PPP protocol. PPP - configuration example and description
LCP provides a method for establishing, configuring, maintaining, and terminating a directly connected link. The LCP process goes through 4 clearly distinguishable phases:
Organization of the channel and coordination of its configuration. Before any datagrams can be exchanged network layer
(eg IP), the LCP must first open communication and negotiate configuration parameters. This phase ends after the configuration confirmation packet has been sent and received. Definition of quality communication channel
. LCP provides an optional link quality determination phase that follows the link establishment and configuration negotiation phase. This phase examines the link to determine whether the link quality is sufficient to call network layer protocols. This phase is completely optional. LCP may delay transmission of network layer protocol information until this phase is completed. Coordination of network layer protocol configurations. After the LCP completes the link quality determination phase, the configuration
network protocols
can be individually selected by the respective NCPs, and they can be called up and released for later use at any time. If LCP closes a given link, it informs the network layer protocols so that they can take appropriate action.
Termination of the channel. LCP can close the channel at any time. This is usually done at the request of the user (human), but can also occur due to some physical event, such as media loss or a timer expiring.
There are three classes of LCP packets:
Packages for organizing a communication channel. Used to organize and select channel configuration.
Packets for channel termination.
Used to terminate the communication channel.
Packages to maintain the functionality of the channel. Used to maintain and debug the channel. These packets are used to make each of the LCP phases operational.(Integrated Services Digital Network) refers to the set of digital services that are made available to end users. ISDN involves the digitization of the telephone network so that voice, information, text, graphics, music, video and other material sources can be transmitted to the end user over existing telephone wires and received by the end user from a single end user terminal. ISDN proponents paint a picture of a worldwide network much like today's telephone network, except that it uses digital transmission and introduces a variety of new services.
ISDN is an attempt to standardize subscriber services, user/network interfaces, and networking and internetworking capabilities. Standardization of subscription services is an attempt to ensure a level of interoperability on an international scale. User/network interface standardization encourages the development and marketing of these interfaces by third party manufacturers. Standardization of networking and inter-networking capabilities helps achieve the goal of eventual global interconnection by making ISDN networks easily communicate with each other.
Applications of ISDN include high-speed imaging systems (such as Group 1V facsimiles), additional telephone lines in homes to serve the telecom industry, high-speed file transfer, and video conferencing. Voice is sure to become a popular ISDN application.
Many commercial communications networks are beginning to offer ISDN at prices below tariff prices. IN North America commercial communication networks with local network switch (Local-exchange carrier) (LEC) are beginning to provide ISDN services as an alternative to the T1 connections that currently carry most "global telephone service" services (WATS) (wide-area telephone service).
fPYuOP FBL CE, LBL SLIP, PPP RTPFPPLPM OHTSEO DMS FPZP, YuFPVSH RPUSHMBFSH RBLEFSCH YUETE RPUMEDPCHBFEMSHOKHA UCHSSH. according to RPЪCHPMSEF UPPVEBAEINUS UFPTPOBN PVUKhDYFSH PRGYY FBLYE, LBL IP-BDTEU, NBLUINBMSHOSHCHK TBNET RBLEFB PE CHTENS ЪBRKHULB Y PVEUREYUYCHBEF BCHFPTYЪBGYA LMYEOFB . DMS LBTSDPK YЪ LFYI CHPNPTSOPUFEK PPP YNEEF PFDEMSHOSCHK RTPFPPLPM. OJCE NSCH LTBFLP TBUUNPFTYN LFY VBYUOSHE UFBODBTFOSHE VMPLY PPP. ьФП ПУХЦДЭОЕ ДБМЭЛП ОЭ РПМОП, й ЕУМИ ЧШИ ИПФИФЭЧШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШШ surface UP-MYVP EEE PFOPUYFEMSHOP PPP, FP WITH OBUFPSFEMSHOP TELPNEODHA chBN RTPYUYFBFSH UREGYZHYLBGYA CH RFC 1548 FBLCE L, BL Y dozen YMY companion RFC. lTPNE FPZP, CH O"Reilly YJDBOB IPPTPIBS LOYZB" Using & Managing PPP"(BCFPT Andrew Sun).
h UBNPK PUOPCHE PPP METSYF HRTBCHMEOYE RETEDBUYEK DBOOSCHI CHSHCHUPLPZP KHTPCOS, UPLTBEEOOOP HDLC ( High-Level Data Link Control), LPFPTPPE PRTEDEMSEF ZTBOYGSCH UFTHLFHT PPP Y PVEUREYUYCHBEF 16 TBTSDPCH LPOFTPMSHOPK UHNNSHCH. h RTPFPYCHPRMPTSOPUFSH VPMEE RTYNYFYCHOPNH PZHTTNMEOYA SLIP-RBLEFB, PPP URPUPVEO L ЪBICHBFKH VMPLPCH YЪ DTHZYI RTPFPLPMPCH FBLYI, LBL IP, IPX Novell YMY Appletalk. PPP DPUFYZBEF LFPZP, DPVBCHMSS PVMBUFSH RTPFPPLPMB L PUOPCHOPNH HDLC.
rTPFPPLPM HRTBCHMEOYS UCHSHA LCP ( Link Control Protocol) YURPMSH'HEFUS ABOUT THE FOURTH HDLC VHI UPZMBUPCHBOYS PRGYK, YNEAEYI PFOPYEOYE L LBOBMH UCHSY FYRB Maximum Receive Unit(MRU), LPFPTBS ЪBSCHMSEF NBLUINBMSHOSHCHK TBNET RBLEFB PDOPK UFPTPOSCH UCHSY.
chBTSOSHCHK YBZ CH LPOZHYZHTBGYY UCHSY PPP, PTZBOYBGYS LMYEOFULPK BCHFPTYBGYY. iPFS LFP OEPVSBFEMSHOP, OP DMS dial-up MYOYK DPMTSOP VSHFSH UDEMBOP. pVSHYUOP CHSHCHSHCHCHBENSCHK IPUF RTPUIF LMYEOFB ЪBTESYUFTYTPCHBFSH UEVS, DPLBYSCHBS, YuFP PO OBEF UELTEFOSHCHK LMAYU. eUMY LMYEOF OBVTBM OERTBCHYMSHOSHCHK LMAYU, UCHSSH VHDEF RTECHBOB. at PPP BCHFPTYЪBGYS TBVPFBEF PVPYNY URPUPVBNY. FP EUFSH, CHSHCHCHCHBAEIK NPTSEF FBLCE RTPUIFSH, YUFPVSH ACCOUNTING PRBPOBM UEVS. bFY RTPGEDHTSCH KHUFBOPCHMEOYS RPDMYOPUFY OE ЪBCHYUSF DTHZ PF DTHZB. yNEAFUS DCHB RTPFPPLPMB DMS TBMYUOSHI FYRPCH BCHFPTYYBGYY, LPFPTSCHE NSCH PVUKhDYN RPTSE. sing OBSCHCHBAFUS "RTPFPLPM HUFBOPCHMEOYS RPDMYOOPUFY RBTPMS" YMY PAP ( Password Authentication Protocol) CHAP ( Challenge Handshake Authentication Protocol).
LBTSDSCHK UEFECHPK RTPFPPLPM, LPFPTSCHK YURPMSHJHEF LBOBM UCHSY RPDPVOP IP, AppleTalk Y F.D., NPTsEF VShchFSH ULPOZHYZHTYTPCHBO DIOBNYUEULY, YURPMSHJHS Network Control Protocol (NCP). OBRTYNET, YUFPVSH RPUMBFSH IP-RBBLEF, PVB PPP-BVPOEOFB DPMTSOSCH UOBYUBMB PVUKhDYFSH, LBLPK YЪ IP-BDTEUPCH LBTSDSCHK YЪ OYI YURPMSHЪHEF. rTPFPPLPM KHRTBCHMEOYS, YURPMSHKHENSHCHK DMS LFPZP, Internet Protocol Control Protocol(IPCP).
