How to encrypt data. Encrypt android phone Android data encryption
Briefly: If you use a graphic key to access your phone, then 99% of the time this is enough to ensure that no one can access the information on your phone without your knowledge. If the data on your phone is very sensitive, then you should use the phone's built-in full encryption feature.
Today, almost all smartphones have become carriers of important personal or corporate data. Also, through the owner's phone, you can easily access his accounts, such as Gmail, DropBox, FaceBook and even corporate services. Therefore, to one degree or another, it is worth worrying about the confidentiality of this data and using special means to protect the phone from unauthorized access in the event of its theft or loss.
- From whom should you protect your phone data?
- Built-in data protection in Android.
- Full phone memory encryption
- Results
What information is stored on the phone and why protect it?
A smartphone or tablet often serves as a mobile secretary, freeing the owner’s head from storing a large amount of important information. The phone book contains numbers of friends, co-workers, and family members. Credit card numbers, access codes, passwords to social networks, email and payment systems are often written in the notebook.
The list of recent calls is also very important.
Losing your phone can be a real disaster. Sometimes they are stolen specifically to penetrate personal life or to share profits with the owner.
Sometimes they are not stolen at all, but are used for a short time, unnoticed, but a few minutes is quite enough for an experienced malicious user to find out all the details.
The loss of confidential information can result in financial ruin, the collapse of your personal life, and the breakup of your family.
I wish I didn't have it! - the former owner will say. - It’s so good that you had him! - the attacker will say.
And so what needs to be protected on the phone:
- Accounts. This includes, for example, access to your gmail inbox. If you have set up synchronization with facebook, dropbox, twitter. Logins and passwords for these systems are stored in clear text in the phone profile folder /data/system/accounts.db.
- History of SMS correspondence and phone book also contain confidential information.
- Web browser program. The entire browser profile must be protected. It is known that the Web Browser (built-in or third-party) remembers all passwords and logins for you. This is all stored in open form in the program profile folder in the phone’s memory. Moreover, usually the sites themselves (using cookies) remember you and leave access to your account open, even if you did not specify to remember the password.
If you use synchronization of a mobile browser (Chrome, FireFox, Maxthon, etc.) with a desktop version of the browser to transfer bookmarks and passwords between devices, then you can assume that you can access all passwords from other sites from your phone. - Memory card. If you store confidential files on your memory card or download documents from the Internet. Typically, photos and videos taken are stored on a memory card.
- Photo album.
Who should you protect your phone data from:
- From a random person who finds your lost phonel because from “accidental” theft of the phone.
It is unlikely that the data on the phone will be of value to the new owner in this case. Therefore, even simple graphic key protection will ensure data safety. Most likely, the phone will simply be reformatted for reuse. - From prying eyes(co-workers/children/wives), who can gain access to your phone without your knowledge, taking advantage of your absence. Simple protection will ensure the safety of your data.
- Providing forced access
It happens that you are voluntarily forced to provide a phone number and open access to the system (information). For example, when your wife, a government official, or an employee of the service center where you took the phone for repair asks you to look at your phone. In this case, any defense is useless. Although it is possible, using additional programs, to hide the fact of the presence of some information: hide part of the SMS correspondence, part of the contacts, some files. - From targeted theft of your phone.
For example, someone really wanted to know what was on your phone and made an effort to get it.
In this case, only full encryption of the phone and SD card helps.
Built-in data protection on Android devices .
1. Lock screen with Pattern Key.
This method is very effective in the first and second cases (protection against accidental loss of the phone and protection from prying eyes). If you accidentally lose your phone or forget it at work, no one will be able to use it. But if your phone purposefully fell into the wrong hands, then this is unlikely to save you. Hacking can even occur at the hardware level.
The screen can be locked with a password, PIN code and Pattern Key. You can select the locking method by launching the settings and selecting the Security -> Screen lock section.
Graphic Key (Pattern) - c The most convenient and at the same time reliable way to protect your phone.

None- lack of protection,
Slide— to unlock, you need to swipe your finger across the screen in a certain direction.
