Sniffer for Windows Intercepter-NG (instructions for use). Description of the ARP-spoofing attack
What is Intercepter-NG
Let's look at the essence of ARP using a simple example. Computer A (IP address 10.0.0.1) and Computer B (IP address 10.22.22.2) are connected by an Ethernet network. Computer A wants to send a data packet to computer B; it knows the IP address of computer B. However, the Ethernet network they are connected to does not work with IP addresses. Therefore, in order to transmit via Ethernet, computer A needs to know the address of computer B on the Ethernet network (MAC address in Ethernet terms). The ARP protocol is used for this task. Using this protocol, computer A sends a broadcast request addressed to all computers in the same broadcast domain. The essence of the request: “computer with IP address 10.22.22.2, provide your MAC address to the computer with MAC address (for example, a0:ea:d1:11:f1:01).” The Ethernet network delivers this request to all devices on the same Ethernet segment, including computer B. Computer B responds to computer A to the request and reports its MAC address (eg 00:ea:d1:11:f1:11) Now, Having received the MAC address of computer B, computer A can transmit any data to it via the Ethernet network.
To avoid the need to use the ARP protocol before each data sending, the received MAC addresses and their corresponding IP addresses are recorded in the table for some time. If you need to send data to the same IP, then there is no need to poll devices every time in search of the desired MAC.
As we just saw, ARP includes a request and a response. The MAC address from the response is written to the MAC/IP table. When a response is received, it is not checked in any way for authenticity. Moreover, it doesn't even check whether the request was made. Those. you can immediately send an ARP response to the target devices (even without a request), with spoofed data, and this data will end up in the MAC/IP table and will be used for data transfer. This is the essence of the ARP-spoofing attack, which is sometimes called ARP etching, ARP cache poisoning.
Description of the ARP-spoofing attack
Two computers (nodes) M and N on an Ethernet local network exchange messages. Attacker X, located on the same network, wants to intercept messages between these nodes. Before the ARP-spoofing attack is applied on the network interface of host M, the ARP table contains the IP and MAC address of host N. Also on the network interface of host N, the ARP table contains the IP and MAC address of host M.
During an ARP-spoofing attack, node X (the attacker) sends two ARP responses (without a request) - to node M and node N. The ARP response to node M contains the IP address of N and the MAC address of X. The ARP response to node N contains the IP address M and MAC address X.
Since computers M and N support spontaneous ARP, after receiving an ARP response, they change their ARP tables, and now the ARP table M contains the MAC address X bound to the IP address N, and the ARP table N contains the MAC address X, bound to the IP address M.
Thus, the ARP-spoofing attack is completed, and now all packets (frames) between M and N pass through X. For example, if M wants to send a packet to computer N, then M looks in its ARP table, finds an entry with the host’s IP address N, selects the MAC address from there (and there is already the MAC address of node X) and transmits the packet. The packet arrives at interface X, is analyzed by it, and then forwarded to node N.
HTTPNetworkSniffer is a packet sniffer tool that captures all HTTP requests/responses sent between the Web browser and the Web server and displays them in a simple table. For every HTTP request, the following information is displayed: Host Name, HTTP method (GET, POST, HEAD), URL Path, User Agent, Response Code, Response String, Content Type, Referer, Content Encoding, Transfer Encoding, Server Name, Content Length, Cookie String, and more...You can easily select one or more HTTP information lines, and then export them to text/html/xml/csv file or copy them to the clipboard and then paste them into Excel.
System Requirements
- This utility works on any version of Windows, starting from Windows 2000 and up to Windows 10, including 64-bit systems.
- One of the following capture drivers is required to use HTTPNetworkSniffer:
- WinPcap Capture Driver : WinPcap is an open source capture driver that allows you to capture network packets on any version of Windows. You can download and install the WinPcap driver from this Web page.
- Microsoft Network Monitor Driver version 2.x (Only for Windows 2000/XP/2003): Microsoft provides a free capture driver under Windows 2000/XP/2003 that can be used by HTTPNetworkSniffer, but this driver is not installed by default, and you have to manually install it, by using one of the following options:
- Option 1: Install it from the CD-ROM of Windows 2000/XP according to the instructions in Microsoft Web site
- Option 2 (XP Only): Download and install the Windows XP Service Pack 2 Support Tools. One of the tools in this package is netcap.exe. When you run this tool in the first time, the Network Monitor Driver will automatically be installed on your system.
- Microsoft Network Monitor Driver version 3.x: Microsoft provides a new version of Microsoft Network Monitor driver (3.x) that is also supported under Windows 7/Vista/2008.
The new version of Microsoft Network Monitor (3.x) is available to download from Microsoft Web site.
- You can also try to use HTTPNetworkSniffer without installing any driver, by using the "Raw Sockets" method. Unfortunately, Raw Sockets method has many problems:
- It doesn't work in all Windows systems, depending on Windows version, service pack, and the updates installed on your system.
- On Windows 7 with UAC turned on, "Raw Sockets" method only works when you run HTTPNetworkSniffer with "Run As Administrator".
Known Limitations
- HTTPNetworkSniffer cannot capture HTTP data of a secured Web site (HTTPS)
Versions History
- Version 1.63:
- Fixed bug from version 1.62: HTTPNetworkSniffer crashed when selecting network interface without connection information.
- Version 1.62:
- The information of the selected network adapter is now displayed in the window title.
- Version 1.61:
