Where to enter the verification code on an iPhone. Trusted device management. What is a security code in the App Store and why is it needed? Code Invalidity Problem
To have access to Apple services, each user must register an account, which is commonly called an Apple ID. Like any other account, this one also consists of a login and password. An email address is used as a login, which users “shine” always and everywhere, so it is not difficult to recognize it. Given the large range of programs for selecting and cracking passwords, it is possible to gain access to Apple ID today. Apple understands this, which is why they offer users the protection that is relevant today - two-step authentication. True, this requires a special code, and many users simply do not know where to enter the Apple ID verification code.
By the way, Apple offers two-step verification for iOS 8 (and earlier) users, and for those luckier (iOS 9 and older), two-step verification. You should still know where to enter the Apple ID verification code, because both methods are similar to each other.
What is two-step verification?
This is additional protection, thanks to which no one will gain access to the Apple ID even if he knows the login/password pair. To access it you will still need a specific set of numbers, which he will not have.
If you don't know where to enter your Apple ID verification code, see the following instructions.
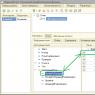
- Go to the official website appleid.apple.com. Enter your login and password, secret code.
- We study the information about the verification that is issued automatically. Next, click “Continue”. It may happen that information about two-step verification will not be displayed. You can find it in the "Edit - Security - Configure - Two-Step Verification" section.
- In the next window you must enter your phone number. It will receive codes via SMS to complete the verification. It is not necessary to choose your phone number. You can indicate the number of your parents, wife, etc.
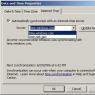
- On the next page you need to check the phone number you specified. You should receive a code via SMS. Enter it in the window that appears. If it is not there, then click on the “Resend code” button.
- After entering the code, the program will prompt you to select auxiliary gadgets to receive a verification code. Here you can specify additional trusted smartphones. Each trusted smartphone will have to be confirmed via SMS.
- After confirmation, you will see the recovery key. It is complex and unchangeable. It needs to be kept in a safe place - it will be used if you suddenly forget the password to your Apple ID account or simply lose your trusted smartphone.
- In the next window you will have to enter the recovery code again. This may seem strange to some, but it's normal. This step focuses the user's attention on the importance of the key. Enter the code from the sheet without copying it programmatically.
- Lastly, we accept the verification conditions.

That's it. The check is activated. Now, when you try to sign in to your Apple ID account, you will need an Apple ID verification code. You now know where to enter it. The attacker also knows, but he will not be able to log into the account, because he simply does not have a trusted smartphone.
By the way, it is best to indicate a trusted phone number not of your own, but of a close relative. If suddenly someone steals your iPhone, they can easily log into your Apple ID, because the verification code will be on the same phone.
Two-Step Verification

There is no practical difference between verification and authentication. At least the user won't notice them. In both cases, you need to know where to enter the Apple ID verification code. In both cases, an SMS with a verification code is sent to the phone, after specifying which access to the account is granted.
Authentication is enabled in the settings. There is a menu item "Password and...". Authentication may also be available in iCloud settings, in the Apple ID tab - “Password and Security”. Click on "Enable". The protection will be enabled, but not yet activated.
Now we need to configure authentication. We enter a trusted number, wait for the code, and confirm the smartphone. Now the protection is activated, next you need to figure out where to enter the Apple ID verification code. When logging into any Apple service, you will need to provide a login and password. And then the code will be sent via SMS. It must be entered after the login/password pair.
What is the difference?