rPNYNP RPUSHMLY IP-RBLEFPCH PPP FBLCE RPDDETTSYCHBEF Van Jacobson header compression IP-RBLEFPCH. lFP NEFPD DMS FPZP, YuFPVSH UPLTBFYFSH ЪБЗПМПЧЛИ TCP-ВМПЛПЧ ШУЭЗП DP ФТЭИ ВБКФПЧ. bFP FBLCE YURPMSH'HEFUS H CSLIP Y PFOPUYFUS L VJ header compression. YURPMSHЪPCHBOYE UTSBFYS NPTSEF VShchFSH ЪBDBOP PE CHTENS ЪBRKHULB YUETE IPCP.
PPP th Linux
h Linux ZHOLGYPOBMSHOSCH CHPNPTSOPUFY PPP TBDEMEOSCH ABOUT DCH YUBUFY: DTBKCHET low-level HDLC (HDLC, IPCP, IPXCP,...), LPFPTSCHK TBNEEEO CH SDTE, Y RPMSHЪPCHBFEMSHULYK DENPO pppd, PVTBVBFSHCHBAEIK TBMYUOSCH RTPFPPLPMSH KHRTBCHMEOYS. FELHABS CHETUIS PPP DMS Linux UPDETSYF SDTP PPP-NPDHMS, pppd Y RTPZTBNNH chat, LPFPTBS YURPMSH'HEFUS DMS FPZP, YUFPVSHCHSHCHRPMOYFSH KHDBMEOOHA UCHSSH.
PPP kernel-DTBKCHET VSCHM OBRYUBO Michael Callahan. dENPO pppd VSHCHM CHCHCHEDEO YЪ TEBMYBGYY PPP DMS Sun Y 386BSD, LPFPTBS VSHMB OBRYUBOB Drew Perkins Y DTHZYNY, Y UEKUBU RPDDETSYCHBEFUS Paul Mackerras. ON VSHM RPTFYTPCHBO CH Linux Al Longyear. rTPZTBNNNB chat VSHMB OBRYUBOB Karl Fox.
fPYuOP FBL CE, LBL Y SLIP, PPP CHSHRPMOEO RPUTEDUFCHPN UREGYBMSHOPK line discipline. dMS FPZP, YUFPVSH YURPMSHЪPCHBFSH RPUMEDPCHBFEMSHOHA MYOYA LBL PPP-UCHSHSH, CHSC UOBYUBMB DPMTSOSCH KHUFBOPCHYFSH UCHSHA U RPNPESHA chBYEZP NPDENB, LBL PVSHYUOP, Y RETECHUFY MYOYA CH PPP-TEZYN. h LFPN NEFPDE CHUE CHIPDSEYE DBOOSCH RTPIPDSF YuETE PPP-DTBKCHET, LPFPTSCHK RTPCHETSEF CHIPDSEYE HDLC-UFTHHLFKhTSCH ABOUT GEMPUFOPUFSH (LBTsDBS HDLC-UFTHLFKHTB OUEEF 16 VYFPCH LPOF TPMSHOPK UHNNSH). h OBUFPSEEE CHTENS BY URPUPVEO L PRGYPOBMSHOPNH RTYNEOOYA Van Jacobson header compression. lBL FPMSHLP Linux UFBMB RPDDETTSYCHBFSH IPX, DTBKCHET PPP VSHM TBUYYTEO DMS FPZP, YuFPVSH PVTBVBFSCHBFSH IPX-RBLEFSH.
Kernel-DTBCCHETKH RPNPZBEF pppd. rPCHEDEOYE pppd NPTsEF RPDUFTBYCHBFSHUS, YURPMSHЪHS TSD PRGYK. PPP RPDTPVOP PUCHEEBEFUS CH LOYSE Using & Managing PPP, S TBUUNPFTA EZP ЪDEUSH MYYSH CH PVEEN CHYDE, RPULPMSHLH RPMOPE PRYUBOIE PYUEOSH ZTPNPJDLP.
bFB TBVPFB OE NPTsEF RPLTSCHFS CHUE BURELFSCH pppd, OP DBUF chBN RPMOPE CHCHEDEOYE. dMS VPMEE RPDTPVOPK YOZHPTNBGYY, PVTBFYFEUSH L man-UFTBOYGBN Y ZHBKMBN README DYUFTYVHFYCHB pppd, LPFPTSHCHE DPMTSOSCH RPNPYUSH chBN TEYYFSH VPMSHYOUFChP CHPRTPUPCH. eUMY X chBU PUFBAFUS RTPVMENSH DBTSE RPUME YUFEOYS CHUEK DPLHNEOFBGYY, FP chShch DPMTSOSCH PVTBFYFSHUS CH LPOZHETEOGYA comp.protocols.ppp . fbn chshch hyobefe nopzpe p pppd, LPOZHETEOGYY RTPUFP OEPVYASFOSCH.
Error 734: The PPP link control protocol was interrupted.
Description of error 734
Error 734 appears when trying to connect via high speed connection PPP. The error appears due to an incorrectly configured connection. Usually the problem occurs because the provider does not use encryption, but your connection settings require it.
Troubleshooting Error 734
Let's try to resolve error 734 on Windows example 7 or 8. To do this you need to get into. There are several ways to do this, but we'll get to it through "Control Panel". To open it, press the keyboard shortcut
Next, click the button
PPP is an Internet standard for transmitting IP packets over serial lines. PPP supports synchronous and asynchronous lines. For some points in the discussion about PPP, as well as PPP versus SLIP, I advise you to look at the document on ftp.uu.net:vendor/MorningStar/papers/sug91-cheapIP.ps.Z (paper) and sug91-cheapIP.shar.Z (overhead projector slides )
2.2 PPP features which may or may not be present
On both sides of compatibility with basic PPP framing, you need to know that many programs add their own additional capabilities. It is advisable to remember that not all freely distributed programs, as well as commercial programs, have a full set of all capabilities.
Demand dial (dialing on request) Connecting a PPP interface and dialing telephone numbers. numbers upon arrival of the package. Disabling the PPP interface after a period of inactivity.
Redial Connecting a PPP interface, which will not be disconnected later and will always keep the connected channel at its disposal.
Campling (see Redial)
Scripting Installation through a series of messages or intermediate connections to establish a PPP connection, more like the sequences used to establish a connection over UUCP.
Parallel Configuring several PPP lines for the same connection to the host, to evenly distribute traffic between them. (In the process of standardization)
Filtering Selection of which packages make sense to start calling the line, and which ones do not. Based on the IP or TCP type of packet or TOS (Type of Service) when making a decision. For example, ignore all ICMP packets.
Header Compression TCP header compression in accordance with RFC1144 Not necessary when used on high-speed lines, but very useful on low-speed lines.
Server Accepts incoming PPP connections, which may also require additional routing.
Tunneling Construction of virtual networks over a PPP connection, through a TCP stream, through an existing IP network. (Build a virtual network over a PPP link across a TCP stream through an existing IP network.)
Extra escaping Byte oriented characters that are not included in the standard character set used when establishing a connection; they can be configured separately, but also do not overlap with those used when establishing a connection. (Byte-stuffing characters outside the negotiated asyncmap, configurable in advance but not negotiable.)
2.3 PPP glossary
Every technology acquires acronyms over time... PPP is no exception. Since almost all terms are used in their English/American transcription, it seems to me that the translation of these abbreviations does not make sense.
ack Acknowledgment
AO Active Open (recently became part of FSM in RFC1331)
C Close
CHAP Challenge-Handshake Authentication Protocol (RFC1334)
D Lower layer down
DES Data Entry Protocol
DNA Digital Network Architecture
IETF Internet Engineering Task Force.
IP Internet Protocol
IPCP IP Control Protocol.
IPX Internetwork Packet Exchange (Novell’s networking stack)
FCS Frame Check Sequence
FSA Finite State Automation
FSM Finite State Machine
LCP Link Control Protocol.
LQR Link Quality Report.
MD4 MD4 digital signature algorithm
MD5 MD5 digital signature algorithm
MRU Maximum Receive Unit
MTU Maximum Transmission Unit