- Added /cfg command-line option, which instructs HTTPNetworkSniffer to use a config file in another location instead if the default config file, for example:
HTTPNetworkSniffer.exe /cfg "%AppData%\HTTPNetworkSniffer.cfg"
- Added /cfg command-line option, which instructs HTTPNetworkSniffer to use a config file in another location instead if the default config file, for example:
- Version 1.60:
- Added "Clear On Capture Start" option. You can turn it off if you don"t want to clear the previous items when you stop the capture and start again.
- Added "Quick Filter" feature (View -> Use Quick Filter or Ctrl+Q). When it"s turned on, you can type a string in the text-box added under the toolbar and HTTPNetworkSniffer will instantly filter the HTTP items, showing only lines that contain the string you typed.
- Version 1.57:
- Added "Save All Items" (Shift+Ctrl+S).
- Version 1.56:
- HTTPNetworkSniffer now automatically loads the new version of WinPCap driver from https://nmap.org/npcap/ if it"s installed on your system.
- Version 1.55:
- Added 2 HTTP request columns: "Accept" and "Range".
- Version 1.51:
- HTTPNetworkSniffer now tries to load the dll of Network Monitor Driver 3.x (NmApi.dll) according to the installation path specified in HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Netmon3. This change should solve the problem with loading the Network Monitor Driver 3.x on some systems.
- Version 1.50:
- Added 4 columns to the adapters list in the "Capture Options" window: "Connection Name", "MAC Address", "Instance ID", "Interface Guid".
- When using WinPCap driver , HTTPNetworkSniffer now displays more accurate information in the adapters list of the "Capture Options" window.
- Version 1.47:
- Added "Auto Size Columns On Every Update" option.
- Version 1.46:
- Added option to export to JSON file.
- Version 1.45:
- Added "Always On Top" option.
- Added secondary sorting support: You can now get a secondary sorting, by holding down the shift key while clicking the column header. Be aware that you only have to hold down the shift key when clicking the second/third/fourth column. To sort the first column you should not hold down the Shift key.
- Version 1.41:
- HTTPNetworkSniffer now offers you to run it as administrator (Under Windows Vista/7/8 with UAC)
- Version 1.40:
- HTTPNetworkSniffer now allows you to automatically add it to the allowed programs list of Windows firewall when starting to capture and remove it when you stop capturing. This option is needed when using the "Raw Socket" capture method while Windows firewall is turned on, because if HTTPNetworkSniffer is not added to Windows firewall, the incoming traffic is not captured at all and thus HTTPNetworkSniffer doesn't work properly.
- Version 1.36:
- Added columns names ("IP Address" and "Adapter Name") to the adapters list on the "Capture Options" window.
- Version 1.35:
- Added integration with utility
- Version 1.32:
- Added "Show Time In GMT" option.
- Version 1.31:
- Fixed bug: The "Promiscuous Mode" check-box in the "Capture Options" window was not saved to the configuration file.
- Version 1.30:
- Added "Response Time" column, which calculates and displays the time (in milliseconds) passed between the moment that the client sent the HTTP request and the moment that the HTTP server response received by the client.
To get more accurate result on this column, it"s recommended to use the WinPcap driver or the Microsoft Network Monitor driver (version 3.4 or later) to capture the packets.
- Added "Response Time" column, which calculates and displays the time (in milliseconds) passed between the moment that the client sent the HTTP request and the moment that the HTTP server response received by the client.
- Version 1.27:
- Added "Scroll Down On New Line" option. If it"s turned on, HTTPNetworkSniffer automatically scrolls to the bottom when a new line is added.
- Version 1.26:
- Fixed the flickering problem on Windows 7.
- Version 1.25:
- Added "Load From Capture File" option. Allows you to load a capture file created by WinPcap/Wireshark (Requires the WinPcap driver) or a capture file created by Microsoft Network Monitor driver (Requires the Network Monitor driver 3.x) and displays the captured data in the format of HTTPNetworkSniffer.
- Added /load_file_pcap and /load_file_netmon command-line options.
- Version 1.22:
- Added "Mark Odd/Even Rows" option, under the View menu. When it"s turned on, the odd and even rows are displayed in different color, to make it easier to read a single line.
- Version 1.21:
- Added "Auto Size Columns+Headers" option, which allows you to automatically resize the columns according to the row values and column headers.
- Fixed issue: The properties dialog-box and other windows opened in the wrong monitor, on multi-monitors system.
- Version 1.20:
- Added URL column.
- Fixed bug: When opening the "Capture Options" dialog-box after Network Monitor Driver 3.x was previously selected, HTTPNetworkSniffer switched back to Raw Sockets mode.
- Version 1.15:
- Added new column: Last Modified Time.
- Version 1.10:
- Added 3 new columns: Location, Server Time, and Expiration Time.
- Version 1.06:
- Fixed the accelerator key of "Stop Capture" (F6)
- Version 1.05:
- Added "Copy URLs" option (Ctrl+U), which copies the URLs of the selected HTTP items into the clipboard
- Version 1.00 - First release.
Start Using HTTPNetworkSniffer
Except of a capture driver needed for capturing network packets, HTTPNetworkSniffer doesn"t require any installation process or additional dll files. In order to start using it, simply run the executable file - HTTPNetworkSniffer.exeAfter running HTTPNetworkSniffer in the first time, the "Capture Options" window appears on the screen, and you"re requested to choose the capture method and the desired network adapter. In the next time that you use HTTPNetworkSniffer, it"ll automatically start capturing packets with the capture method and the network adapter that you previously selected. You can always change the "Capture Options" again by pressing F9.
After choosing the capture method and network adapter, HTTPNetworkSniffer captures and displays every HTTP request/response sent between your Web browser and the remote Web server.
Command-Line Options
