What services connect to udp ports. What are computer network ports? Usage in URLs
To communicate with applications running on other network hosts (as well as with other applications on the same host).
The basic rule necessary to understand the operation of the port: 1) The port can be occupied by only one program and at this moment cannot be used by another. 2) All programs use ports to communicate with each other via the network.
For each of the TCP and UDP protocols, the standard specifies the ability to simultaneously allocate up to 65536 unique ports on a host, identified by numbers from 0 to 65535. When transmitted over a network, the port number in the packet header is used (together with the host IP address) to address a specific application (and specific network connection belonging to him).
Port numbers
TCP ports do not overlap with UDP ports. That is, TCP port 1234 will not interfere with UDP traffic over port 1234.
A number of port numbers are standardized (see List of TCP and UDP ports). The list is maintained by the non-profit organization IANA.
On most UNIX-like operating systems, listening on ports numbered 0-1023 (almost all of which are registered) requires special privileges. Each of the remaining ports can be seized by the first process that requested it. However, there are many more numbers registered than 1024.
Brief list of port numbers
TCP is assumed to be used unless otherwise noted.
- DISCARD: 9, Discard port (RFC 863)
- FTP: 21 for commands, 20 for data
- SSH: 22 (remote access)
- telnet: 23 (remote access)
- SMTP: 25, 465, 587
- isserver: 3055
- XMPP (Jabber): 5222/5223 - client-server, 5269 - server-server
- traceroute : above 33434 (UDP) (some sources indicate that it is enough to specify a port range from 33434 to 33534)
Sender and Receiver Ports
TCP or UDP packets always contain two port number fields: source and destination. The type of service program is determined by the recipient port of incoming requests, and the same number is the sender port of responses. The “reverse” port (the port of the sender of requests, also known as the port of the recipient of responses) when connecting via TCP is determined arbitrarily by the client (although numbers less than 1024 and already occupied ports are not assigned), and is of no interest to the user. The use of reverse port numbers in UDP is implementation dependent.
Links
Notes
Wikimedia Foundation. 2010.
See what "Port (TCP/IP)" is in other dictionaries:
Name: Transport Control Protocol Layer (OSI model): Transport Family: TCP/IP Port/ID: 6/IP Specification: RFC 793 / STD 7 Main implementations ... Wikipedia
Port: Wiktionary has an entry for “port” Port (Latin portus “harbour”, “pier”) ... Wikipedia
Name: Transmission Control Protocol Layer (OSI model): Transport Family: TCP/IP Port/ID: 6/IP Specification: RFC 793 / STD 7 Main implementations: Linux, Windows Extensibility ... Wikipedia
The TCP/IP protocol stack (Transmission Control Protocol/Internet Protocol) is a set of network protocols at different levels of the DOD network interaction model used in networks. Protocols work with each other in a stack (English stack, stack) ... ... Wikipedia
A TCP port number that identifies a process or application within a computer. For client applications, the port number is dynamically assigned by the operating system. For software servers, port numbers do not change and are prescribed by the Internet... ... Financial Dictionary
Network port is a parameter of the UDP protocols that determines the purpose of data packets in the format This is a conditional number from 0 to 65535, allowing different programs running on the same host to receive data independently of each other (provided like this ... ... Wikipedia
Network port is a parameter of the UDP protocols that determines the purpose of data packets in the format This is a conditional number from 0 to 65535, allowing different programs running on the same host to receive data independently of each other (provided like this ... ... Wikipedia
Network port is a parameter of the UDP protocols that determines the purpose of data packets in the format This is a conditional number from 0 to 65535, allowing different programs running on the same host to receive data independently of each other (provided like this ... ... Wikipedia
Network port is a parameter of the UDP protocols that determines the purpose of data packets in the format This is a conditional number from 0 to 65535, allowing different programs running on the same host to receive data independently of each other (provided like this ... ... Wikipedia
In computer networks, a port is the end point of communication in the operating system. The term is also used for hardware devices, but in software it is a logical construct that identifies a specific process or type of service.
A port is always associated with a host IP address and type and thus completes the session address assignment. It is identified for each address and protocol using a 16-bit number, commonly known as the port number. Specific port numbers are often used to identify specific services. Of the thousands listed, 1024 well-known port numbers are protected by convention to identify specific types of services on the host. Protocols that primarily use ports are used to control processes (such as Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) from the Internet protocol suite).
