How to use telnet on the command line. What is Telnet. Telnet remote control
Few computer users today know about the existence of various special protocols on the computer that allow them to perform various actions without using a graphical interface or third-party programs. Therefore, the desire to learn how to use the TELNET service immediately arises when they learn about the corresponding protocol.
Next, we will outline a little theory about what TELNET is, what many people strive to master it for: the capabilities of the service, as well as a list of basic commands that allow these capabilities to be implemented on Windows.
TELNET is a communication tool that establishes a transport connection between terminal devices, clients, that is, your computer and someone else’s machine, a server that supports this connection standard. This is not a special program, but just a network protocol, but the word TELNET (terminal network) also refers to various utilities that also use this protocol. Today Telnet is present almost everywhere, all operating systems, one way or another, use it, in
TELNET implements a text interface, which differs from the graphical interface familiar to the average user in that all commands must be entered manually.
What does all this give us?
Previously, this service was one of the few ways to connect to the network, but over time it has lost its relevance. Today there are much more convenient programs that do all the work for the user, and do not force him to memorize various commands in order to perform the simplest actions. However, some things can still be done using Telnet.

Network connections
With Telnet you can:
- connect to remote computers;
- check the port for access;
- use applications that are only available on remote machines;
- use various directories that can only be accessed in this way;
- send emails without using special programs (clients);
- understand the essence of the work of many protocols used today and derive certain benefits from this;
- provide other users with access to data located on their computer.
Let's start using it
Launch
Launching TELNET on Windows 7 and any other Windows is quite simple. To do this, you first need the client, if it is not already installed:
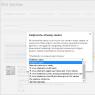
- Go to the Control Panel.

- Select “Programs”.
- Select the “Turn Windows features on or off” tab.

- Find the Telnet client and put a marker next to it if it is not already installed.
Then click “OK” and wait a minute while the client is installed.
The terminal is launched in Windows via the command line, if you do not have any special utilities installed for working with Telnet. But since you are reading this article, it means that you are just starting to get acquainted with this topic, and first it would be nice to master the basics of management using the command line.
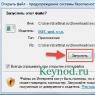
- Launch the command line as administrator.
- Enter "telnet".
The command line will reboot, and the TELNET command line will now open, in which we will work.
Checking the port
One of the simplest actions performed in TELNET is port checking. You can check the port to see if it can be accessed from your computer. To do this you need to do the following:
In the command line opened using the method above, enter: telnetip address port number

For example, if your IP address is 192.168.0.1 and the port number is 21 (FTP port), then enter:
telnet 192.168.0.1 21
If the command produces an error message, it means the port is unavailable. If a blank window appears or a request to enter additional data, then the port is open. For Windows, this method of checking the port can be quite convenient.
Teams
TELNET commands are the basis for using the terminal. With their help, you can control a computer that uses this protocol, if access is allowed for you, as well as perform various other actions. As mentioned above, on Windows they are entered in the command line of the Telnet application.
To see the main list of commands, enter in the line help and press "Enter". Basic commands:
- Open- connection to a remote server. You must enter this command along with the managed server name and port number, for example: openredmond 44. If parameters are not specified, the default local server and port are used.
- Close- disconnect from a remote server. Similar parameters are used.
- Set- setting up a remote server, used with the name of the managed server. Together with Set The following commands are used:
- - used to specify a terminal of the specified type.
- - sets the control character.
- - sets the operating mode.
- Unset [option]- disables a previously specified parameter.
- Start- starts the Telnet server.
- Pause- pauses the server.
- Continue- resumes work.
- Stop- stops the server.
TELNET is one of the oldest protocols, but it is still used today. This means that you can start using it for your own purposes. To do this, you just need to learn the syntax and list of commands and start practicing. You can learn a lot of new things, and at the same time begin to look at the Internet and your previously familiar online activities in a completely different way.
Progress is a phenomenon that knows no stops. In the field of information technology, changes occur every day: new products appear, obsolete services become a thing of the past. But there are tools that are still popular despite the emergence of an alternative. A prime example is the Telnet protocol. What is Telnet and how to use it?
A little history: when and why did Telnet appear?
Telnet appeared more than 40 years ago, shortly after the installation of the first ARPANET server. This is one of the oldest protocols on the Internet. In an era when there was no trace of it, but the first networks had already appeared, the need for remote connection to devices dictated its requirements. The first solution to the problem that appeared, like all subsequent ones, allowed you to work on a remote device as if it were your own. All supported functionality has become available in the interface. You just need to get the required access level and know the Telnet commands. We figured out what this protocol is and why we need it. But how is Telnet connection implemented today?
Launch the terminal. Enable required services
In modern operating systems of the Windows family, before starting Telnet, you need to check whether this component is installed on the system. This is not difficult to do. For Windows 7, the most common operating system today, you need to perform the following sequence of actions:
- Select "Control Panel" or Control Panel from the Start menu.
- In the window that opens, select “Programs”. In the English version of the system this will be Programs.
- Go to the “Turn Windows features on or off” tab. The system generates a list of all available components. Already installed ones will be marked with checkboxes. This process may take several minutes.
- After the list is loaded, you need to find the Telnet client item. There is also a Telnet server in the menu, but we will return to this a little later. If there is no checkmark next to the item we need, it needs to be checked.
- After clicking the "OK" button, the system will begin to install the necessary components for the correct operation of the protocol. This may take some time, but on modern computers the process is unlikely to take more than a minute. Thus, the question of how to enable Telnet was resolved in 5 simple steps.