| /cfg | Start HTTPNetworkSniffer with the specified configuration file. For example: HTTPNetworkSniffer.exe /cfg "c:\config\hns.cfg" HTTPNetworkSniffer.exe /cfg "%AppData%\HTTPNetworkSniffer.cfg" |
| /load_file_pcap | Loads the specified capture file, created by WinPcap driver. |
| /load_file_netmon | Loads the specified capture file, created by Network Monitor driver 3.x. |
Integration with IPNetInfo utility
If you want to get more information about the server IP address displayed in HTTPNetworkSniffer utility, you can use the Integration with IPNetInfo utility in order to easily view the IP address information loaded directly from WHOIS servers:- and run the latest version of .
- Select the desired connections, and then choose "IPNetInfo - Server IP" from the File menu (or simply click Ctrl+I).
- IPNetInfo will retrieve the information about server IP addresses of the selected items.
Translating HTTPNetworkSniffer to other languages
In order to translate HTTPNetworkSniffer to other language, follow the instructions below:- Run HTTPNetworkSniffer with /savelangfile parameter:
HTTPNetworkSniffer.exe /savelangfile
A file named HTTPNetworkSniffer_lng.ini will be created in the folder of HTTPNetworkSniffer utility. - Open the created language file in Notepad or in any other text editor.
- Translate all string entries to the desired language. Optionally, you can also add your name and/or a link to your Web site. (TranslatorName and TranslatorURL values) If you add this information, it"ll be used in the "About" window.
- After you finish the translation, Run HTTPNetworkSniffer, and all translated strings will be loaded from the language file.
If you want to run HTTPNetworkSniffer without the translation, simply rename the language file, or move it to another folder.
License
This utility is released as freeware. You are allowed to freely distribute this utility via floppy disk, CD-ROM, Internet, or in any other way, as long as you don"t charge anything for this and you don"t sell it or distribute it as a part of commercial product. If you distribute this utility, you must include all files in the distribution package, without any modification !Disclaimer
The software is provided "AS IS" without any warranty, either expressed or implied, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose. The author will not be liable for any special, incidental, consequential or indirect damages due to loss of data or any other reason.Feedback
If you have any problem, suggestion, comment, or you found a bug in my utility, you can send a message to [email protected]| Download HTTPNetworkSniffer (32-bit version) |
| Download HTTPNetworkSniffer (x64 version) |
HTTPNetworkSniffer is also available in other languages. In order to change the language of HTTPNetworkSniffer, download the appropriate language zip file, extract the "httpnetworksniffer_lng.ini", and put it in the same folder that you Installed HTTPNetworkSniffer utility.
| Language | Translated By | Date | Version |
|---|---|---|---|
When an ordinary user hears the term “sniffer”, he immediately becomes interested in what it is and why it is needed.
We will try to explain everything in simple language.
However, this article will be intended not only for novice users, but also for.
Definition
Sniffer is a traffic analyzer. In turn, traffic is all information that passes through computer networks.
This analyzer looks at what information is being transmitted. To do this, it must be intercepted. In fact, this is an illegal thing, because in this way people often gain access to other people's data.
This can be compared to a train robbery - a classic plot of most Westerns.
You are transferring some information to another user. It is carried by a “train”, that is, a network channel.
The idiots from Bloody Joe's gang intercept the train and rob it completely. In our case, the information goes further, that is, attackers do not steal it in the literal sense of the word.
But let's say that this information is passwords, personal notes, photographs and the like.
Attackers can simply rewrite and photograph all this. This way they will have access to sensitive data that you would like to hide.
Yes, you will have all this information, it will come to you.
But you will know that complete strangers know the same thing. But in the 21st century, information is most valued!
In our case, this is exactly the principle used. Certain people stop traffic, read data from it and send it on.
True, in the case of sniffers, everything is not always so scary. They are used not only to gain unauthorized access to data, but also to analyze the traffic itself. This is an important part of the work of system administrators and simply administrators of various resources. It’s worth talking about the application in more detail. But before that, we will touch on how these same sniffers work.
Principle of operation
In practice, sniffers can be portable devices that are literally placed on a cable and read data and programs from it.
In some cases, it is simply a set of instructions, that is, codes that must be entered in a certain sequence and in a certain programming environment.
In more detail, traffic interception by such devices can be read in one of the following ways:
1 By installing hubs instead of switches. In principle, listening to a network interface can be done in other ways, but all of them are ineffective.
2 By connecting a literal sniffer to the place where the channel breaks. This is exactly what was discussed above - and a small device is installed that reads everything that moves along the channel.
3 Installation of a traffic branch. This fork is routed to some other device, possibly decrypted and sent to the user.
4 An attack whose goal is to completely redirect traffic to the sniffer. Of course, after the information reaches the reading device, it is again sent to the end user for whom it was originally intended. in its purest form!
5 By analyzing electromagnetic radiation, which arise due to traffic movement. This is the most complex and rarely used method.
Here is an approximate diagram of how the second method works.
True, it is shown here that the reader is simply connected to the cable.
In fact, doing it this way is almost impossible.
The fact is that the end user will still notice that there is a break in the channel at some point.