Meaning
TCP ports are not needed over direct point-to-point links where the computers at each end can only run one program at a time. They became necessary as machines became capable of running more than one program at a time and were connected to modern packet-switched networks. In the client-server model, ports and network clients connect to initiate service, provide multiplexing services after the initial communication is associated with a known port number, and it is released by switching each request service instance to a dedicated line. A connection is made to a specific number, and thanks to this, additional clients can be served without waiting.

Details
Data transfer protocols - Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) - are used to indicate the destination port number and source in their segment headers. The port number is a 16-bit unsigned integer. So it can be in the range from 0 to 65535.
However, TCP ports cannot use number 0. The source port for UDP is optional, and a value of zero means it is not present.
A process communicates its input or output channels through an Internet socket (a type of file descriptor) using a transport protocol, port number, and IP address. This process is known as binding, and it enables data to be sent and received across a network.

The operating system is responsible for transmitting outgoing data from all application ports to the network, as well as forwarding incoming network packets (by mapping the IP address and number). Only one process can be bound to a specific IP address and port combination using the same transport protocol. Common application crashes, sometimes called port conflicts, occur when multiple programs try to communicate with the same port numbers on the same IP address using the same protocol.
How are they used?
Applications implementing shared services often use a specially reserved and well-known list of TCP and UDP ports to accept service requests from clients. This process is known as listening, and it involves receiving a request from a well-known port and establishing a one-to-one conversation between the server and client using the same local port number. Other clients can continue to connect - this is possible because the TCP connection is identified as a chain consisting of local and remote addresses and ports. Standard TCP and UDP ports are determined by agreement under the control of the Internet Assigned Numbers Authority (IANA).

The core network services (most notably WorldWideWeb) tend to use small port numbers - less than 1024. Many operating systems require special privileges for applications to bind to them because they are often considered critical to the functioning of IP networks. On the other hand, the end client of the connection usually uses a large number of them, allocated for short-term use, which is why there are so-called ephemeral ports.
Structure
TCP ports are encoded in the transport protocol packet header, and they can be easily interpreted not only by the sending and receiving computers, but also by other components of the network infrastructure. In particular, firewalls are typically configured to distinguish packets based on their source or destination port numbers. Redirection is a classic example of this.
The practice of trying to connect to a range of ports sequentially on a single computer is known as port scanning. This is usually due to either malicious disruption attempts or network administrators looking for possible vulnerabilities to help prevent such attacks.
Activities that focus on how often computers are monitored and recorded. This technique uses a number of spare connections to ensure an uninterrupted connection to the server.

Examples of using
The most important example where TCP/UDP ports are actively used is the Internet mail system. The server is used to work with email (sending and receiving), and in general requires two services. The first service is used for transport via email and other servers. This is achieved by using Typically, the SMTP service application listens on TCP port number 25 for the purpose of processing incoming requests. Another service is POP (Post Office Protocol) or IMAP (or Internet Message Access Protocol) which is required for email client applications on users' machines to receive email messages from the server. POP services listen for numbers on TCP port 110. The above services can both run on the same host computer. When this happens, the port number distinguishes the service requested by the remote device - the user's PC or some other mail server.
While the server's listening port number is well defined (IANA calls them well-known ports), this client parameter is often selected from a dynamic range. In some cases, clients and server separately use specific TCP ports assigned in IANA. A good example is DHCP, where the client uses UDP 68 in all cases, and the server uses UDP 67.

Usage in URLs
Port numbers are sometimes clearly visible on the Internet or other Uniform Resource Locators (URLs). By default, HTTP uses and HTTPS uses 443. However, there are other variations. For example, the URL http://www.example.com:8080/path/ indicates that the web browser is connecting to 8080 instead of the HTTP server.
List of TCP and UDP ports
As noted, the Internet Assigned Numbers Authority (IANA) is responsible for the global coordination of DNS-Root, IP addressing, and other Internet Protocol resources. This includes logging frequently used port numbers for well-known Internet services.
Port numbers are divided into three ranges: well-known, registered, and dynamic or private. Well-known (also known as system) are those numbered from 0 to 1023. The requirements for new appointments in this range are more stringent than for other registrations.
Well-Known Examples
Examples found in this list include:
- TCP 443 port: HTTP Secure (HTTPS).
