How to open a port for remote desktop. What is the standard RDP connection port and how to change it
Good afternoon, dear readers and guests of the blog, today we have the following task: change the incoming port of the RDP service (terminal server) from the standard 3389 to some other one. Let me remind you that the RDP service is a functionality of Windows operating systems, thanks to which you can open a session over the network to the computer or server you need using the RDP protocol, and be able to work on it, as if you were sitting on it locally.
What is RDP protocol
Before changing something, it would be good to understand what it is and how it works, I keep telling you about this. RDP or Remote Desktop Protocol is a remote desktop protocol for Microsoft Windows operating systems, although its origins come from PictureTel (Polycom). Microsoft just bought it. Used for remote work of an employee or user with a remote server. Most often, such servers play the role of a terminal server, on which special licenses are allocated, either per user or per device, CAL. The idea here was this: there is a very powerful server, then why not use its resources together, for example, for a 1C application. This becomes especially relevant with the advent of thin clients.
The world saw the terminal server itself, already in 1998 in the Windows NT 4.0 Terminal Server operating system. To be honest, I didn’t even know then that such a thing existed, and in Russia at that time we all played dandy or sega. RDP connection clients are currently available in all versions of Windows, Linux, MacOS, Android. The most modern version of the RDP protocol at the moment is 8.1.
Default rdp port
I’ll immediately write the default rdp port 3389, I think all system administrators know it.
How the rdp protocol works
And so you and I understand why we came up with the Remote Desktop Protocol, now it’s logical that you need to understand the principles of its operation. Microsoft distinguishes two modes of the RDP protocol:
- Remote administration mode > for administration, you go to the remote server and configure and administer it
- Terminal Server mode > to access the application server, Remote App or share it for work.

In general, if you install Windows Server 2008 R2 - 2016 without a terminal server, then by default it will have two licenses, and two users will be able to connect to it at the same time, the third will have to kick someone out to work. In client versions of Windows, there is only one license, but this can also be circumvented; I talked about this in the article Terminal Server on Windows 7. Also Remote administration mode, you can cluster and load balance, thanks to NLB technology and the Session Directory Service connection server. It is used to index user sessions, thanks to this server the user can log into the remote desktop of terminal servers in a distributed environment. Also required components are a licensing server.

The RDP protocol operates over a TCP connection and is an application protocol. When a client establishes a connection with the server, an RDP session is created at the transport level, where encryption and data transmission methods are negotiated. When all negotiations are determined and initialization is complete, the terminal server sends graphical output to the client and waits for keyboard and mouse input.

Remote Desktop Protocol supports multiple virtual channels within a single connection, allowing you to use additional functionality
- Transfer your printer or COM port to the server
- Redirect your local drives to the server
- Clipboard
- Audio and video


RDP connection stages
- Establishing a connection
- Negotiating encryption parameters
- Server Authentication
- Negotiating RDP session parameters
- Client Authentication
- RDP session data
- Terminating RDP session

Security in the RDP protocol
Remote Desktop Protocol has two authentication methods Standard RDP Security and Enhanced RDP Security, we will look at both in more detail below.
Standard RDP Security
The RDP protocol with this authentication method encrypts the connection using the RDP protocol itself, which is in it, using this method:
- When your operating system starts, a pair of RSA keys is generated
- Proprietary Certificate is being created
- After which the Proprietary Certificate is signed with the RSA key created earlier
- Now the RDP client connecting to the terminal server will receive a Proprietary Certificate
- The client looks at it and verifies it, then receives the server’s public key, which is used at the stage of agreeing on encryption parameters.
If we consider the algorithm with which everything is encrypted, it is the RC4 stream cipher. Keys of different lengths from 40 to 168 bits, it all depends on the edition of the Windows operating system, for example in Windows 2008 Server - 168 bits. Once the server and client have decided on the key length, two new different keys are generated to encrypt the data.
If you ask about data integrity, then it is achieved through the MAC (Message Authentication Code) algorithm based on SHA1 and MD5
Enhanced RDP Security
The RDP protocol with this authentication method uses two external security modules:
- CredSSP
- TLS 1.0
TLS is supported from version 6 of RDP. When you use TLS, an encryption certificate can be created using a terminal server, a self-signed certificate, or selected from a store.
When you use the CredSSP protocol, it is a symbiosis of Kerberos, NTLM and TLS technologies. With this protocol, the check itself, which checks permission to enter the terminal server, is carried out in advance, and not after a full RDP connection, and thereby you save resources on the terminal server, plus there is more reliable encryption and you can log in once (Single Sign On). ), thanks to NTLM and Kerberos. CredSSP only works in OSs no lower than Vista and Windows Server 2008. Here is this checkbox in the system properties
Allow connections only from computers running Remote Desktop with network level authentication.