Telnet service: and Telnet client?
Both concepts from the title have already been mentioned a little higher. Like many other applications, Telnet has a client side and a server side. However, a Telnet server is not necessarily a server in the general sense of the word. The computer from which the connection is made is considered to be a client, the device to which this connection is made will be the server. This could be a router, a computer, or any other host that supports command line control. If we are talking about remote administration of a personal user computer or server, the Telnet port must be open. It is often closed for security reasons, so when you try to establish a session, an error message will appear. To check open and closed ports, you can use a special utility or web service. The standard Telnet port is 23. If you want to not only connect to other computers yourself, but also allow administration of your PC via Telnet, then in the same operating system snap-in you need to check the box next to the Telnet server component. The PCs and server hardware that you administer should be configured in the same way.

Programs for working with Telnet
After starting all the necessary Telnet services, you can safely start working using the built-in Windows tool - the command line. It is called up from the Start menu, either by clicking on the corresponding item, or by speed dialing (cmd). It is advisable to always run the command line with “Administrator” user rights (either local, the device on which you are working, or domain). This way, you won't have to restart the application if elevation is required. In addition to the existing tool of the operating system itself, there are also third-party programs that allow access via the Telnet protocol. The most popular of them is Putty. Along with it, other applications running under different operating systems are also popular, such as TeraTerm, AnyConnect, DTelnet, EasyTerm, KoalaTerm and many others. Which program to use, everyone decides for themselves, depending on personal preferences, interface requirements, etc. There are no significant differences in terms of functionality between them, and there cannot be. Each utility implements the entire available list of Telnet commands.

Telnet commands: how to figure it out?
For an experienced user, it will not be difficult to install the necessary components in a matter of minutes (if they have not been installed previously), open a Telnet session and perform all the configuration of the remote host. However, there are also newcomers who see the console almost for the first time in their lives. How to find out the list of available commands in Telnet? What is WONT AUTH or SET LOCALECHO? Everything is not as difficult as it seems at first. Firstly, you should always remember that any command interface has built-in help. It can be accessed using standard keys, for example, help or “?”. Secondly, given how old it is, there are endless resources on the web with useful syntax information. Thus, there is absolutely nothing to worry about. And practice shows that using several lines of commands the result is much easier to achieve in most cases. And after just a few sessions, you will confidently type the necessary commands without resorting to the syntax assistant.

Telnet on network devices
We have already said that using the Telnet protocol you can manage not only computers, but also a wide variety of network devices. The most common class of such devices is routers. So what is Telnet in a router, what is it for, how to enable it?
Depending on the manufacturer and specific model, you can enable Telnet access in different ways. You can log into the router via the web interface or through the console. In the first case, you will need to find a remote administration point where one or another type of connection is allowed (Telnet, ssh). In the second case, access can be granted via the command line. Each administrator chooses a scenario that is convenient for themselves. However, there are routers that implement only one of two possible initial connection options, for example, only a web interface is available. An administrator who is accustomed to working with the console will find it rather uncomfortable to look for the item where he needs to put the coveted checkbox, but in reality there is nothing complicated about it. The interface of most modern routers is quite clear. The names of the menu items speak for themselves; the minimalist design will not allow you to get confused.