- 22: Secure Shell (SSH).
- 25: Simple Mail Transfer Protocol (SMTP).
- 53: Domain Name System (DNS).
- 80: Hypertext Transfer Protocol (HTTP).
- 119: Network News Transfer Protocol (NNTP).
- 123: Network Time Protocol (NTP)..
- 143: Internet Message Access Protocol (IMAP)
- 161: Simple Network Management Protocol (SNMP)1.
- 94: Internet Relay Chat (IRC).
Registered ports range from 1024 to 49151. IANA maintains an official list of known and registered ranges. Dynamic or Private - 49152 to 65535. One use of this range is for temporary ports.

History of creation
The concept of a port number was created by early ARPANET developers in an informal collaboration between software authors and system administrators.
The term "port number" was not yet used at that time. The number sequence for the remote host was a 40-bit number. The first 32 bits were similar to today's IPv4 address, but the first 8 bits were the most significant. The smallest part of the number (bits 33 to 40) represented another object called AEN. This is the prototype of the modern port number.
On March 26, 1972, the creation of a socket number directory was first proposed in RFC 322, which called for each persistent number to be described in terms of its functions and network services. This directory was subsequently published in RFC 433 in December 1972 and included a list of hosts, their port numbers, and the corresponding function used on each node on the network. In May 1972, official assignments of port numbers, network services, and a special administrative function for maintaining this registry were first documented.
The first TCP port list had 256 AEN values, which were divided into the following ranges:
- 0 to 63: standard functions of the entire network
- 64 to 127: Host-specific functions
- 128 to 239: Reserved for future use
- 240 to 255: Any experimental feature.
The Telnet service received the first official assignment of the value 1. In the early days of the ARPANET, the term AEN also referred to the name of the socket that was used with the original connection protocol (MSP) and the network control program (NCP) component. Moreover, NCP was the predecessor of modern Internet protocols using TCP/IP ports.
About computer network ports.
The article clearly describes what a system port is, why programs need it, how and what devices use ports to communicate on the network, and what ports have to do with the security of your data. Introductory article; We’ll talk another time about how to monitor system ports, configure and scan correctly, avoiding errors and understanding what’s happening.
Computer network ports: what are they?
As soon as computers are about to exchange information over the network, they immediately open information portals for exchange. In network architecture, communication between ANY two systems is based on five immutable principles. So that the data “flys” from the point A exactly B, should be known:
- IP address of the information source
- Recipient IP address
- protocol by which devices will communicate
- source transmit port
- and the destination port used by the RFC793 transport protocol
Port- this is a kind of virtual extension, an addition to the network address (like an addition in numbers to the name of the street or house at the address where you live). The postman will come to your street, but will not deliver the letter - he does not know to whom, because he does not know the apartment number. So the information will reach your computer via IP, but without the proper port number, the information will not get to the computer. The computer simply will not understand how to process it, using what application. Computer network ports- these are paths between services and that are running in the operating system installed on the computer and mother/sister processes on host computers, which are sometimes located thousands of kilometers away from you.
By the way, y. These are physical connectors that, unlike those described, can be touched. But their function is essentially the same: all ports are designed to receive information from other devices.
Transport protocols (the most common and used are TCP and UDP) penetrate the computer, using in the message, among other things, numbers from the total number of ports. When an application wants to talk to another device, it directly asks the local OS to open a channel for transmission. Applications that can communicate using both protocols (UDP and TCP) can use the same port to do so, but this condition is not required.
What are computer ports: how many are there?
The exact number of ports on a computer is 65 535 . And they have their own gradation. So, ports with numbers up to 1023 Linux and Unix-like operating systems are considered “critical” systems for network operations, so access to them and the services associated with them often requires root rights. Windows also considers them system ones and closely monitors them.
Ports from 1024 before 49151 are marked “ready for registration”. This means that these ports are reserved or can be reserved for certain services. Fortunately or unfortunately, they are not assigned to these services by strong rules, but they can provide a key to recognize the running program on the host side. The rest (starting from 49152 ) ports are not registered and are used at the discretion of OS users and are called “dynamic” ports. So remembering which port is dedicated to which service is often simply useless (at least today; however, the situation may change). But there is a list of ports that have been used by specific services “from time immemorial”:
20
: FTP data
21
: FTP control
22
: SSH
23
: Telnet<= незащищённый, так что не рекомендуется к использованию
25
: SMTP
43
: WHOIS
53
: DNS services
67
: DHCP service
68
: DHCP client
80
: HTTP traffic<= обычный веб трафик
110
: POP3 postal
113
: authentication services in IRC networks
143
: IMAP mail
161
: SNMP
194
: IRC
389
:LDAP
443
: HTTPS<= защищённый сетевой трафик
587
: SMTP<= добавление сообщений
631
: CUPS port for virtual printers.
