Access control methods. Differentiation of access rights in the network, shared disk space in the local network
- transmitter;
- receiver;
- messages (digital data of a certain format: database file, table, response to a request, text or image);
- transmission media (physical transmission medium and special equipment that ensures the transmission of information).
- Topology of local networks. The topology of a computer network usually refers to the physical location of computers on the network relative to each other and the way they are connected by lines.
- The topology determines the equipment requirements, the type of cable used, communication control methods, operational reliability, and the possibility of network expansion. There are three main types of network topologies: bus, star and ring.
| Local networks(LAN, Local Area Network) connect subscribers located within a small area, usually no more than 2–2.5 km. Local computer networks will allow organizing the work of individual enterprises and institutions, including educational ones, and solving the problem of organizing access to common technical and information resources. | Global networks(WAN, Wide Area Network) connect subscribers located at considerable distances from each other: in different areas of the city, in different cities, countries, on different continents (for example, the Internet). Interaction between subscribers of such a network can be carried out on the basis of telephone communication lines, radio communications and satellite communication systems. Global computer networks will solve the problem of uniting the information resources of all humanity and organizing access to these resources. |
Advantages:
ease of adding new nodes to the network (this is possible even while the network is running);
the network continues to function even if individual computers fail;
inexpensive network equipment due to the widespread use of this topology.
Flaws:
complexity of network equipment;
difficulty diagnosing network equipment malfunctions due to the fact that all adapters are connected in parallel;
a cable break leads to the failure of the entire network;
limitation on the maximum length of communication lines due to the fact that signals are attenuated during transmission and cannot be restored in any way.
Star (star), in which other peripheral computers are connected to one central computer, each of them using its own separate communication line. All information exchange occurs exclusively through the central computer, which bears a very heavy load, so it is intended only for network maintenance.
Advantages:
failure of a peripheral computer does not in any way affect the functioning of the rest of the network;
simplicity of the network equipment used;
all connection points are collected in one place, which makes it easy to control the operation of the network and localize network faults by disconnecting certain peripheral devices from the center;
there is no signal attenuation.
Flaws:
failure of the central computer makes the network completely inoperable;
strict limitation on the number of peripheral computers;
significant cable consumption.
Ring, in which each computer always transmits information to only one computer next in the chain, and receives information only from the previous computer in the chain, and this chain is closed. The peculiarity of the ring is that each computer restores the signal coming to it, so the attenuation of the signal throughout the ring does not matter, only the attenuation between neighboring computers is important.
Advantages:
it’s easy to connect new nodes, although this requires pausing the network;
a large number of nodes that can be connected to the network (more than 1000);
high resistance to overloads.
Flaws:
the failure of at least one computer disrupts the operation of the network;
A cable break in at least one place disrupts the operation of the network.
In some cases, when designing a network, a combined topology is used. For example, a tree is a combination of several stars.
Each computer that operates on a local network must have a network adapter (network card). The function of the network adapter is to transmit and receive signals distributed through communication cables. In addition, the computer must be equipped with a network operating system.
When constructing networks, the following types of cables are used:
unshielded twisted pair. The maximum distance at which computers connected by this cable can be located reaches 90 m. Information transfer speed is from 10 to 155 Mbit/s; shielded twisted pair. Information transfer speed is 16 Mbit/s over a distance of up to 300 m.
coaxial cable. It is characterized by higher mechanical strength, noise immunity and allows you to transmit information over a distance of up to 2000 m at a speed of 2-44 Mbit/s;
fiber optic cable. An ideal transmission medium, it is not affected by electromagnetic fields, allows you to transmit information over a distance of up to 10,000 m at a speed of up to 10 Gbit/s.
The concept of global networks. Global network - These are associations of computers located at a remote distance for the common use of the world's information resources. Today there are more than 200 of them in the world. Of these, the most famous and most popular is the Internet.
Unlike local networks, global networks do not have any single control center. The network is based on tens and hundreds of thousands of computers connected by one or another communication channels. Each computer has a unique identifier, which allows you to “plot a route to it” for the delivery of information. Typically, a global network unites computers that operate according to different rules (having different architectures, system software, etc.). Therefore, gateways are used to transfer information from one type of network to another.
