What does the hosts file look like in windows 7. What should the hosts file look like? Where is the hosts file located?
It is a “dark forest” for the average user. If you are not sure that this is where the problem with your computer lies, then it is better not to touch anything there at all and leave it to professionals to deal with the problems. Today we will talk about what threats one small and inconspicuous text file. What should it look like? How to distinguish it from a virus?
Definition
First, let's figure out what kind of beast this is - Hosts? This is a file responsible for blocking Internet pages and redirecting IP addresses. If you enter the web address of any Internet resource into it, then the computer user will not be able to access the blocked site or will be redirected to another link specified in the file.
In fact, this file is used by most system administrators to disable social networks for employees at work, as well as to organize and block sites inappropriate for children. So if you cannot access any resource from your work computer, be sure to first check the contents of the file, which we will talk about a little later. Because it looks right
The main thing that determines the authenticity of a file and its belonging to the system and not to viruses is its contents. Or rather, the text written in it. What should the Hosts file look like in Windows 7 and other operating systems from the inside?
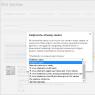
To open the file we are studying, use Notepad. You will see English-language instructions for using this tool. It consists of 20 lines starting with the "#" character. Here's some sample content:
- The first line contains the rights to the OS. 1993-... - the year of Microsoft's existence. The second number will be the release date of your OS version. You can check the authenticity of the file by clicking right click mouse to “My Computer - Properties”. There you can find the OS version and release date. They must match the file.
- Then there are 10 lines explaining what you need this file.
- And finally, examples of how to register a block.

Location
The location of the file also plays an important role. How will the file we are looking at perform its function if it is not in the right folder?
So, what should it look like and where should it be located. Depending on the OS version, it may be located in different folders, but it will always be the original Windows system:
- For Win98 and ME, the “Hosts” file is located in the root of C:\WINDOWS.
- In WinXP and more later versions Hosts is located in the following directory: C:\WINDOWS\SYSTEM32\DRIVERS\ETC. This is where it is located working version file if you have a system or it initially contains several switchable versions and patches. Then you may find a second, similar copy of the file, but it will also be in the system folder.
Size
What does it look like correct file Hosts? Its size is also initially determined. If you opened and saw only what was described in the previous paragraph, then the file size will be 824 bytes. Or it will be empty if the instruction was removed from there.

Any deviation suggests that something other than comments was written into the file. On the one hand, these may be included there system administrators sites. On the other hand, if we're talking about O home computer and you are absolutely sure that no one has “cheated” with it, you should think about whether this file is a virus.
The main thing is to remember that no antivirus works with the Hosts file. More precisely, protective programs block the ability of programs from an unknown manufacturer to change the file. Thus, no one can enter any information there without your knowledge, block access to your favorite sites, or, worse than that, redirect to a copy of the portal you need, where you can inadvertently enter your personal data, which will later go to the attackers. But if this happens, then immediately check your computer for viruses.
Virus
Now you know what the Hosts file should look like. It’s also worth figuring out what it shouldn’t look like.
- This file is not hidden, that is, by going to system folder, in which it is located, you can always see it. If he tries to disguise himself, this is at least a sign of viral activity.
- If you find it in any folder other than the one indicated above, delete it, and it appears again, this should also alert you.

Among other things, the registry can help with the question of what the Hosts file should look like. The fact is that the path to the file is written in a very specific directory, and in this way you can determine whether the file you found is true or false (a virus).
- To see the location of “Hosts” in the registry, run and type regedit.
- Path: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\Tcpip\Parameters
- By clicking on the settings folder, look to the right. In the list of parameters we are interested in DataBasePath. It is in it that the path to the true Hosts file is written. Any deviation from this path means that the file you found is malware.
That's all. We've sorted everything out characteristic features and determined what the Hosts file should actually look like.
In this lesson we will understand what it is hosts file , where it is located, how to change it and what it should be like in normal condition.
Hosts file - regular file, which provides a list of IP addresses that are associated with site names.
It serves as a kind of local DNS server, indicating where the computer should contact when entering a specific address into the browser. Below you can see an example of the contents of such a file.
By default, hosts contains only one IP address (127.0.0.1), which is occupied by your computer.

When we enter the website address in address bar browser, before the site loads, the computer first accesses the hosts file, looks to see whether this address is in the list or not, and only then accesses the DNS servers on the Internet. Unlike servers, we control the file ourselves. If there is no address in it, then the DNS servers are contacted and the site is loaded, but if there is an entry in the file, then the computer looks at which IP address it should contact.
Hosts can be used to block access to Internet resources. To do this, add immediately after the line 127.0.0.1 localhost new line type:
127.0.0.1 site_address
The site address is matched to the computer's IP address and therefore does not load.
Below are the features of editing the hosts file:
Each entry must be on a separate line;
- the IP address comes first in the entry;
- IP and site address must be separated by at least one space;
- the hash symbol # at the beginning of a line allows you to comment it out, i.e. make sure it doesn't work.
Very often, the hosts file is used by attackers. The virus replaces or edits the file so that when you type specific address, it is not the original site that opens, but the site of the attackers, which is very similar to the real one. In addition to redirection, blocking can be used when scammers simply block access to the site.
Where is hosts located?
Now let's figure it out where is hosts located?. Find hosts can be found at:
C:\Windows\System32\drivers\etc
The path presented above is relevant for operating system Windows. For other OSes this path may be different.
The file location can be changed in the registry
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\Tcpip\Parameters\DataBasePath
How to change the hosts file.
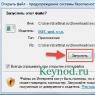
The hosts file does not have an extension, so you cannot open it by simply double-clicking on it with the left mouse button. Click on it right key mouse and select "Open with".