Pattern- this is a Graphic Key, it looks something like this:
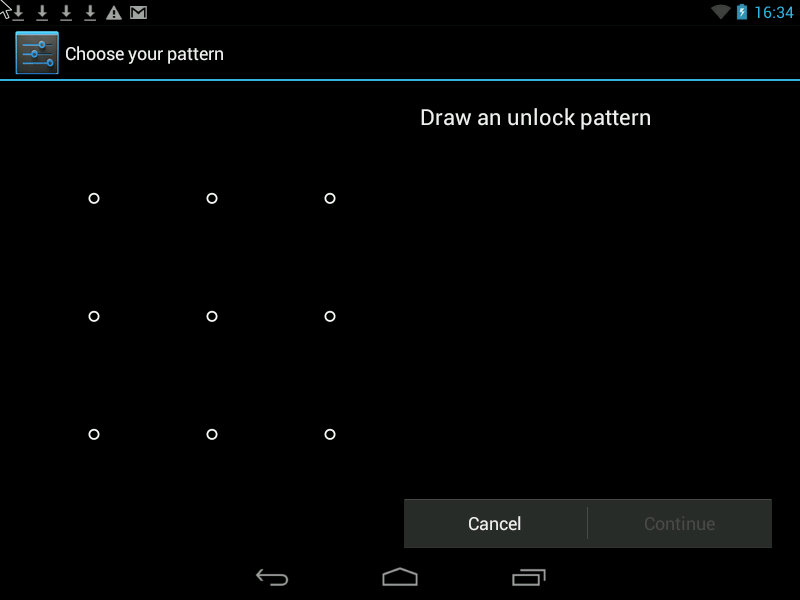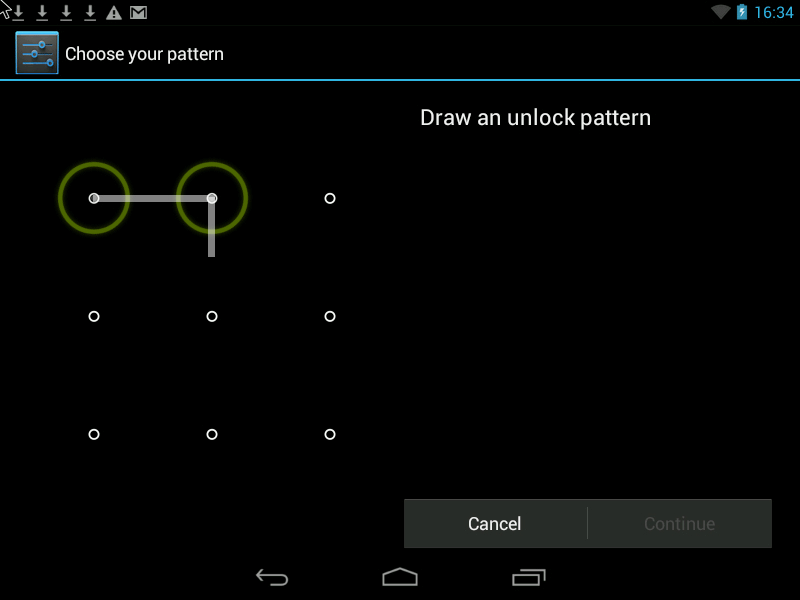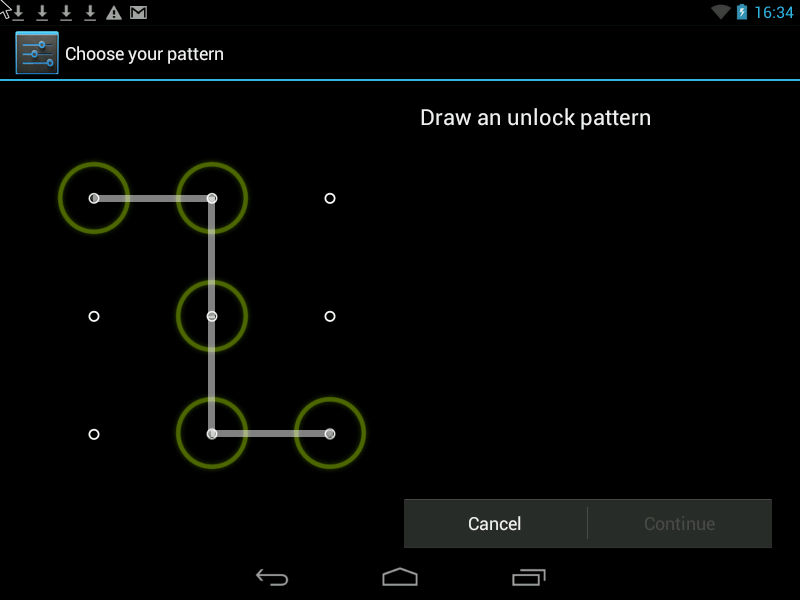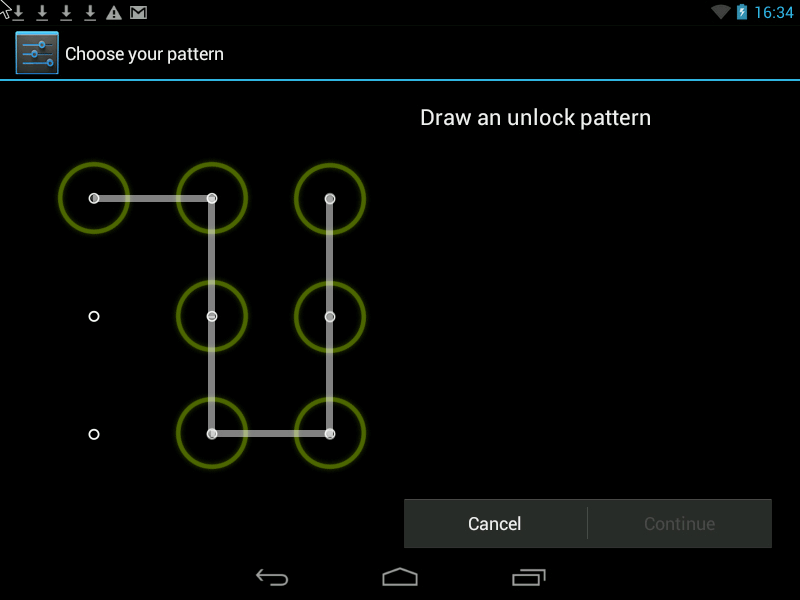
You can improve security in two ways.
1. Enlarge the Graphic key input field. It can vary from 3x3 dots on the screen to 6x6 (Android 4.2 is found in some models, depending on the Android version and phone model).
2. Hide the display of the points and “path” of the graphic key on the smartphone screen so that it is impossible to peek at the key.
3. Set the screen to automatically lock after 1 minute of inactivity on the phone.
Attention!!! What happens if you forgot your pattern key:
- The number of incorrect attempts to draw a Graphic Key is limited to 5 times (in different phone models the number of attempts can be up to 10 times).
- After you have tried all your attempts but still have not drawn the Pattern Key correctly, the phone is locked for 30 seconds. After this, you will most likely have a couple of attempts again, depending on your phone model and Android version.