Gateways– These are devices (computers) that serve to connect networks with completely different exchange protocols.
Exchange protocol– this is a set of rules (agreement, standard) that defines the principles of data exchange between different computers on the network.
Protocols are conventionally divided into basic (lower level), responsible for the transfer of information of any type, and application (higher level), responsible for the operation of specialized services.
The host computer of a network that provides access to a common database, enables sharing of input/output devices and user interaction is called server.
A network computer that only uses network resources, but does not give its resources to the network, is called client(often also called workstation).
To work on the global network, the user must have the appropriate hardware and software.
Software can be divided into two classes:
server programs that are located on the network node serving the user’s computer;
client programs located on the user’s computer and using the services of the server.
Global networks provide users with a variety of services: e-mail, remote access to any computer on the network, search for data and programs, and so on.
Task No. 1.
Create a folder in the “My Documents” folder called Mail_1 (the number in the name corresponds to the number of your computer).
Using the text editor Word or WordPad, create a letter to your classmates.
Save this text in the Mail_1 folder of your computer in the letter1.doc file, where 1 is the computer number.
Open a folder on another computer, for example, Mail_2 and copy the file letter1 from your Mail_1 folder into it.
In your Mail_1 folder, read letters from other users, for example letter2. Add your answer to them.
Rename the letter2 .doc file to the letter2_answer1.doc file
Move the file letter2_answer1.doc to the Mail _2 folder and delete it from your folder
Next, repeat steps 2-4 for other computers.
Read messages from other users in your folder and repeat steps 5-8 for them.
Task No. 2. Answer the questions and write them down in your notebook:
| |
| |
| |
| |
| |
| |
| |
| |
|
Automated system ASOMI provides for the possibility of flexible differentiation of user access rights to stored metrological information. This approach ensures the protection of stored and processed information, namely:
- limiting rights to read, modify or destroy;
- the ability to store and transmit information between ASOMI objects in a form that significantly complicates its recognition during unauthorized access or maintenance (in particular, using encryption technologies);
- ensuring the integrity of information, as well as the availability of information for management bodies and authorized users;
- eliminating information leakage during processing and transfer between computer objects.
Access control for users of the ASOMI system is implemented in the context of the following groups of entities: reporting and operational data (protocols), reference data, history logs (logging user actions and data on the history of changes to entities), accounting data (SI cards). Let us consider each of the groups in detail below.
Access to credentials is defined through the following conceptual concepts:
- The person responsible for processing the current status of the measuring instrument is an employee of the enterprise who, in the current status of the measuring instrument, must perform the actions determined by this status and transfer the measuring instrument to a subsequent status within the work cycle of one of the metrological works. Determined from the parameters of the current status of the SI. For example, such a person is a person playing the role of a dispatcher (hereinafter referred to as the Dispatcher), who accepted the SI to perform repairs and is then obliged to transfer it to the person playing the role of the repair performer (hereinafter referred to as the Repair Performer).
- The person materially responsible for the measuring instrument is an employee of the enterprise who is financially responsible for the measuring instrument or operates it. Determined in the SI registration card. As a rule, such a person is the master in charge of this SI.
- Leaders of the “first two” persons - literally by definition. They are determined from the organizational structure of the enterprise according to the following principle: they are the managers of persons from the first two categories “The person responsible for processing the current status of the SI” and “The person materially responsible for the SI”; or they are the heads of a higher division of the enterprise, which includes (subordinates to) a structural unit where persons from the first two categories work as performers. Within the framework of ASOMI, this conceptual principle leads to the fact that information about measuring instruments is available both to all superior managers of the Metrologist and to all senior managers of performers of certain MRs (for example, the head of a workshop has access to information about measuring instruments for which his foremen are responsible).
- The person responsible for metrological supervision and control is, for example, an employee of a calibration, repair department or a metrologist of a structural unit performing supervision and control duties. In accordance with his duties, he has the right to have access to read accounting information about all SI assigned to him.
Thus, those employees of the enterprise who fall into one of the four (possibly several) categories listed above, in relation to a specific SI, have the opportunity to see at their workplace information about the current status of each SI and, accordingly, the data of the SI registration card, including data on the history of metrological work.
