - thanks to the efforts of both developers Microsoft, both hardware developers and application software developers . However, emergency situations - all kinds of failures and system crashes - are inevitable, and depending on whether theknowledge and skills in eliminating them, it depends whether he will have to spend a few minutes troubleshooting (for example, updating/debugging or reinstalling the application program causing the failure), or several hours reinstalling/configuring the operating system and application software (which does not guarantee the absence of failures and crashes in the future!).
Many administrators neglect to analyze crash dumps Windows , believing that working with them is too difficult. It’s difficult, but it’s possible: even if, for example, the analysis of one out of ten will be successful - the efforts spent on mastering the simplest techniques for analyzing emergency situations , will not be in vain!..
By and large, you, as a user, should not be interested in a memory dump. This is just information about a system failure, which ideally should be sent to Microsoft developers to find and fix critical errors. If you do not plan to engage in such charity, then you can disable the dump.
Disabling memory dump will not affect system performance in any way. When you use your computer, the system does not access the dump, whether it is turned on or not. Recording occurs only when Windows is “brought” to BSOD (blue screen). It lasts a couple of seconds at most.
Types of dump
For general development, let's get acquainted with the types of dump. There are three of them: small dump, core dump and large. A small dump stores the most important information about the problem. Developers literally have to piece it together bit by bit. For a small dump you need to allocate 2 MB of virtual memory (swap file).
Core dump– the most common type of dump. This option is usually the default. It records all the memory that is allocated to the core - the state of working drivers and data on the hardware-dependent level. For it you need to allocate about 30% of the total amount of RAM. For example, if you have 2 GB DDR, then allocate about 700 MB for the swap file.
A full dump records the entire contents of RAM. Accordingly, for it to work, you will have to allocate the same volume to the paging file as RAM. We need a full dump for hibernation mode, when all data from RAM is loaded onto the hard drive.
In Windows 7, the dump parameters are hidden quite deeply. Enter in the search bar in the menu " Start" word " system", For example.

Select result " System" A window will open. There is a list of options at the top right, select the last one - “ Advanced System Settings».

One of the most common Windows failures is system exceptions, which the user sees in the form of a “blue screen of death” (BSOD). As a rule, this fatal error occurs either due to a malfunction of drivers, hardware (usually when loading the OS) or due to the action of viruses and antiviruses.
The blue screen of death contains information about the reasons that caused the exception (in the form of a STOP error code of the form 0x0000007b), memory addresses that were accessed when an exception occurred, and other useful information. Such information is called a STOP error, the variable parameters of which are precisely memory addresses. Sometimes it also contains the name of the file that caused the exception.
All this information is not displayed on the screen for long (up to 100 seconds), after which the computer reboots. During this short time, as a rule, a memory dump is generated and written to a file. One of the important professional methods for diagnosing failures is memory dump analysis, which will be discussed in detail in this article.
What is a dump
- dump (English) – garbage heap; dump; hole; slum.
- dump (memory dump) – 1) dump, outputting the contents of RAM to print or screen; 2) a “snapshot” of RAM; data obtained as a result of dumping; 3) emergency removal, shutdown, reset.
- dumping – dumping, dump removal.
Settings for saving a memory dump are stored in the Windows system registry.
Information about the memory dump in the system Registry:
In the Windows Registry section, a crash dump is defined by the following parameters:
– REG_DWORD parameter AutoReboot with the value 0×1 (option Automatically reboot the auxiliary window Boot and Restore of the System Properties dialog box);
– REG_DWORD parameter CrashDumpEnabled with a value of 0×0, if a memory dump is not created; 0×1 – Complete memory dump; 0×2 – Kernel memory dump; 0x3 – Small memory dump (64KB);
– REG_EXPAND_SZ DumpFile parameter with the default value %SystemRoot%\MEMORY.DMP (dump file storage location);
– REG_DWORD parameter LogEvent with a default value of 0×1 (option Log event to the system log of the Boot and Recovery window);
– REG_EXPAND_SZ MinidumpDir parameter with the default value %SystemRoot%\Minidump (Small dump folder option of the Boot and Recovery window);
– REG_DWORD parameter Overwrite with a default value of 0×1 (option Overwrite existing dump file of the Boot and Restore window);
– REG_DWORD parameter SendAlert with a default value of 0x1 (option Send administrative alert of the Boot and Recovery window).