Change rdp port
In order to change the rdp port, you will need:
- Open the registry editor (Start -> Run -> regedit.exe)
- Let's move on to the next section:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp
Find the PortNumber key and change its value to the port number you need.

Be sure to select a decimal value; for example, I’ll put port 12345.

Once you have done this, restart the Remote Desktop Service via the command line using the following commands:



And we create a new incoming rule for the new rdp port. Let me remind you that the default rdp port is 3389.

We choose what the rule will be for the port

We leave the protocol as TCP and specify a new RDP port number.

The rule will be to allow RDP connection on a non-standard port

If necessary, set the necessary network profiles.

Well, let’s call the rule in a language that we understand.

To connect from Windows client computers, write the address indicating the port. For example, if you changed the port to 12345, and the address of the server (or simply the computer you are connecting to): myserver, then the MSTSC connection will look like this:
mstsc -v:myserver:12345

01. Firewall Well, everything is clear here. The main rule is “ban everything”. Windows 2008 R2 has a pretty good firewall built in, so that's a good place to start. Leave ports 80 and 443 (and maybe 3389 for RDP) open and that's it.
02. Setting up GPO. Go to “Start - Run - secpol.msc - Security Settings - Account Policies - Account Lockout Policy”. And set, for example, “5 attempts” and “5 minutes” - this will block the user for 5 minutes after 5 unsuccessful authorizations.
Go to “Start - Run -gpupdate.msc - PC Configuration - Windows Configuration - Security Settings - Local Policies - Security Settings: Local Security Settings” checkbox to use only RC4_HMAC_MD5.
03. Install a password manager. A bunch of my friends (really a bunch) use the “one complex password for everything” scheme. Even familiar programmers, admins, designers... In general, they are not stupid people. Think again. Even for service accounts (such as database users, etc.), use only complex generated passwords. And keep them in the pass manager. Personally, I use LastPass - it's free, cool, and available as a Chrome extension.
04.Change port for RDP The terminal service port (the same “Remote Desktop”) changes in the registry here: “HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\TerminalServer\WinStations\RDP-Tcp\PortNumber” (don’t forget to open this port on the firewall and restart the RDP service ).

Select a rule based on the port.

We indicate the number of the port we have specified (in the example TCP 50000).
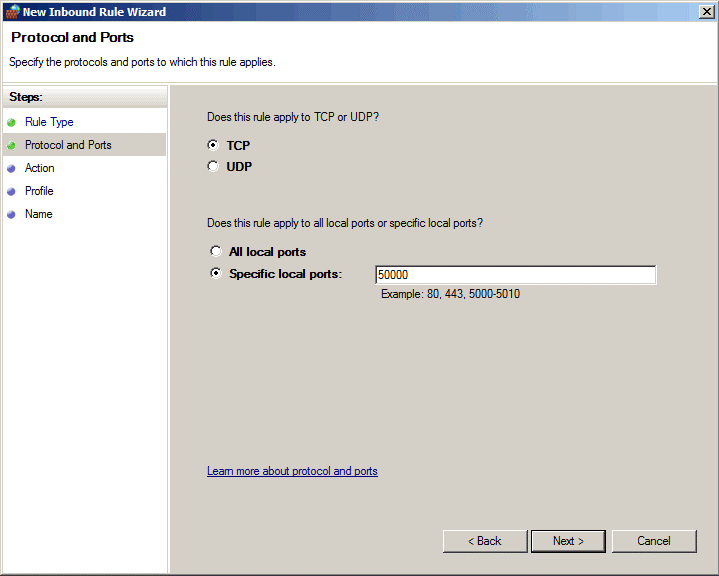
Then we specify the action for our rule - Allow the connection. Here, if necessary, you can enable encryption for our connection.
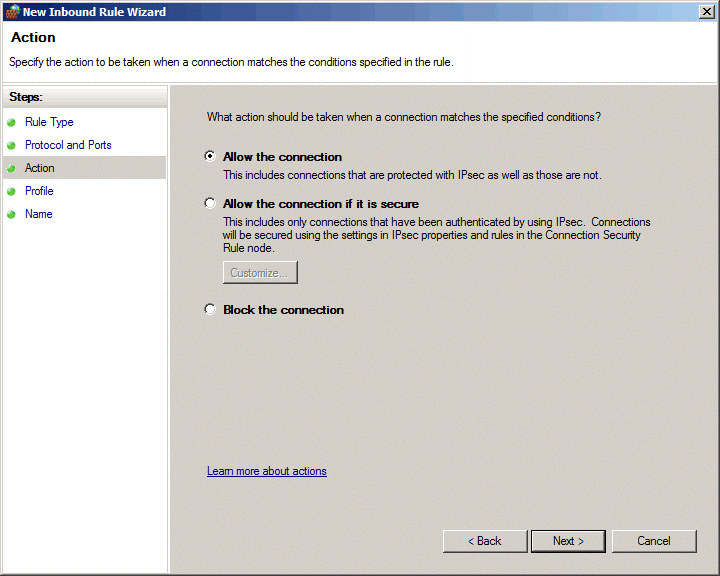
Depending on where the server is located - in a workgroup, in a domain or in public access, we indicate the network profile for which the rule applies.