In this case, the enterprise employee who is currently responsible for processing the current status of the SI has the right to change the SI information associated with this status and transfer the SI to a subsequent status corresponding to the current MR work cycle, but does not have the right to influence the history of transitions according to SI status diagram.
Now let's look at the Rules and procedure for accessing reference data. Functions such as viewing and using reference data to fulfill their metrological support responsibilities are available to all ASOMI users.
At the same time, access to replenish and edit reference data is allowed only to enterprise employees who perform the role of administrator or controller in the ASOMI system. They are fully responsible for the relevance and correctness of the information contained in the directories. When filling out directories concerning the structure of access rights in ASOMI, data from the directories included in the reference block “Structure of access rights in ASOMI” is used. When filling out specific (additional) reference books, data from the NTD (normative and technical documentation) on measuring instruments, data from the State Register of measuring instruments approved for use in the Russian Federation, and other reliable sources are used.
The rules and procedure for access to reporting and operational data (protocols) are organized as follows. Access to standard reporting implemented in ASOMI is organized by roles in the system. At the same time, for each position, a list of standard reports is indicated (a selection from the general list of all standard ASOMI reports) that an employee occupying this position can generate from his workplace.
As part of reporting, access to special functions can be organized. An example of such a function could be searching and obtaining information about any of the measuring instruments registered in the system according to its various parameters; for example, the master will be able to display in the form of a report a list of all measuring instruments registered in ASOMI, in order, for example, to find replacement options its SI to the same SI, which is being preserved in a neighboring workshop.
Access to operational data (user work protocols) is allowed only to ASOMI Administrators and the Chief Metrologist of the enterprise.
The rules and procedure for assigning and changing access to information data can be assigned or changed only by the ASOMI Administrator.
If you are interested in this product or have any questions,
questions you would like to ask, write:
Introduction.
Formulation of the problem.
Implementation of the task.



End of Procedure
endIf;
Function ProvDostRight(Right)
Request = New Request;
Query.Text = "SELECT
| ValuesAdditionalRightValue
Selection.Next();
Return Sample.Value;
Return False;
endIf;
EndFunction
Procedure OnOpen()
End of Procedure

Conclusion.
Bibliography.
Application.




Introduction.
Today, the Russian accounting automation market is dominated by application solutions developed on the basis of a platform developed by the Russian company 1C. According to sociological studies published on the Internet, in Russia and the CIS countries, 90% of organizations use these systems to automate accounting. Also, these systems have no analogues for full automation of accounting according to RAS. Since accounting and tax reporting processed and stored in such systems constitutes confidential information of any organization, this information must be protected at the proper level. In addition to accounting, many areas of accounting were automated using these systems (for example, personnel records and payroll, operational and management accounting, customer relationships, etc.).
Formulation of the problem.
In this work, I want to describe methods and methods for protecting information in databases built on the basis of 1C Enterprise systems.
Currently, 3 versions of 1C are actively used, namely versions 7.7, 8.1 and 8.2. Version 7.7 has already become obsolete and outdated, and I see no practical point in considering this system as an example. Since version 8.2 went on official sale quite recently, I settled on version “1C Enterprise 8.1”. As an example, we took a previously developed training system for automating operational and accounting tasks and payroll calculations.
Because Since the system operates on the organization’s local network, or on a local computer, protecting this system from possible external attacks falls on the network administrator. In this example, I will mainly describe the mechanism for limiting access to information for specific employees of the organization.
This system allows you to purchase goods into a warehouse and sell them, while it is possible to provide some services to the buyer. When carrying out purchase and sale transactions, the system automatically accumulates accounting and operational accounting data. Also, to implement accounting tasks, it is possible to enter manual transactions, i.e. entering correspondence accounts, indicating the necessary analytics, quantities and amounts on the relevant accounts. For the task of calculating wages, the system has implemented the ability to enter salary accruals, bonuses, travel accruals and enter absenteeism.
The following rights to access objects must be set:
Create administrator rights for full access to all data.
For the head of the organization, grant rights to reports and rights to view all documents.
For accounting employees, provide the right to access accounting documents and reports.
For employees of the operational department, grant the rights to create incoming and outgoing documents, while each employee can create and view documents only for the counterparty to whom he is assigned as a responsible person.