- Next, the phone asks for the login and password of your Gmail account, which is registered in the phone’s Accounts settings.
This method will only work if your phone or tablet is connected to the Internet. Otherwise deadlock or reboot to manufacturer settings.
It happens that the phone falls into the hands of a child - he starts playing, draws the key many times and this leads to the key being blocked.
PIN is a password consisting of several numbers.
And finally, Password— the most reliable protection, with the ability to use letters and numbers. If you decide to use a password, then you can enable the Phone encryption option.
Encryption of phone memory.
The function is included in the Android package version 4.0* and higher. for tablets. But this feature may be missing in many budget phones.
Allows you to encrypt your phone's internal memory so that it can only be accessed with a password or PIN code. Encryption helps protect the information on your phone in case ts
targeted theft. There is no way that attackers will be able to access your data from your phone.
A prerequisite for using encryption is to set a screen lock using a password.
This method achieves the preservation of user data located in the phone's memory, such as the phone book, browser settings, passwords used on the Internet, photos and videos that the user received using the camera and did not copy to the SD card.



— SD card encryption is enabled as a separate option.
— Memory encryption may take up to an hour depending on the amount of memory on the device. The phone cannot be used during encryption.
What if you forgot your password?
Password recovery is not provided in this case. You can do a full RESET on your phone or tablet, i.e. reinstall Android, but user data from the phone or tablet will be erased. Thus, if an attacker does not know the password to unlock the phone, he will not be able to use it. It will also be impossible to see data from the phone’s memory using other programs by connecting the phone to a computer, because all internal memory is encrypted. The only way to get your phone working again is to reformat it.
Attention, the full encryption function is present only starting from Android OS 4.0 - 4.1 and may simply not be available on some phone models. Most often found in phones from Samsung, HTC, LG, Sony. Some Chinese models also have an encryption feature. On some phones this function is located in the “Memory” section.
Flaws:
- You will need to constantly enter a fairly complex password (6-10 characters) even if you just want to make a call. Although it is possible to set a long time interval (30 minutes) during which the password will not be requested when you turn on the phone screen. On some phone models, the minimum password length can be 3 characters.
- On some phone models, it is not possible to disable encryption if you want to avoid having to constantly enter a password. Encryption can only be disabled by returning the phone to factory settings and erasing all data.
Encrypting an external SD memory card
The function is included in the standard Android 4.1.1 package for tablets. Missing from many budget builds.
The function provides reliable data protection on an external SD card. Personal photographs, text files with commercial and personal information can be stored here.
Allows you to encrypt files on an SD card without changing their names or file structure, while maintaining a preview of graphic files (icons). The function requires setting a display lock password of at least 6 characters.




It is possible to cancel encryption. When changing the password, automatic re-encryption occurs.
If the user has lost the memory card, encrypted files cannot be read through the card-reader. If you put it on another tablet with a different password, then the encrypted data also cannot be read.
Other Encryption Properties:
- Transparent encryption. If the card is inserted into the tablet and the user has unlocked the screen with a password, any application sees the files in decrypted form.
- If you connect the tablet via a USB cable to a computer, encrypted files can also be read on the computer by first unlocking the card from the screen of the mobile device.
- If you write some other unencrypted files onto the card via the card-reader, they will also be encrypted after inserting the card into the tablet.
- If you have an encrypted card, you cannot cancel the lock password.
- Data is encrypted at the file level (the file names are visible, but the contents of the file are encrypted).
Disadvantage of the program:O missing from most Android builds.
It should be emphasized that the best safety of data is a complete copy of it on your Computer in A smartphone is a fairly fragile small device, which means there is always a possibility of it breaking or being lost.
Improving the usability of a secure smartphone
Full phone encryption provides the strongest level of protection, but constantly entering a 6-digit password makes it difficult to use. But there is a solution.
In the Android system from version 4.2*, it is possible to display some applications\widgets on the lock screen, and thus you can perform simple actions without constantly unlocking the phone (without entering a 6-digit password).
Results:
- The built-in and free features to protect your phone are very reliable. They are able to protect the user’s contacts, correspondence and calls, accounts in various programs and networks, as well as files and folders located both in the phone’s memory and on a removable SD card from prying eyes.
- Before buying a phone, you should make sure how the required protection works in this particular phone model: the requirement to use an overly complex PIN code or password on the lock screen (Pattern Key is not suitable), irreversible encryption of the phone’s internal memory, i.e. The only way to refuse encryption is to completely reset your phone.
- Important! Make sure that if you forget your password or Pattern Key, you can restore access to the phone or you can easily restore the phone settings and information in case you have to do a hard reset (resetting the phone to factory settings with the loss of all data).
- You only need to store a backup copy of confidential data on your Computer, on a DVD or in the cloud.
Google introduced full data encryption on Android phones running Gingerbread (2.3.x), but it has undergone some dramatic changes since then. As on some more expensive phones running Lollipop (5.x) and above, it is enabled out of the box, while on some older or earlier devices, you have to enable it yourself. You can read how to encrypt flash drives.
Why you might need phone encryption
Encryption stores your phone's data in an unreadable, almost encrypted form. (In order to actually perform low-level encryption functions, Android uses DM-crypt, which is the standard disk encryption system in the Linux kernel. It is the same technology used by various Linux distributions.) When you enter a PIN, password, or pattern on lock screen, the phone decrypts the data, making it readable. If someone doesn't know the PIN or password, they won't be able to access the data. (On Android 5.1 and above, encryption does not require you to set a PIN or password, but it is highly recommended because without a PIN or password, the effectiveness of the encryption is reduced.)
