Connecting to another computer's webcam. How to connect to someone else's camera? What you need to connect to a webcam remotely
Remote video surveillance is becoming more popular every day, and with the advent of special cloud services, its availability is increasing. Thanks to remote access, you can view what is happening in front of CCTV cameras online from almost anywhere on the planet. All that is needed for this is an Internet connection.
Today, the implementation of this type of video surveillance is available both for large organizations and for private use. To install and configure video surveillance via the Internet in the second case, it is not necessary to resort to the services of specialists - you can easily do it yourself.
Remote video surveillance can be useful in various life situations, for example, for organizing, for monitoring the actions of a nanny caring for a child, for the progress of repairs or construction of a house by workers - there can be a lot of situations.
Necessary components of a remote video surveillance system
To implement Internet video surveillance, the following functional elements are required (depending on the volume of the system and the user’s desires):
- Cameras – IP, or regular web;
- Digital video recorder;
- HDD;
- Router (router);
- Required quantity of UTP network cable;

Required components of a remote video surveillance system
But each individual case is different, and when creating a simple video surveillance system with one IP camera, only it and a dedicated IP address will be enough if you do not need to record an archive on, but only remotely monitor what is happening.
To create online video surveillance without using various cloud servers, you will need a dedicated static IP address. You can get it from your provider, or use the special DynDNS service. By the way, achieving a result in independently obtaining a static IP through such services can be long and difficult, and it is not a fact that you will achieve your goal. So the best option would be to obtain a static IP for an additional fee from the provider (about 200 rubles per month), or use a special cloud service.
In general, today it is possible to implement remote video surveillance without a static IP address and DDNS services. Not long ago, so-called cloud video surveillance services appeared, to which you can connect your cameras and view the video stream in real time. Read more at the end of the article.
The main disadvantage of remote video surveillance in general is the fact that not everywhere it is possible to connect to cable Internet, and through wireless networks the quality of the connection, as a rule, leaves much to be desired. In this case, it will be very problematic to remotely monitor a large video surveillance system consisting of a large number of cameras.
So, let's look at 4 main options for implementing online video surveillance via the Internet, ranging from simple to full-fledged system.
Organizing online video surveillance - basic methods
To install equipment and configure remote access to cameras, we first need to connect all parts of the system into one whole and install cameras in their permanent locations.We install the cameras in such a way that in the future it will be possible to easily identify the faces of all people who come under their review. To do this, you need to determine the optimal installation height, as well as the required focal length and viewing angle in advance. To ensure the best quality, today it is better to buy IP cameras with high image resolution.
After installing the cameras, we need to connect them to the DVR via UTP cable. We also connect a hard drive to the recorder (preferably with external power), and power our entire system from the network. In order not to bother with unnecessary wires, you need to immediately buy cameras with network power supply (PoE), as well as a video recorder with PoE ports, or in the future use PoE adapters and a power supply for IP cameras (PoE injector).
Next, we connect our entire system to the router, and make all the necessary settings: port forwarding, setting camera parameters, etc. Later we will look at setting up a remote video surveillance system with a DVR and a router in more detail, but first we’ll talk about organizing remote access to one camera.

Video surveillance using one IP camera
The simplest, and therefore popular, way to organize remote monitoring is directly via the provider’s network cable. To implement this method, we will need the same dedicated IP address, which will need to be assigned to the camera itself.
- First, you need to connect the camera to your computer and enter its IP address in the browser line. You can find out the IP cameras in the user manual, on the manufacturer's label affixed to the body, or using the manufacturer's software on the disk included in .
- After entering the IP, we will be taken to its web interface, where we will need to go to the network settings subsection, and in the “IP address” line, indicate “Receive automatically,” or manually enter the IP address allocated to you by your provider for greater reliability.
- Now you need to find out the port used by the camera for the incoming connection - most often port 80 is open.
- Next, we set the login and password with which you will log into the camera’s network interface, disconnect the device from the computer, and connect the provider’s network cable to the IP camera.
If configured correctly, the image from the camera will be available from any device at: http://(your permanent IP address):(camera open port)– without parentheses.
It happens that the provider blocks port 80 - in this case, in the camera settings, change it to another one. As you can see, everything is simple, and all this can be easily done without the help of specialists.

Remote video surveillance using a router
To connect two or more cameras to the Internet, we will need to enter a router into our system. It creates its own subnet, which includes all cameras, and will also need a dedicated IP address.
To configure the router, we need to get into its web interface. This is done by analogy with one - in the address bar of the browser we enter its standard IP address, set by default by the manufacturer, and get into the login and password entry form. The IP address can be found on the device label, or in the user manual, where we also take the login and password (usually the login is admin, and the password is a combination of several zeros).
After logging into the network interface, you need to assign each camera its own port - as a rule, this can be done in the “Routing” section (Port Forwarding, “Virtual Server”, etc., depending on the router) in which rules are created for forwarding external requests from the Internet to one or another IP address of the internal network. For example, we will set the external port number 8086 to redirect to the internal port 80 of the IP address of the first camera (for example, 192.168.1.11). For external port 8087, we will set redirection to port 80 of the internal IP address of another camera, etc. Depending on the router model, the settings may vary, for example, it is possible that in your case you will simply need to register the ports of each camera with IP addresses and other information:
- Service name - for example, “IP camera 1”;
- Port range - the port of the first camera 8086, manually assigned during further configuration;
- Local IP address - 192.168.1.11 (camera IP address);
- Local port - 8186, or 80 if the camera did not have the ability to configure the port;
- Protocol: TCP;
- Protocol number: 1 (or any other number).
After setting up the router, we move on to the cameras. In turn, we connect to each of them directly from the computer, and manually assign them the IP addresses that were specified in the router settings - for convenience, use the list of IP addresses written down earlier on a piece of paper. The port remains the default - 80, or is specified manually.
All that remains is to set up a connection with the provider and connect all the cameras to the router. To connect to video surveillance cameras via the Internet, you need to enter the following request in the address bar of your browser: http://(your permanent IP address): (specified in the forwarding settings external port)– remove the parentheses. When you click on the link, a window should open with a form for entering your login and password - enter the data specified when setting up the camera. Again, it is better to write down the data for each camera in a separate list so as not to get confused in the future.
By analogy, we carry out the connection.
Read also:
Video surveillance via cloud services is becoming more popular and accessible every day. Due to this increased demand, supply is also growing - more and more manufacturers of video surveillance equipment are beginning to offer their consumers to use their own cloud services. The number of new companies specializing specifically in organizing a specialized cloud for viewing video surveillance cameras online is also growing. Read our article about the most popular and technologically advanced cameras that can connect to a remote cloud.
Adding a DVR

Remote video surveillance system with DVR connection
Thanks to the system, its functionality is significantly expanded. Now it becomes possible not only to view images from cameras online, but also to maintain an archive, which will also be available through remote access. In addition, you can connect various security sensors to the DVR, with which the system can notify you about the occurrence of an alarming event.
The principle of setting up IP video surveillance via the Internet with the addition of a DVR to the system is practically no different from the previous method.
- We obtain a dedicated IP address from the provider, then set up redirection from it to the IP address of the local network in which the DVR will be located.
- Typically, all the necessary network settings are located in the “Network” tab. In this section you need to enter the local IP address of your DVR (for example, 192.168.1.1), the gateway (the IP address of the router on the local network), and the subnet mask (usually it looks like 255.255.255.0).
Important! One rule must be followed, which states that the router and the DVR must be on the same subnet, otherwise they simply will not be able to see each other.
Now it’s time to configure the router parameters:
- We go to its web interface, select the “Remote Management” item, and allow remote control of the device by highlighting the corresponding port.
- Now in the “Virtual Servers” section we configure redirection by analogy with setting up a system with only a router: for example, external port 8086, DVR port (80), and its IP address to which requests from the outside will be redirected (as an example, we indicated 192.168.1.1) .
- It is also worth assigning a permanent IP address of your DVR to its MAC address, otherwise the router may assign it an arbitrary IP after a reboot. Typically these settings are located in the “Address Reservation” section.
If the settings are correct, the DVR will be available upon request: http://(your permanent static IP address from your provider):(8086)– must be specified without parentheses.
Important! Let us clarify one important point that many users stumble over, having successfully configured the equipment, but still not being able to connect via remote access. It is impossible to access the DVR settings remotely from the same static IP address that you assigned to it (and that your Internet has), since the request, from a technical point of view, is generated from the same address. Therefore, to check its functionality, you need to access the recorder from a device that has a different IP address - a mobile phone or computer with a different external IP.
Video surveillance via cloud services

Cloud video surveillance
The main advantage of organizing video surveillance via the Internet is that there is no need for a dedicated external IP address. The main requirement in this case will be support by your DVR (must be specified upon purchase).
The principle of remote access to a video surveillance system in this case is to constantly connect the DVR or camera to a cloud service and transfer data to it, while at any time you can connect to the system and view what is happening online, or work with the archive. To do this, you simply need to go to the service website from any device (or use a special application from the equipment manufacturer) and enter the registrar identification number and password in the service authorization form. When registering separately in the cloud service, enter the data specified during registration. This method greatly simplifies the task for people who do not understand or do not want to spend their time setting up a router, obtaining an external permanent IP address, etc.
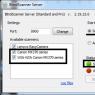
To configure the DVR, in most cases, you just need to go to its interface, and check the box next to the “P2P” or “Cloud” line, and that’s it - the equipment is automatically connected to its native cloud service. And to start viewing what is happening from cameras remotely, we log in from any device and simply enter our data into the service authorization form.
The main disadvantage of video surveillance via the cloud is the limitation of connection speed, therefore there will be restrictions on the bitrate of the video stream, which will not have a positive effect on the image quality. Users of 3G modems will not even notice this, since the connection speed is already quite low and is strictly limited by the parameters of the 3G standard.
We also invite you to familiarize yourself with our rating of cloud video surveillance services:
Briefly about the equipment that supports the technology P2 P:
- RVI DVRs, for example, IP camera brand RVi-IPC43DNS and DVR RVi-R04LA;
- Dahua DVRs, with the designations V2 and S2 at the end;
- Equipment from NoviCam. Any recorders from the F series. The manufacturer’s cloud service is called NOVIcloud;
 Conditionally free service IVideon (connection of 15 cameras for free). You can connect any video camera to this service via a computer with server software. The service also has its own online store, where you can currently buy Axis, Hikvision, adapted to the Internet cloud. You can connect these IP cameras to IVideon without using a DVR or computer. It is possible to maintain a video archive on the website.
Conditionally free service IVideon (connection of 15 cameras for free). You can connect any video camera to this service via a computer with server software. The service also has its own online store, where you can currently buy Axis, Hikvision, adapted to the Internet cloud. You can connect these IP cameras to IVideon without using a DVR or computer. It is possible to maintain a video archive on the website.
So, here we have looked at the 4 main ways to connect CCTV cameras to the Internet. Experts predict that the future lies in cloud-based video surveillance services, and even now they advise checking when purchasing equipment whether it supports P2P technology. We hope our article will be useful to you and will clarify the issue of implementing online video surveillance! All the best to you, and we wish you to create your own remote system without any problems!
26 comments
Hello. You will need a radio relay complex transceiver + amplifier + highly directional parabolic antenna with a gain of more than 30 dB. The estimated cost of one set (two required) is 80-100 thousand rubles. But their maximum range is just 200 kilometers. This is the maximum range in IDEAL conditions, i.e. naturally direct visibility and without interference from villages, cities, etc., through a field or forest (above the forest).
Good afternoon
a couple of hundred km along the RRL are usually flights of 60-70 km (provided that there are very high supports for placing antennas). An exception is if the extreme points are on a mountain and there are no obstacles between them, and then antennas with a diameter of approximately 3.7 m will be needed. So for 200 km you will need 2-3 re-receiving points with supports of 40-60m. It’s better to rent a channel if possible (here you have to assume that it will be cheaper). Ideally via satellite, but it's not exactly cheap.Gentlemen, I think you have gone astray. The author of the question clarified that there is high-speed Internet in the places where both the cameras and the recorder are installed. Why fence a radio relay line?
It is much easier and cheaper to organize a communication channel through existing access points.Forward the ports on the router on the camera installation network. On the recorder, write the static address and ports of the cameras.
You connect the cameras to the router so that they can be seen via the Internet.
And at a distance of 200 km, install a computer with the CMS program from these cameras. You set up access to each camera via the cloud, and with a stable Internet connection, the computer will write streams from the cameras to its disk.
But unfortunately, I have not seen such functionality on the recorder.Good afternoon.
Please advise which outdoor camera with a built-in port for a SIM card to choose for organizing surveillance at a site under construction with sending photos according to a schedule to a registered E-mail via a 3G/4G GSM channel.
Currently two SimPal G-312 cameras are used. The cameras suit everyone, except that every month, with an interval of two days, first one and then the other fail. The first time the service center repaired it under warranty (they said they replaced the board) and removed the warranty. Now the repair costs as much as the camera itself...Cameras with built-in 4G are always unstable due to interference from the 4G amplifier to the camera circuit.
It is better to install separately: a camera with SD and a Wi-Fi router.We are not familiar with such a DVR. Modern DVRs are indifferent to router types because they use cloud access. By the way, they are already quite inexpensive. For example, you can buy 8 channels from us for 7,000 rubles, and with analytics (face recognition, loss of objects, etc.) 12 channel for 10,000 rubles. They work stably, the guarantee is Russian. So there is no point in saving money by buying Chinese recorders now.
I can buy an IP address for my Wi-Fi camera, which is located in the country, add a router to the camera (17 km from the house with the apartment) via Android from time to time and see what is happening there. And the camera has the ability to record motion on an internal SD 32Gb. Cellular communication at the dacha is stable, 220V network all year round. Is there such a simple solution for one camera?
It will be unstable to work through a mobile operator. Of course, you can use industrial 4G routers, but still the stability will not be very good.
Hello. What if you need to record on a remote DVR? That is, there are three IP cameras and high-speed Internet via a wire with a dedicated static address at one end (facility) and a recorder with high-speed Internet and a static address at the other end (office) a COUPLE HUNDRED KILOMETERS FROM EACH OTHER. It is required to record 24/7 cameras on a DVR.
Hello. You will have to connect the DVR to the router, you can use a wireless bridge.
Very intelligible even for those from the last carriage of the armored train. Thanks a lot!
I usually live in another country. There are practically no criminal police there, and the rented apartment was “surrounded” a couple of times with the purpose of “just to cause mischief.” I believe that the visitors are acquaintances, but I really want to get to know each other better.
Is it really that easy to hack the camera on your laptop? The author of Medialeaks, having read the latest news about the hacking of millions of video cameras, hacking applications and sites on which streaming from hacked cameras from around the world has become an analogue of a reality show, decided to study programs for hacking webcams, and also tried to find ways in which you can protect yourself from anonymous spies and other online voyeurs.
Troll. James Troll. Who spies on webcam owners
Talk about hacking video cameras is no longer surprising these days. This has become such a widespread phenomenon that some hackers (crackers) maintain a website that shows broadcasts from non-password-protected surveillance cameras and webcams from around the world, and others a program that allows you to gain remote access to various video cameras connected to the Internet.
In most cases, devices are hacked due to the fact that their owners do not change the factory password of the cameras by connecting them to a public network, but ordinary webcams on laptops do not fall into this category. To gain access to them, hackers need something more serious than the “admin admin” password, and there is nowhere to enter it.
Contrary to the popular belief that webcams are hacked by intelligence agencies, much more often you can come across stories about hacks committed not by people in uniform, but by mere mortals. Moreover, in the comments on thematic sites it is often not even overly curious individuals who are trying to spy on their loved ones, but hacker trolls. For them, it doesn’t make much difference who they watch, but they can do much more harm to their victims, because they may not limit themselves to observation. Sometimes they take control of someone else's computer, destroying or changing user data as a joke.
Even a pre-pubescent schoolboy can hack a laptop camera: there are a lot of videos on YouTube about hacking, the authors of which troll unsuspecting users by connecting to their webcams. There are many authors of such videos, but the essence of the videos is the same: gain access to a webcam, and then stream the victim’s facial expression while she tries to figure out why the wallpaper on the desktop suddenly changed or porn with sound turned on. Most often, such videos are made by teenagers, and the title contains the words “funny”, “trolling”, “getting excited”, etc.
Schoolchildren have become so familiar with hacking programs that they give full lessons on how to set up hacking programs on their channels, where, between videos about hacking other people’s computers, they talk about their childhood hobbies a la “growing a cactus” and “here’s my favorite doll.”
The webcam hacking trend has gained great popularity. Hackers (crackers) have created several specialized sites on which they talk about various methods of hacking computers, share their discoveries and successes in the trolling field in the corresponding threads on forums and create their own assemblies of crackers that will allow those who want to start mocking unknown people on the network without unnecessary problems with installation of programs.
Eyes everywhere. Business for voyeurs
In addition to trolls, those who are trying to make real money by spying on strangers also connect to the cameras. There are communities on VKontakte that sell access to various cameras. Most often these are surveillance cameras installed in rented apartments and public places. It’s easy to connect to them: owners often do not change the factory passwords when connecting the camera to the network, and the only problem for the cracker is finding the device in the desired location - and if he works as an installer or configurer of such cameras, the task becomes even easier.
For example, the administration of the community “IVMS distribute, sell, exchange / IP Camera” sells broadcasts from cameras from apartments in the group’s built-in store on VKontakte, ranking them by cost. The prettier the broadcast victim (in the vast majority of cases these are women), the more expensive it is to spy on her. The price ceiling does not exceed 400 rubles - for this money the admin offers anyone who wants to connect to the camera in the young girl’s room.

To get started, the admins offer subscribers a free way to observe life in some houses, where surveillance systems are installed in almost every room. Broadcasts are conducted around the clock; in some cases, admins sign them with comments in the style of “something good here.” The groups also offer installation of pre-configured surveillance cameras and even service, replacement and product warranty.

Almost legal. How webcams are hacked
Most often, computers are hacked using completely legal utilities, which are usually used as a means of optimizing the work of system administrators and other IT department employees in various large organizations - TeamViewer, RMS, LuminosityLink, Radmin and the like. The principle of their operation assumes that one of the computers on the network can be controlled by another remotely, and within corporate networks this can hardly become a problem: each computer on the network is connected to the “master” with general settings, their connection is often password-protected.
Such programs can also be used by ordinary network users. You just need to install equipment on two or more computers, interconnected by the same pre-designated settings - “client” utilities on the computers under management, and a server utility on the device that will be the master.

It is unlikely that many victims of hacking deliberately install clients with programs that will allow them to be monitored. In most cases, the client is installed on the computer as a companion utility during the installation of some pre-modified program (most often it is something free and downloaded from an unknown resource). With the help of such a Trojan installed in the MediaGet torrent search engine, in April 2016, one of the Dvach users for several days in a row.
In addition to official programs designed to make life easier for system administrators, there are also utilities designed specifically for secretly monitoring computers. These include, for example, RemCam and DarkComet. The latter suddenly turned out to be connected to the Syrian conflict: according to Wired, the government used DarkComet to spy on opposition activists, sending them a hidden link to its installation, disguised as a pop-up window with a message. After information about the actions of the Syrian government appeared in the media, the developer of the application officially stopped supporting it, saying that he never wanted the authorities to use it.
It is ironic that the creators of hacking applications, who talk on their website about how to hack other people’s computers, are at the same time associated with communities on VKontakte, in which they report on information security and protecting a computer from various hacking methods.

Android applications work on the same principle, but mobile phone users are protected to some extent by the license. For example, the GPP Remote Viewer application allows you to receive data from your computer in the same way as TeamViewer, but as long as you download it from the Play Market, you can be a little more confident that Trojans will not be installed with it.
With Apple products, the situation is easier to manage and more difficult to hack: modern remote access utilities on iOS often require synchronization via Apple ID, and this leaves even less opportunity for quickly hacking computers or installing a harmful utility on them that will transfer control to a third party .
Medialeaks is watching you. Let's try to hack each other's webcams
The editors of Medialeaks tested two common programs for monitoring via webcam and remote data management - the legal RMS and the “gray” RemCam2. The table tried to hack Tatyana’s computer, bombarding her personal account with all sorts of incomprehensible files, which were supposed to install the corresponding software on her computer. Everything is on Windows; software was used for monitoring without user modifications.
RMS asked for a lot of different permissions at startup, which should be ignored if you are running a pre-configured version by someone else (or by you, if you are a Hackerman). In addition, in order to connect to the victim’s computer, the program asked for a password, which Tanya entered during installation. The silent hack was unsuccessful, and when we connected remote control of the camera, a corresponding notification appeared on the victim’s screen. Mom's voyeur was defeated, but only because he used a legally downloaded and unmodified utility.
RemCam2 turned out to be much more useful in this regard - it is a full-fledged Trojan, the installation of which even the user himself will not guess: no screens, the application was installed unnoticed when Tanya clicked on the file icon with a stupid name in the chat. Having learned her IP, the insidious Stolik began to observe the editor who was working at that time, instead of working himself.
It was possible to completely remove programs only after cleaning the registry. Don't try this at home.
Thin and sticky protection. How they try to protect themselves from voyeurs
Unfortunately, if you actively use the Internet, then it is simply impossible today to completely protect yourself from spying on a webcam and remote access to data. This doesn't mean you have malware installed on your computer right now, but the more you download strange applications from various dubious sources (or click on links in emails from strangers), the more likely you are to stumble upon one of these Trojans.
But even if the camera is disabled, some Trojans may try to turn it back on, so those who are worried about possible spies should check their computer with the banal Program Manager utility - it shows which processes are currently running, and this will allow you to notice whether someone's video camera. It’s not even worth writing about antiviruses.
It is precisely because of the inability to achieve one hundred percent security that among many PC users there is a widespread tradition of sealing webcams - oddly enough, at the moment this is the most effective way to combat voyeurism. Facebook founder Mark Zuckerberg and former FBI Director James Comey have spoken out about the benefits of taping video cameras, and according to antivirus manufacturers ESET, about 17% of PC users tap video cameras.
The use of duct tape as a means of protection against voyeurs has reached a new level in recent years: enthusiasts are replacing it with special camera shutters, and some laptop manufacturers are adding camera shutters at the production stage. However, even in this case, burglars can spy on victims - if not by spying, then at least by eavesdropping using the built-in microphone. So when taping your camera, think about this too.
In fact, an uncovered video camera also has its advantages: it can help a potential victim detect a hack, since its operation indicator on the laptop case will indicate that an outsider has connected to the computer. In this case, the only correct solution is to turn off the Internet as soon as you see the light of a video camera flashing for an unknown reason, even for a second: this almost never happens by accident.
Today, technological progress has reached such a level that sometimes you just want to play God. Of course, we are not yet able to create people, but it is quite possible to interact with pieces of equipment. This article will discuss the theoretical possibilities of connecting to various webcams. Please note that the content of this article is for informational purposes only, so remember that invading the personal space of another person, especially in this way, is punishable by law.
general information
Many people are afraid that the camera built into their laptops or connected to the computer can spy on and eavesdrop. It should be noted that for good reason. Moreover, not only they can do this, but also mobile devices, televisions and even household appliances like irons (there was a scandal with them in the Russian Federation several years ago). And now we will look at how to connect to someone else's webcam.
Choosing a tool
The necessary tools can be provided by the fourth version of the .NET Framework and VS2010. DirectDraw and MSDN technologies are also suitable for connection. But to solve the problem, the article will focus on Video For Windows (VFW) technology. In this case, WinAPI functions are widely used. Of course, these are not all the available technologies with which you can access the camera. But they are the most developed and perfect of those widely known and accessible to people.
Begin
So how to connect to someone else's webcam? Initially, it should be taken into account that the device may have several devices for recording images and sound. Therefore, you should take care of the possibility of choosing the tool with which you will work. To solve this problem, we use the capGetDriverDescription() function.

It can accept five parameters:
- wDriverIndex is the index of the video capture driver. It can take values from zero to nine.
- lpszName - the parameter points to the buffer that contains the corresponding driver name.
- cbName is used to specify the size in bytes of the lpszName buffer.
- lpszVer contains a pointer to a buffer where a description of a particular driver can be found.
- cbVer is the size in bytes of the buffer where the driver description is stored.
How to connect to someone else's webcam? Ipb image can show camera activation. Therefore, we need to work on this too. You can, of course, write a small code here that allows you to connect and control the operation of the device, but since this is an invasion of privacy, only a description will be provided. You can use C# to create the required program.

When working, you must indicate the name of the function that is connected, and also write the name of the DLL where it is defined. A class should be used to assemble all the individual work.
What should you do next?
We continue to figure out how to connect to the webcam of someone else's computer. To a specialist, the code may seem very simple to implement. What should be done? Above we wrote about the first parameter of the capGetDriverDescription() function, which can take a value from zero to nine. Therefore, you should run a loop that will purposefully work in this range to search for the required values. So, we have a list of devices. Now you need to take care of transmitting the video stream. The capCreateCaptureWindow() function will help with this, the main purpose of which is to create a capture window. What should be done in this case? It all sounds trivial - you only need to send messages to the capture window. The well-known SendMessage() function will help with this. But let's return to capCreateCaptureWindow().
Capturing the image
The capCreateCaptureWindow() function has the following arguments that are of interest to us:
- lpszWindowName is a null-terminal string that contains the name of the capture window;
- x - location of the X coordinate;
- y is the location of the Y coordinate;
- nWidth - window width;
- nHeight - window height;
- dwStyle - window style;
- hWnd - access to the parent window;
- nID - window identifier.

As a result of the function execution, NULL will be received (in case of an error) or the connection will be successfully created. But keep in mind that since it belongs to WinAPI, you need to import it. With all this data, you can already start the camera initialization process. Immediately after creating the window, you can already try to send a message. If the result is distinguishable from zero, this means that the attempt was successful. Messages on which a number of operations depend must then be defined and sent. So, in order of priority:
- connect to the device driver, which provides video capture;
- make a break;
- copy frame to clipboard;
- if necessary, enable preview mode;
- if necessary, activate the overlap;
- if necessary, adjust the preview speed;
- enable scaling if necessary;
- if necessary, set the call function for preview;
- receive a single frame from the video capture driver;
- save the frame received from the camera to a file.
Well, that's basically it.
What about other devices?
There are not only computers in the world. If you are interested in how to connect to the webcam of someone else’s laptop, then the described method is perfect for this purpose. Of course, if the Windows operating system is installed there. This is not suitable for Penguin fans. After all, there, as a rule, the user’s permission is required for any action. And if you want to connect to Linux, you will have to ask the person to allow him to monitor him.

Of course, purely theoretically, he can resolve it out of stupidity or accident. But in reality there is no need to rely on this. If the question is how to connect to someone else’s iPhone or Android webcam, then a lot depends on the operating system used. And it is very difficult to speak even in general terms because of their great diversity.
Conclusion
But nothing is impossible if you set a goal and work hard to achieve it. Let's take the iPhone for example. Phones in this series are considered well protected. And it is impossible (at least officially) to hack them programmatically. But in practice it is possible to find a gap. The main thing is to look well. Let's say we make an application that transmits video to us. And under the guise of something, we will force the user to download and install it. At the same time, we will register the creation of a secret copy, which will not be displayed in the registers. That's all. Even if the user deletes the application, we will still monitor him.
Tip 1: How to connect to a remote webcam
Sometimes users of a personal computer of various classes may need to remotely connect to web camera . The reason for this may be the desire to observe a certain point where the camera is installed and, accordingly, be aware of what is happening there.
You will need Personal computer, webcam
Instructions
1. First of all, in order to connect to web camera and view videos or photos, you need to create a local network connection. To do this you need to have a switch, i.e. a special network switch that allows you to create several connections at once, and at least two Ethernet cables. After that, connect all devices using Ethernet cables.
2. Now, using the installation program that is usually included in the initial package, determine the IP address for the camera. You will enter it into the address bar of your browser or other program. It is best to create a static IP address, as it is much more convenient for work. Then you need to open an Internet browser and type the IP address in the address bar. If you are using a modern browser, then no software will be downloaded, as it necessarily supports video streams.
3. This is how a webcam is connected to a computer, but if you want to connect to a camera located at a very long distance, then special programs are needed for this, for example, WebCam Monitor 4.20 or Webcam Surveyor 1.7.0, in which you also need to specify the IP address and some other data. The process of setting up programs of this kind is extremely simple, since you only have to answer questions. But, despite their simplicity, they offer many important advantages, since you will be able to detect illegal entry into your home or other troubles in time. As you can see, connect remotely to web camera not so difficult, and thanks to this you can always be aware of what is happening in the observed area.
Tip 2: How to turn on the camera remotely
To observe events taking place in a certain place, you need to have a camera installed there, connected to the Internet and a personal computer from which you can control it. By connecting to it, you will see everything that happens in real time.
You will need- network switch.
Instructions
1. Create a local network connection to connect to the remote camera. To do this, you will need a special network switch. It is needed in order to create several connections at once. Take two Ethernet cables and connect all your devices.
2. Use the installation program. As a rule, it is included in the basic package. If not, then download it from the Internet and install it on your personal computer. Using this program, determine the IP address of the remote camera. Subsequently, you will enter it into the address bar of your browser or any other program convenient for you.
3. Create a static IP address so that you can turn it on remotely without any problems. camera. Open your browser. Enter the IP address of the camera in the address bar. Use modern browsers that support video streaming to avoid the need for additional software.
4. Use special programs if you want to connect to a camera located at a fairly large distance from you. To use remote camera install WebCam Monitor 4.20 or WebCam Survevor 1.7.0 on your personal computer. Using this program, specify the IP address of the camera you are interested in. What follows is a fairly simple setup procedure. You will only need to answer the questions that the program will ask.
5. If the installed program is not Russified, download the Russifier, or use a translator to correctly configure the software. After this, you will be able to use the remote webcam, if this use is legal and the administrator of the computer to which this camera is connected will grant you the appropriate rights.
If, by coincidence, you are tormented by suspicions about what is happening in your absence (for example, a child or pet is alone at home, an apartment is unattended), there is an option to control the situation from a distance using a camera.
The Internet portal ru.ivideon.com optimally implements the ability to remotely connect from any device to web cameras, IP cameras and analog cameras. On the “Tariffs” tab, you can familiarize yourself with the characteristics of possible service connection options and select the appropriate one. Click on the “Add camera or DVR” button, select the appropriate type of camera to connect, read the instructions in the next step and click “Continue”. Now you need to download and install the program on the computer to which the camera is connected; to do this, select your operating system. The standard installation will begin, simply select your language and follow the instructions in the installation wizard. The setup wizard will start automatically. Click “Next”, then enter your e-mail that you specified during registration, and select the camera location from the list. This formality is created for your convenience (if the list of cameras is large, these groups will be easier to navigate). Make sure your camera is connected and working properly, click “Next”. If active cameras are detected, you will see a list of them, otherwise try to “reconnect” the working camera again and click “Repeat search”, if everything went well - “Next”. If you want the video to be saved in the archive, check the “Include in archive recording” checkbox; if you are only interested in online broadcasting of images from cameras, uncheck it. To prevent the program from starting automatically when you turn on the computer, uncheck the “Start Ivideon Server when the OS starts” checkbox, and then click “Finish”. If the “Log in to your Personal Account” checkbox remains active (by default), your page on the website ru.ivideon.com will automatically open in the browser. In the list on the right, select the active camera, marked in green, and you will immediately see the live broadcast. To make it more convenient for you to watch videos from your tablet, phone, laptop or other computer, you can download the application. To do this, either add to your wishlist and install the Ivideon application, as shown in the screenshot, or exit the gadget to “google play” and find it through the search bar. The second way to monitor the situation is using Skype. Create in the program, add this one on Skype. On the computer to which the camera is connected, log into Skype under this account, in the video settings, in the “Automatically receive video and share the screen for” field, select “only people from my contact list.” Now in the menu on the left, activate the “Calls” item, click on the “Open additional settings” button located in the window on the right. Select “Only from my contacts” in the “Receive calls” field and check the remaining boxes so that the video broadcast will automatically start as soon as you call your additional account. Advanced users also offer the following option: install a terminal server on the computer with the camera (to spy on it unnoticed, i.e. if someone is working on the computer, so that they don’t get kicked out), connect the Remote Desktop Protocol (RDP) and use any program that works with the camera. An indicative list of programs is available on web-kamera.ru. However, no one bears responsibility for the possible maliciousness of the programs. Therefore, be vigilant, check sites on the online service trustvset.rf and do not neglect antiviruses.The described methods of connecting to remote video cameras are legal, but keep in mind that interfering in someone else's personal life may not bring the expected result. Act solely for your own peace of mind and for the benefit of others.