For HR department employees, provide access only to objects necessary for payroll.
For all employees except management, prohibit the printing of unpublished documents.
Set appropriate rights for all users and provide identification using a password or using the operating system.
Implementation of the task.
Access control using roles.
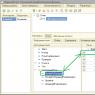
The role mechanism allows you to set rights to read, view, change, delete, conduct, etc. for each configuration object. Configuration objects mean directories (storage of reference information, for example, items, counterparties, etc.), documents (intended to reflect business transactions, for example, invoice, payroll, etc.) and registers that accumulate any information . Figure 1 shows some of the main objects considered in this example.

Figure 1. Main configuration objects.
You can create an unlimited number of roles in the system, in each role you can set rights for one object, and each user can set several roles. When assigning several roles to one user, his rights are set based on the following rule: An action is available if it is allowed in at least one role, and an action is not available if it is prohibited in all roles. You can provide a particular role only visually, and only at the stage of configuring the configuration. At the execution stage, roles cannot be changed in any way.
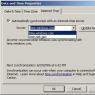
Figure 2 provides an example of establishing full rights for the system administrator.

Figure 2. Setting all rights for a role.
For other users it is necessary to set the necessary rights, this is illustrated in Figure 3.

Figure 3. An example of establishing rights for a specific user.
Segregation of rights at the record level.
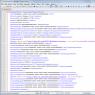
A mechanism for delineating rights at the record level is necessary to restrict access to records in infobase tables according to certain criteria. For example, access only to those entries in the directory of counterparties in which the current user is responsible. For example, Figure 4 shows program text that restricts user access to entries in the list of invoice documents.

Figure 4. Example of record-level access restriction.
The user is identified using the “Current Contractor” session parameter; information about users is stored in the “Employees” directory. The "Current Executor" session parameter is set when the program starts using the following program text:
Procedure When System Starts()
Session Parameters.CurrentExecutor= Directories.Employees.FindByCode(UserName());
End of Procedure
Access control using software methods.
In addition to the role mechanism, the program can configure access to data by writing procedures and functions in the language built into 1C Enterprise. An example is the ability of the system to open a form (the visual element with which the user works) only for viewing when certain conditions are met, for example:
IfSessionParameters.CurrentUser =
Directories.Employees.FindByName("Ivanov") Then
ThisForm.ViewOnly = True;
endIf;
A more complex example is a mechanism that allows, in program execution mode, to grant the necessary rights to the user, for example, permission or prohibition of printing unpublished documents. To implement this task, an enumeration was created that stores a list of additional rights, and a table (Information Register) that stores the values of additional rights. The following procedure has been created in the general module to obtain the right value for the current user:
Function ProvDostRight(Right)
Request = New Request;
Query.Text = "SELECT
| ValuesAdditionalRightValue
| Information Register.Additional Rights Values AS Additional Rights Values
| ValuesAdd.Employee = &Employee
| And ValuesAdditionalRight.Right = &Right";
Request.SetParameter("Employee",
SessionParameters.CurrentExecutor);
Request.SetParameter("Right", Right);
Result = Query.Run();
If Not Result.Empty() Then
Selection = Result.Select();
Selection.Next();
Return Sample.Value;
Return False;
endIf;
EndFunction
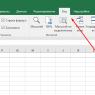
On the Invoice document form there is a “Print” button, which is responsible for generating the printed form of this document. When opening this document, we will set the availability of this button for the user using the following program text:
Procedure OnOpen()
Form Elements.MainFormActions.Buttons.Print.
Availability = ProvDostRight(Enumerations.
Additional Rights.Print of Unposted Documents);
End of Procedure
Assigning roles and means of user identification.
Users who are allowed to work with the program are created in task configuration mode, or the user can be created programmatically. Figure 5 shows an example of creating a user and assigning the appropriate rights to him.

Figure 5. List of users, roles and identification tools.
Conclusion.
In this work, we looked at a fairly simple example of an accounting task, and a simple example of setting up user rights in this task. But this example allows us to clearly illustrate the capabilities of the system in terms of separation of rights, which is very important in many organizations, and gives each employee access only to the information that he needs.