How the system creates a crash dump file
During boot, the operating system checks the crash dump settings in the registry key. If at least one parameter is specified, the system generates a map of disk blocks occupied by the paging file on the boot volume and stores it in memory. The system also determines which disk device driver controls the boot volume, calculates checksums for the driver's memory image, and for data structures that must be integer for the driver to perform I/O operations.
After a failure, the system kernel checks the integrity of the page file map, disk driver, and disk driver control structures. If the integrity of these structures is not violated, then the system kernel calls special I/O functions of the disk driver designed to save the memory image after a system failure. These I/O functions are self-contained and do not rely on kernel services because the programs responsible for writing the crash dump cannot make any assumptions about which parts of the system kernel or device drivers were damaged when a crash occurred. The system kernel writes data from memory to the paging file sector map (it does not have to use file system drivers).
First, the system kernel checks the status of each component involved in the dump process. This is done so that when writing directly to disk sectors, it does not damage data located outside the page file. The size of the page file should be 1 MB larger than the size of physical memory, because when information is written to the dump, a header is created that contains the crash dump signature and the values of several critical system kernel variables. The header is less than 1MB, but the operating system can increase (or decrease) the size of the page file by at least 1MB.
After the system boots, Session Manager (Windows NT Session Manager; disk address - \WINDOWS\system32\smss.exe) initializes the system page files, using its own NtCreatePagingFile function to create each file. NtCreatePagingFile determines whether the page file being initialized exists and, if so, whether it has a dump header. If there is a header, then NtCreatePagingFile sends a special code to the Session Manager. Session Manager then starts the Winlogon process (Windows NT Logon Program; disk address is \WINDOWS\system32\winlogon.exe), which is notified of the existence of a crash dump. Winlogon runs the SaveDump program (Windows NT Memory Copy Program; disk address - \WINDOWS\system32\savedump.exe), which analyzes the dump header and determines further actions in an emergency situation.
If the header indicates the existence of a dump, then SaveDump copies the data from the page file to the crash dump file, the name of which is specified by the REG_EXPAND_SZ parameter of the DumpFile section of the Registry. While SaveDump rewrites the dump file, the operating system does not use the part of the page file that contains the crash dump. During this time, the amount of virtual memory available to the system and applications is reduced by the dump size (and messages may appear on the screen indicating that virtual memory is low). SaveDump then informs the memory manager that the dump has completed saving, and it releases the part of the page file in which the dump is stored for general use.
After saving the dump file, the SaveDump program records the creation of a crash dump in the System event log, for example: “The computer was rebooted after a critical error: 0x100000d1 (0xc84d90a6, 0x00000010, 0x00000000, 0xc84d90a6). Memory copy saved: C:\WINDOWS\Minidump\Mini060309-01.dmp".
If the Send administrative alert option is enabled, SaveDump sends an alert to the administrator.
Types of dumps
- Full memory dump writes the entire contents of system memory when a fatal error occurs. For this option, you must have a paging file on the boot volume, the size of which is equal to the amount of all physical RAM plus 1MB. By default, a complete memory dump is written to the %SystemRoot%\Memory.dmp file. When a new error occurs and a new full memory dump (or kernel memory dump) file is created, the previous file is replaced (overwritten). The Full memory dump option is not available on PCs that have a 32-bit operating system and 2 gigabytes or more of RAM.
When a new error occurs and a new full memory dump file is created, the previous file is replaced.