nak Negative Acknowledgment
NCP Network Control Protocol.
NRZ Non-Return to Zero bit encoding. (SYNC ppp default because of availability)
NRZI Non-Return to Zero Inverted bit encoding. (SYNC ppp preferred alternative to NRZ)
OSI Open Systems Interconnect
PAP Password Authentication Protocol (RFC1334)
PDU Protocol Data Unit (same as packet)
PO Passive open
PPP Point to Point Protocol (RFC1548 /RFC1549,1332,1333,1334,1551,1376,1377,1378)
RCA Receive Configure-Ack
RCJ Receive Code-Reject
RCN Receive Configure-Nak or -Reject
RCR+ Receive good Configure-Request
RER Receive Echo-Request
RFC Request for Comments (internet standard)
RTA Receive Terminate-Ack
RTR Receive Terminate-Request
RUC Receive unknown code
sca Send Configure-Ack
scj Send Code-Reject
scn Send Configure-Nak or -Reject
scr Send Configure-Request
ser Send Echo-Reply
sta Send Terminate-Ack
str Send Terminate-Request
ST-II Stream Protocol
TO+ Timeout with counter > 0
TO- Timeout with counter expired
VJ Van Jacobson (RFC1144 header compression algorithm)
XNS Xerox Network Services
General information
Point-to-Point Protocol (PPP) was developed to solve problems associated with the insufficient number of standard means of encapsulating protocols of the “point-to-point IP” type. In addition, PPP was also designed to simplify the issuance and management of IP addresses, asynchronous and bit-oriented synchronous encapsulation, network protocol multiplexing, configuration and testing of communication quality, error detection and options for establishing such network layer features as configuration addresses and setting data compression. To support the above qualities, PPP must provide control over the extended Link Control Protocol (LCP) and the Network Control Protocols (NCPs) family of protocols that are used to establish communication parameters. Today, PPP supports not only IP, but also other protocols, including IPX and DECNet.
PPP Components
PPP provides the ability to transmit datagrams over serial point-to-point lines. It has 3 components:
* A method of providing encapsulation of datagrams over serial PPP lines using the HDLC (High-Level Data Link Control) protocol for packaging datagrams over PPP communications.
* Extended LCP (Link Control Protocol) for establishing, configuring and testing the physical connection (test the data-link connection)
* A family of protocols (NCPs) for establishing and managing other network protocols, in other words: PPP is designed to support multiple network protocols simultaneously.
General Operation
When a PPP connection is established, the PPP driver first sends LCP packets to configure and (possibly) test the communication link. After communications and additional capabilities have been established as needed via LCP, the PPP driver sends NCP frames to change and/or configure one or more network protocols. When this process ends, network packets are able to be transmitted through established connection. It will remain configured and active until certain LCP or NCP packets close the connection, or until some external event occurs that causes the connection to be lost (for example: an inactivity timer or user intervention)
Physical-Layer Requirements
PPP is adapted to work with any DTE/DCE interface, including EIA/TIA-232-C (RS-232), EIA/TIA-422-C(RS-422), EIA/TIA-423-C(RS-423) , ITU-T (CCITT) V.35. The only hardware requirement imposed by PPP is the presence of duplex hardware, whether dedicated or switched, that can operate on asynchronous or bit-oriented synchronous, PPP-transparent packets.
PPP Link Layer
—————
PPP uses the principles, terminology and packet structure described by ISO documents relating to HDLC (ISO 3309-1979) and its extended version:
* ISO 3309:1984/PDAD1 “Addendum 1: Start/stop transmission.”
* ISO 3309-1979: describes the structure of HDLC packets for use in synchronous systems.
* ISO 3309:1984/PDAD1: describes proposals for changes to ISO 3309-1979 that would allow the use of asynchronous systems.
PPP control procedures use definitions and control fields standardized in the documents: ISO 4335-1979 and ISO 4335-1979/Addendum 1-1979.
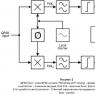
PPP packet format:
1 1 1 2 Variable 2 or 4
Flag Address Control Protocol DATA FCS
Flag: One byte indicating the beginning or end of a packet. The flag field contains the binary sequence: 01111110.
Address: One byte containing the binary sequence: 11111111, Standard broadcast address. PPP does not support station unicasting.
Control: One byte containing the binary sequence: 00000011, which is sent to transmit user data in undivided packets. (for transmission of user data in an unsequenced frame.
Protocol: 2 bytes encode the protocol packed into the PPP protocol time. The protocol values can be found in the Assigned Numbers Request for Comments (RFC) document.
Data: 0 or more bytes that make up the datagram of the protocol specified in the “Protocol” field. The end of the information field is determined by finding the ending sequence and the 2-byte sequence in the FCS field. Default maximum length information field 1500 bytes. However, by mutual agreement, taking into account the use of PPP, other field lengths can be used
Frame Check Sequence (FCS): Typically 16bit (2 bytes). However, by mutual agreement, 32bit (4 bytes) packet integrity control can be used.
PPP Link Control Protocol
PPP LCP provides methods for establishing, configuring, maintaining, and testing point-to-point connections. LCP is divided into 4 phases:
* Configuration and communication - Before transmitting any datagram (eg IP), the LCP must first open a connection and perform an initial exchange of configuration parameters. This stage ends when a packet confirming the configuration has been sent and received back.
* Determining the quality of communication - LCP allows (but does not require) to add a phase of testing the communication channel, this phase will follow immediately after the first. During this phase, it is determined whether the connection is capable of transporting any network protocol with sufficient quality. This phase is optional. The LCP must delay the transfer of any network protocol until this phase is completed.
