How to set up Apple ID two-factor authentication on iPhone, iPad and Mac. Apple two-factor authentication: features, principle of protection, disabling
User. Moreover, we are talking not only about the account, saved contacts and messages, but also about personal documents and files. The highest level of data protection is guaranteed by Apple's two-factor authentication, when to access personal data you need to enter two special numeric codes in a row.
How it works
The main feature of Apple's new security system is to ensure that only you can log into your device, even if the password is known to others. With two-step verification, you can only sign in to your account from a trusted iPhone, iPad, or Mac. In this case, two-factor authentication will require you to sequentially enter two types of passwords: a regular one and a six-digit verification code, which will automatically be displayed on the verified gadget.
For example, let's say you have a Mac laptop and want to sign in to your account on your recently purchased iPad. To do this, you first enter your username and password, and then a verification code that automatically appears on the screen of your laptop.
After this, Apple's two-factor authentication will “remember” your device and allow access to personal data without additional verification. You can also make the browser of any PC trusted by setting this option when logging into your account for the first time.
Trusted devices
You can only make a gadget trusted by Apple. Moreover, the operating system installed on it must be no lower than iOS 9 for mobile devices and no lower than OS X El Capitan for laptops and personal computers. “Two-factor authentication” explains this by saying that only in this case can Apple guarantee that the laptop you are using belongs to you.
Six-digit verification codes can be sent not only to trusted devices, but also to mobile device numbers. At the same time, the method of confirming the number and gadget is no different. It is also worth remembering that in any case, no matter what method you use to obtain a verification code, two-factor authentication will require you to know your own Apple ID. Learn it by heart, otherwise you risk not being able to access your account.
New level of protection
Each time you sign in to your user account, your location is sent to trusted devices. In cases where it coincides with your actual location, you can allow entry by pressing the highlighted button.

If two-factor authentication offers to allow login on another device, although the current location of the device does not coincide with yours, then you should prohibit this action. This indicates unauthorized access to your gadget, and can also serve as a signal about the location of the attacker who stole your phone.
Disabling two-factor protection
It is strongly recommended not to perform any manipulations with the device that could disable Apple's two-factor authentication; this will reduce the level of security of your gadget. However, in some cases it is simply not required. For example, you constantly use both a laptop and a smartphone. There is no need to confirm your identity and, moreover, the procedure is very tiring.

There are two ways to disable Apple's two-factor authentication. In the first case, you need to log into your account, select the “Edit” menu and select the appropriate option in the “Security” menu item. By confirming your date of birth and answering the security questions, you will turn off two-factor protection.
Disable email authentication
If you discover that two-step protection is activated on your device without your knowledge, you can disable it remotely using the email you provided at the time of registration or a backup address. How to disable two-factor authentication using email?
To do this, you need to open the letter that will arrive in your mailbox immediately after activating the protection system. At the bottom of the message you will see the treasured “Turn off...” item. Click on it once, and the previous settings for protecting your personal data will be restored.

You must follow the link within two weeks of receiving the message, otherwise it will become invalid. Now you won't have to wonder how to disable two-factor authentication, and you know a few more Apple secrets.
Two-factor authentication on Instagram is a method that can be used to further protect your social network profile from hacking attempts.
Two-factor is explained by the fact that in order to enter the page from another device each time you need to enter additional data:
- at the first stage, this is the username and password to log in;
- at the second stage, this is an authentication code received in an SMS message or through special applications such as Duo Mobile, Google Authenticator.
Every year the number of attempts to hack accounts on many social networks is growing. Fraudsters are developing increasingly sophisticated ways to gain access to your data. According toCNews Analytics, in 2014-2015 alone there were several successful hacker attacks:
| Year | What happened: |
| September 2014 | Hackers obtained data from about 5 million Gmail accounts. |
| September 2014 | Using phishing and virus infection, attackers stole more than 1 million Yandex user passwords. |
| September 2014 | Approximately 4.6 million Mail.ru passwords were hacked and collected into a database. |
| October 2014 | Fraudsters attacked about 200 thousand VKontakte users; all accounts contained Gmail, Mail.ru and Yandex email addresses. |
| May 2015 | 6.7 million user accounts of a popular website were hacked" Ask RU". |
| October 2015 | Hackers took over the data of 15 million T-mobile customers. |
The two-factor authentication feature is equally important for both ordinary users and for owners and public accounts with a large number of followers, when it is important to keep Instagram data safe from the hands of scammers. For regular users, this feature may be useful, but visiting the profile will take more time.
Instagram offers to get an authentication code using one of the following methods:
- via SMS message;
- using a specialized application.
Advantages of this method:
- Each time you visit, you will receive a randomly generated password on your phone. If they try to hack the page after finding out your login and password, attackers will not be able to predict the combination of numbers that you will receive;
- Login is not possible without a mobile device whose number is linked to the Instagram page.
The disadvantages of this method include the following:
- by constantly requesting codes from the same device, the likelihood that fraudsters will be able to hack your account increases;
- If there is no cellular signal, it becomes necessary to enter a backup code, which may be lost.
To set up this method you need:



The advantages of this method are that:
- You can log into your account even if there is no mobile connection;
- You can generate passwords for multiple devices in one application.
Of the minuses it is worth saying that:
- if the server is hacked and the primary key is obtained, scammers will be able to generate a password and access your page;
- If the application creates security codes on the same gadget from which you access Instagram (for example, a tablet or smartphone), two-factor functionality is reduced.
The method for setting up two-factor authentication using a mobile application is identical to the settings using SMS messages, but:



Now, when visiting your Instagram page, you must enter an identification code each time.
How to disable two-factor authentication and why it’s better not to do it
If necessary, you can turn off two-factor authentication settings. But, if the function does not work, your data may be at risk from attackers. To disable, go to the “Settings” menu, select “Two-factor authentication” and deactivate each of the sliders:

The relevance of additional protection of your personal data on the social network Instagram is growing exponentially. The two-factor verification option is an excellent opportunity to further protect your account from the hands of scammers. Every time you visit a social network from an unidentified gadget, you will need to prove that you are the owner of this page. This feature is robust enough to make it difficult for attackers to take over your account. In addition, if they try to hack the page, you will receive a confirmation code, this will make it clear that someone is trying to access the page.
Hello again everyone. Agree, the most important thing when working on the Internet is safety. She needs special attention. When registering on an important site, you should create a strong password or use. Because the more complex the combination of letters and numbers, the more difficult it will be for attackers to hack it. However, there are times when hackers manage to gain access to your account, for example, to your personal email. This is very sad: important information may end up in the wrong hands and can be used against you, correspondence with your partners may be completely deleted, etc. In a word, your account should be protected like the apple of your eye.
To increase security, many services offer two-factor authentication. Today we will look at what this is using the example of Yandex mail.
When you enable this feature, an attacker, even if he guesses your main password correctly, will not be able to get into your mailbox. Because to do this you will need to specify a random one-time password, which is generated by a special application on your smartphone or tablet. Now we will try to tell you in detail how to enable two-factor authentication in Yandex. In the future, there will be a similar review on Google Mail and Mail.ru.
So, to connect this function we need a smartphone or tablet. Go to your Yandex mailbox. If you don't have one yet, create one. How? Read in.
After we have logged into our account, click on your account and select “ Account management»
A Yandex passport will open with all sorts of settings. In the block " Access control"follow the link" Set up two-factor authentication»

Now we have to go through 4 steps.
1 step. Confirming your phone number.

After enabling the new feature, your account will be linked to your phone number. Therefore, indicate the number to which you have free access. After that, click on the button “ to get the code»
In a couple of seconds you will receive an SMS message containing the code that we enter in the field...

... and click " Confirm»
Step 2. Pin code.

In order for the application to generate a one-time password, you need to enter a PIN code, the one that we will now indicate. Attention!!! Remember this code and do not share it with anyone. Even if your phone is stolen, without knowing your PIN code, attackers will not be able to use this application.
Enter your PIN code, then repeat. To open symbols, click on the eye. This way you can make sure you typed everything correctly. And click " Create».
Step 3. Yandex Key mobile application.

At this stage, we need to install the very application that will create one-time passwords. Click on the button “ Get a link to your phone».

Let's move along it. An Android phone will automatically open the Google Play service with an offer to install the Yandex Key application. Let's install it.

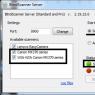
Open Yandex Key. After a few introductory pages, you will be asked to scan a QR code. The app will ask for permission to access your camera. We agree. Next, we point the camera at the monitor screen so that the square with the QR code falls into the camera lens. The application will automatically scan and add your account. If scanning fails, you can maintain a secret key. To view it, click on the link " Show secret key"under the QR code. In the application, also select the method for entering the secret key.
Now let's move on to the next step.
Step 4. Entering a one-time password from the Yandex key.

We launch our application on our gadget. Now you will need to enter your PIN code. And after that you will see that same random one-time password.

The password is updated every 30 seconds. Therefore, have time to enter it in the field before updating and click the “ Turn on».
That's it, we have enabled two-factor authentication for our Yandex account.

Let's check how it works. Log out of your current account.

Now you can log into your account in 2 ways. 1) enter your login (or Yandex email address) and then enter NOT the password we used before, permanent, but the ONE we receive in the Yandex mobile application key after entering the PIN code. And click the Login button. Second way means logging in using QR code. Click on the QR code icon (to the right of the Login button).
Then we get to this page

We follow the instructions: launch Yandex Key, enter our PIN code and then select “ Login using QR code»

Then we point the camera of the tablet or phone at the QR code. The application scans the code and we get access to our mail.
How to disable two-factor authentication in Yandex
If for some reason you decide to disable two-factor authentication, then this can be done quickly and easily. Log in to your mailbox, go to Account Management (see where and how to do this at the beginning of this article) and turn off this function.

In the next step we need to enter a one-time password from the Yandex Key application

Enter it and confirm.

Create a new password (this time permanent), repeat it and save it.

That's it, now our two-factor authentication is disabled. The permanent password created in the previous step will be used to log in.
So, today we looked at how to make our Yandex mail account more secure by connecting two-factor authentication to it. Are you using this feature? Share in the comments.
And that's all for today. See you again!
Every person should have a dream. A dream is what drives a person. When you are little, you dream of growing up. A dream must first become a goal. Then you must achieve your goal. And you should have a new dream!
The additional user verification feature completely controls all attempts to log into your account and use of applications: find out how to properly use and how to disable two-factor authentication in your Apple ID on your Apple device.
One of the main advantages of Apple is approach to security and privacy policy user information.
Two-step authentication is one of the modern techniques for achieving the maximum level of security in logging into your account.
The company uses this technology to verify the owner of the gadget when trying to log into an account. Multi-level authentication is a 100% guarantee that only its owner will have access to the system.
Operating principle. Difference in operation of authentication and verification
The activated multi-level authentication function perfectly protects your account from hacking and unauthorized entry by other users.
Only the owner of the ID will be able to log in, because the system will require you to enter two types of data:
- Apple ID password;
- Digital code, which will be sent to all trusted devices - it is proof of legal authorization.
Example: You decide to log in from any browser or client program. For this action you need to enter your username and password. After authorization, you will not be able to log into your account - you must additionally enter a code that confirms authorized entry.
The required code is displayed on all gadgets linked to an Apple ID. Enter the numbers into the iCloud authentication window to access your profile.
A visual diagram of how the function works is shown in the figure:
After the first correct entry of the code, entering numbers will no longer be requested after the next software startup. Re-authentication only required in a few cases:
- When resetting;
- When you re-enter.
Also, the constant introduction of digital codes is mandatory for functions that have an increased degree of security - changing smartphone settings, deleting system parameters, and others.
Verification and authentication. What is the difference?
It is important to distinguish between concepts two-step verification And two-factor authentication , since they have a similar effect, but different meaning.
Examination was implemented and introduced into Apple gadgets back in 2015. The main purpose of the option is additional control. The check is available starting with iOS 9 firmware.
Authentication - This is an advanced version of the check. Apple has improved the function and introduced new security management systems into it. In particular, working with location. The principle of working with cards is to mark “safety” points.
Each person regularly visits the same places, so on the map you can definitely select several points from which you can easily log in.
If the login is made outside these points, a verification code and a warning about possible actions of an attacker are immediately sent to trusted devices.
As you can see, authentication is indeed a more automated and reliable method of identity control.
The purpose of the verification is to send a code to a trusted gadget, and authentication also analyzes the location of the device and warns the owner of possible danger.
Feature Requirements
Multi-level authentication is designed for the following gadgets:
Disable authentication
Disabling authentication will prevent you from entering additional access codes. You won't have to confirm your location either. Follow the instructions:
- Using a desktop browser go to the cloud storage page iCloud.com;
- Log in to the system- Enter login and password;
- Further type the access code into the text field that appears, which is shown on other gadgets;
- Press the key "Allow" in the window that appears on the mobile device;
- Next, the browser will automatically redirect you to the user page. If you are not included in the trusted list, on your mobile gadget click on "I trust this browser" and click on "Continue";
- After successful login, click on the tile "Settings". It is located on the main page of the desktop version of iCloud. Another option for entering settings is to select your username in the upper right corner. Next, in the drop-down list, click on "iCloud Settings";
- In the window that appears, press the button "Control". It is located next to the account owner's name;
- Next, you will be redirected to the Apple website. In a new window you need to log in by entering your username and password from;
- Go to your account management window and click on the tab "Safety"-"Change";
- Find the field "Disable Authentication" and select it. Next, confirm the action by entering the password, which will be sent to the trusted device.
The two-step authentication system is designed in such a way that to protect users as much as possible from all possible hacking attempts. That is why, in order to completely disable the option, the developers have provided for the need to answer a block of questions that you specified.
Only after entering the correct answers into the text fields will you be able to deactivate the option.
Confirm disconnection:
Trusted devices
Verified device– this is any of your Apple devices. The only requirement is that all gadgets must be linked to one ID. It is on the basis of this binding that a group of trusted devices is created.
You will not be able to confirm authentication from a device that is not part of your Apple gadgets group.
Only one owner of a tablet or computer can work with two-step authentication.
List of trusted devices - this is a list of all gadget models to which a digital code will be sent to confirm entry into the Apple ID or program.
You can view this list in the application itself in the Devices tab.
Trusted numbers
Trusted numbers– this is a list of cellular operator numbers to which a digital access code will be sent for authentication. Messages can come not only in text form, but also in the form of a call from an Apple robot.
When you first set up multi-level authentication, you must specify at least one real phone number.
To add a number, you need to enter it in the field and confirm. As confirmation, enter the code sent to the number in the window that appears.
A SIM card with an associated number must be installed in a trusted device. Otherwise, verification codes will not be received.
What data do you need to remember?
It is important to remember that two-step authentication is a whole set of actions that are aimed at protecting your data.
For full operation of the function You will need to remember or write down the following information:
- Account login and password;
- Custom codes for programs– digital access identifiers that you have independently set in your account;
- Primary key is a set of letters and numbers that is automatically generated after enabling the option. You will need it if you lose access to all trusted numbers and devices.
Be sure to screenshot your master key and move it to a folder on your PC or other device. Also, the code can be written down on a flash drive or piece of paper.
Store this data in this way so that no one can find and use the universal key.
We also recommend that you update trusted numbers in a timely manner. If you change your SIM card, don't forget to enter the new number into your Apple ID. Otherwise, access to the identifier may be lost.
Monitor the physical security of your devices.
Do not leave your smartphone unattended near strangers and use the fingerprint scanner to restrict unlocking of the gadget.
It is important to protect yourself not only from virtual ID hacking, but also from unauthorized access of other people to your phone/tablet.
Enabling the feature
Activating the feature will only take a few minutes.
As a result, you will receive an additional security factor that will protect data in the device memory, installed programs and in cloud storage.
On iPhone and iPad
Follow the instructions to enable authentication on your iPhone:
1 Open your phone settings window;
2 Go to the iCloud field;
3 Click on the item "Password»;
4 Select “Set up 2-factor authentication”;
5 Enter the code that will be sent to your trusted devices and complete the setup. Write the universal key onto physical media.
On Mac OS
On Mac OS, two-step user authentication is only available in El Capitan and newer operating system firmware:
1 Go to the system settings window;
2 Click on the iCloud field and start the account data editing mode;
3 In a new window Click on "Safety". Next, the system will require you to enter the password for the identifier;
4 Click on the key "Set up authentication", which is located at the bottom of the window. Confirm the digital code that will appear on all devices linked to your Apple ID.
Alternative receipt of notifications
Receive access codes m Available not only on trusted devices, but also to the Find iPhone service.
You can set this option in the Apple ID settings (Security-Send access codes).
As a result, the verification code will be sent not only to trusted devices, but also to .
Thus, in one window you will be able to monitor login attempts from suspicious locations and view the access code.
This option only works with authentication. It is not possible to work with cards for verification purposes.
Benefits of Multi-Level Authentication
Any Apple ID stores not only information about linked devices, but also credit card data and personal information of users.
Many people store scans of documents and other important information in the cloud, theft of which can lead to irreversible consequences.
If you want to always be sure that your information is safe, use two-factor authentication. Feature benefits:
- A unified security organization for all Apple gadgets;
- Advanced function control settings;
- Guaranteed protection against all levels and types of hacking.
Disadvantages in the function
Despite all the obvious advantages regarding the security of gadgets, multi-level authentication complicates the life of users - remembering keys, The possibility of losing a number or a trusted device creates a number of problems:
- Along with multi-level authentication It is impossible to use third-party software. For example, iMobie AnyTrans or the popular PhoneRescue utility;
- Difficulty logging into iCloud– due to a flaw in the option, users often encounter system errors even after entering the correct access key to the cloud storage;
- Working with a cellular network. If you are in an area with poor coverage, authentication may not work;
- Linking to codes. The verification can only be carried out if you have a second gadget at hand, which is linked to the same Apple ID as the first device.
If you don’t currently have a second gadget near you, you can use a permanent key, which is stored in your account settings, but in practice, users very rarely write down or remember it.