There is something else you need to know when getting to know what computer ports are. These are special terms that characterize the state of ports in the sense of data exchange at the current moment. So:
- Port– network localization in the operating system with the assignment of a specific numerical value for the exchange of information via appropriate protocols
- Internet sockets- or simply sockets– file descriptors specifying the IP address and the associated port number plus a special transmission protocol that will work with data
- Binding– the process of using an Internet socket by a service or service when transmitting and receiving files
- Listening– an attempt to contact a service or a service with a port/protocol/IP address or a combination of these components of the network identification of the system in order to wait for requests from the service client
- – checking the status of ports in order to recognize their readiness for further actions
What are computer ports? Do you want to admire them?
You are familiar with the list of common ports, but some services may well use a port that is not assigned to them by default. Or, which is not uncommon, open ports are used as a backdoor for an attacker. So, if you decide to change the port settings yourself, you need to make sure that the law-abiding client and server will find each other. Otherwise, you should let Windows block the port, configure blocking in the router, or rely on the provider, who often blocks ports at the end of the day, without specifically asking the clientele.
You can see on your computer right now which ports are doing what. Type in the terminal:
less /etc/servicesand scroll with your mouse until the end. Here they are in all their glory.

Kali Linux is useful in every sense nmap can also display a list of them:
Less /usr/share/nmap/nmap-services
If you are reading this article on Windows, to see currently open ports, run the Command Console as an administrator cmd and run the command in it:
Netstat -a

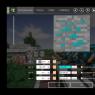
However, more extensive ports working in Windows will be opened to you by a small program called Process and port analyzer, which can be easily downloaded online. It will simply and clearly explain which ports are currently open and what programs these ports are listening to. Here is one of the utility tabs:

Using the program, you can easily check the location of this process in the system and determine how safe it is.
Computer Ports and Network Security
The programs and services that are described here allow you to see the ports that are open specifically in your OS(Windows and Linux) for some programs already running on the computer. However, remember that in the information transfer system between your computer and a distant web server somewhere in Holland, there are still many devices that filter traffic more seriously, including monitoring ports (by the way, including the one located in your room router). Not yours, of course. But it's up to these servers to decide whether any data gets into your Windows. Your provider also has a hand in this, to whom you pay money for access to the network, blocking ports for security purposes or to prevent unnecessary network activity (what if you want to set up your own web server at home? - it won’t work).
Why is this being done? Let me continue the analogy with houses and streets. Imagine that you have decided to buy a garage for your car (computer) at a nearby co-op. The first thing to do is to protect and strengthen the inability to enter the premises: install good doors and install reliable locks (close ports). But what else can you do? Someone sets an alarm (special network scanners to check the status of ports). Save money and install an additional fence with a gate (router withbuilt-in firewall) so that you can park a motorcycle inside (tablet) . And so that the lawns are not spoiled by trucks, for its part the board (provider) installed an automatic barrier (network anti- filters): everything seems to be open, but a stranger will not pass. And so on…
However, if you are still going to find out how your computer is visible from the global network (for example, to attackers trying to test your strength), the methods described here are completely unsuitable. We will develop this topic in future articles.
Read: 2,419
Network ports can provide vital information about the applications that access computers over the network. By knowing the applications that use the network and the corresponding network ports, you can create precise firewall rules and configure host computers to allow only useful traffic. By building a network profile and deploying tools to recognize network traffic, you can more effectively detect intruders - sometimes simply by analyzing the network traffic they generate. We began to consider this topic in the first part of the article published in the previous issue of the magazine. It provided basic information about TCP/IP ports as the foundation of network security. Part 2 will describe some network and host methods that can be used to identify applications listening on a network. Later in the article we will talk about how to evaluate the traffic passing through the network.