The appendix contains screenshots while the program is running, illustrating the settings made.
Bibliography.
Gabets A.P., Goncharov D.I. 1C:Enterprise 8.1. Simple development examples. – M.: LLC “1C-Publishing”; St. Petersburg: Peter, 2008. – 383 pp.: ill. + CD-ROM.
1C:Enterprise 8.2. Developer's Guide. Part 1. – M.: ZAO “1C”, 2009 – 638 pp.: ill.
Radchenko M.G. 1C:Enterprise 8.1. Practical guide for developers. Examples and typical techniques. M.: 1C-Publishing LLC, 2008. 874 p.: ill.
Belousov P.S. Methodological materials for the training course “Configuring the 1C:Enterprise 8.1 platform.” – M.: ZAO “1C”, 2007 – 272 p.: ill.
Application.
An example of an unauthorized login attempt.

An example of access control by restricting access through roles, the illustration shows an attempt to open a directory that the user does not have rights to read.

An example of delimiting rights at the record level.

An example of a software implementation of the unavailability of the “Print” button in the “Invoice” document.

Access control
| Parameter name | Meaning |
| Article topic: | Access control |
| Rubric (thematic category) | Warfare |
Fig.8.2. Cost and level of authentication technologies
4. The newest trend in authentication is proving the authenticity of a remote user by location . This protective mechanism is based on the use of a space navigation system such as GPS (Global Positioning System). A user with GPS equipment repeatedly sends the coordinates of specified satellites located in the line of sight. The authentication subsystem, knowing the satellite orbits, can determine the user’s location with an accuracy of up to a meter. GPS equipment is simple and reliable to use and relatively inexpensive. This allows it to be used in cases where an authorized remote user must be located in a specific location.
Summarizing the capabilities of authentication mechanisms and means, According to the level of information security, we will distinguish three types of authentication: 1) static; 2) sustainable; 3) constant.
Static authentication provides protection only against unauthorized access in systems where an attacker cannot read authentication information during a work session. An example of a static authentication tool is traditional persistent passwords. Their effectiveness primarily depends on the difficulty of guessing the passwords and how well they are protected. To compromise static authentication, an attacker can snoop, guess, guess, or intercept authentication data.
Strong authentication uses dynamic authentication data that changes with each session. Implementations of strong authentication are systems that use one-time passwords and electronic signatures. Strong authentication provides protection against attacks where an attacker can intercept authentication information and use it in subsequent sessions. At the same time, strong authentication does not provide protection against active attacks, during which a masquerading attacker can quickly (during the authentication session) intercept, modify information and insert it into the stream of transmitted data.
Constant authentication ensures identification of each block of transmitted data, which protects it from unauthorized modification or insertion. An example of the implementation of this type of authentication is the use of algorithms for generating electronic signatures for each bit of transmitted information.
After identification and authentication have been completed, it is extremely important to establish the powers (set of rights) of the subject for subsequent control of the authorized use of computing resources available in the AS. This process is usually called differentiation (logical control) of access.
Typically, the subject's powers are represented by: a list of resources available to the user, and access rights to each resource from the list. Computing resources include programs, data, logical devices, memory, processor time, priority, etc.
The following can be distinguished access control methods: 1) according to lists; 2) using the authority establishment matrix; 3) by privacy levels and categories; 4) password.
1. When access control based on lists the following correspondences are specified: for each user - a list of resources and access rights to them, or for each resource - a list of users and their access rights to a given resource. Lists allow you to set rights down to the user. It is not difficult to add rights or explicitly deny access here. Lists are used in most operating systems and DBMSs.
2. Using the Authority Matrix involves the use of an access matrix (authority table). In the specified matrix, the rows are the identifiers of subjects who have access to the AS, and the columns are the objects (information resources) of the AS. Each element of the matrix can contain the name and size of the resource provided, an access right (read, write, etc.), a link to another information structure that specifies access rights, a link to a program that manages access rights, etc.
Posted on ref.rf
(Table 8.3). This method provides a more unified and convenient approach, since all information about permissions is stored in the form of a single table, and not in the form of different types of lists. The disadvantages of the matrix are its possible bulkiness and non-optimality (most cells are empty).