We name the created rule so that it is easy to identify and click the “Finish” button.
Good afternoon, dear readers and guests of the blog, today we have the following task: change the incoming port of the RDP service (terminal server) from the standard 3389 to some other one. Let me remind you that the RDP service is a functionality of Windows operating systems, thanks to which you can open a session over the network to the computer or server you need using the RDP protocol, and be able to work on it, as if you were sitting on it locally.
What is RDP protocol
Before changing something, it would be good to understand what it is and how it works, I keep telling you about this. RDP or Remote Desktop Protocol is a remote desktop protocol for Microsoft Windows operating systems, although its origins come from PictureTel (Polycom). Microsoft just bought it. Used for remote work of an employee or user with a remote server. Most often, such servers play the role of a terminal server, on which special licenses are allocated, either per user or per device, CAL. The idea here was this: there is a very powerful server, then why not use its resources together, for example, for a 1C application. This becomes especially relevant with the advent of thin clients.
The world saw the terminal server itself, already in 1998 in the Windows NT 4.0 Terminal Server operating system. To be honest, I didn’t even know then that such a thing existed, and in Russia at that time we all played dandy or sega. RDP connection clients are currently available in all versions of Windows, Linux, MacOS, Android. The most modern version of the RDP protocol at the moment is 8.1.
Default rdp port
I’ll immediately write the default rdp port 3389, I think all system administrators know it.
How the rdp protocol works
And so you and I understand why we came up with the Remote Desktop Protocol, now it’s logical that you need to understand the principles of its operation. Microsoft distinguishes two modes of the RDP protocol:
- Remote administration mode > for administration, you go to the remote server and configure and administer it
- Terminal Server mode > to access the application server, Remote App or share it for work.

In general, if you install Windows Server 2008 R2 - 2016 without a terminal server, then by default it will have two licenses, and two users will be able to connect to it at the same time, the third will have to kick someone out to work. In client versions of Windows, there is only one license, but this can also be circumvented; I talked about this in the article Terminal Server on Windows 7. Also Remote administration mode, you can cluster and load balance, thanks to NLB technology and the Session Directory Service connection server. It is used to index user sessions, thanks to this server the user can log into the remote desktop of terminal servers in a distributed environment. Also required components are a licensing server.

The RDP protocol operates over a TCP connection and is an application protocol. When a client establishes a connection with the server, an RDP session is created at the transport level, where encryption and data transmission methods are negotiated. When all negotiations are determined and initialization is complete, the terminal server sends graphical output to the client and waits for keyboard and mouse input.