Blocking network applications
Network attack surface is a common term to describe network vulnerability. Many network attacks take place through vulnerable applications, and the attack surface can be significantly reduced by reducing the number of active applications on the network. In other words, you should disable unused services, install a firewall on the dedicated system to check the legitimacy of traffic, and create a comprehensive access control list (ACL) for the firewall at the network perimeter.
Each open network port represents an application listening on the network. The attack surface of each server connected to the network can be reduced by disabling all non-essential network services and applications. Windows Server 2003 is superior to previous versions of the operating system because it enables fewer network services by default. However, auditing is still necessary to detect newly installed applications and configuration changes that open unnecessary network ports.
Every open port is a potential backdoor for attackers to exploit spaces in the host application or surreptitiously access the application with another user's name and password (or use another legitimate authentication method). Either way, an important first step to protecting your network is to simply disable unused network applications.
Port scanning
Port scanning is the process of detecting listening applications by actively polling the network ports of a computer or other network device. Being able to read scan results and compare network reports with host port polling results allows you to get a clear picture of the traffic flowing through your network. Knowledge of network topology is important in preparing a strategic plan for scanning specific areas. For example, by scanning a range of external IP addresses, you can gather valuable data about an Internet attacker. Therefore, you should scan your network more often and close all unnecessary network ports.
External firewall port scanning can detect all responding services (such as the Web or email) hosted on internal servers. These servers should also be protected. Configure a familiar port scanner (for example, Network Mapper - Nmap) to scan the desired group of UDP or TCP ports. Typically, TCP port scanning is more reliable than UDP scanning due to deeper feedback from TCP's connection-oriented protocols. There are versions of Nmap for both Windows and Unix. Starting a basic scan is easy, although the program offers much more advanced features. To find open ports on the test computer, I ran the command
Nmap 192.168.0.161
Screen 1 shows the results of a scan session - in this case, a Windows 2003 computer in a standard configuration. The data collected from the port scan shows that there are six open TCP ports.
| Screen 1: Basic Nmap scan session |
- Port 135 is used by the RPC endpoint mapping feature found in many Windows technologies, such as COM/DCOM applications, DFS, event logging, file replication, message queuing, and Microsoft Outlook. This port should be blocked by the network perimeter firewall, but it is difficult to block it and still maintain Windows functionality.
- Port 139 is used by the NetBIOS session service, which enables the Find Other Computers Browser, File Sharing Services, Net Logon, and the Server service. It is difficult to close, just like port 135.
- Port 445 is used by Windows for file sharing. To close this port, you must block File and Printer Sharing for Microsoft Networks. Closing this port does not prevent the computer from connecting to other remote resources; however, other computers will not be able to connect to this system.
- Ports 1025 and 1026 are opened dynamically and are used by other Windows system processes, in particular various services.
- Port 3389 is used by Remote Desktop, which is not enabled by default, but is active on my test computer. To close the port, go to the Remote tab in the System Properties dialog box and clear the Allow users to connect remotely to this computer check box.
Be sure to search for open UDP ports and close unnecessary ones. The scanning program shows the open ports of the computer that are visible from the network. Similar results can be obtained using tools located on the host system.
Host scan
In addition to using a network port scanner, open ports on the host system can be detected using the following command (run on the host system):
Netstat -an
This command works on both Windows and UNIX. Netstat provides a list of active ports on a computer. On Windows 2003 Windows XP, you must add the -o option to get the corresponding program identifier (PID). Figure 2 shows the Netstat output for the same computer that was previously port scanned. Please note that several ports that were previously active are closed.
Firewall Log Audit
Another useful way to detect network applications that are sending or receiving data over the network is to collect and analyze more data in the firewall log. Deny entries that provide information from the firewall's front end are unlikely to be useful due to the "noise traffic" (eg, from worms, scanners, ping testing) that clogs the Internet. But if you log allowed packets from the internal interface, you can see all incoming and outgoing network traffic.
To see the raw traffic data on your network, you can install a network analyzer that connects to the network and records all detected network packets. The most widely used free network analyzer is Tcpdump for UNIX (the Windows version is called Windump), which is easy to install on your computer. After installing the program, you should configure it to work in the mode of receiving all network packets in order to log all traffic, and then connect it to a port monitor on the network switch and monitor all traffic passing through the network. Setting up a port monitor will be discussed below. Tcpdump is an extremely flexible program that can be used to view network traffic using specialized filters and show only information about IP addresses and ports or all packets. It is difficult to view network dumps on large networks without the help of appropriate filters, but care must be taken not to lose important data.