Data encryption protects sensitive data on your phone. For example, corporations with sensitive business data on their phones will need to use encryption (with screen locking) to protect that data from corporate espionage. An attacker will not be able to access the data without the encryption key, although there are more advanced hacking methods that make this possible.
If you're a regular user, you might think you don't have sensitive data on your phone, but you're probably wrong. If your phone is stolen, the thief now has access to your email inbox, knows your home address, and a large amount of other personal information. Most thieves will not access data using a standard unlock code, regardless of whether the device is encrypted or not. Most thieves are more interested in selling your phone (resetting data) than in accessing your personal data. But this does not mean that you do not need to protect your data.
Things to consider before enabling encryption
Most new Android phones come with encryption already turned on by default. If this is the case with your phone, then there is no way to disable encryption. But if you're using a device that doesn't have encryption enabled by default, then there are some things to consider before enabling it:
Performance deteriorates:
Once you enable the encryption feature, the data will have to be decrypted on the fly every time you unlock your phone. So you may notice a slight drop in performance when it's enabled, although it's not noticeable at all for most users (especially if you have a powerful phone).Encryption of existing data can be enabled once: If you have enabled encryption, the only way to cancel encryption is to reset the device to factory settings and all data will be lost. So make sure you are sure you are ready for this before you start the process.
The next screen will present a warning so you know what to expect once the process is complete, most of which we've already covered in this article. If you're ready to continue, click the "encrypt phone" button.
Another warning (seriously, we want to make sure you understand what you're about to do), do not interrupt the process under any circumstances. If you are still not scared, then click on the “” button and start the process.
The phone will reboot and begin the encryption process. A progress bar and estimated time to completion will be shown on the display, which should at least give you an idea of how long you'll be without your beloved phone. Just expect everything to be fine soon. You can do it. You are strong.
After the phone finishes the process, it will reboot and you will be together again. If you have set up a screen lock password, PIN or pattern, you must enter it into the system and the device will complete the power-on process.
If you haven't set up a PIN or password, now is the time to do so. Head to Settings > Security on your device. Next, select the "Lock Screen" option (keep in mind that the names of the menu options may vary slightly between different Android phones, and even the Samsung Galaxy line of devices).

Today, every user has to think about protecting confidential information from unauthorized persons. Mobile device manufacturers care about future customers and their right to privacy, so they are paying more and more attention to preserving personal data. Tablets can also be classified as personal devices, so let's talk about protecting them.
Is it possible to disable encryption on a tablet?
The system functions of modern tablets support encryption mode for information stored both on the internal memory of the device and on an external SD card. It should be remembered that running encryption has a negative impact on the performance of the device. Those who value computing power over the safety of personal data should definitely read this article.If you're lucky enough to own an Android tablet that originally runs a version of the operating system, you won't be able to disable the encryption feature. The developers decided to introduce forced encryption of information on the latest versions of the OS, but don’t despair, because hackers don’t sleep either. There is no doubt that these workers will soon offer their own solution to this problem. At the same time, tablets whose operating system has been updated to the latest version from earlier ones are not limited by such prohibitions, so the option to disable encryption is available. However, we recommend that you think about whether you really need this?
On earlier versions of Android, up to 2.3.4, encryption must be started manually. This option is in the settings menu: Security->Encryption->Encrypt device. It must be borne in mind that after this it is impossible to decrypt the encrypted data, since the developer did not provide such a possibility. Thus, if you need to decrypt information, its loss is inevitable. To do this, you will need to reset the device to factory settings from "recovery" mode.
To perform such a reset, you need to hold down the volume up and down keys, as well as the power key, while the tablet is turned off. You will be loaded into the engineering menu, where using the volume buttons you need to find the “wipe data/factory reset” menu item and, having selected it, press the power key. When the reset operation is completed, you need to reboot by selecting "reboot". After booting into operating mode on the tablet, you should restore your personal data, and then no longer run encryption.
Data encryption in the Android OS is closely related to two problems: controlling access to memory cards and transferring applications to them. Many programs contain activation data, payment information, and confidential information. Its protection requires managing access rights, which are not supported by the FAT 32 file system typical for cards. Therefore, in each version of Android, approaches to encryption have changed dramatically - from the complete lack of cryptographic protection of removable media to their deep integration into a single partition with on-the-fly encryption.
The special role of the memory card
Initially, Android developers intended to use the memory card only as a separate storage for user files. It was just a multimedia warehouse without any requirements for its protection and reliability. microSD(HC) cards with FAT32 coped well with the role of simple storage, freeing the internal memory from photos, videos and music.
The ability to transfer not only multimedia files, but also applications to a memory card first appeared in Android 2.2 Froyo. It was implemented using the concept of encrypted containers for each application, but this exclusively protected against the card falling into the wrong hands - but not the smartphone.
In addition, this was a half-measure: many programs were transferred partially, leaving some of the data in the internal memory, and some (for example, system ones or containing widgets) were not transferred to the card at all. The very possibility of transferring applications depended on their type (pre-installed or third-party) and internal structure. For some, the directory with user data was immediately located separately, while for others it was located in a subdirectory of the program itself.
If applications intensively used read/write operations, then the reliability and speed of the cards could no longer satisfy the developers. They deliberately made it impossible to transfer programs using standard means. Thanks to this trick, their creation was guaranteed to be registered in the internal memory with a large rewriting resource and high performance.
With the fourth version of Android, it became possible to choose where to place the application. It was possible to designate a memory card as a disk for installing programs by default, but not all firmware correctly supported this function. How it works in a specific device could only be determined experimentally.