Table 8.3
Access control - concept and types. Classification and features of the category "Access Control" 2017, 2018.
Laboratory work
Topic: Differentiation of access rights in the network, shared disk space in the local network
Target: mastering techniques for exchanging files between users of a local computer network.
Theoretical information for laboratory work
The main devices for fast transmission of information over long distances are currently the telegraph, radio, telephone, television transmitter, and telecommunication networks based on computer systems.
The transfer of information between computers has existed since the emergence of computers. It allows you to organize the joint work of individual computers, solve one problem using several computers, share resources and solve many other problems.
Under computer network understand a set of hardware and software designed for information exchange and user access to common network resources.
The main purpose of computer networks is to provide users with shared access to information (databases, documents, etc.) and resources (hard drives, printers, CD-ROM drives, modems, access to the global network, etc.).
Network subscribers – objects that generate or consume information.
Network subscribers can be individual computers, industrial robots, CNC machines (computer numerical control machines), etc. Any network subscriber is connected to the station.
Station – equipment that performs functions related to transmitting and receiving information.
To organize interaction between subscribers and stations, a physical transmission medium is required.
Physical transmission medium – communication lines or space in which electrical signals propagate and data transmission equipment.
One of the main characteristics of communication lines or channels is the data transfer rate (bandwidth).
Data transfer rate – the number of bits of information transmitted per unit of time.
Typically, data transfer rates are measured in bits per second (bps) and in multiples of Kbps and Mbps.
Relationships between units of measurement: 1 Kbit/s = 1024 bit/s; 1 Mbit/s =1024 Kbit/s; 1 Gbit/s = 1024 Mbit/s.
A communication network is built on the basis of the physical transmission medium. Thus, a computer network is a collection of subscriber systems and a communication network.
Types of networks.According to the type of computers used, there arehomogeneous Andheterogeneous networks . Heterogeneous networks contain software-incompatible computers.
Based on territorial characteristics, networks are divided into local And global.
| Local networks (LAN, Local Area Network) unite subscribers located within a small area, usually no more than 2–2.5 km. Local computer networks will allow organizing the work of individual enterprises and institutions, including educational ones, and solving the problem of organizing access to common technical and information resources. | Global networks (WAN, Wide Area Network)unite subscribers located at considerable distances from each other: in different parts of the city, in different cities, countries, on different continents (for example, the Internet).Interaction between subscribers of such a network can be carried out on the basis of telephone communication lines, radio communications and satellite communication systems. Global computer networks will solve the problem of uniting the information resources of all humanity and organizing access to these resources. |
|
|
Basic communication network components:
transmitter;
receiver;
messages (digital data of a certain format: database file, table, response to a request, text or image);
transmission media (physical transmission medium and special equipment that ensures the transmission of information).
Topology of local networks. The topology of a computer network usually refers to the physical location of computers on the network relative to each other and the way they are connected by lines.
The topology determines the equipment requirements, the type of cable used, communication control methods, operational reliability, and the possibility of network expansion. There are three main types of network topologies: bus, star and ring.
Bus, in which all computers are connected in parallel to one communication line, and information from each computer is simultaneously transmitted to all other computers. According to this topology, a peer-to-peer network is created. With such a connection, computers can transmit information only one at a time, since there is only one communication line. 
Advantages:
ease of adding new nodes to the network (this is possible even while the network is running);
the network continues to function even if individual computers fail;
inexpensive network equipment due to the widespread use of this topology.
Flaws:
complexity of network equipment;
difficulty diagnosing network equipment malfunctions due to the fact that all adapters are connected in parallel;
a cable break leads to the failure of the entire network;
limitation on the maximum length of communication lines due to the fact that signals are attenuated during transmission and cannot be restored in any way.
Star, in which other peripheral computers are connected to one central computer, each of them using its own separate communication line. All information exchange occurs exclusively through the central computer, which bears a very heavy load, so it is intended only for network maintenance. 
Advantages:
failure of a peripheral computer does not in any way affect the functioning of the rest of the network;
simplicity of the network equipment used;
all connection points are collected in one place, which makes it easy to control the operation of the network and localize network faults by disconnecting certain peripheral devices from the center;
there is no signal attenuation.