* Establishing network protocol settings - After the LCP has finished defining the communication parameters, the network protocols must be independently configured by the corresponding NCPs, which can be started or stopped being used at any time.
* End of connection - LCP can terminate the established connection at any time. This may occur due to user demand or due to some physical event, such as loss of carrier or the expiration of a permissible period of unused channel time.
There are three types of LCP packets:
* Establishment packets - Used to establish and configure communications
* Interrupt packets - Used for interrupting established connection
* Communication saving packages - Used for communication management and diagnostics
2.4 PPP relevant RFCs
This is a list of RFCs related to PPP. Some of these documents (obsolete) are outdated...
* 1717 - Sklower, K.; Lloyd, B.; McGregor, G.; Carr, DThe PPP Multilink Protocol (MP). November 1994; 21 p.m. (Format: TXT=46264 bytes)
* 1663 - Rand, DPPP Reliable Transmission. July 1994; 8 p.m. (Format: TXT=17281 bytes)
* 1662 — Simpson, W.,edPPP in HDLC-like Framing. July 1994; 25 p. (Format: TXT=48058 bytes) (Obsoletes RFC 1549)
* 1661 — Simpson, W., edThe Point-to-Point Protocol (PPP). July 1994; 52 p. (Format: TXT=103026 bytes) (Obsoletes RFC 1548)
* 1638 - Baker, F.; Bowen, R.,edsPPP Bridging Control Protocol (BCP). 1994 June; 28 p.m. (Format:TXT=58477 bytes)
* 1619 - Simpson, WPPP over SONET/SDH. May 1994; 4 p.m. Format: TXT=8893 bytes)
* 1618 - Simpson, WPPP over ISDN. May 1994; 6 p.m. (Format: TXT=14896 bytes)
* 1598 - Simpson, WPPP in X.25. March 1994; 7 p.m. (Format: TXT=13835 bytes)
* 1570 — Simpson, W.,ed. PPP LCP Extensions. January 1994; 18 p.m. (Format: TXT=35719 bytes) (Updates RFC 1548)
* 1553 - Mathur, S.; Lewis, M. Compressing IPX Headers Over WAN Media (CIPX). 1993 December; 23 p.m. (Format: TXT=47450 bytes)
* 1552 - Simpson, W. The PPP Internetwork Packet Exchange Control Protocol (IPXCP). 1993 December; 14 p.m. Format: TXT=29174 bytes)
* 1551 - Allen, M. Novell IPX Over Various WAN Media IPXWAN). 1993 December; 22 p.m. (Format: TXT=54210 bytes) (Obsoletes RFC 1362)
* 1549 — Simpson, W.,ed. PPP in HDLC Framing. 1993 December; 18 p.m. (Format: TXT=36353 bytes) Obsolete by RFC 1662)
* 1548 — Simpson, W. The Point-to-Point Protocol (PPP). 1993 December; 53 p. (Format: TXT=111638 bytes) (Obsoletes RFC 1331; Obsoleted by RFC 1661; Updated by RFC 1570)
* 1547 - Perkins, D. Requirements for an Internet Standard Point-to-Point Protocol. 1993 December; 21 p.m. Format: TXT=49811 bytes)
* 1378 - PPP AppleTalk Control Protocol (ATCP). Parker, B. 1992 November; 16 p.m. (Format: TXT=28496 bytes)
* 1377 - PPP OSI Network Layer Control Protocol (OSINLCP). Katz, D. 1992 November; 10 p.m. (Format: TXT=22109 bytes)
* 1376 - PPP DECnet Phase IV Control Protocol (DNCP). Senum, S.J. November 1992; 6 p.m. (Format: TXT=12448 bytes)
* 1362 - Allen, M. Novell IPX Over Various WAN Media IPXWAN). 1992 September; 18 p.m. (Format: TXT=30220 bytes)
* 1334 - PPP authentication protocols. Lloyd, B.; Simpson, W.A. 1992 October; 16 p.m. (Format: TXT=33248 bytes)
* 1333 - PPP link quality monitoring. Simpson, W.A. May 1992; 15 p.m. (Format: TXT=29965 bytes)
* 1332 - PPP Internet Protocol Control Protocol (IPCP). McGregor, G. 1992 May; 12 p.m. (Format: TXT=17613 bytes) (Obsoletes RFC1172)
* 1331 - Point-to-Point Protocol (PPP) for the transmission of multi-protocol datagrams over point-to-point links. Simpson, W.A. May 1992; 66 p. (Format: TXT=129892 bytes) (Obsoletes RFC1171, RFC1172; obsoleted by RFC 1548)
* 1220 - Point-to-Point Protocol extensions for bridging. Baker, F.,ed. April 1991; 18 p.m. (Format: TXT=38165 bytes)
* 1172 - Point-to-Point Protocol (PPP) initial configuration options. Perkins, D.; Hobby, R. 1990 July; 38 p. (Format: TXT=76132 bytes) (Obsoleted by RFC1331, RFC1332)
* 1171 - Point-to-Point Protocol for the transmission of multi-protocol datagrams over Point-to-Point links. Perkins, D. 1990 July; 48 p. (Format: TXT=92321 bytes) (Obsoletes RFC1134; Obsoleted by RFC1331)
* 1134 - Point-to-Point Protocol: A proposal for multi-protocol transmission of datagrams over Point-to-Point links. Perkins, D. 1989 November; 38 p. (Format: TXT=87352 bytes) (Obsoleted by RFC1171)
* 1144 - Compressing TCP/IP headers for low-speed serial links. Jacobson, V. 1990 February; 43 p. Format: TXT=120959 PS=534729 bytes)
- Authentication. Connected routers exchange authentication messages. Two authentication options are available: PAP-based and CHAP-based.
- Compression. This feature improves the efficiency throughput PPP connections, reducing the amount of data per frame transmitted over the link. The protocol decompresses the frame at the destination. There are two compression protocols available on Cisco routers: Stacker and Predictor.
- Error detection. This function detects failure conditions. The Quality and Magic Number parameters help ensure a reliable loop-free data transmission channel. The Magic Number field is used to detect channels that have a loop. Until the Magic-Number configuration parameter negotiation is successfully completed, the null value this parameter. Magic-Number parameter values are generated randomly at each end of the connection.
- PPP Callback. The PPP callback is used to improve security. By using this LCP option, the Cisco router can act as a callback client or a callback server. The client makes the initial call, asks the server for a callback, and completes the initial call. The callback router answers the initial call and makes a callback to the client based on configuration commands. The command used is ppp callback [ accept | request ] .
After setting the parameters, the corresponding field value is inserted into the LCP protocol parameter field.
Basic PPP Setup Commands
Starting PPP on an interface
For PPP settings The encapsulation method used by the serial interface is the interface configuration command encapsulation ppp .
The following example enables PPP encapsulation on serial interface 0/0/0.
R3# configure terminal
R3(config)# interface serial 0/0/0
R3(config-if)# encapsulation ppp
The team encapsulation ppp no arguments. Remember that if your Cisco router is not configured for PPP encapsulation, the serial interfaces will default to HDLC encapsulation.