The very principle of operation of a regular sniffer is based on the fact that within one segment they are sent to all connected machines. Quite a stupid, but so far no alternative method! And between segments, data is transferred using switches. This is where the possibility of intercepting information using one of the above methods appears.
Actually, this is what is called cyber attacks and hacking!
By the way, if you install these same switches correctly, you can completely protect the segment from all kinds of cyber attacks.
There are other methods of protection, which we will talk about at the very end.
Helpful information:
Pay attention to the program. It is used to analyze network traffic and parse data packets, for which the pcap library is used. This significantly narrows the number of packages available for parsing, since only those packages that are supported by this library can be parsed.
Application
Of course, first of all, this concept has the application discussed above, that is, hacker attacks and illegal acquisition of user data.
But besides this, sniffers are also used in other areas, specifically in the work of system administrators.
In particular, such devices or programs help to perform the following tasks:

As you can see, the devices or programs we are considering can greatly facilitate the work of system administrators and other people who use networks. And that's all of us.
Now let's move on to the most interesting part - a review of sniffer programs.
We figured out above that they can be made in the form of physical devices, but in most cases special ones are used.
Let's study them.
Sniffer programs
Here is a list of the most popular such programs:
CommView. The program is paid, like everyone else on our list. One minimum license costs $300. But the software has rich functionality. The first thing worth noting is the ability to set rules yourself. For example, you can make sure that (these protocols) are completely ignored. It is also noteworthy that the program allows you to view details and a log of all sent packets. There is a regular version and a Wi-Fi version.