Combining Components
So far, we have looked at various methods and tools that can be used to detect applications using the network. It's time to combine them and show how to determine open network ports. It's amazing how chatty computers are on the network! First, it is recommended that you read the Microsoft document “Service overview and network port requirements for the Windows Server system” ( http://support.microsoft.com/default.aspx?scid=kb;en-us;832017), which lists the protocols (TCP and UDP) and port numbers used by applications and most core Windows Server services. This document describes these services and the associated network ports they use. We recommend that you download and print this helpful reference guide for Windows network administrators.
Setting up a network analyzer
It was previously noted that one way to determine the ports used by applications is to monitor traffic between computers using a network analyzer. To see all traffic, you need to connect a network analyzer to a hub or port monitor on the switch. Each port on a hub sees all the traffic from every computer connected to that hub, but hubs are an outdated technology and most companies are replacing them with switches, which provide good performance but are cumbersome to analyze: each switch port only accepts traffic destined for one computer connected to the hub. to this port. To analyze the entire network, you need to monitor the traffic sent to each switch port.
This requires setting up a port monitor (different vendors call it span port or mirrored port) on the switch. Installing a port monitor on a Cisco Catalyst switch from Cisco Systems is easy. You need to register on the switch and activate Enable mode, then go to configure terminal mode and enter the interface number of the switch port to which all monitored traffic should be sent. Finally, you must specify all monitored ports. For example, the following commands monitor three Fast Ethernet ports and forward a copy of the traffic to port 24.
Interface FastEthernet0/24 port monitor FastEthernet0/1 port monitor FastEthernet0/2 port monitor FastEthernet0/3 end
In this example, a network analyzer connected to port 24 will view all outgoing and incoming traffic from computers connected to the first three ports of the switch. To view the created configuration, enter the command
Write memory
Initial analysis
Let's look at an example of analyzing data passing through a network. If you are using a Linux computer for network analysis, you can get a comprehensive understanding of the type and frequency of packets on the network using a program such as IPTraf in Statistical mode. Traffic details can be found using the Tcpdump program.
The TCP/IP protocol is the foundation of the Internet, through which computers send and receive information from anywhere in the world, regardless of geographic location. Accessing a TCP/IP computer in another country is as easy as accessing a computer in the next room. The access procedure is identical in both cases, although connecting to a machine in another country may take a few milliseconds longer. As a result, citizens of any country can easily shop on Amazon.com; however, due to logical proximity, the task of information security becomes more complicated: any owner of a computer connected to the Internet anywhere in the world can try to establish an unauthorized connection with any other machine.
It is the responsibility of IT professionals to install firewalls and systems to detect suspicious traffic. Packet analysis retrieves information about the source and destination IP addresses and the network ports involved. The value of network ports is not inferior to IP addresses; these are the most important criteria for separating useful traffic from fake and harmful messages entering and leaving the network. Most Internet network traffic consists of TCP and UDP packets, which contain information about the network ports that computers use to route traffic from one application to another. A prerequisite for firewall and network security is for the administrator to have a thorough understanding of how computers and network devices use these ports.
Studying ports
Knowledge of the basic principles of network ports operation will be useful to any system administrator. With a basic understanding of TCP and UDP ports, an administrator can independently diagnose a failed network application or protect a computer that will access the Internet without calling a network engineer or firewall consultant.
The first part of this article (consisting of two parts) describes the basic concepts necessary to discuss network ports. The place of network ports in the general network model and the role of network ports and NAT (Network Address Translation) firewall in the connections of company computers to the Internet will be shown. Finally, network points will be indicated at which it is convenient to identify and filter network traffic on the corresponding network ports. Part 2 looks at some of the ports used by common applications and operating systems and introduces some tools for finding open network ports.
Brief overview of network protocols
TCP/IP is a set of network protocols through which computers communicate with each other. The TCP/IP suite is nothing more than pieces of software code installed in the operating system that provide access to these protocols. TCP/IP is a standard, so TCP/IP applications on a Windows machine should communicate successfully with the same application on a UNIX machine. In the early days of networking, in 1983, engineers developed the seven-layer OSI interconnection model to describe computer networking processes, from cable to application. The OSI model consists of physical, data link, network, transport, session, and application layers. Administrators who constantly work with the Internet and TCP/IP primarily deal with the network, transport and application layers, but for successful diagnostics it is necessary to know other layers. Despite the advanced age of the OSI model, it is still used by many specialists. For example, when a network engineer talks about Layer 1 or Layer 2 switches, or a firewall vendor talks about Layer 7 control, they are talking about the layers defined in the OSI model.