Advantages of Telnet sessions
At this point, we've become familiar enough with the technology to talk about the pros and cons of Telnet. No matter how successful the product is, it cannot be said that it is absolutely devoid of disadvantages. And if we are talking about a service that was released at the very beginning of the 70s of the last century, you should not forget about this fact.
Among the obvious advantages, it is necessary to note the simplicity, speed and convenience of the protocol. In less than a minute, a convenient client will contact the server TCP port of your choice and create a local terminal emulation. Above we talked about the standard 23 working port. In fact, you can “listen” and “talk” via Telnet on any port. This is where the flexibility of the protocol lies.
Compared to other remote administration protocols, Telnet is less processor intensive. With the current pace of development, this plus may seem insignificant, but only at first glance. Along with the development of technology, companies producing software do not stand still. Applications are becoming more and more bulky, requiring more and more hard drive space, more RAM, and more powerful processors. A utility that, compared to other installed software, will consume a small amount of system resources will come in handy.
Disadvantages of the Telnet protocol
The main and often cited disadvantage of Telnet is that access to a remote device is carried out over an unencrypted communication channel. The only barrier for an attacker is user authentication at the time of opening a Telnet session, that is, the requirement for a login and password. However, this data is also transmitted unencrypted. Therefore, if someone sets out to hack Telnet access, he only needs to briefly run a packet sniffer (software for “catching” packets). After some time, the administrator will open his Telnet session and provide the remote server with a login and password, which will be immediately intercepted by the attacker in clear text. In this context, an alternative to Telnet is SSH (secure connection). Therefore, it is not recommended to use Telnet on widely available networks, such as outside your secure office LAN. In addition, you should remember that the connection to the server may be interrupted.

Conclusion. To use or not?
Of course, other methods of remote administration have emerged over more than four decades. SSH is very popular. It would seem that Telnet should have disappeared a long time ago. But it is still in demand and is still used. If you follow certain security principles, remembering that your local network must be reliably protected from outside penetration, using Telnet will not cause harm to your equipment. If you neglect security, neither SSH nor any other technology will save you.
Telnet is still used in areas such as connecting to databases, checking the availability of network devices (routers and switches), server equipment, etc.
The Telnet protocol is a standard for data exchange between two network devices, designed to implement remote control. Not everyone knows that setting up a Wi-Fi router can be done via Telnet from any computer on the local network. To do this, it is necessary that the Telnet access option is enabled in the router, and it must be enabled via the web interface.
An interesting fact is that sometimes you can log into the router using Telnet, while access via HTTP, that is, through the graphical interface, remains unavailable.
Condition for being able to connect to the router
If you want to go to the router management interface, you first need to find out what the IP address of this device is. Without an IP address, you won’t even be able to open a Telnet session, let alone access it through a browser. Most network harvesters are assigned the following address by default: 192.168.1.1. For D-Link, you need to make a correction in the last two digits (should be “0.1”). Configure your PC's network card to the appropriate values by changing the last digit of its IP.
Setting up a connection on a computer
How to open a communication session
Every operating system has a command line. Once you launch it, just run one command: telnet 192.168.1.1. After which the router, connected to the PC via Ethernet or Wi-Fi, immediately responds to us, asking for a login and password.

Starting a communication session
In our response we used the name “admin” and password “1234”, that is, the default values in ZyXEL devices. As you can see, these values were accepted and the “config” prompt appeared.
Some ZyXEL models use not only a text interface, but also a command list (menu):

Start list view
To return to text command mode, go to 28 -> 4 (use step 28 and then step 4). As a result, you will receive the inscription “config” and a cursor for entering commands. In what follows, we will consider only this mode.
Configuring the device via Telnet
The text command interface, that is, the command line of routers and other ZyXEL devices, is called the word “CLI” (Command Line Interpreter). Most of the commands for all models are the same, for example, “system reboot” (reboot), “system config-save” (save settings), and others. Some commands for a particular model may differ, and you can download a detailed manual on the support website, where they provide proprietary firmware for download.

Download the directory with commands
Devices from companies other than ZyXEL provide a “help” command, which gives you a list of available commands.
Remote access to the web interface
The WAN port of the network harvester is assigned an IP address. The value of this address usually does not change, even if dynamic addresses are used. Knowing his IP address, the user can open the device management interface from any computer with an Internet connection. By default, this access method is prohibited in ZyXEL routers. And the command line will help you get rid of this limitation.
Type the following command: ip static tcp ISP 80 192.168.1.1 80 // port “80” is used by the web interface.
The “ip static” command actually creates a binding of local addresses to global IP addresses. Note that if you are using a type of connection where authorization is provided (PPTP, L2TP or PPPoE), then instead of the word “ISP” you must substitute another name. It’s easy to find out: Interface ?// all network interfaces will be displayed.
For the PPPoE protocol, the Internet connection interface is usually named “PPPoE0” (case is important). Don't forget to save the settings (system config-save). As a result, it will be possible to open the web interface from the Internet.

The interface opened from the “external”
Some providers block port 80, so it probably won’t work the first time. But you can do it more cunningly by redirecting external port number 8080 to internal port 80: ip static tcp ISP 8080 192.168.1.1 80 // this way we bypass the provider’s restrictions.
In general, the port for Telnet is forwarded in a similar way (its number is “23”).
A sea of commands for Wi-Fi
The easiest way to start mastering the command line is to use those commands that are responsible for the parameters of the access point (Wi-Fi network). Each of these commands begins with the word “interface”, and then there is a qualifying sequence. The simplest option: interface ssid SYSDAY// the wireless network name will be set to “SYSDAY”.
Note that by specifying the “auto” parameter instead of the name, you can return the “access point” to the SSID value that was set at the factory.
There are several more interesting commands that control the radio module. To avoid typing the word “interface” every time, use it as a separate command (the prompt is transformed into “config-if”). We provide a list of commands used in the “config-if” mode below.