- Kernel memory dump writes only kernel memory, making the process of writing data to the log when the system suddenly stops proceeds faster. Depending on the amount of physical memory of the PC, in this case the paging file requires from 50 to 800MB or one third of the physical memory of the computer on the boot volume. By default, the kernel memory dump is written to the %SystemRoot%\Memory.dmp file.
This dump does not include unallocated memory or memory allocated to user-mode programs. It includes only memory allocated to the kernel and hardware-dependent layer (HAL) in Windows 2000 and later versions of the system, as well as memory allocated to kernel-mode drivers and other kernel-mode programs. In most cases, such a dump is the most preferable option. It takes up much less space than a full memory dump, while excluding only those memory sectors that are most likely not related to the error.
When a new error occurs and a new kernel memory dump file is created, the previous file is replaced.
- Small memory dump records the smallest amount of useful information necessary to determine the cause of the problem. To create a small memory dump, the page file size must be at least 2MB on the boot volume.
Small memory dump files contain the following information:
- Fatal error message, its parameters and other data;
- list of loaded drivers;
- the processor context (PRCB) on which the failure occurred;
- process information and kernel context (EPROCESS) for the process that caused the error;
- process information and kernel context (ETHREAD) for the thread that caused the error;
- The kernel-mode call stack for the thread that caused the error.
The small memory dump file is used when hard disk space is limited. However, due to the limited information it contains, analysis of this file may not always detect errors that were not directly caused by the thread that was running when the error occurred.
When the next error occurs and a second small memory dump file is created, the previous file is saved. Each additional file is given a unique name. The date is encoded in the file name. For example, Mini051509-01.dmp is the first memory dump file created on May 15, 2009. A list of all small memory dump files is stored in the folder %SystemRoot%\Minidump.
The Windows XP operating system is undoubtedly much more reliable than previous versions, thanks to the efforts of both Microsoft developers, hardware driver developers, and application software developers. However, emergency situations - all kinds of failures and system crashes - are inevitable, and whether the PC user has the knowledge and skills to eliminate them depends on whether he will have to spend a few minutes troubleshooting (for example, updating/debugging a driver or reinstalling an application). program causing a system crash) - or several hours to reinstall/configure the operating system and application software (which does not guarantee the absence of failures and crashes in the future!).
Many system administrators still neglect to analyze Windows crash dumps, believing that working with them is too difficult. It’s difficult, but it’s possible: even if, for example, the analysis of one dump out of ten turns out to be successful, the efforts spent on mastering the simplest techniques for analyzing crash dumps will not be in vain!..
I will give examples from my “sysadmin” practice.
On the local network, for no apparent reason (“the hardware is in order, the absence of viruses is guaranteed, the users have “normal hands”), several workstations with Windows XP SP1/SP2 “on board” went down. It was not possible to boot the computers in normal mode - it got to "Greetings" - and it took forever to reboot. At the same time, the PCs booted into Safe Mode.
Studying the memory dumps made it possible to identify the cause of the malfunction: the culprit turned out to be Kaspersky Anti-Virus, more precisely, fresh anti-virus databases (more precisely, two database modules - base372c.avc, base032c.avc).
...There was another such case. On a local PC running Windows XP SP3, a reboot occurred when trying to open video files in .avi and .mpeg formats. Studying the memory dump allowed us to identify the cause of the problem - the nv4_disp.dll file of the NVIDIA GeForce 6600 video card driver. After updating the driver, the problem was eliminated. In general, the nv4_disp.dll driver is one of the most unstable drivers, which often led to BSOD.
In both of these cases, studying the crash memory dump made it possible to reduce the time for diagnosing and eliminating the malfunction to a minimum (several minutes!).
Memory dump analysis
There are many programs for analyzing crash memory dumps, for example, DumpChk, Kanalyze, WinDbg.
Let's look at analyzing crash memory dumps using the WinDbg program (part of Debugging Tools for Windows).