This article talks about network ports located at layer 4 - transport. In the TCP/IP suite, these ports are used by the TCP and UDP protocols. But before we get into the details of one layer, it's important to take a quick look at the seven OSI layers and the roles they play in modern TCP/IP networks.
Layers 1 and 2: Physical cables and MAC addresses
Layer 1, physical, represents the actual medium through which the signal travels, such as copper cable, fiber optic cable, or radio signals (in the case of Wi-Fi). Layer 2, data link, describes the data format for transmission in the physical medium. At Layer 2, packets are organized into frames and basic flow control and error handling functions can be implemented. The IEEE 802.3 standard, better known as Ethernet, is the most common Layer 2 standard for modern local area networks. A typical network switch is a Layer 2 device through which multiple computers physically connect and exchange data with each other. Sometimes two computers cannot connect to each other even though the IP addresses appear to be correct; the problem may be caused by errors in the Address Resolution Protocol (ARP) cache, indicating a problem at Layer 2. Additionally, some wireless access points (Access Point, AP) provide MAC address filtering, allowing only network adapters with a specific MAC address to connect to a wireless AP.
Layers 3 and 4: IP addresses and network ports
Layer 3, networking, supports routing. In TCP/IP, routing is implemented in IP. The packet's IP address belongs to Layer 3. Network routers are Layer 3 devices that analyze packet IP addresses and forward the packets to another router or deliver packets to local computers. If a suspicious packet is detected on the network, the first step is to check the IP address of the packet to determine the origin of the packet.
Together with the network layer, layer 4 (transport) is a good starting point for diagnosing network problems. On the Internet, Layer 4 contains the TCP and UDP protocols and information about the network port that associates a packet with a specific application. A computer's networking stack uses a TCP or UDP network port association with an application to direct network traffic to that application. For example, TCP port 80 is associated with a Web server application. This mapping of ports to applications is known as a service.
TCP and UDP are different. Essentially, TCP provides a reliable connection for communication between two applications. Before communication can begin, the two applications must establish a connection by completing the three-step TCP handshake process. UDP is more of a fire-and-forget approach. The reliability of the connection for TCP applications is ensured by the protocol, but the UDP application has to independently check the reliability of the connection.
The network port is a number between 1 and 65535 that is specified and known to both applications between which communication is being established. For example, a client typically sends an unencrypted request to a server at a target address on TCP port 80. Typically, a computer sends a DNS request to a DNS server at a target address on UDP port 53. The client and server have a source and destination IP address, and the source and destination network port, which may vary. Historically, all port numbers below 1024 are called "known port numbers" and are registered with the Internet Assigned Numbers Authority (IANA). On some operating systems, only system processes can use ports in this range. Additionally, organizations can register ports 1024 through 49151 with IANA to associate the port with their application. This registration provides a structure that helps avoid conflicts between applications attempting to use the same port number. However, in general, there is nothing to prevent an application from requesting a specific port as long as it is not occupied by another active program.
Historically, the server could listen on low-numbered ports, and the client could initiate a connection on a high-numbered port (above 1024). For example, a Web client might open a connection to a Web server on destination port 80, but associate a randomly selected source port, such as TCP port 1025. When responding to the client, the Web server addresses the packet to the client with source port 80 and destination port 1025. The combination of an IP address and port is called a socket and must be unique on the computer. For this reason, when setting up a Web server with two separate Web sites on the same computer, you must use multiple IP addresses, such as address1:80 and address2:80, or configure the Web server to listen on multiple network ports, such as address1:80 and address1:81. Some Web servers allow multiple Web sites to run on a single port by requesting a host header, but this function is actually performed by the Web server application at a higher layer 7.
As networking capabilities became available in operating systems and applications, programmers began using port numbers higher than 1024 without registering all applications with IANA. By searching the Internet for any network port, you can usually quickly find information about applications that use that port. Or you can search for Well Known Ports and find many sites that list the most common ports.