Where x:y is the memory card number.
$ sm partition disk: x: y mixed nn |
where nn is the remaining volume as a percentage for a FAT32 volume.
For example, the command sm partition disk:179:32 mixed 20 will add 80% of the card’s capacity to the built-in memory and leave a FAT32 volume on it with 1/5 of its capacity.
On some smartphones, this method “as is” no longer works and requires additional tricks. Manufacturers are doing everything to artificially divide their products into market niches. Top models are available with different amounts of built-in memory, and there are fewer and fewer people willing to overpay for it.
Some smartphones do not have a memory card slot (for example, the Nexus series), but support connecting USB-Flash drives in OTG mode. In this case, the flash drive can also be used to expand the internal memory. This is done with the following command:
$ adb shell sm set - force - adoptable true |
By default, the ability to use USB-OTG to create custom storage is disabled because unexpected removal could result in data loss. The likelihood of a memory card suddenly disconnecting is much lower due to its physical placement inside the device.

Select a pattern, PIN or password to set up your security.

You will be offered a choice: protection using a PIN code, password or pattern at startup. The choice is up to you, but we recommend choosing some kind of protection as it increases the security of your device.

Note that even with a fingerprint reader, you can't use your fingerprint to unlock the device the first time you boot—you'll have to enter a password, PIN, or pattern. Once the device has been decrypted using the correct method, the fingerprint scanner can already be used to unlock the screen.
From now on, your device will be encrypted, but if you want to disable encryption, you can do so by performing a factory reset. If you have a new device that automatically has encryption enabled, there is no way to disable it, not even through a factory reset.
Hello, friends! Today's article will look at programs for encrypting files, more precisely for working with cryptocontainers in Android. For those who do not know what a crypto container is, we talked about it in this article.
We will not consider highly specialized items, photographs, etc. We have already talked about all this in previous publications (use the site search form). In this article, we will not study each application separately. This is a superficial overview of all popular data encryption programs for Android. In the future, following this article, there will be separate instructions for each application.
You may also be interested in the article “”, in which we talked about how to securely encrypt correspondence using the application and K-9 Mail.
The following encryption programs are currently available on Google Play:
- LUKS Manager;
- EDS Lite;
- Cryptonite;
- CyberSafe Mobile.
In addition, the application allows you to share encrypted files with other users and allows you to encrypt arbitrary folders on Google Drive. However, for every barrel of honey there is a fly in the ointment. The application is paid. And its free version limits the maximum password length to only 2 characters, which, as you understand, is very little. On the other hand, the application is very inexpensive (less than $3) and it does not restrict the password when opening the container, but only when creating it. That is, if you need to use an application with the same set of data on different devices, then you can create a container on one device and copy it to another, and buy the program only on one device (on which you will create the container).
Data encryption application for Android
Which app should you choose?
The answer is simple. If you use TrueCrypt on a personal computer, then the choice is obvious - EDS Lite. If you want cloud encryption, it looks like you'll have to upgrade to CyberSafe on your computer.
Briefly: If you use a graphic key to access your phone, then 99% of the time this is enough to ensure that no one can access the information on your phone without your knowledge. If the data on your phone is very sensitive, then you should use the phone's built-in full encryption feature.
Today, almost all smartphones have become carriers of important personal or corporate data. Also, through the owner's phone, you can easily access his accounts, such as Gmail, DropBox, FaceBook and even corporate services. Therefore, to one degree or another, it is worth worrying about the confidentiality of this data and using special means to protect the phone from unauthorized access in the event of its theft or loss.
- From whom should you protect your phone data?
- Built-in data protection in Android.
- Full phone memory encryption
- Results
What information is stored on the phone and why protect it?
A smartphone or tablet often serves as a mobile secretary, freeing the owner’s head from storing a large amount of important information. The phone book contains numbers of friends, co-workers, and family members. Credit card numbers, access codes, passwords to social networks, email and payment systems are often written in the notebook.
The list of recent calls is also very important.
Losing your phone can be a real disaster. Sometimes they are stolen specifically to penetrate personal life or to share profits with the owner.
Sometimes they are not stolen at all, but are used for a short time, unnoticed, but a few minutes is quite enough for an experienced malicious user to find out all the details.
The loss of confidential information can result in financial ruin, the collapse of your personal life, and the breakup of your family.
I wish I didn't have it! - the former owner will say. - It’s so good that you had him! - the attacker will say.
And so what needs to be protected on the phone:
- Accounts. This includes, for example, access to your gmail inbox. If you have set up synchronization with facebook, dropbox, twitter. Logins and passwords for these systems are stored in clear text in the phone profile folder /data/system/accounts.db.
- History of SMS correspondence and phone book also contain confidential information.
- Web browser program. The entire browser profile must be protected. It is known that the Web Browser (built-in or third-party) remembers all passwords and logins for you. This is all stored in open form in the program profile folder in the phone’s memory. Moreover, usually the sites themselves (using cookies) remember you and leave access to your account open, even if you did not specify to remember the password.
If you use synchronization of a mobile browser (Chrome, FireFox, Maxthon, etc.) with a desktop version of the browser to transfer bookmarks and passwords between devices, then you can assume that you can access all passwords from other sites from your phone. - Memory card. If you store confidential files on your memory card or download documents from the Internet. Typically, photos and videos taken are stored on a memory card.
- Photo album.
Who should you protect your phone data from:
- From a random person who finds your lost phonel because from “accidental” theft of the phone.