Installing Debugging Tools
- visit Microsoft Corporation's Web site http://www.microsoft.com/whdc/devtools/debugging/default.mspx;
- download Debugging Tools for Windows, for example, for a 32-bit version of Windows this can be done on the Download the Debugging Tools for Windows page;
- after downloading, run the installation file;
- in the Debugging Tools for Windows Setup Wizard window, click Next;
- in the window with the license agreement, select the I agree –> Next switch;
- in the next window, select the installation type (by default, debugging tools are installed in the \Program Files\Debugging Tools for Windows folder) –> Next –> Install –> Finish;
- To interpret memory dump files, you must also download the Symbol Packages for your version of Windows - go to the Download Windows Symbol Packages page;
- select your version of Windows, download and run the Symbol Packages installation file;
- in the window with the license agreement, click Yes;
- in the next window, select the installation folder (the default is \WINDOWS\Symbols) –> OK –> Yes;
- In the Microsoft Windows Symbols window with the message “Installation is complete,” click OK.
Using WinDbg to Analyze Crash Dumps
- run WinDbg (installed in the \Program Files\Debugging Tools for Windows folder by default);
- select menu File –> Symbol File Path…;
- in the Symbol Search Path window, click the Browse... button;
- in the Browse Folder window, specify the location of the Symbols folder (by default – \WINDOWS\Symbols) –> OK –> OK;
- select menu File –> Open Crash Dump… (or press Ctrl + D);
- in the Open Crash Dump window, specify the location of the Crash Dump File (*.dmp) –> Open;
- in the Workspace window with the question “Save information for workspace?”, check the Don’t ask again –> No box;
- The Command Dump window will open in the WinDbg window<путь_и_имя_файла_дампа>with dump analysis;
- review the memory dump analysis;
- in the “Bugcheck Analysis” section the possible cause of the crash will be indicated, for example, “Probably caused by: smwdm.sys (smwdm+454d5)”;
- to view detailed information, click the “!analyze -v” link in the “Use !analyze -v to get detailed debugging information” line;
- close WinDbg;
- Use the information obtained to eliminate the cause of the problem.
For example, in the following screenshot the cause of the malfunction is the nv4_disp.dll file of the video card driver.
Sometimes even the smallest adjustment in optimizing the Windows XP system can have a beneficial effect on the operation of the entire system. This optimization is especially valuable after you first received a “black mark” - BSOD (Blue Screen of Death). What happens when the Blue Screen of Death appears? Some strange “crazy words” are running across the monitor, the meaning of which is not clear even to experienced users. It is at this moment that a “MEMORY DUMP” is created, a very good tip for optimizing Windows XP.
What is a memory dump and how to close it?
A memory dump is a recording of your PC's RAM onto the hard drive. The contents of this file may be of any interest only to a special caste of users - programmers. But for a “dummies” such a file is of absolutely no interest, which means it is simply not needed. Therefore, you can disable the memory dump function with a clear conscience. By the way, in this way you will free your hard drive from unnecessary records and reduce loading time. Let's move on to the algorithm for closing a memory dump. So!
We perform the following steps:
- Click on the “Start” button (not the start of the computer, but the virtual button located at the bottom left of the screen);
- RIGHT click on “My Computer” and select “Properties” in the window that opens;
- The “System Properties” tab will open, where we are interested in the “Advanced” section;
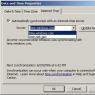
- in this section, select the bottommost item “Download and Recovery” and click the word “Options”;
- A section called “Download and Recovery” will open. We look and select the item “Record debugging information” (it is highlighted in blue) and select “Absent” from the drop-down list;
- Click on “OK”.
Briefly and clearly. Even if you don’t fully understand everything yet, it doesn’t matter: understanding comes with time and experience. And today you have taken the first small step in mastering the deeper principles of the computer system. And let this lesson seem too simple to some, but all those who now consider themselves more or less advanced users themselves started from scratch.