The figure shows routers R1 and R2 configured to use both an IPv4 address and an IPv6 address on their serial interfaces. PPP is a Layer 2 encapsulation that supports various Layer 3 protocols, including IPv4 and IPv6.
PPP compression commands
You can configure point-to-point software compression on serial interfaces after activating PPP encapsulation. Because in this mode the compression process is called programmatically, it may affect system performance. If the traffic already consists of compressed files such as .zip, .tar, or .mpeg, this feature should not be used. The figure shows the command syntax compress .

To configure PPP transmission compression, enter the following commands.
R3(config)# interface serial 0/0/0
R3(config-if)# encapsulation ppp
R3(config-if)# compress [ predictor | stac ]
PPP Link Quality Monitoring Team
Remember that LCP provides additional stage determining channel quality. At this point, the LCP examines the link to determine whether the link quality is sufficient to support Layer 3 protocols.
Team ppp quality percentage ensures that the channel meets the established quality requirements; otherwise the channel is closed.
The percentage is calculated for both incoming and outgoing directions. Upstream link quality is calculated by comparing the total number of packets and bytes sent with total number packets and bytes received by the destination node. Inbound link quality is calculated by comparing the total number of packets and bytes received with the total number of packets and bytes sent by the destination node.
If the channel quality percentage is not supported, then the channel quality is considered low and the channel is disabled. The Quality Monitor (LQM) implements a time-delay mechanism to ensure that the channel does not undergo sequential activation and deactivation.