It is unlikely that the data on the phone will be of value to the new owner in this case. Therefore, even simple graphic key protection will ensure data safety. Most likely, the phone will simply be reformatted for reuse. - From prying eyes(co-workers/children/wives), who can gain access to your phone without your knowledge, taking advantage of your absence. Simple protection will ensure the safety of your data.
- Providing forced access
It happens that you are voluntarily forced to provide a phone number and open access to the system (information). For example, when your wife, a government official, or an employee of the service center where you took the phone for repair asks you to look at your phone. In this case, any defense is useless. Although it is possible, with the help of additional programs, to hide the fact of the presence of some information: hide part of the SMS correspondence, part of the contacts, some files. - From targeted theft of your phone.
For example, someone really wanted to know what was on your phone and made an effort to get it.
In this case, only full encryption of the phone and SD card helps.
Built-in data protection on Android devices .
1. Lock screen with Pattern Key.
This method is very effective in the first and second cases (protection against accidental loss of the phone and protection from prying eyes). If you accidentally lose your phone or forget it at work, no one will be able to use it. But if your phone purposefully fell into the wrong hands, then this is unlikely to save you. Hacking can even occur at the hardware level.
The screen can be locked with a password, PIN code and Pattern Key. You can select the locking method by launching the settings and selecting the Security -> Screen lock section.
Graphic Key (Pattern) - c The most convenient and at the same time reliable way to protect your phone.

None- lack of protection,
Slide- To unlock, you need to swipe your finger across the screen in a certain direction.
Pattern- this is a Graphic Key, it looks something like this:

You can improve security in two ways.
1. Enlarge the Graphic key input field. It can vary from 3x3 dots on the screen to 6x6 (Android 4.2 is found in some models, depending on the Android version and phone model).
2. Hide the display of the points and “path” of the graphic key on the smartphone screen so that it is impossible to peek at the key.
3. Set the screen to automatically lock after 1 minute of inactivity on the phone.
Attention!!! What happens if you forgot your pattern key:
- The number of incorrect attempts to draw a Graphic Key is limited to 5 times (in different phone models the number of attempts can be up to 10 times).
- After you have tried all your attempts but still have not drawn the Pattern Key correctly, the phone is locked for 30 seconds. After this, you will most likely have a couple of attempts again, depending on your phone model and Android version.
- Next, the phone asks for the login and password of your Gmail account, which is registered in the phone’s Accounts settings.
This method will only work if your phone or tablet is connected to the Internet. Otherwise deadlock or reboot to manufacturer settings.
It happens that the phone falls into the hands of a child - he starts playing, draws the key many times and this leads to the key being blocked.
PIN- this is a password consisting of several numbers.
And finally, Password- the most reliable protection, with the ability to use letters and numbers. If you decide to use a password, then you can enable the Phone encryption option.
Encryption of phone memory.
The function is included in the Android package version 4.0* and higher. for tablets. But this feature may be missing in many budget phones.
Allows you to encrypt your phone's internal memory so that it can only be accessed with a password or PIN code. Encryption helps protect the information on your phone in case ts
targeted theft. There is no way that attackers will be able to access your data from your phone.
A prerequisite for using encryption is to set a screen lock using a password.
This method achieves saving user data located in the phone's memory, such as phone book, browser settings, passwords used on the Internet, photos and videos that the user received using the camera and did not copy to the SD card.



SD card encryption is enabled as a separate option.
- Memory encryption may take up to an hour depending on the amount of memory on the device. The phone cannot be used during encryption.
What if you forgot your password?
Password recovery is not provided in this case. You can do a full RESET on your phone or tablet, i.e. reinstall Android, but user data from the phone or tablet will be erased. Thus, if an attacker does not know the password to unlock the phone, he will not be able to use it. It will also be impossible to see data from the phone’s memory using other programs by connecting the phone to a computer, because all internal memory is encrypted. The only way to get your phone working again is to reformat it.
Attention, the full encryption function is present only starting from Android OS 4.0 - 4.1 and may simply not be available on some phone models. Most often found in phones from Samsung, HTC, LG, Sony. Some Chinese models also have an encryption feature. On some phones this function is located in the “Memory” section.
Flaws:
- You will need to constantly enter a fairly complex password (6-10 characters) even if you just want to make a call. Although it is possible to set a long time interval (30 minutes) during which the password will not be requested when you turn on the phone screen. On some phone models, the minimum password length can be 3 characters.
- On some phone models, it is not possible to disable encryption if you want to avoid having to constantly enter a password. Encryption can only be disabled by returning the phone to factory settings and erasing all data.
Encrypting an external SD memory card
The function is included in the standard Android 4.1.1 package for tablets. Missing from many budget builds.
The function provides reliable data protection on an external SD card. Personal photographs, text files with commercial and personal information can be stored here.
Allows you to encrypt files on an SD card without changing their names or file structure, while maintaining a preview of graphic files (icons). The function requires setting a display lock password of at least 6 characters.




It is possible to cancel encryption. When changing the password, automatic re-encryption occurs.
If the user has lost the memory card, encrypted files cannot be read through the card-reader. If you put it on another tablet with a different password, then the encrypted data also cannot be read.
Other Encryption Properties:
- Transparent encryption. If the card is inserted into the tablet and the user has unlocked the screen with a password, any application sees the files in decrypted form.
- If you connect the tablet via a USB cable to a computer, encrypted files can also be read on the computer by first unlocking the card from the screen of the mobile device.
- If you write some other unencrypted files onto the card via the card-reader, they will also be encrypted after inserting the card into the tablet.
- If you have an encrypted card, you cannot cancel the lock password.
- Data is encrypted at the file level (the file names are visible, but the contents of the file are encrypted).