Example commands for Wi-Fi
- power number // instead of the word “number”, set the power as a percentage;
- channel number // instead of “number”, specify the radio channel number (1-13);
- country-code country // the “country” parameter contains 2 letters, for example, RU;
- hide-ssid // hide network name;
- no hide-ssid // open network name.
And this is not a complete list of parameters that can be changed directly from the command line.
It should be noted that using Telnet you can change or enable the Wi-Fi encryption algorithm (WPA or WPA2).
And the key value is set by the “interface authentication wpa-psk” command. Thus, it becomes possible to log into the router remotely, from anywhere in the world, via Telnet and change the password for the wireless network. Very useful, isn't it?
Telnet to the router-modem
Telnet Commands
Teams telnet allow you to communicate with a remote computer using the Telnet protocol. You can run the command telnet without parameters to enter the telnet context indicated on the Telnet command line ( telnet). From the Telnet command line, use the following commands to control the computer running the Telnet client.
Teams tlntadmn allow you to remotely control a computer running a Telnet server. These commands are executed from the command line. Team tlntadmn without parameters displays the local server setting.
To use commands telnet from the Telnet command line
To launch the Telnet client and enter the Telnet command line
Syntax
telnet [\\ remote server]
Options
\\ remote server Displays the name of the connected server /? Displays help on the command line.Notes
- When using the command telnet The Telnet client starts without parameters.
- At the Telnet command line, you must use Telnet commands.
To stop the Telnet client
Syntax
Options
none
Notes
- q.
To connect a Telnet client to a remote computer
Syntax
open [\\ remote server] [port]
Options
\\ remote server Specifies the name of the managed server. If no server is specified, the local server is used. port Indicates the port to use. If no port is specified, the default port is used.Notes
- This command can be shortened to o.
Examples
To connect to the remote Redmond server on port 44, enter at the command prompt:
redmond 44
To disconnect the Telnet client from a remote computer
Syntax
close [\\ remote server]
Options
\\ remote server Specifies the name of the managed server. If no server is specified, the local server is used.Notes
- This command can be shortened to c.
Examples
To disconnect from the remote Redmond server, enter the command:
redmond 44
To configure Telnet client settings
Syntax
set [\\ remote server] [ntlm] [localecho] [term {ansi | vt100 | vt52 | vtnt}] [escape symbol] [logfile file name] [logging] [bsasdel] [crlf] [delasbs] [mode {console | stream}] [? ]
Options
\\ remote server Specifies the name of the managed server. If no server is specified, the local server is used. ntlm Enables NTML authentication, if available on the remote server. localecho Enables local display of commands. term {ansi | vt100 | vt52 | vtnt) Specifies a terminal of the specified type. escape symbol Specifies the control character. The control character can be a single character or a combination of the CTRL key and a character. To set a key combination, hold down the CTRL key while typing the character you want to assign. logfile file name Specifies the Telnet activity log file. The log file must be located on your local computer. Logging starts automatically after selecting this option. logging Enables logging. If a log file is not specified, an error message is displayed. bsasdel Specifies the BACKSPACE key to delete. crlf Assigns a new linear mode that defines the ENTER key as 0x0D, 0x0A. delasbs Assigns the DELETE key to delete the last character. mode {console | stream) Sets the operating mode. ? Allows you to view the full command syntax.Notes
- To disable a previously assigned setting, at the Telnet command prompt, enter:
unset [parameter]
- To assign a control character, enter the command:
e symbol
- In non-English versions of Telnet, the command is available codesetparameter. Codeset parameter specifies the current code set for the parameter, which can be one of the following: Shift JIS, Japanese EUC, JIS Kanji,JIS Kanji (78), DEC Kanji, NEC Kanji. You must assign the same code set on the remote computer.
To send Telnet client commands
Syntax
send [\\ remote server] [ao] [ayt] [esc] [ip] [synch] [ ? ]
Options
\\ remote server The name of the server that you want to manage. If no server is specified, the local server is used. ao Cancels an input command. ayt Sends the command “Are you there?” esc Sends the current control character. ip Interrupts execution of a processing command. synch Performs a Telnet synchronization operation. ? Allows you to view the full command syntax.To view the current Telnet client settings
Syntax
displayOptions
none
Notes
- This command displays the current operating parameters for the Telnet client. When operating in Telnet session mode (in other words, while connected to a Telnet server), you can exit the session to change settings by pressing CTRL+]. To return to the Telnet session, press ENTER.
To use tlntadmn commands from the command line
To administer a computer running Telnet Server
Syntax
tlntadmn [\\ remote server] [start] [stop] [pause] [continue]
Options
\\ remote server start Starts the Telnet server. stop Stops the Telnet server. pause Interrupts the Telnet server. continue Resumes the Telnet server. /? Displays help on the command line.Notes
- Using commands tlntadmn tlntadmn
To administer Telnet sessions
Syntax
tlntadmn [\\ remote server] [-s] [-k{session_code | all}] [-m {session_code | all} " message" ]
Options
\\ remote server Specifies the name of the server that you want to take control of. If no server is specified, the local server is used. -s Displays active Telnet sessions. -k{session_code | all) Ends sessions. Enter a session code to end a specific session or enter all to end all sessions. -m {session_code | all} " message" Sends a message to one or more sessions. Enter a session code to send a message to a specific session, or enter all to send a message to all sessions. Type the message you want to send in quotes (i.e. " message" ). /? Displays help on the command line.Notes