The following configuration example monitors the data sent to the channel and prevents frame generation loops (see figure).
R3(config)# interface serial 0/0/0
R3(config-if)# encapsulation ppp
R3(config-if)# ppp quality 80
To disable the LQM tool, use the command no ppp quality .
Multilink PPP Commands
Multilink PPP (also referred to as MP, MPPP, MLP, or Multilink) provides a method for distributing traffic across multiple physical WAN links. Multilink PPP also provides packet fragmentation and reassembly, proper sequencing, cross-vendor capability, and load balancing of incoming and outgoing traffic.
MPPP allows you to fragment packets and send those fragments simultaneously over multiple point-to-point links over the same to a remote address. In response to user defined Load threshold opens several physical channels. MPPP can measure the load on only incoming traffic or only on outgoing traffic, but not the total load on both traffics.
Setting up MPPP is a two-step process (see figure).

Step 1. Creating a multi-channel group.
- The multi-channel interface is created by the team interface multilink number .
- In interface configuration mode, the multilink interface is assigned an IP address. In this example, both an IPv4 address and an IPv6 address are configured on routers R3 and R4.
- Multilink PPP is started on the interface.
- The interface is assigned a multichannel group number.
Step 2. Assigning interfaces to a multichannel group.
The following settings are made on each interface that is part of a multi-channel group.
- PPP encapsulation is enabled.
- Multilink PPP is activated.
- You are assigned to a group by specifying the group number configured in step 1.
To disable multilink PPP, use the command no ppp multilink .
Checking PPP Settings
To verify that HDLC or PPP encapsulation is configured correctly, use the command show interfaces serial . The command output displays the PPP setting (see figure).