Disadvantage of the program:O missing from most Android builds.
It should be emphasized that the best safety of data is a complete copy of it on your Computer in A smartphone is a fairly fragile device of small size, which means there is always the possibility of it breaking or being lost.
Improving the usability of a secure smartphone
Full phone encryption provides the strongest level of protection, but constantly entering a 6-digit password makes it difficult to use. But there is a solution.
In the Android system from version 4.2*, it is possible to display some applications\widgets on the lock screen, and thus you can perform simple actions without constantly unlocking the phone (without entering a 6-digit password).
Results:
- The built-in and free features to protect your phone are very reliable. They are able to protect the user’s contacts, correspondence and calls, accounts in various programs and networks, as well as files and folders located both in the phone’s memory and on a removable SD card from prying eyes.
- Before buying a phone, you should make sure how the required protection works in this particular phone model: the requirement to use an overly complex PIN code or password on the lock screen (Pattern Key is not suitable), irreversible encryption of the phone’s internal memory, i.e. The only way to refuse encryption is to completely reset your phone.
- Important! Make sure that if you forget your password or Pattern Key, you can restore access to the phone or you can easily restore the phone settings and information in case you have to do a hard reset (resetting the phone to factory settings with the loss of all data). http://www..png lyuda 2013-06-19 19:13:07 2015-06-24 17:54:26 Protect data on Android phones and tablets.
The FBI tried through the court to twist the arms of Apple, which did not want to create code to bypass its own security system. A critical vulnerability has been discovered in the Android kernel, allowing superuser access to bypass all security mechanisms. These two events, although unrelated, coincided in time, clearly demonstrating the differences in the security systems of the two popular mobile operating systems. Let's put aside for a moment the issue of a critical vulnerability in the Android kernel, which is unlikely to ever be fixed by most manufacturers in already released models, and consider the data encryption mechanisms in Android and Apple iOS. But first, let’s talk about why encryption is needed in mobile devices at all.
Why encrypt your phone?
An honest person has nothing to hide - the most popular leitmotif that sounds after every publication on the topic of data protection. “I have nothing to hide,” many users say. Alas, much more often this only means the confidence that no one will bother to get into the data of a particular Vasya Pupkin, because who is interested in them at all? Practice shows that this is not so. We won’t go far: just last week, the career of a school teacher who left her phone on the table for a moment ended with her dismissal. The students instantly unlocked the device and took out photographs of the teacher in a form that is condemned by the puritanical morality of American society. The incident served as sufficient grounds for the teacher's dismissal. Stories like this happen almost every day.
How unencrypted phones are hacked
We won't go into detail, just keep in mind: data from an unencrypted phone can be recovered in almost a hundred percent of cases. “Almost” here refers rather to cases where the phone was attempted to be physically damaged or destroyed immediately before the data was removed. Many Android and Windows Phone devices have a service mode that allows you to drain all data from the device’s memory via a regular USB cable. This applies to most devices on the Qualcomm platform (HS-USB mode, which works even when the bootloader is locked), on Chinese smartphones with MediaTek (MTK), Spreadtrum and Allwinner processors (if the bootloader is unlocked), as well as all smartphones manufactured by LG (there in general a convenient service mode that allows you to merge data even from a “bricked” device).
But even if the phone does not have a service “back door”, data from the device can still be obtained by disassembling the device and connecting to the JTAG test port. In the most advanced cases, the eMMC chip is removed from the device, which is inserted into a simple and very cheap adapter and operates using the same protocol as the most common SD card. If the data was not encrypted, everything can be easily extracted from the phone, down to the authentication tokens that provide access to your cloud storage.
What if encryption was enabled? In older versions of Android (up to 4.4 inclusive), this could be bypassed (with the exception, however, of devices manufactured by Samsung). But in Android 5.0, a strong encryption mode finally appeared. But is it as useful as Google thinks it is? Let's try to figure it out.
Android 5.0–6.0
The first device running Android 5.0 was the Google Nexus 6, released in 2014 by Motorola. At that time, 64-bit mobile processors with the ARMv8 architecture were already actively promoted, but Qualcomm did not have a ready-made solution on this platform. As a result, the Nexus 6 used the Snapdragon 805 chipset, based on Qualcomm's own 32-bit cores.
Why is it important? The fact is that processors based on the ARMv8 architecture have a built-in set of commands to speed up stream data encryption, but 32-bit ARMv7 processors do not have such commands.
So watch your hands. There are no instructions for accelerating crypto in the processor, so Qualcomm has built a dedicated hardware module into the system logic set to perform the same functions. But something didn’t work out for Google. Either the drivers were not completed at the time of release, or Qualcomm did not provide the source codes (or did not allow them to be published in AOSP). The details are unknown to the public, but the result is known: the Nexus 6 shocked reviewers with its extremely slow data read speed. How slow? Something like this:
The reason for the eight-fold lag behind its “younger brother”, the Motorola Moto X 2014 smartphone, is simple: forcibly enabled encryption, implemented by the company at the software level. In real life, Nexus 6 users on the original firmware version complained about numerous lags and freezes, noticeable heating of the device and relatively poor battery life. Installing a kernel that disables forced encryption immediately solved these problems.
However, firmware is such a thing, you can finish it, right? Especially if you are Google, have unlimited finances and have the most qualified developers on your staff. Well, let's see what happened next.
And then there was Android 5.1 (six months later), in which the necessary drivers for working with the hardware accelerator were first added in the preliminary version of the firmware, and then removed again in the final version due to serious problems with sleep mode. Then there was Android 6.0, at the time of its release users had already lost interest in this game and began to disable encryption by any means, using third-party kernels. Or don’t disable it if a read speed of 25–30 MB/s is enough.