It’s easy to see that there are practically no differences between two-step verification and authentication. Both require an Apple ID verification code to sign in, so what's the difference?
Apple claims that two-factor authentication is more reliable and modern security. And although the user does not see the difference, the authentication system more effectively verifies devices and sends verification codes. Overall the optimization is much better.
Now you know where to enter your Apple ID verification code. But first, the protection must be turned on.
Conclusion
I highly recommend using this protection. Regardless of what operating system you have (old or new), use two-step authentication or verification, as this protection negates any efforts of thieves to find out access to your account. Well, if you don’t know where to enter the Apple ID verification code, then there will be no problems with this, because the user interface is so simple that even a child can figure it out.
04.01.2018
What is a security code in the App Store and why is it needed? Code Invalidity Problem
The security code is a 3-digit number that is absolutely necessary to make purchases online. You can find it on the back of your bank card. The code is usually abbreviated CVV2/CVC2. Users of the Apple store who are going to make purchases there using a card absolutely need to know it. In addition, their card must be registered in the system.
Consulting and management of trusted devices
Creating application passwords
- Sign in.
- Click "Create Password" under "Special App Passwords."
- Follow the steps that appear on the screen.
Use different methods to assign trusted devices and send verification codes; Moreover, it offers an improved user interface. Two-factor authentication is required to use certain features that require increased security.
First, you need to decide whether the selected card is suitable for making online payments. A good alternative to a bank card is the QIWI virtual card, which can be ordered on the payment system website after registration. Now such a card needs to be linked to the system. In this case, you must indicate all the details and necessary information, including the type of card, its number, expiration date and security code. As already mentioned, you can find the latter on the back of the map. In this way, a debit, credit or virtual card is “linked”.
If you want to sign in and you don't have a trusted device at your disposal that can display verification codes, you can request that the code be sent to a trusted phone number via text message or automated phone call.
If you can't login, reset your password or get verification codes, you can. Account recovery is an automatic process that allows you to regain access to your account as quickly as possible while at the same time denying access to anyone who may be impersonating you. This may take a few days or longer, depending on the specific account information you may provide to verify your identity.
This ensures that you are the only person who can access your account, even if someone knows your password. If you want to connect to a new device for the first time, you must provide two pieces of information: your password and a six-digit verification code that automatically appears on your trusted devices.
By entering this code, you confirm that your new device is secure. The verification code is only required once for each new device, unless you sign out of it completely, delete its data, or change your password for security reasons. If you share your account in a browser, you can approve the browser so you don't have to enter a code every time you log in.
1. Open in " Settings" chapter " iCloud»;
2. Select your Apple ID and go to " password and safety»;
3. In the window that opens, activate “ Two-factor authentication»;
4. Click " Continue».
Verification of a trusted phone number
After completing the steps above, a window will appear in which you will need to specify a phone number - it is to this number that the verification code will subsequently be sent. It should also be noted in what form confirmation will be requested: in the form of a text message or a phone call.
It allows you to receive a verification code, which you can then use to verify your identity when accessing your account using a new device or browser. When activating two-factor identification, you must provide at least one trusted number.
Enable two-factor authentication in settings
Enter and confirm your reliable phone number
Enter the verification code to verify your phone number and activate two-factor identification.

How to Set Up Two-Factor Authentication for Apple ID on Mac
To set up two-factor authentication, you must be an iCloud user and have OS X El Capitan (and later) on board.
In this case, this feature is already enabled. If you're already using two-step verification and want to take it to the next level. If your account can't take advantage of two-factor authentication, you can still use it to protect your information.
Information to consider when using two-factor authentication
Once activated, your account can only be accessed by someone with your password and devices or trusted numbers. To keep your account as secure as possible and to ensure you don't lose access to it, follow these steps.
Updating the list of trusted numbers
- Protect all devices with a passcode.
- Update your trust numbers.
- Store trusted devices in a safe place.
1 . Open the Apple menu and go to " System Settings" and then in " iCloud" And " Account».


2 . Select the " Safety».
3 . Click " Enable two-factor authentication».



4 . You should be aware that if two-step verification is already enabled, you should disable it before activating two-factor authentication. Also, some Apple IDs created in iOS 10.3 or macOS 10.12.4 (or later versions of these operating systems) may automatically enable two-factor authentication protection.
6 . Firstly, it is advisable to remember the password for your account. Otherwise, it may happen that this data, being recorded or saved in some file, will end up with third parties.
8 . Thirdly, do not forget to promptly update the list of trusted phone numbers.
9 . It is also important to ensure that the device does not fall into the hands of strangers.
All these security measures can provide the maximum degree of protection for the gadget and the information stored on it.
Manage your Apple ID account
In your account, you can edit information about trusted devices and phones.
Update verified phone numbers
In order to use two-factor authentication, the service database must have at least one trusted phone number. If this number needs to be changed, follow these steps:
- Log in to your Apple ID account;
- Open tab " Safety" and click on the item " Edit».
If you need to specify a verified phone number, you should click " Add a verified phone number" and enter this number. You can confirm it by specifying one of the methods: by sending a code in a text message or by calling. In order to erase a number that is no longer current, click on the icon located next to this number.
Review and management of trusted gadgets
You can view information about gadgets that have received verified status in the “ Devices» in your Apple ID account. There you can also find information regarding these gadgets.