Remote Desktop Protocol supports multiple virtual channels within a single connection, allowing you to use additional functionality
- Transfer your printer or COM port to the server
- Redirect your local drives to the server
- Clipboard
- Audio and video


RDP connection stages
- Establishing a connection
- Negotiating encryption parameters
- Server Authentication
- Negotiating RDP session parameters
- Client Authentication
- RDP session data
- Terminating RDP session

Security in the RDP protocol
Remote Desktop Protocol has two authentication methods Standard RDP Security and Enhanced RDP Security, we will look at both in more detail below.
Standard RDP Security
The RDP protocol with this authentication method encrypts the connection using the RDP protocol itself, which is in it, using this method:
- When your operating system starts, a pair of RSA keys is generated
- Proprietary Certificate is being created
- After which the Proprietary Certificate is signed with the RSA key created earlier
- Now the RDP client connecting to the terminal server will receive a Proprietary Certificate
- The client looks at it and verifies it, then receives the server’s public key, which is used at the stage of agreeing on encryption parameters.
If we consider the algorithm with which everything is encrypted, it is the RC4 stream cipher. Keys of different lengths from 40 to 168 bits, it all depends on the edition of the Windows operating system, for example in Windows 2008 Server - 168 bits. Once the server and client have decided on the key length, two new different keys are generated to encrypt the data.
If you ask about data integrity, then it is achieved through the MAC (Message Authentication Code) algorithm based on SHA1 and MD5
Enhanced RDP Security
The RDP protocol with this authentication method uses two external security modules:
- CredSSP
- TLS 1.0
TLS is supported from version 6 of RDP. When you use TLS, an encryption certificate can be created using a terminal server, a self-signed certificate, or selected from a store.
When you use the CredSSP protocol, it is a symbiosis of Kerberos, NTLM and TLS technologies. With this protocol, the check itself, which checks permission to enter the terminal server, is carried out in advance, and not after a full RDP connection, and thereby you save resources on the terminal server, plus there is more reliable encryption and you can log in once (Single Sign On). ), thanks to NTLM and Kerberos. CredSSP only works in OSs no lower than Vista and Windows Server 2008. Here is this checkbox in the system properties
Allow connections only from computers running Remote Desktop with network level authentication.

Change rdp port
In order to change the rdp port, you will need:
- Open the registry editor (Start -> Run -> regedit.exe)
- Let's move on to the next section:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp
Find the PortNumber key and change its value to the port number you need.

Be sure to select a decimal value; for example, I’ll put port 12345.

Once you have done this, restart the Remote Desktop Service via the command line using the following commands:



And we create a new incoming rule for the new rdp port. Let me remind you that the default rdp port is 3389.

We choose what the rule will be for the port

We leave the protocol as TCP and specify a new RDP port number.

The rule will be to allow RDP connection on a non-standard port

If necessary, set the necessary network profiles.

Well, let’s call the rule in a language that we understand.

To connect from Windows client computers, write the address indicating the port. For example, if you changed the port to 12345, and the address of the server (or simply the computer you are connecting to): myserver, then the MSTSC connection will look like this:
mstsc -v:myserver:12345

Greetings, dear readers, and Denis Trishkin is in touch again.
Recently I came across such a question as “Remote Desktop” (RDP Windows 7). This tool allows you to work with your computer using another device. For example, a user can use home equipment to perform all the necessary functions on a PC located in the office. Agree, in some situations this option is convenient. But at the same time, everything must be debugged correctly first.
In order to enable rdp, you need to perform several steps:
Establishing a connection( )
To establish a connection via rdp, you first need to know its IP address. To do this, on the desired device, go to the command line (open “” and enter “ cmd»).

In the window that appears, indicate "". A list will open in which you need to find the line with the IPv4 parameter. The numbers indicated opposite are the data we need.

After this, on the computer from which we plan to connect, launch the rdp client or “”. To do this you need to go to " Start" and then go to " Standard».

increase
A window will open where you can set the equipment address (IPv4). Then click "".

If everything is specified as expected, a menu will appear in which you need to enter your login and password to establish a connection.