Android 7.0
Okay, but could Android 7 fix a serious problem with a flagship device that is almost two years old? It’s possible, and it’s been fixed! The ElcomSoft lab compared the performance of two identical Nexus 6s, one running Android 6.0.1 with the ElementalX kernel (and encryption disabled), while the other was running the first preview version of Android 7 with default settings ( encryption enabled). The result is clear:
Data encryption in the Android OS is closely related to two problems: controlling access to memory cards and transferring applications to them. Many programs contain activation data, payment and...
The FBI tried through court to twist the hands of Apple, which did not want to create code to bypass its own security system. A critical vulnerability has been discovered in the Android kernel, allowing superuser access to bypass all security mechanisms. These two events, although unrelated, coincided in time, clearly demonstrating the differences in the security systems of the two popular mobile operating systems. Let's put aside for a moment the issue of a critical vulnerability in the Android kernel, which is unlikely to ever be fixed by most manufacturers in already released models, and consider the data encryption mechanisms in Android and Apple iOS. But first, let’s talk about why encryption is needed in mobile devices at all.
Why encrypt your phone?
An honest person has nothing to hide - the most popular leitmotif that sounds after every publication on the topic of data protection. “I have nothing to hide,” many users say. Alas, much more often this only means the confidence that no one will bother to get into the data of a particular Vasya Pupkin, because who is interested in them at all? Practice shows that this is not so. We won’t go far: just last week, the career of a school teacher who left her phone on the table for a moment ended with her dismissal. The students instantly unlocked the device and took out photographs of the teacher in a form that is condemned by the puritanical morality of American society. The incident served as sufficient grounds for the teacher's dismissal. Stories like this happen almost every day.
How unencrypted phones are hacked
We won't go into detail, just keep in mind: data from an unencrypted phone can be recovered in almost a hundred percent of cases. “Almost” here refers rather to cases where the phone was attempted to be physically damaged or destroyed immediately before the data was removed. Many Android and Windows Phone devices have a service mode that allows you to drain all data from the device’s memory via a regular USB cable. This applies to most devices on the Qualcomm platform (HS-USB mode, which works even when the bootloader is locked), on Chinese smartphones with MediaTek (MTK), Spreadtrum and Allwinner processors (if the bootloader is unlocked), as well as all smartphones manufactured by LG (there in general a convenient service mode that allows you to merge data even from a “bricked” device).
But even if the phone does not have a service “back door”, data from the device can still be obtained by disassembling the device and connecting to the JTAG test port. In the most advanced cases, the eMMC chip is removed from the device, which is inserted into a simple and very cheap adapter and operates using the same protocol as the most common SD card. If the data was not encrypted, everything can be easily extracted from the phone, down to the authentication tokens that provide access to your cloud storage.
What if encryption was enabled? In older versions of Android (up to 4.4 inclusive), this could be bypassed (with the exception, however, of devices manufactured by Samsung). But in Android 5.0, a strong encryption mode finally appeared. But is it as useful as Google thinks it is? Let's try to figure it out.
Android 5.0–6.0
The first device running Android 5.0 was the Google Nexus 6, released in 2014 by Motorola. At that time, 64-bit mobile processors with the ARMv8 architecture were already actively promoted, but Qualcomm did not have a ready-made solution on this platform. As a result, the Nexus 6 used the Snapdragon 805 chipset, based on Qualcomm's own 32-bit cores.
Why is it important? The fact is that processors based on the ARMv8 architecture have a built-in set of commands to speed up stream data encryption, but 32-bit ARMv7 processors do not have such commands.
So watch your hands. There are no instructions for accelerating crypto in the processor, so Qualcomm has built a dedicated hardware module into the system logic set to perform the same functions. But something didn’t work out for Google. Either the drivers were not completed at the time of release, or Qualcomm did not provide the source codes (or did not allow them to be published in AOSP). The details are unknown to the public, but the result is known: the Nexus 6 shocked reviewers with its extremely slow data read speed. How slow? Something like this:
The reason for the eight-fold lag behind its “younger brother”, the Motorola Moto X 2014 smartphone, is simple: forcibly enabled encryption, implemented by the company at the software level. In real life, Nexus 6 users on the original firmware version complained about numerous lags and freezes, noticeable heating of the device and relatively poor battery life. Installing a kernel that disables forced encryption immediately solved these problems.
However, firmware is such a thing, you can finish it, right? Especially if you are Google, have unlimited finances and have the most qualified developers on your staff. Well, let's see what happened next.
And then there was Android 5.1 (six months later), in which the necessary drivers for working with the hardware accelerator were first added in the preliminary version of the firmware, and then removed again in the final version due to serious problems with sleep mode. Then there was Android 6.0, at the time of its release users had already lost interest in this game and began to disable encryption by any means, using third-party kernels. Or don’t disable it if a read speed of 25–30 MB/s is enough.
Android 7.0
Okay, but could Android 7 fix a serious problem with a flagship device that is almost two years old? It’s possible, and it’s been fixed! The ElcomSoft lab compared the performance of two identical Nexus 6s, one running Android 6.0.1 with the ElementalX kernel (and encryption disabled), while the other was running the first preview version of Android 7 with default settings ( encryption enabled). The result is clear:
Continuation is available only to members
Option 1. Join the “site” community to read all materials on the site
Membership in the community within the specified period will give you access to ALL Hacker materials, increase your personal cumulative discount and allow you to accumulate a professional Xakep Score rating!