If necessary, the verified device can be removed from the list. After this, it will not be possible to access iCloud and other Apple services until it is authorized again through two-factor authentication.
Many people encounter problems after purchasing a used iPhone, iPad and iPod due to the fact that the device is tied to the account of the former owner of the device sold to you.
Due to the fact that I get a lot of questions like “I bought a used iPhone, but I can’t delete the former owner’s account to enter my own... help!”, in this article I will tell you how to protect yourself from buying a “brick” that is tied up to someone else’s account (due to which you will not be able to fully use the device).
So, before you say goodbye to your hard-earned money for a used iPhone or iPad, iPod, we need to check the activation lock of the device.
Activation lock.
1.
Go from your computer to the link https://www.icloud.com/activationlock/
2.
Enter the IMEI or serial number of the device.
3.
Enter the verification code.
4.
Click the “Continue” button and wait for the test result.
Activation lock will not allow you to activate an iPhone with a new SIM card or activate any iCloud account on this device other than the account linked to the device.
To unlock, you will need to enter the password for the linked account and follow the steps below.
Removing a device from the previous owner's account.
If you have already erased your device
If you see one of these pictures


ask the device owner to enter the Apple ID and password for the attached account. Then you need to remove the device from its iCloud account.
If you cheated and bought a device without checking the activation lock, and found that the device is linked to someone else’s account (see images above), but you have a connection with the previous owner, contact him and ask him to do the following, having first turned on Wi-Fi Fi on device:
- www.icloud.com/find.
- Click All Devices to open a list of devices associated with your account. Then select the device you want to remove from the list. A gray dot or the word “Offline” appears next to the name of the desired device.
- Click Remove from Find My iPhone to remove the device from your account.
After removing a device from the previous owner's account, turn it off. To do this, press and hold the Sleep/Wake button located on the top right side of the device. Then reboot your device and continue setup as normal.
If your device has not yet been erased
If you haven't already erased your device, you'll be able to go to the Lock screen or Home screen as shown below.