Before this, there is a choice " Parameters", where various rdp settings are provided:

Update( )
It is important to understand that when constantly working with this tool, you need it to perform all its functions 100%. Otherwise, users may simply not achieve their goals.
For correct operation, all settings must be specified correctly. But in some cases this is not enough. It is also worth installing all upcoming rdp updates from Microsoft on time. This can be done not only in the appropriate center provided in the operating system itself, but also on the official developer page.
Changing the RDP port( )
For a standard connection to a remote computer, port 3389 is used. In this case, interaction occurs via the TCP protocol. Therefore it is used without udp.
To increase the security of the connection, it is possible to change the RDP port. Changing the value will reduce the risk of system intrusion in the event of automated password guessing.
For the procedure you need to use the registry editor:

No connection( )
Sometimes users may encounter a situation where rdp does not work. It is important to note that, judging by statistics, the user still manages to get to the server, but some network tools do not allow him further. There are several effective ways to solve this problem.
Quite often, many users who use remote access sessions have a question about how to change the RDP port. Now let's look at the simplest solutions, and also indicate several main stages in the setup process.
What is the RDP protocol for?
First, a few words about RDP. If you look at the decoding of the abbreviation, you can understand that remote access
In simple terms, this is a tool for a terminal server or workstation. Windows settings (and any version of the system) use default settings that suit most users. However, sometimes there is a need to change them.
Standard RDP port: should it be changed?
So, regardless of the modification of Windows, all protocols have a preset meaning. This is RDP port 3389, which is used to carry out a communication session (connecting one terminal to remote ones).
What is the reason for the situation when the standard value needs to be changed? First of all, only with ensuring the security of the local computer. After all, if you look at it, with a standard port installed, in principle, any attacker can easily penetrate the system. So now let's see how to change the default RDP port.
Changing settings in the system registry
Let us immediately note that the change procedure is carried out exclusively in manual mode, and the remote access client itself does not provide for any reset or installation of new parameters.

First, call the standard registry editor with the regedit command in the Run menu (Win + R). Here we are interested in the HKLM branch, in which we need to go down the partition tree through the terminal server directory to the RDP-Tcp directory. In the window on the right we find the PortNumber key. It is its meaning that we need to change.
We go into editing and see 00000D3D there. Many people are immediately perplexed about what it is. And this is just a hexadecimal representation of the decimal number 3389. To indicate the port in decimal form, we use the corresponding line to display the value representation, and then specify the parameter we need.

After this, we reboot the system, and when trying to connect, specify a new RDP port. Another way to connect is to use the special command mstsc /v:ip_address:XXXXX, where XXXXX is the new port number. But that's not all.
Windows Firewall Rules
Unfortunately, the built-in Windows firewall may block the new port. This means that you need to make changes to the settings of the firewall itself.

Call up the firewall settings with advanced security settings. Here you should first select incoming connections and click on the line to create a new rule. Now we select the item to create a rule for the port, then enter its value for TCP, then allow the connection, leave the profiles section unchanged and finally assign a name to the new rule, after which we click the complete configuration button. All that remains is to reboot the server and, when connecting, specify the new RDP port through a colon in the appropriate line. In theory, there should be no problems.
Forwarding the RDP port on the router
In some cases, when you are using a wireless connection rather than a cable connection, you may need to forward the port on your router. There is nothing complicated about it.
First, in the system properties, we allow and indicate the users who have the right to do so. Then we go to the router settings menu through the browser (192.168.1.1 or at the end 0.1 - it all depends on the router model). In the field (if our main address is 1.1), it is advisable to indicate the address, starting with the third (1.3), and write the rule for issuing the address for the second (1.2).
Then in network connections we use the details view, where you should view the details, copy the physical MAC address from there and paste it into the router parameters.

Now, in the NAT settings section on the modem, enable the connection to the server, add a rule and specify port XXXXX, which needs to be forwarded to the standard RDP port 3389. Save the changes and reboot the router (the new port will not be accepted without a reboot). You can check the connection on some specialized website like ping.eu in the port testing section. As you can see, everything is simple.
Finally, note that the port values are distributed as follows:
- 0 - 1023 - ports for low-level system programs;
- 1024 - 49151 - ports allocated for private purposes;
- 49152 - 65535 - dynamic private ports.
In general, many users usually select RDP ports from the third range of the list to avoid problems. However, both specialists and experts recommend using these values in the settings, since they are suitable for most of the tasks.
As for this particular procedure, it is used mainly only in cases of Wi-Fi connection. As you can already see, with a normal wired connection it is not required: just change the values of the registry keys and add rules for the port in the firewall.