SpyNet. This is, in fact, the Trojan that we are all so tired of. But it can also be used for noble purposes, which we talked about above. The program intercepts and that are in the traffic. There are many unusual features. For example, you can recreate pages on the Internet that the “victim” visited. It is noteworthy that this software is free, but it is quite difficult to find.

BUTTSniffer. This is a pure sniffer that helps analyze network packets rather than intercept other people's passwords and browser history. At least that's what its author thought. In fact, his creation is used for you know what. This is a regular batch program that works via the command line. To get started, two files are downloaded and launched. “Captured” packets are saved on your hard drive, which is very convenient.
There are many other sniffer programs. For example, fsniff, WinDump, dsniff, NatasX, NetXRay, CooperSniffer, LanExplorer, Net Analyzer and many others are known. Choose any! But, in fairness, it is worth noting that the best is CommView.
So, we have looked at what sniffers are, how they work and what they are like.
Now let's move from the place of a hacker or system administrator to the place of an ordinary user.
We are well aware that our data can be stolen. What to do to prevent this from happening? here). It works extremely simply - it scans the network for all kinds of spies and reports if any are detected. This is the simplest and most understandable principle that allows you to protect yourself from cyber attacks.

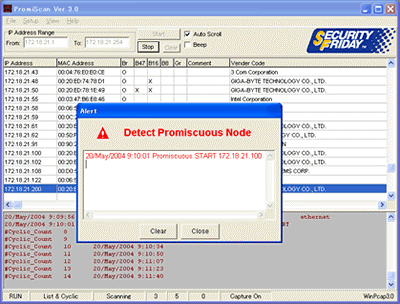
3 Use PromiScan. In its properties and tasks performed, this program is very similar to AntiSniff for Windows, so choose one. There are also many download links on the Internet (here is one of them). This is an innovative program that allows you to remotely control computers connected to the same network. The principle of its operation is to determine nodes that should not exist in the network. Actually, these are most likely sniffers. The program identifies them and signals this with an eloquent message. Very comfortably!.
4 Use cryptography and if deployed, a public key cryptographic system. This is a special encryption or electronic signature system. Its “trick” is that the key is public and everyone can see it, but it is impossible to change the data, since this must be done on all computers on the network at the same time. An excellent method - as bait for a thief. In you can read about blockchain, where exactly such a system is used.
5 Do not download suspicious programs, do not go to suspicious sites, and so on. Every modern user knows about this, and yet this is the main way for Trojans and other nasty things to get into your operating system. Therefore, be very responsible when using the Internet in principle!
If you have any more questions, ask them in the comments below.
We hope we were able to explain everything in simple and understandable language.
Many users do not realize that by filling out a login and password when registering or authorizing on a closed Internet resource and pressing ENTER, this data can easily be intercepted. Very often they are transmitted over the network in an unsecured form. Therefore, if the site you are trying to log into uses the HTTP protocol, then it is very easy to capture this traffic, analyze it using Wireshark, and then use special filters and programs to find and decrypt the password.
The best place to intercept passwords is the core of the network, where the traffic of all users goes to closed resources (for example, mail) or in front of the router to access the Internet, when registering on external resources. We set up a mirror and we are ready to feel like a hacker.
Step 1. Install and launch Wireshark to capture traffic

Sometimes, to do this, it is enough to select only the interface through which we plan to capture traffic and click the Start button. In our case, we are capturing over a wireless network.

Traffic capture has begun.
Step 2. Filtering captured POST traffic
We open the browser and try to log in to some resource using a username and password. Once the authorization process is complete and the site is opened, we stop capturing traffic in Wireshark. Next, open the protocol analyzer and see a large number of packets. This is where most IT professionals give up because they don't know what to do next. But we know and are interested in specific packages that contain POST data that is generated on our local machine when filling out a form on the screen and sent to a remote server when we click the “Login” or “Authorization” button in the browser.
We enter a special filter in the window to display captured packets: http.request.method == “POST"
And we see, instead of thousands of packages, only one with the data we are looking for.

Step 3. Find the user's login and password
Quickly right-click and select the item from the menu Follow TCP Steam

After this, text will appear in a new window that restores the contents of the page in code. Let's find the fields “password” and “user”, which correspond to the password and username. In some cases, both fields will be easily readable and not even encrypted, but if we are trying to capture traffic when accessing very well-known resources such as Mail.ru, Facebook, VKontakte, etc., then the password will be encrypted:
HTTP/1.1 302 Found
Server: Apache/2.2.15 (CentOS)
X-Powered-By: PHP/5.3.3
P3P: CP="NOI ADM DEV PSAi COM NAV OUR OTRo STP IND DEM"
Set-Cookie: password= ; expires=Thu, 07-Nov-2024 23:52:21 GMT; path=/
Location: loggedin.php
Content-Length: 0
Connection: close
Content-Type: text/html; charset=UTF-8
Thus, in our case:
Username: networkguru
Password:
Step 4. Determine the encoding type to decrypt the password
For example, go to the website http://www.onlinehashcrack.com/hash-identification.php#res and enter our password in the identification window. I was given a list of encoding protocols in order of priority:
Step 5. Decrypting the user password
At this stage we can use the hashcat utility:
~# hashcat -m 0 -a 0 /root/wireshark-hash.lf /root/rockyou.txt
At the output we received a decrypted password: simplepassword
Thus, with the help of Wireshark, we can not only solve problems in the operation of applications and services, but also try ourselves as a hacker, intercepting passwords that users enter in web forms. You can also find out passwords for user mailboxes using simple filters to display:
- The POP protocol and filter looks like this: pop.request.command == "USER" || pop.request.command == "PASS"
- The IMAP protocol and filter will be: imap.request contains "login"
- The protocol is SMTP and you will need to enter the following filter: smtp.req.command == "AUTH"
and more serious utilities for decrypting the encoding protocol.
Step 6: What if the traffic is encrypted and uses HTTPS?
There are several options to answer this question.
Option 1. Connect when the connection between the user and the server is broken and capture traffic at the moment the connection is established (SSL Handshake). When a connection is established, the session key can be intercepted.
Option 2: You can decrypt HTTPS traffic using the session key log file recorded by Firefox or Chrome. To do this, the browser must be configured to write these encryption keys to a log file (FireFox based example) and you should receive that log file. Essentially, you need to steal the session key file from another user's hard drive (which is illegal). Well, then capture the traffic and use the resulting key to decrypt it.
Clarification. We're talking about the web browser of a person whose password they're trying to steal. If we mean decrypting our own HTTPS traffic and want to practice, then this strategy will work. If you are trying to decrypt the HTTPS traffic of other users without access to their computers, this will not work - that is both encryption and privacy.
After receiving the keys according to option 1 or 2, you need to register them in WireShark:
- Go to the menu Edit - Preferences - Protocols - SSL.
- Set the flag “Reassemble SSL records spanning multiple TCP segments”.
- “RSA keys list” and click Edit.
- Enter data in all fields and write the path in the file with the key