After setting HDLC in the command output show interfaces serial The line encapsulation HDL C should appear. If PPP is configured, LCP and NCP status should also be displayed. Note that the IPCP and IPV6CP network control protocols are open to IPv4 and IPv6 because routers R1 and R2 have both IPv4 and IPv6 addresses installed.

In Fig. shows a list of commands for checking PPP.
Team show ppp multilink checks whether PPP multilink is enabled on R3 (see Figure 3).

The output shows the Multilink 1 interface, the host names of the local and remote endpoints, and the serial interfaces included in the multilink group.
PPP authentication
PPP defines an extensible LCP protocol that allows an authentication protocol to be negotiated to verify the identity of the interlocutor before allowing network layer protocols to carry data over the link. RFC 1334 defines two protocols for authentication, PAP and CHAP (see figure).

PAP (Password Authentication Protocol) is a very simple two-step process. It does not use encryption. The username and password are sent unencrypted. Once received, the connection is allowed to be established. CHAP (Challenge Handshake Authentication Protocol) has a higher level of security than PAP. It uses a three-step shared secret key exchange.
The PPP session authentication step is optional. If used, the peer is authenticated after the LCP establishes a channel and selects an authentication protocol. If it is used, authentication is performed before the network layer protocol configuration phase begins.
Authentication options require the caller to enter authentication information. This ensures that the user has network administrator permission to make the call. Connected routers exchange authentication messages.
Password Authentication Protocol (PAP)
One of PPP's many functions is to perform Layer 2 authentication in addition to authentication, encryption, access control, and general security procedures at other layers.
PAP initialization

The PAP protocol provides a simple method of verifying a peer through a two-step handshake. PAP is a non-interactive protocol. If the command is used ppp authentication pap , the username and password can be sent as a single LCP data packet instead of the server asking for a login name and waiting for a response, as shown in Fig. 1. After PPP completes the connection establishment phase, the remote node resends the username/password pair over the channel until the receiving node acknowledges it or completes the connection.
Completion of PAP