If the previous owner is near you and has access to the device
Ask the previous owner to delete all content and settings. To do this, he must go to Settings > General > Reset > Erase Content and Settings. Then he should enter his Apple ID and password. After erasing the data from the device, you can continue the setup process.
If the previous owner is not around
Make sure your device is turned on and connected to a Wi-Fi or cellular network. Once done, contact the previous owner and ask them to follow the steps below to remove the device from their account.
- Sign in to your iCloud account at www.icloud.com/find.
- Click All Devices to open a list of devices associated with your account. Then select the device you want to remove from the list.
- Erase all content and settings on your device by clicking the Erase button. Do not enter a phone number or message when prompted. Click the “Next” button until all data is erased.
- Once the erase is complete, click Remove from Find My iPhone to remove the device from your account.
Once the device is erased and removed from the previous owner's account, you can continue setting it up.
Preparing to sell or give away an iPhone, iPad, or iPod touch
If you still have your iOS device
Before you sell or give your iOS device to someone else, make sure you erase all personal data from it. To protect your data and return your device to factory condition before handing it over to a new owner, follow these steps:
- Go to Settings > General > Reset, then Erase Content and Settings.
- This will remove all data from your device, including credit and debit cards added to Apple Pay, as well as photos, contacts, music, and apps. iCloud, iMessage, FaceTime, Game Center and others will also be disabled.
- If your device is running iOS 7 or later and Find My iPhone is turned on, you'll need to enter your Apple ID and password. By entering your password, you can erase all data from your device and remove it from your account. This will allow the new owner to activate the device.
- When you delete data from your device, its contents will not be deleted from iCloud storage.
- Contact your mobile operator for instructions on how to switch services to the new owner.
When you turn on your device for the first time as a new owner, Setup Assistant will help you complete the device setup process.
Important! Don't manually delete contacts, calendars, reminders, documents, photo streams, or other data while you're connected to an iCloud account, because doing so will also delete the content from iCloud servers and all your iCloud-connected devices.
If you no longer have an iOS device
If you haven't completed the instructions above before selling or giving away your iOS device, follow the steps below.
- Ask the new owner to erase all content and settings as described above.
- If you use iCloud and Find My iPhone is turned on, you can erase your data remotely and remove the device from your account. To do this, go to icloud.com/find, select your device and click the Erase button. After erasing data from your device, click the “Remove from account” button. After you delete your device, you must wait 24 hours before you can activate iMessage on your new device.
- If you can't complete the suggested steps, change your Apple ID password. Changing your password doesn't delete any personal data stored on the device, but it does make it impossible for the new owner to delete the information from iCloud.
If you use Apple Pay, you can also delete your credit or debit card information on iCloud.com. To do this, tap Settings to view the devices that use Apple Pay, then select the device and tap the Remove button next to Apple Pay.
The additional user verification function completely controls all attempts to log into your account and use of applications: find out how to properly use and how to turn off two-factor authentication in your Apple ID on your Apple device.
One of the main advantages of Apple is approach to security and privacy policy user information.
Two-step authentication is one of the modern techniques for achieving the maximum level of security in logging into your account.
The company uses this technology to verify the owner of the gadget when trying to log into an account. Multi-level authentication is a 100% guarantee that only its owner will have access to the system.
Operating principle. Difference in operation of authentication and verification
The activated multi-level authentication function perfectly protects your account from hacking and unauthorized entry by other users.
Only the owner of the ID will be able to log in, because the system will require you to enter two types of data:
- Apple ID password;
- Digital code, which will be sent to all trusted devices - it is proof of legal authorization.
Example: You decide to log in from any browser or client program. For this action you need to enter your username and password. After authorization, you will not be able to log into your account - you must additionally enter a code that confirms authorized entry.
The required code is displayed on all gadgets linked to an Apple ID. Enter the numbers into the iCloud authentication window to access your profile.
A visual diagram of how the function works is shown in the figure:
After the first correct entry of the code, entering numbers will no longer be requested after the next software startup. Re-authentication only required in a few cases:
- When resetting;
- When you re-enter.
Also, the constant introduction of digital codes is mandatory for functions that have an increased degree of security - changing smartphone settings, deleting system parameters, and others.
Verification and authentication. What is the difference?
It is important to distinguish between concepts two-step verification And two-factor authentication , since they have a similar effect, but different meaning.
Examination was implemented and introduced into Apple gadgets back in 2015. The main purpose of the option is additional control. The check is available starting with iOS 9 firmware.
Authentication - This is an advanced version of the check. Apple has improved the function and introduced new security management systems into it. In particular, working with location. The principle of working with cards is the marked “safety” points.
Each person regularly visits the same places, so on the map you can definitely select several points from which you can easily log in.
If the login is made outside these points, a verification code and a warning about the possible actions of an attacker are immediately sent to trusted devices.
As you can see, authentication is indeed a more automated and reliable method of identity control.
The purpose of the verification is to send a code to a trusted gadget, and authentication also analyzes the location of the device and warns the owner of possible danger.

Feature Requirements
Multi-level authentication is designed for the following gadgets:
Disable authentication
Disabling authentication will prevent you from entering additional access codes. You won't have to confirm your location either. Follow the instructions:
- Using a desktop browser go to the cloud storage page iCloud.com;
- Log in to the system- Enter login and password;
- Further type the access code into the text field that appears, which is shown on other gadgets;

- Press the key "Allow" in the window that appears on the mobile device;
- Next, the browser will automatically redirect you to the user page. If you are not included in the trusted list, on your mobile gadget click on "I trust this browser" and click on "Continue";

- After successful login, click on the tile "Settings". It is located on the main page of the desktop version of iCloud. Another option for entering settings is to select your username in the upper right corner. Next, in the drop-down list, click on "iCloud Settings";

- In the window that appears, press the button "Control". It is located next to the account owner's name;

- Next, you will be redirected to the Apple website. In a new window you need to log in by entering your username and password from;

- Go to your account management window and click on the tab "Safety"-"Change";

- Find the field "Disable Authentication" and select it. Next, confirm the action by entering the password, which will be sent to the trusted device.

The two-step authentication system is designed in such a way that to protect users as much as possible from all possible hacking attempts. That is why, in order to completely disable the option, the developers have provided for the need to answer a block of questions that you specified.
Only after entering the correct answers into the text fields will you be able to deactivate the option.

