Two-factor authentication. Requirements of the Federal Service for Technical and Export Control for multi-factor authentication. What should I do if I don't remember my password?
Hello, dear readers of the blog site. I would like to continue the topic of interpreting in simple words common terms that can be found everywhere in our computer age. A little earlier we already, as well as about and about.
Today we have a turn authentication. What does this word mean? Is this concept different from authorization or identification? What authentication methods are there, how secure are they, why can errors occur, and why is two-factor authentication better than one-factor authentication?
Interesting? Then let's continue, and I will try not to disappoint you.
What is authentication?
In fact, this is a procedure that is well known not only to us (modern residents), but also to our distant ancestors (almost from time immemorial).
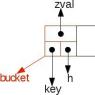
To put it briefly, then authentication is the process of verifying authenticity(authenticity). And it doesn’t matter in what way (there are at least several types). The simplest example. You enter your apartment using the key to open the lock. And if the door does open, it means you have successfully passed authentication.
Let's break everything down in this example:
- The key to the lock is your identifier (inserted and turned - you are identified). In the computer world, this is analogous to the fact that you told the system yours.
- The process of opening (key and lock matching) is authentication. In the computer world, this is analogous to going through the authentication stage (verifying the entered password).
- Opening the door and entering the apartment is already authorization (gaining access). Online is an entrance to a site, service, program or application.
As you probably already understood, two-factor authentication in this example will be answered by the presence of a second lock on the door (or the presence of a dog in the house, which will already carry out its own authentication based on biometric signs - smell, appearance, presence of treats in your pocket) .
One more example. Stamp on a document (in a passport, wax seal on old letters).
As you can see, everything is extremely simple. But today this term is most often understood as electronic authentication, i.e. the process of logging into websites, services, systems, programs, and even connecting to your home WiFi network. But in essence, there are few differences from the example given.
In the electronic version, you will also have an identifier (in the simplest case) and a password (analogous to a lock) necessary for authentication (login to the system, gaining access to the Internet, logging into an online service, etc.).
As I said above, there is several types of authenticators:
As you can see, there is no ideal. Therefore, so-called two-factor (two-step) authentication is often used to enhance security. Let's look at an example.
Two-factor (2FA - two-step) authentication
For example, in and other services related to access to money, two-factor authentication comes down to the following:

What does this give? Significantly improve security and reduce the risk of fraudsters authenticating for you. The fact is that intercepting a one-time password is much more difficult than finding out a multiple-use password. In addition, getting access to a mobile phone (and simply finding out its number) is much more difficult than digging through your computer or email.
But this is just one of examples of two-factor authentication (2FA). Let's take the bank cards already mentioned above. Here, too, two stages are used - authentication using the device (identification code on the card) and by entering a personal password (PIN code).
Another example from movies is when the access code is first entered, and then the retina or fingerprint is checked. In theory, you can do three stages, or four, or five. Everything is determined by the advisability of maintaining between heightened paranoia and a reasonable number of checks, which in some cases have to be done quite often.
In most cases, combining two factors is enough and does not cause very great inconvenience with frequent use.
Authentication errors
When using any of the types of authenticators mentioned above (passwords, devices, and biometrics), errors may occur. Where do they come from and how can they be avoided and resolved? Let's look at an example.
Let's say that you want to connect a computer or smartphone to the wireless network you have in your apartment. To do this, you will be required to enter the network name (identifier) and access password (authenticator). If everything is entered correctly, you will be authorized and you will have access to the Internet from the connected device.
But sometimes you may display an authentication error message. What should you do in this case?
- Well, first of all, check that the data you are entering is correct. Often, when entering, the password is closed with asterisks, which makes it difficult to understand the cause of the error.
- Passwords with characters in different cases (with capital and small letters) are often used, which not everyone takes into account when typing.
- Sometimes the error may be caused by a two-factor authentication system that is not entirely obvious. For example, the router may have access blocking enabled. In this case, the system checks not only whether the username and password are entered correctly, but also whether the Mac address of the device (from which you are logging in) matches the list of allowed addresses. In this case, you will have to go into the router settings (via a browser from a computer connected via Lan) and add the address of this device in the wireless network security settings.
Biometric systems can also produce recognition errors due to their imperfections or due to changes in your biometric data (hoarseness, swelling, numb eyes, cut finger). The same can happen with apps used for two-factor authentication. It is for these cases that a system for obtaining access using backup codes. Essentially, these are one-time passwords that will need to be printed and stored in a desk drawer (safe).
If you cannot authenticate using the usual method (an error is displayed), then backup codes will allow you to log in. For the next login you will need to use a new backup code. But this lifesaver also has the other side of the coin - if these backup codes are stolen or enticed (as happened to me), then they will work as a master key (universal master key) and all protection will go to waste.
Good luck to you! See you soon on the pages of the blog site
You can watch more videos by going to");">

You might be interested
Authentic - what is it, what does authenticity mean? Yandex Account - registration and how to use the service How to delete your page on Odnoklassniki  How to restore a page in Contact (if access is lost, deleted or blocked)
How to restore a page in Contact (if access is lost, deleted or blocked)  How to put a password on a folder (archive or otherwise password protect it in Windows) Why VK won’t load and the browser won’t log into VKontakte Identification - what is it and how is identity confirmed
How to put a password on a folder (archive or otherwise password protect it in Windows) Why VK won’t load and the browser won’t log into VKontakte Identification - what is it and how is identity confirmed
Currently, one of the most discussed and highlighted topics in the field of ensuring maximum protection is two-factor protection. Due to the growing number of services and attacks on user accounts, we must take a closer look at what it is, how it works, and why it is worth using this type of protection.
What is two-factor protection?
Two-factor protection- identification method in any service, when requesting two different types of authentication. This two-layer protection will provide a more secure login and make it more difficult for third parties to intercept your data. In practice, it looks like this: the first step is your login and password; the second stage is a special code that comes to your mobile phone or email (special USB keys or biometric data are used less often). In simple words: in order to get somewhere, you need to confirm the fact that you are making an authorized login to the system. Do you know how a bank vault with individual safes works, where you have one key and the other goes to a bank employee? So here, one key is in your memory, the second comes to your phone or mail.
However, two-factor protection is not a panacea for hacking, but it will greatly complicate the task of attackers who want to gain access to your account; and will also eliminate the shortcomings of the classical protection system. The login method using a login and password causes the following paradox: the longer and more complex the password, the more difficult it is to guess, but at the same time more difficult to remember; and the simpler and more trivial the password, the easier it is to hack it; moreover, the overwhelming number of users set the same passwords for authentication in various services. Using two-factor protection, even if an attacker guesses, finds out, or steals your password, he will also have to steal your cell phone or gain access to your mailbox (which, by the way, can also be protected by a two-factor authentication method).
Although modern man, in trying to replace the entrenched password authentication system with something more interesting and reliable, because of its simplicity, he could not completely get rid of the paradigm familiar to everyone. And examining the different options, we must agree that in our time two-factor protection provides the highest level of protection. Another advantage is the fact that if you attempt an unauthorized login to the system, you will receive a notification, and if at that moment you were not going to log into your account, then it’s time to think about the reliability of your old password and the presence of malware on your personal computer.
Where and in what cases should two-step protection be enabled?
How many logins and passwords for various accounts and mailboxes are publicly available? How many candid, personal photographs of famous personalities have made it to public view? Even such a simple example shows how unreliable the method of one, permanent password is.
If the service you are using contains important, personal data and asks you to install two-layer degree of protection, then do it without hesitation. However, if this is some kind of file hosting service or forum, then I would hardly complicate everything. But regarding social networks, online banking, mailboxes or service services, then definitely yes. Have you noticed that leading banks even use a three-factor level of protection? Namely: a permanent password, a temporary password (on a cell phone), as well as a confirmation call. After all, such institutions suffer the most losses from illegal penetration of the service.

By the way, if you have your own website and the ability to enter two-factor degree of protection, then try to use it. After all, as was said earlier: if you value your account and its contents, then strengthening the protection will be a beneficial decision for everyone.
What types of two-step protection are there?
As mentioned earlier, self-respecting Internet resources and VPN networks use enhanced protection methods such as a code via SMS/call to a mobile phone, letters to the mail, USB keys, smart cards, calls. But besides them, there are also such methods as a code generator (a key fob with buttons and a small screen), SecurID technology and other specific methods that are used mainly by the corporate sectors. Older security methods are also relevant, such as TAN passwords (Transaction Authentication Number). Most likely, you have dealt with this method when, using Internet banking, you were given a piece of paper with pre-generated passwords (one-time passwords). By the way, even not the most progressive banks use two-factor protection. After all, to enter the service you use a card (first key) and a password that you have in your head (second key).
Let's look at authentication methods that are even more unusual for us. Scanning fingerprints, iris, there are even those that are guided by the “pattern” of the heartbeat. Although we do not encounter such methods in everyday life, they are still relevant and necessary in very serious institutions. Electromagnetic tattoos are even being tested, which, following the example of radio chips, can serve as an element two-factor protection. We hope that it won’t take long from idea to implementation. Personally, I wouldn't mind doing this.
Two-factor authentication is based on the use of not only the traditional login-password combination, but also an additional level of protection - the so-called second factor, the possession of which must be confirmed in order to gain access to an account or other data.
The simplest example of two-factor authentication that each of us constantly encounters is withdrawing cash from an ATM. To receive money, you need a card that only you have and a PIN code that only you know. Having obtained your card, the attacker will not be able to withdraw cash without knowing the PIN code, and in the same way will not be able to receive money if he knows it, but does not have the card.
The same principle of two-factor authentication is used to access your accounts on social networks, mail and other services. The first factor is the combination of login and password, and the second factor can be the following 5 things.
SMS codes
Ken Banks/flickr.comVerification using SMS codes works very simply. As usual, you enter your username and password, after which an SMS with a code is sent to your phone number, which you need to enter to log into your account. This is all. The next time you log in, a different SMS code is sent, valid only for the current session.
Advantages
- Generate new codes every time you log in. If attackers intercept your username and password, they will not be able to do anything without the code.
- Link to a phone number. Login is not possible without your phone number.
Flaws
- If there is no cellular signal, you will not be able to log in.
- There is a theoretical possibility of number substitution through the service of the operator or employees of communication stores.
- If you log in and receive codes on the same device (for example, a smartphone), then the protection ceases to be two-factor.
Authenticator apps
 authy.com
authy.com This option is in many ways similar to the previous one, with the only difference being that, instead of receiving codes via SMS, they are generated on the device using a special application (Google Authenticator, Authy). During setup, you receive a primary key (most often in the form of a QR code), on the basis of which one-time passwords with a validity period of 30 to 60 seconds are generated using cryptographic algorithms. Even if we assume that attackers can intercept 10, 100, or even 1,000 passwords, it is simply impossible to predict with their help what the next password will be.
Advantages
- The authenticator does not require a cellular network signal; an Internet connection is sufficient during initial setup.
- Supports multiple accounts in one authenticator.
Flaws
- If attackers gain access to the primary key on your device or by hacking the server, they will be able to generate future passwords.
- If you use an authenticator on the same device you are logging in from, you lose two-factor functionality.
Login verification using mobile applications


This type of authentication can be called a hodgepodge of all the previous ones. In this case, instead of requesting codes or one-time passwords, you must confirm the login from your mobile device with the service application installed. A private key is stored on the device, which is verified every time you log in. This works on Twitter, Snapchat and various online games. For example, when you log into your Twitter account in the web version, you enter your username and password, then a notification arrives on your smartphone asking you to log in, after confirming which your feed opens in the browser.
Advantages
- You don't need to enter anything when logging in.
- Independence from the cellular network.
- Supports multiple accounts in one application.
Flaws
- If attackers intercept your private key, they can impersonate you.
- The point of two-factor authentication is lost when using the same device to log in.
Hardware tokens
 yubico.com
yubico.com Physical (or hardware) tokens are the most secure method of two-factor authentication. Being separate devices, hardware tokens, unlike all the methods listed above, will under no circumstances lose their two-factor component. Most often they are presented in the form of USB keychains with their own processor that generates cryptographic keys that are automatically entered when connected to a computer. The choice of key depends on the specific service. Google, for example, recommends using FIDO U2F tokens, prices for which start at $6 excluding shipping.
Advantages
- No SMS or apps.
- No mobile device required.
- It is a completely independent device.
Flaws
- Need to buy separately.
- Not supported in all services.
- When using multiple accounts, you will have to carry a whole bunch of tokens.
Backup keys
In fact, this is not a separate method, but a backup option in case of loss or theft of a smartphone, which receives one-time passwords or confirmation codes. When you set up two-factor authentication with each service, you are given several backup keys to use in emergency situations. With their help, you can log into your account, unlink configured devices and add new ones. These keys should be stored in a safe place, and not as a screenshot on a smartphone or a text file on a computer.
As you can see, there are some nuances in using two-factor authentication, but they seem complicated only at first glance. What should be the ideal ratio of protection and convenience, everyone decides for themselves. But in any case, all the troubles are more than justified when it comes to the security of payment data or personal information not intended for prying eyes.
You can read where you can and should enable two-factor authentication, as well as which services support it.
Many users whose activities are related to making money on the Internet or storing important information online try to protect their accounts from hacking and theft of confidential data.
Of course, a complex password, including numbers and letters, as well as special characters, is quite reliable protection, but two-factor authentication provides the maximum effect.
However, not every person knows about this option for protecting their accounts, and this despite the fact that today more and more services (mail providers, social networks, etc.) offer to take advantage of this opportunity.
What is two-factor authentication?
So, what type of protection are we talking about? In fact, you've already seen two-step verification. For example, when you are going to perform any operation with money on the WebMoney website, then, in addition to your login and password, you will need to indicate a confirmation code that will be sent to your mobile phone.