At the receiving node, the username-password is checked by the authentication server, which either allows or denies the connection. An acceptance or rejection message is returned to the requester, as shown in Figure. 2.
PAP is not a strong authentication protocol. With PAP, passwords are sent unencrypted, so there is no protection against replay attacks or repeated trial-and-error attacks. The remote node controls the frequency and timing of attempts to enter the network.
However, there are situations in which the use of PAP is justified. For example, despite its disadvantages, PAP can be used in the following conditions.
- A large fleet of installed client applications that do not support the CHAP protocol
- Incompatibility between CHAP implementations from different vendors

Encapsulation and PPP Authentication Process
Scheme in Fig. explains the PPP authentication process when performing PPP setup. The diagram shows a visual example of the decision logic of the PPP protocol.

For example, if an incoming PPP request does not require authentication, PPP goes to next level. If an incoming PPP request requires authentication, the request can be authenticated by either the local database or the security server. As shown in the diagram, after successful authentication the process goes to new level, and if authentication fails, the connection is terminated and the incoming PPP request is ignored.
Follow the steps in the figure to see how R1 establishes a CHAP-authenticated PPP connection to R2.

Step 1. R1 first negotiates a link connection with R2 using LCP, and the two systems agree to use CHAP authentication during PPP LCP negotiation.
Step 2. R2 generates an ID and a random number, then sends this data and its username to R1 as a CHAP control packet.
Step 3. Router R1 uses the username of the challenger (R2) and, based on this name, cross-references it to look for the corresponding password in its local base data. R1 then generates an MD5 hash using R2's router username, ID, random number, and shared secret password. In this example, the shared secret password is boardwalk.
Step 4. Router R1 then sends router R2 the control packet ID, the hash value, and its username (R1).
Step 5. R2 generates its eigenvalue hash code using the ID, shared secret password, and random number originally sent to R1.
Step 6. R2 compares its hash value with the value sent by R1. If the values match, then R2 sends a link establishment response to router R1.
If the request fails authentication, a CHAP packet with error information is generated, consisting of the following components:
- 04 = CHAP error message type
- id = copied from response package
- "Authentication failure" or similar text message, understandable to the user.
The shared secret password must be identical on both routers R1 and R2.
Setting up PPP authentication
To specify the order in which the CHAP and PAP protocols are requested on an interface, use the interface configuration command ppp authentication, as it shown on the picture. To disable authentication, use a negated version of this command ( no ).

After CHAP, PAP, or both authentication is enabled, the local router prompts the remote device evidence of its authenticity. To do this, perform the following steps.
- PAP authentication prompts the remote device for a username and password to compare with the corresponding entry in the local username database or the remote TACACS/TACACS+ database.
- CHAP authentication sends a control request to the remote device. The remote device must encrypt the control value using a shared secret key and return the encrypted value and its name to the local router in a response message. The local router uses the remote device name to look up the corresponding secret key in the local username database or the remote TACACS/TACACS+ database. He uses the one he found The secret key to encrypt the original check value and checks the encrypted values for identity.
Note. TACACS is a dedicated Authentication, Authorization and Accounting (AAA) server used to authenticate users. TACACS clients send a request to the TACACS authentication server. The server authenticates the user, authorizes the user's actions, and tracks the user's actions.
You can enable PAP, CHAP, or both protocols. If both methods are enabled, the method specified first is requested during communication negotiation. If the remote node suggests using the second method or simply refuses to use the first method, the second method is attempted. Some remote devices only support CHAP, and some only support PAP. The order in which methods are specified is based on considerations regarding the remote device's ability to correctly negotiate the appropriate method, as well as data link security considerations. PAP usernames and passwords are sent as open lines and can be intercepted and reused. The CHAP protocol has addressed most of the known security holes.
Configuring PPP with Authentication
The table describes the procedure for configuring PPP encapsulation and PAP/CHAP authentication protocols. It is important to configure this correctly because PAP and CHAP use these parameters for authentication.
Setting up PAP authentication

In Fig. An example of setting up two-way PAP authentication is provided. Each router both performs and passes authentication, so the corresponding PAP authentication commands mirror each other. The PAP username and password sent by each router must match the one specified in the command username name password password another router.
The PAP protocol provides a simple method of verifying a peer through a two-step handshake. This is only done after the channel is initially created. The hostname on one router must match the username configured for PPP on the other router. The passwords must also match. Specify the parameters passing the username and password in the command ppp pap sent-username name password password .
Setting up CHAP authentication
CHAP periodically verifies the identity of the remote host using a three-way handshake. The hostname on one router must match the username configured on the other router. The passwords must also match. The procedure is performed after the initial creation of the channel and can be repeated at any time after communication is established. In Fig. An example of setting up CHAP is given.