- Using commands tlntadmn You can remotely administer a computer running Telnet Server if both computers are running Windows XP. Teams tlntadmn cannot be used to remotely administer a Telnet server running Windows 2000 from a computer running Windows XP.
To set event logging settings for the computer running Telnet Server
Syntax
tlntadmn [\\ remote_computer] config [auditlocation={eventlog | file | both}] [audit=[{+ | - } admin][{+ | - } user][{+ | - } fail]]
Options
\\ remote server Specifies the name of the server that you want to take control of. If no server is specified, the local server is used. auditlocation={eventlog | file | both) Specifies whether event information should be sent to the Event Viewer, to a file, or to both. audit=[{+ | - } admin][{+ | - } user][{+ | - } fail] Specifies which events require auditing (administrator logon events, user logon events, or failed logon attempts). To audit a specific event type, enter a plus sign (+) in front of the event type. To stop auditing of a specific event type, enter a minus sign (-) in front of the event type. /? Displays help on the command line.Notes
- Using commands tlntadmn You can remotely administer a computer running Telnet Server if both computers are running Windows XP. Teams tlntadmn cannot be used to remotely administer a Telnet server running Windows 2000 from a computer running Windows XP.
- If you specify where to send event information without specifying the information type or types to be audited, only administrator log event information will be audited and sent to the specified location.
Examples
To send event information to the Event Viewer, enter:
tlntadmn config auditlocation=eventlog
To audit administrator logon events and failed logon attempts, enter:
tlntadmn config audit=+admin +fail
To set the primary domain for the computer running Telnet Server
Syntax
tlntadmn [\\ remote server] config [dom=domain name]
Options
\\ remote server Specifies the name of the server that you want to take control of. If no server is specified, the local server is used. dom=domain name Specifies the domain that you want to make primary. /? Displays help on the command line.Notes
- Using commands tlntadmn You can remotely administer a computer running Telnet Server if both computers are running Windows XP. Teams tlntadmn cannot be used to remotely administer a Telnet server running Windows 2000 from a computer running Windows XP.
Examples
To make the Redmond domain the primary domain on your local server, enter:
tlntadmn config dom=Redmond
To map the ALT key to the computer running the Telnet server
Syntax
tlntadmn [\\ remote server] config [ctrlakeymap={yes | no}]
Options
\\ remote server Specifies the name of the server that you want to take control of. If no server is specified, the local server is used. ctrlakeymap={yes | no) Indicates whether the Telnet server should interpret the CTRL+A key combination as ALT. Enter yes to map a keyboard shortcut or no to refuse matching. /? Displays help on the command line.Notes
- Using commands tlntadmn You can remotely administer a computer running Telnet Server if both computers are running Windows XP. Teams tlntadmn cannot be used to remotely administer a Telnet server running Windows 2000 from a computer running Windows XP.
- If the ALT key is not mapped, the Telnet server does not send the ALT keystroke to applications where it might be needed.
To set the maximum number of connections for the computer running Telnet Server
Syntax
tlntadmn [\\ remote server] config [maxconn=positive_integer]
Options
\\ remote server Specifies the name of the server that you want to take control of. If no server is specified, the local server is used. maxconn=positive_integer Sets the maximum number of connections. This number can be specified using any positive integer less than 10 million. /? Displays help on the command line.Notes
- Using commands tlntadmn You can remotely administer a computer running Telnet Server if both computers are running Windows XP. Teams tlntadmn cannot be used to remotely administer a Telnet server running Windows 2000 from a computer running Windows XP.
To set the maximum number of failed access attempts for the computer running the Telnet server
Syntax
tlntadmn [\\ remote_computer] config [maxfail=positive_integer]
Options
\\ remote server Specifies the name of the server that you want to take control of. If no server is specified, the local server is used. maxfail=positive_integer Sets the maximum number of failed login attempts allowed for a user. This number can be specified using any positive integer less than 100. /? Displays help on the command line.Notes
- Using commands tlntadmn You can remotely administer a computer running Telnet Server if both computers are running Windows XP. Teams tlntadmn cannot be used to remotely administer a Telnet server running Windows 2000 from a computer running Windows XP.
To set the operating mode for the computer running the Telnet server
Syntax
tlntadmn [\\ remote server] config [mode={console | stream}]
Options
\\ remote server Specifies the name of the server that you want to take control of. If no server is specified, the local server is used. mode {console | stream) Indicates the operating mode. /? Displays help on the command line.Notes
- Using commands tlntadmn You can remotely administer a computer running Telnet Server if both computers are running Windows XP. Teams tlntadmn cannot be used to remotely administer a Telnet server running Windows 2000 from a computer running Windows XP.
To set the Telnet port for the computer running the Telnet server
Syntax
tlntadmn [\\ remote server] config [port=integer_value]
Options
\\ remote server Specifies the name of the server that you want to take control of. If no server is specified, the local server is used. port=integer_value Specifies the Telnet port. The port can be specified using any integer less than 1024. /? Displays help on the command line.Notes