What should the hosts file look like?
Below are original texts hosts files for different Windows operating systems. This is the default file content.
Windows XP
# Copyright (c) 1993-1999 Microsoft Corp.
#
#
# entry should be kept on an individual line. The IP address should
#space.
#
#
# For example:
#
#102.54.94.97 rhino.acme.com
# source server
127.0.0.1 localhost
Windows Vista
# Copyright (c) 1993-2006 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
#space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a "#" symbol.
#
# For example:
#
# 38.25.63.10 x.acme.com # x client host
127.0.0.1 localhost
::1 localhost
Windows 7
# Copyright (c) 1993-2009 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
#space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a "#" symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
# localhost name resolution is handled within DNS itself.
#127.0.0.1 localhost
# ::1 localhost
In conclusion, I would like to say about how to protect yourself from hosts changes. Of course, antiviruses come first. Be sure to use them and keep the database up to date. Also, I recently wrote about a program called Browser Manager. It allows you to track and prevent changes to a file without your participation. And of course, do not install unverified programs and do not run strange files.
If you have any questions, be sure to ask them.
In this lesson we'll talk about what it is RAM computer.
Computer users rarely try to understand the principles of operation various functions the operating system they are using. Most people know that to connect to the Internet via wire or Wi-Fi, you just need to enter your username/password and enter your request in the browser. At the same time, the very principle of the Internet is much more complex. An important role in connecting a computer to the Internet is played by the system hosts file in Windows, which is often attacked by viruses. software. In this material we will tell you: what the hosts file should look like, where to find it in Windows, how to change it and what tasks it performs.
Why is a hosts file needed in Windows?
In the operating system Windows file hosts can be called a kind of “Instructions for connecting to the Internet.” Its main task is to convert incoming character information about the requested domain into the required IP address. When connecting to a specific website on the Internet, the character request is converted into the IP address of the server to which connection in progress computer. The hosts file is responsible for this transformation, and the computer’s request to it has higher priority than the request to DNS servers.
Having studied the functions of the hosts file, virus developers seek to use it for their own purposes. In particular, this file can contain information about prohibiting the computer from connecting to a specific IP address or website. Most often, attackers block access to popular social networks or sites containing anti-virus software through the hosts website on a computer.

Another common model is to deceive the user by replacing information in the hosts file about the IP address to which the browser should connect when entering a specific domain name of the site. In a similar way, attackers direct a computer user to a site that looks similar to the requested resource, for example, a popular social network. An inattentive user enters the login and password for his account in the window that appears, which are sent to the attacker.
To get rid of problems with unwanted redirects to malicious sites, you should keep the hosts file in proper condition and edit it if necessary.
Where is the hosts file located in Windows 10, Windows 8?
Since the hosts file is a system file, and it is installed with the Windows operating system, you should look for it in the appropriate folder. There are two ways to find the hosts file on your computer.
First way
Open a search on your computer, enter as search query"hosts" and start searching required file. This method searching for a hosts file has one significant disadvantage - waste large quantity time. If the computer has large hard disks filled with information, then searching for the hosts file can take tens of minutes, or even more than an hour. To reduce the file search time, you can designate sample disk(or folder) in which it is located.

Second way
The second method is much simpler - just go to the folder where the hosts file is located. IN Windows location This file does not change from version to version, and it is located at " C:\Windows\System32\drivers\etc" If your system disk not C (that is, the disk on which the operating system is installed), then, accordingly, you need to search on it, and not as shown in the example.

In the operating room Windows system You can change the values of the hosts file only if you access it as an administrator. Many virus programs do this without problems, while users often forget that system files can only be changed after accessing them as a computer administrator. Simple instructions how to change the hosts file in Windows:

You now have the ability to change the hosts file in Windows as it is opened through Notepad running with administrator rights. A common mistake among users is when they open the hosts file without administrator rights, they change it, but the information in the file remains the same after saving.
What should the hosts file look like?
If the virus software has changed the hosts file, then you should change the information in it to the standard one in order to again be able to connect to all sites on the Internet. After you have launched the hosts file as an administrator, you need to check the information in it against the ideal. Below you can see what the hosts file should look like unmodified. The easiest way would be to copy the presented code and completely replace what is in your hosts file.
What should be in the hosts file:
# Copyright (c) 1993-2009 Microsoft Corp. # # This is a sample HOSTS file used by Microsoft TCP/IP for Windows. # # This file contains the mappings of IP addresses to host names. Each # entry should be kept on an individual line. The IP address should # be placed in the first column followed by the corresponding host name. # The IP address and the host name should be separated by at least one # space. # # Additionally, comments (such as these) may be inserted on individual # lines or following the machine name denoted by a "#" symbol. # # For example: # # 102.54.94.97 rhino.acme.com # source server # 38.25.63.10 x.acme.com # x client host # localhost name resolution is handled within DNS itself. # 127.0.0.1 localhost # ::1 localhost
Attention: Virus software is becoming more and more developed, and if, at first glance, it seems to you that the hosts file on your computer is exactly the same as what is presented above, this may not be the case. For example, sometimes a virus changes similar English letters to Russian or the number 0 to the letter O. Another common way to manipulate the hosts file is to add information about blocking access to sites much lower visible to the user areas. 
Hosts - a text file containing a database of domain names and used when broadcasting them to network addresses nodes A request to this file takes precedence over calls to DNS servers. Unlike DNS, the contents of the file are controlled by the computer administrator. All of the above means that with the help of this file you can very easily and simply set up access to any of the existing Internet resources. Let's say you wanted to block access to one of the popular social networks, For example, . To do this, you will have to write just a few lines in hosts and save the changes. After this, any user who uses your computer will simply not be able to get into VK, since access will be denied. Of course, with a set of minimal knowledge, this prohibition is easily circumvented.
An ordinary user should theoretically know nothing about the hosts file, since it simply has no use for him. Alas, modern realities are such that we have to learn a lot of new things. The fact is that in the last few years a lot of fraudulent organizations have appeared that use hosts to steal personal information, as well as to take money from a person by redirecting him to other sites for the purpose of extortion. So that you understand what I'm talking about, I'll give you an example. Let's say you decide to go to the same VK. Only instead of your page you see a warning asking you to send an SMS to short number in order to make sure that you a real man, not a robot. There may be other reasons, including in this case it does not matter. You send a message, after which money begins to be debited from your account. This is the fraud of which you have become a participant. You must immediately call your telecom operator, explain the situation and ask for a refund to your account. Most likely, you will have to write a written statement, after which the funds will be returned to you, since they were withdrawn from the account illegally.
How could this happen? By using hosts file you are automatically redirected to a fraudulent site that only appearance resembles the usual VKontakte, while the address in the line can be real (that is, vk.com). However, this is not VK. To verify this, you can open hosts and see extra lines like 111.222.333.333 vk.com, with the help of which the redirection occurs.
Another question arises - how can the hosts change? Yes, it’s very simple: to do this, you just need to install a Trojan on your PC, which will perform the entire operation without your knowledge. And you can pick it up on almost any website.
So, now let's move on to the main question, namely: what does the file look like? I will say right away that it varies slightly depending on the operating system.
Windows XP

# Copyright (c) 1993-1999 Microsoft Corp.
#
#
#space.
#
#
# For example:
#
127.0.0.1 localhost
Windows Vista

#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
#space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a "#" symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
127.0.0.1 localhost
::1 localhost
Windows 7 and 8

# Copyright (c) 1993-2006 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
#space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a "#" symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
# localhost name resolution is handle within DNS itself.
#127.0.0.1 localhost
As you can see, the files are practically no different from each other, with some differences. However, I recommend using your own hosts for each operating system. Just copy the specified data.
By the way, the files are located in the following sections:
- In Windows XP/2003/Vista/7/8 C:\WINDOWS\system32\drivers\etc\hosts
- On Windows NT/2000: C:\WINNT\system32\drivers\etc\hosts
If you do not have the ability or desire to change this file yourself, you can use a utility called, which I recently talked about - it automatically changes the contents of hosts if it contains extra characters.
No matter how much a user owns a computer, he still heard about a file called “hosts”. So, this one Text Document is the most important system file in Windows OS, which is why many people wonder what the hosts file should look like. Since when a computer is infected with viruses, this file is most often distorted. It is capable of both blocking the Internet and negatively affecting the operation of the PC as a whole. This happens as follows: the virus makes certain entries in this file, which, as we said, affect the operation of the computer. To prevent such entries from appearing, you need to know what a clean “hosts” file looks like.
What does the correct “hosts” file look like?
The correct host file should only have 1 single line: “127.0.0.1 localhost”, are also acceptable Windows recording under the hash sign (#) is a kind of explanation of the file (comments), that is, what kind of file it is, how and with what it is eaten. Therefore, all lines starting with the “#” sign do not affect the operation of the system in any way. It is also possible that other lines will appear, only (necessarily) with a different IP address. But still, it is better to adhere to established standards. For example, when installing Adobe software, timely changes are also made to this file. By deleting several lines, you can disrupt the operation of this program, so before doing anything, carefully study the above material.
By following these rules, you will not only be able to configure quality work your PC, but also protect your PC from various types of hacking on social networks. Since it happens that when you log into social media. the network sends out a message, supposedly your account is frozen and to unfreeze it you need to send an SMS to the number... This is pure scam, so in order to prevent similar situations, you need to check this file more often for preventive purposes.