In other words, two-factor authentication is the second key to your account. If you activate this option, for example, in Evernote (there is such an option), then an attacker who managed to guess the password for this notes service will face another problem - the requirement to specify a one-time code that is sent to your phone number. It is worth noting that if an attempt is made to hack your account, you will receive an SMS and you will be able to instantly change your password.
Agree that this is a very convenient option, using which you will worry less about the loss of personal information.
Where is the best place to use it?
Of course, some users may object, arguing that two-step authentication is too much “unnecessary steps”, and in general, it is intended for paranoid people who always think that someone is watching them.
Perhaps they are right in some ways. For example, for social networks it is not at all necessary to use this method of protection. Although here one can argue. As a rule, attackers try to hack the accounts of administrators of popular “publics.” And you, most likely, would also not want to one day notice that your account in one of the “social networks” was hacked and completely indecent photos were posted on the “Wall”.
As for other services, for example, Yandex two-factor authentication will allow you to safely store your registration data from WebMoney and others) or letters containing secret information.
Google Account Protection
One of the most popular services today is Google. This is where you can register an email account, store documents on Google Drive, create a blog or channel on YouTube for free, which can later bring you profit.
In order for users to be confident in the safety of documents stored on mail or disk, they are offered two-factor authentication by Google. To activate it, you must log into your account.

Now, having opened, for example, your mailbox, pay attention to the avatar in the upper right corner. Click on it and go to “My Account”. Here you need the “Security and Login” section, namely the “Sign in to Google Account” link.
On the right you will see the “Two-Step Verification” option, where you need to click the arrow to activate it. A window will open in which you are interested in the “Proceed with setup” button. Enter your password and follow further instructions.
Two-factor authentication "Yandex"
Yandex also offers its users quite a lot of useful services. In addition to cloud storage of information on Yandex.Disk, you can get yourself an electronic wallet where you will withdraw the money you earn on the Internet.
And, of course, Yandex did not stand aside and also offers its users to use two-factor authentication to protect documents stored in the mailbox.

To enable it, you will need to follow a few simple steps. Log in to your account and click LMB on your profile photo (top right corner). Select "Passport" from the drop-down menu. A window will open in which you need to click on the “Access Control” link. Set the “slider” to the “ON” position. You will be redirected to a page where you need to click on the “Start setup” button. Now go through the 4 steps to activate two-factor protection.
Social network VKontakte"

As mentioned above, attackers usually try to gain access to the accounts of “admins” of popular groups. But this is not always the case, because simply the personal correspondence of some person well-known on the Internet may be of interest.
It is worth noting that for some users, this method of protecting an account begins to cause irritation over time, since it requires constant entry of a secret code, in addition to the login and password. In such cases, you need to know how to disable two-factor authentication. However, first we will deal with activating this option.
In fact, enabling two-step verification is very simple. Select "My Settings" and then go to the "Security" tab. In the “Login Confirmation” section, click on the “Connect” button. Now follow all the requirements one by one.
Disable two-factor authentication
In order to deactivate two-step protection in Yandex, you will need to go back to your “Passport” by clicking on your avatar. After that, open the “Access Control” section and set the slider to the “Off” position.
Conclusion
Now you know what two-loop authentication is and why it is needed. When using a particular service, you can activate this additional protection or refuse this feature.
Of course, in some cases it is highly recommended to enable two-step verification. For example, when registering on WebMoney, you indicated your email from Yandex. When working on the Internet, you can become a victim of hackers who will hack your mailbox and gain access to your electronic wallet. To prevent this from happening, it is better to install and link your e-mail to your phone. This way you can react quickly if they try to hack you.