- Using commands tlntadmn You can remotely administer a computer running Telnet Server if both computers are running Windows XP. Teams tlntadmn cannot be used to remotely administer a Telnet server running Windows 2000 from a computer running Windows XP.
To set authentication methods for the computer running the Telnet server
Syntax
tlntadmn [\\ remote server] config [sec=[{+ | - } ntlm][{+ | - } passwd]]
Options
\\ remote server Specifies the name of the server that you want to take control of. If no server is specified, the local server is used. sec=[{+ | - } ntlm][{+ | - } passwd] Specifies whether NTML or password authentication is used, or both, to authenticate login attempts. To use a specific authentication type, enter a plus sign (+) in front of that authentication type. To prevent a specific type of authentication from being used, enter a minus sign (-) in front of that type. /? Displays help on the command line.Notes
- Using commands tlntadmn You can remotely administer a computer running Telnet Server if both computers are running Windows XP. Teams tlntadmn cannot be used to remotely administer a Telnet server running Windows 2000 from a computer running Windows XP.
- NTML is an authentication protocol for transactions between two computers, one or both of which are running Windows NT 4.0 and earlier. Additionally, the NTML authentication protocol is used for computers that are not part of a domain, such as independent servers and workgroups.
To set the idle session timeout for the computer running the Telnet server
Syntax
tlntadmn [\\ remote server] config [timeout=hh: mm: ss]
Options
\\ remote server Specifies the name of the server that you want to take control of. If no server is specified, the local server is used. timeout=hh: mm: ss Sets the elapsed time value in hours, minutes, and seconds. /? Displays help on the command line.Notes
- Using commands tlntadmn You can remotely administer a computer running Telnet Server if both computers are running Windows XP. Teams tlntadmn cannot be used to remotely administer a Telnet server running Windows 2000 from a computer running Windows XP.
Notes
- To switch from the Telnet client to command mode, at the Telnet command prompt, press CTRL+]. To return to the Telnet client, press ENTER.
Using the telnet command makes it possible to establish a communication channel with computers at a distance.
And the utility itself is almost a kind of browser emulator in the terminal, supporting several network protocols.
In the past, telnet was often used to manage PCs running the Linux operating system.
And now, using the same utility, they test the network, check ports, manage routers and other IoT devices.
Content:Features of the utility
Despite the fact that the main task of telnet is to create a connection between PCs remote from each other using the protocol of the same name, you can also manage other services using the utility.
For example, access POP3, HTTP, IRC or SMTP.
After all, these and some other services operate on the basis of the TCP transport protocol, to work with which you can use the telnet client.
The syntax of telnet commands when connecting to a remote computer is as follows: $ telnet (options) (host) (port).
The host is the domain of the computer to which the connection is made. Port – port on the computer from which access is being made. And the options could be as follows:
- -4 and -6 enforce the use of ipv4 and ipv6 addresses, respectively;
- -8 makes it possible to use 8-bit encoding;
- -E disables support for escape sequences;
- -a automatically registers the user on the remote system;
- -d enables debugging mode;
- -p enables rlogin emulation;
- -e sets the initial escape character;
- -l authorizes the user in the system.
After a connection to the remote host is established, the telnet utility begins working in one of two modes - line by line or character by character.
The first option is the most preferable due to the ability to edit the text directly and send it only after the user has completely typed in all the information.
The disadvantage of this line-by-line mode is the lack of support for it by some services. While character-by-character can be used in any case.
However, when using it, all information is sent instantly.
And if the user makes a mistake, it will be impossible to correct it - after all, even spaces and Backspace are sent to the server in the form of characters.
You should know: When using the telnet protocol, there is no possibility of encrypting information transfer. All data is sent directly and can be intercepted by an unauthorized user. And it is not recommended to transmit them in this way - it is advisable to use the secure Secure Shell network protocol for this.
Basic commands
When working with the telnet protocol, the user enters the appropriate commands into the console. The most popular include the following:
- OPEN (PC name) (port). Allows you to communicate with the computer whose name is specified in the command. If you do not specify a port, the utility will try to use the default number. Sometimes it is indicated instead of the PC name;
- DISPLAY (argument).
- Command to display a full or partial set of telnet utility parameters;
- CLOSE.

Designed to close the telnet session and return the system to command mode;
- QUIT.
- Command to end all open connections and exit telnet;
- Rice. 2. Using the Quit command in the MS Telnet client.
- MODE TYPE.
- Used to control one of two input mode options (character-by-character or line-by-line). In this case, a request is sent to the remote computer to switch to a certain mode, and, if it is supported by the service, the corresponding switching is provided;
- STATUS.
- A command that displays the current utility status, name and exchange mode;
- ? (team). Reports information about the corresponding command sequence. It is needed in cases where the user is going to use a command that is unfamiliar to him;
! (team). Executes a command sequence on the local system;
SEND ARGUMENTS.
Although, for example, for a telnet client on Windows, the list may be shortened.