WireShark can decrypt packets that are encrypted using the RSA algorithm. If the DHE/ECDHE, FS, ECC algorithms are used, the sniffer will not help us.
Option 3. Gain access to the web server that the user is using and obtain the key. But this is an even more difficult task. In corporate networks, for the purpose of debugging applications or content filtering, this option is implemented on a legal basis, but not for the purpose of intercepting user passwords.
BONUS
VIDEO: Wireshark Packet Sniffing Usernames, Passwords, and Web Pages
Any online tracking is based on the use of sniffer technologies (network packet analyzers). What is a sniffer?
A sniffer is a computer program or a piece of computer equipment that can intercept and analyze traffic passing through a digital network or part of it. The analyzer captures all streams (intercepts and logs Internet traffic) and, if necessary, decodes the data, sequentially storing the transmitted user information.
Nuances of using online tracking through sniffers.
On the broadcast channel of the user’s computer network LAN (Local Area Network), depending on the structure of the network (switch or hub), sniffers intercept traffic of either the entire or part of the network coming from one laptop or computer. However, using various methods (for example, ARP spoofing) it is possible to achieve Internet traffic and other computer systems connected to the network.
Sniffers are also often used to monitor computer networks. Performing constant, continuous monitoring, network packet analyzers identify slow, faulty systems and transmit (via email, phone or server) the resulting failure information to the administrator.
Using network taps, in some cases, is a more reliable way to monitor Internet traffic online than monitoring ports. At the same time, the probability of detecting faulty packets (flows) increases, which has a positive effect under high network load.
In addition, sniffers are good at monitoring wireless single- and multi-channel local networks (the so-called Wireless LAN) when using several adapters.
On LAN networks, a sniffer can effectively intercept both one-way traffic (transfer of a packet of information to a single address) and multicast traffic. In this case, the network adapter must have a promiscuous mode.
On wireless networks, even when the adapter is in “promiscuous” mode, data packets that are not redirected from the configured (main) system will be automatically ignored. To monitor these information packets, the adapter must be in a different mode - monitoring.
Sequence of intercepting information packets.
1. Intercepting headers or entire content.
Sniffers can intercept either the entire contents of data packets or just their headers. The second option allows you to reduce the overall requirements for storing information, as well as avoid legal problems associated with the unauthorized removal of users’ personal information. At the same time, the history of transmitted packet headers may have a sufficient amount of information to identify the necessary information or diagnose faults.

2. Decoding packets.
The intercepted information is decoded from a digital (unreadable form) into a type that is easy to perceive and read. The sniffer system allows protocol analyzer administrators to easily view information that has been sent or received by a user.
Analyzers differ in:
- data display capabilities(creating timing diagrams, reconstructing UDP, TCP data protocols, etc.);
- type of application(to detect errors, root causes, or to track users online).
Some sniffers can generate traffic and act as a source device. For example, they will be used as protocol testers. Such test sniffer systems allow you to generate the correct traffic necessary for functional testing. In addition, sniffers can purposefully introduce errors to test the capabilities of the device under test.
Hardware sniffers.

Traffic analyzers can also be of a hardware type, in the form of a probe or a disk array (the more common type). These devices record information packets or parts thereof onto a disk array. This allows you to recreate any information received or transmitted by the user to the Internet or promptly identify a malfunction in Internet traffic.
Methods of application.
Network packet analyzers are used for:
- analysis of existing problems in the network;
- detecting network intrusion attempts;
- determining traffic abuse by users (inside and outside the system);
- documenting regulatory requirements (possible login perimeter, traffic distribution endpoints);
- obtaining information about network intrusion possibilities;
- isolation of operating systems;
- monitoring the loading of global network channels;
- used to monitor network status (including user activity both within and outside the system);
- monitoring of moving data;
- WAN monitoring and endpoint security status;
- collecting network statistics;
- filtering suspicious content coming from network traffic;
- creating a primary data source for monitoring the status and management of the network;
- online tracking as a spy collecting confidential user information;
- debugging server and client communications;
- checking the effectiveness of internal controls (access control, firewalls, spam filters, etc.).
Sniffers are also used by law enforcement agencies to monitor the activities of suspected criminals. Please note that all ISPs and ISPs in the US and Europe comply with the CALEA.
Popular sniffers.
The most functional system analyzers for online tracking:

The NeoSpy spy program, whose main activity is monitoring online user actions, includes, in addition to the universal sniffer program code, keylogger (keylogger) codes and other hidden tracking systems.