When blocking network applications on a computer or troubleshooting firewall flaws, most of the work comes from classifying and filtering Layer 3 IP addresses and Layer 4 protocols and network ports. To quickly distinguish between legitimate and suspicious traffic, you should learn to recognize the 20 most widely used ones in the enterprise TCP and UDP ports.
Learning to recognize and become familiar with network ports goes beyond assigning firewall rules. For example, some Microsoft security patches describe how to close NetBIOS ports. This measure helps limit the spread of worms that penetrate through vulnerabilities in the operating system. Knowing how and where to close these ports can help reduce network security risks while preparing to deploy a critical patch.
And straight to level 7
It's rare to hear about Layer 5 (session) and Layer 6 (presentation) these days, but Layer 7 (application) is a hot topic among firewall vendors. The newest trend in network firewalls is Layer 7 inspection, which describes the techniques used to analyze how an application interacts with network protocols. By analyzing the payload of a network packet, a firewall can determine whether the traffic passing through it is legitimate. For example, a Web request contains a GET statement inside a Layer 4 packet (TCP port 80). If your firewall has Layer 7 functionality, you can verify that the GET statement is correct. Another example is that many peer-to-peer (P2P) file sharing programs can hijack port 80. As a result, an outsider can configure the program to use a port of their own choosing - most likely a port that should be left open in a given firewall. If a company's employees need access to the Internet, port 80 must be opened, but to distinguish legitimate Web traffic from P2P traffic directed by someone to port 80, the firewall must provide layer 7 control.
Role of the firewall
Having described the network layers, we can move on to describe the mechanism for communication between network applications through firewalls, paying particular attention to the network ports used. In the following example, the client browser communicates with a Web server on the other side of the firewall, just as a company employee would communicate with a Web server on the Internet.
Most Internet firewalls operate at layers 3 and 4 to examine and then allow or block incoming and outgoing network traffic. In general, the administrator writes access control lists (ACLs) that define the IP addresses and network ports of traffic that is blocked or allowed. For example, to access the Web, you need to launch a browser and point it at the Web site. The computer initiates an outgoing connection by sending a sequence of IP packets consisting of a header and payload information. The header contains route information and other packet attributes. Firewall rules are often written with routing information in mind and typically contain the source and destination IP addresses (layer 3) and the packet protocol (layer 4). When browsing the Web, the destination IP address belongs to the Web server, and the protocol and destination port (by default) are TCP 80. The source IP address is the address of the computer from which the user accesses the Web, and the source port is usually a dynamically assigned number , greater than 1024. The useful information is independent of the header and is generated by the user application; in this case, it is a request to the Web server to provide a Web page.
The firewall analyzes outgoing traffic and allows it according to the firewall rules. Many companies allow all outbound traffic from their network. This approach simplifies configuration and deployment, but reduces security due to the lack of control over the data leaving the network. For example, a Trojan horse can infect a computer on a business network and send information from that computer to another computer on the Internet. It makes sense to create access control lists to block such outgoing information.
In contrast to the outgoing approach of many firewalls, most are configured to block incoming traffic. Typically, firewalls only allow incoming traffic in two situations. The first is traffic arriving in response to an outgoing request sent previously by the user. For example, if you point your browser to the address of a Web page, the firewall allows HTML code and other components of the Web page to enter the network. The second case is hosting an internal service on the Internet, such as a mail server, Web or FTP site. Hosting such a service is usually called port translation or server publishing. The implementation of port translation varies among firewall vendors, but the underlying principle is the same. The administrator defines a service, such as TCP port 80 for the Web server and a back-end server to host the service. If packets enter the firewall through the external interface corresponding to this service, then the port translation mechanism forwards them to a specific computer on the network hidden behind the firewall. Port translation is used in conjunction with the NAT service described below.
NAT Basics
With NAT, multiple computers in a company can share a small public IP address space. A company's DHCP server can allocate an IP address from one of the private, Internet-non-routable IP address blocks defined in Request for Comments (RFC) No. 1918. Multiple companies can also share the same private IP address space. Examples of private IP subnets are 10.0.0.0/8, 172.16.0.0/12, and 192.168.0.0/16. Internet routers block any packets directed to one of the private addresses. NAT is a firewall feature that allows companies using private IP addresses to communicate with other computers on the Internet. The firewall knows how to translate incoming and outgoing traffic to private internal IP addresses so that every computer can access the Internet.