Confirm disconnection:

Trusted devices
Verified device– this is any of your Apple devices. The only requirement is that all gadgets must be linked to one ID. It is on the basis of this binding that a group of trusted devices is created.
You will not be able to confirm authentication from a device that is not part of your Apple gadgets group.
Only one owner of a tablet or computer can work with two-step authentication.
List of trusted devices - this is a list of all gadget models to which a digital code will be sent to confirm entry into the Apple ID or program.
You can view this list in the application itself in the Devices tab.

Trusted numbers
Trusted numbers– this is a list of cellular operator numbers to which a digital access code will be sent for authentication. Messages can come not only in text form, but also in the form of a call from an Apple robot.
When you first set up multi-level authentication, you must specify at least one real phone number.
To add a number, you need to enter it in the field and confirm. As confirmation, enter the code sent to the number in the window that appears.
A SIM card with an associated number must be installed in a trusted device. Otherwise, verification codes will not be received.

What data do you need to remember?
It is important to remember that two-step authentication is a whole set of actions that are aimed at protecting your data.
For full operation of the function You will need to remember or write down the following information:
- Account login and password;
- Custom codes for programs– digital access identifiers that you have independently set in your account;
- Primary key is a set of letters and numbers that is automatically generated after enabling the option. You will need it if you lose access to all trusted numbers and devices.

Be sure to screenshot your master key and move it to a folder on your PC or other device. Also, the code can be written down on a flash drive or piece of paper.
Store this data in this way so that no one can find and use the universal key.
We also recommend that you update trusted numbers in a timely manner. If you change your SIM card, don't forget to enter the new number into your Apple ID. Otherwise, access to the identifier may be lost.
Monitor the physical security of your devices.
Do not leave your smartphone unattended near strangers and use the fingerprint scanner to restrict unlocking of the gadget.
It is important to protect yourself not only from virtual ID hacking, but also from unauthorized access of other people to your phone/tablet.
Enabling the feature
Activating the feature will only take a few minutes.
As a result, you will receive an additional security factor that will protect data in the device memory, installed programs and in cloud storage.
On iPhone and iPad
Follow the instructions to enable authentication on your iPhone:
1 Open your phone settings window;
2 Go to the iCloud field;
3 Click on the item "Password»;

4 Select “Set up 2-factor authentication”;
5 Enter the code that will be sent to your trusted devices and complete the setup. Write the universal key onto physical media.
On Mac OS
On Mac OS, two-step user authentication is only available in El Capitan and newer operating system firmware:
1 Go to the system settings window;
2 Click on the iCloud field and start the account data editing mode;
3 In a new window Click on "Safety". Next, the system will require you to enter the password for the identifier;

4 Click on the key "Set up authentication", which is located at the bottom of the window. Confirm the digital code that will appear on all devices linked to your Apple ID.

Alternative receipt of notifications
Receive access codes m Available not only on trusted devices, but also to the Find iPhone service.
You can set this option in the Apple ID settings (Security-Send access codes).
As a result, the verification code will be sent not only to trusted devices, but also to .
Thus, in one window you will be able to monitor login attempts from suspicious locations and view the access code.
This option only works with authentication. It is not possible to work with cards for verification purposes.

Benefits of Multi-Level Authentication
Any Apple ID stores not only information about linked devices, but also credit card data and personal information of users.
Many people store scans of documents and other important information in the cloud, theft of which can lead to irreversible consequences.
If you want to always be sure that your information is safe, use two-factor authentication. Feature benefits:
- A unified security organization for all Apple gadgets;
- Advanced function control settings;
- Guaranteed protection against all levels and types of hacking.
Disadvantages in the function
Despite all the obvious advantages regarding the security of gadgets, multi-level authentication complicates the life of users - remembering keys, The possibility of losing a number or a trusted device creates a number of problems:
- Along with multi-level authentication It is impossible to use third-party software. For example, iMobie AnyTrans or the popular PhoneRescue utility;
- Difficulty logging into iCloud– due to a flaw in the option, users often encounter system errors even after entering the correct access key to the cloud storage;
- Working with a cellular network. If you are in an area with poor coverage, authentication may not work;
- Linking to codes. The verification can only be carried out if you have a second gadget at hand that is linked to the same Apple ID as the first device.
If you don’t have a second gadget near you at the moment, you can use a permanent key, which is stored in your account settings, but in practice, users very rarely write down or remember it.