Flaws:
failure of the central computer makes the network completely inoperable;
strict limitation on the number of peripheral computers;
significant cable consumption.
Ring, in which each computer always transmits information to only one computer next in the chain, and receives information only from the previous computer in the chain, and this chain is closed. The peculiarity of the ring is that each computer restores the signal coming to it, so the attenuation of the signal throughout the ring does not matter, only the attenuation between neighboring computers is important. 
Advantages:
it’s easy to connect new nodes, although this requires pausing the network;
a large number of nodes that can be connected to the network (more than 1000);
high resistance to overloads.
Flaws:
the failure of at least one computer disrupts the operation of the network;
A cable break in at least one place disrupts the operation of the network.
In some cases, when designing a network, a combined topology is used. For example, tree(tree) – a combination of several stars.
Each computer that operates on a local network must have network adapter (network card). The function of the network adapter is to transmit and receive signals distributed through communication cables. In addition, the computer must be equipped with a network operating system.
When constructing networks, the following types of cables are used:
unshielded twisted pair. The maximum distance at which computers connected by this cable can be located reaches 90 m. Information transfer speed is from 10 to 155 Mbit/s; shielded twisted pair. Information transfer speed is 16 Mbit/s over a distance of up to 300 m. 
coaxial cable. It is characterized by higher mechanical strength, noise immunity and allows you to transmit information over a distance of up to 2000 m at a speed of 2-44 Mbit/s; ![]()
An ideal transmission medium, it is not affected by electromagnetic fields, allows you to transmit information over a distance of up to 10,000 m at a speed of up to 10 Gbit/s.
The concept of global networks. Global network- These are associations of computers located at a remote distance for the common use of the world's information resources. Today there are more than 200 of them in the world. Of these, the most famous and most popular is the Internet.
Unlike local networks, global networks do not have any single control center. The network is based on tens and hundreds of thousands of computers connected by one or another communication channels. Each computer has a unique identifier, which allows you to “plot a route to it” for the delivery of information. Typically, a global network unites computers that operate according to different rules (having different architectures, system software, etc.). Therefore, gateways are used to transfer information from one type of network to another.
Gateways– These are devices (computers) that serve to connect networks with completely different exchange protocols.
Exchange protocol– this is a set of rules (agreement, standard) that defines the principles of data exchange between different computers on the network.
Protocols are conventionally divided into basic (lower level), responsible for the transfer of information of any type, and application (higher level), responsible for the operation of specialized services.
The host computer of a network that provides access to a common database, enables sharing of input/output devices and user interaction is called server .
A network computer that only uses network resources, but does not give its resources to the network, is called client(often also called workstation).
To work on the global network, the user must have the appropriate hardware and software.
Software can be divided into two classes:
server programs that are located on the network node serving the user’s computer;
client programs located on the user’s computer and using the services of the server.
Global networks provide users with a variety of services: e-mail, remote access to any computer on the network, search for data and programs, and so on.
The content of the work:
Task No. 1.
Create a folder on “Exchanger 403” under the name Mail_1 (the number in the name corresponds to the number of your computer).
Using a text editorWord or WordPadwrite a letter to your classmates.
Save this text in the Mail_1 folder on your computer in the file letter1.doc, where 1 is the computer number.
Open a folder on another computer, for example, Mail_2 and copy the file letter1 from your Mail_1 folder into it.
In your Mail_1 folder, read letters from other users, for example letter2. Add your answer to them.
Rename the file letter2.docto file letter2_response1.doc
Move the file letter2_response1.docto the Mail _2 folder and delete it from your folder
Read messages from other users in your folder and repeat steps 5-8 for them.
Task No. 2. Answer the questions:
Indicate the main purpose of a computer network.
Specify an object that is a network subscriber.
Indicate the main characteristics of communication channels.
What is a local area network, a global network?
What is meant by local network topology?
What types of local network topology are there?
Briefly describe the bus, star, and ring topologies.
What is an exchange protocol?
Solve the problem. The maximum data transfer speed on the local network is 100 Mbit/s. How many pages of text can be transmitted in 1 second if 1 page of text contains 50 lines and each line has 70 characters
Task No. 3. Draw a conclusion about the laboratory work done: