Frequently asked questions about the "1C: Document Flow" configuration. The form configures scanning. The form appears from the personal settings form Image recognition 1c document flow
The document management system "Corporate Document Management" includes a mechanism for recognizing text from graphic files. The text recognition engine can be used to solve the following problems:
- Text extraction for organizing full-text search of document management system files
- Creating new text (as well as html) files based on graphic files
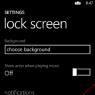
To enable the ability to recognize text in images, you must enable the “Use recognition” functional option in the system settings on the “Working with Files” tab (System Administration subsystem). After enabling this option, the following items will become available:
- Setting up an image recognition system
- Install the CuneiForm component
- Create a queue for image recognition
The system configuration form is shown in the figure below:
click to enlarge image
In the image recognition system setup form, you can specify which language is used in most files, and whether you want to change the author of the file after it is recognized.

In the future, the recognition language can be set for each specific user of the system, as well as for each file in the system. The following languages are supported:
English, German, French, Russian, Swedish, Spanish, Italian, Russian-English, Ukrainian, Serbian, Croatian, Polish, Danish, Portuguese, Dutch, Czech, Romanian, Hungarian, Bulgarian, Slovenian, Latvian, Lithuanian, Estonian, Turkish.
After setting up the recognition system, you can click on the “Install CuneiForm component” button to install the CuneiForm COM component version 12 (“CuneiForm.Puma”). In addition to installing the recognition components, you must also install the CuneiForm application itself. This application is freely distributed and can be downloaded from the official website cuneiform.ru. Direct download links can be obtained by clicking on the “help” link. After downloading the OCR CuneiForm V.12 distribution, run the setup.exe file and click the “Next” button.

After installing the application and COM components, the recognition system is ready for use. If by the time the recognition system is turned on in the “Corporate Document Flow” EDMS there are already graphic files that need to be recognized, then you can put them in a queue for recognition by clicking on the “Create a queue...” link. In the future, all graphic files moved to the EDMS will have an indication that recognition is required. You can change this attribute on the “Extracted Text” tab of the file form. The user can set the value to "Need to be recognized" or "Do not need to be recognized" for the selected file.

The recognition process in the EDMS “Corporate Document Flow” is launched through a special regulatory task “Files: Image Recognition”. The scheduled task is available in the “Automatic processing” subsystem as shown in the figure below.

If the “Corporate Document Flow” EDMS database is operating in the “1C” client-server mode, this routine task will be launched automatically (according to the configured schedule). If the document flow database operates in the normal 1C file mode, you will need to launch a separate session for processing routine tasks. You can open such a session by clicking on the “Open processing session” button as shown in the figure above. You can also run a routine image recognition task one-time by clicking on the “Run Now” button.
There are several options (strategies) performed after recognition of the graphic file of the actions of the EDMS system "Corporate Document Flow":
- Place in "Extracted Text" only. After recognition, the text will be placed in a special file text storage. This storage is used for full-text search of system file texts. The extracted text can be viewed (and, if necessary, changed) on the “Extracted Text” tab of the file form.
- Create a new html version of the file. After extracting the text from the graphic file, a new version of the file will be created in HTML format. This version will become the current version, and the original graphic file will remain in the previous version of this file.
- Create a new txt version of the file. In this option, after extracting text from a graphic file, a new version of the file will be created in TXT format. This version will become the current version, and the original graphic file will remain in the previous version of this file.
- Create a new html file. When choosing this option, a new file will be created in html format, and the owner of the file will be the same owner as the original file (for example, a certain corporate document).
- Create a new txt file. Selecting this option will create a new file in txt format, and the owner of the file will be the same owner as the original file. An example of this option for a system document is shown in the figure below.

If for any reason the document could not be recognized, the file will be assigned the status “Unable to Recognize”. Users can eliminate the cause (for example, install the CuneiForm distribution kit) and re-queue this file for recognition, changing the status to “Needs recognition.”
Note: To solve the problem of organizing full-text search in office application files, a mechanism is designed to extract texts from office files (MS Word, MS Excel, as well as OpenOffice files). Unlike image recognition, this mechanism extracts texts not from graphic files, but from office application files. The mechanism is launched by the routine task “Files: Extracting text (from office files)”.
"1C: Document Flow 8 KORP" provides maintenance of a hierarchy of business processes and tasks.
The hierarchy is maintained automatically when business processes are created based on the tasks of other business processes and can be taken into account manually by filling in the “Main task” attribute in the card of any business process.
The level of hierarchy of business processes and tasks is not limited by anything.
You can view the hierarchy either from the business process card or from the business process subject card - a document or file.
2. Is there a mechanism of substituents?
In "1C: Document Flow 8" versions PROF and CORP, role-based addressing of tasks is supported. This means that the task can be sent not to a specific employee, for example, I. S. Ivanov, but to a special role, for example, “Clerk”. With this addressing option, the task will be available for processing to all executors of the “Clerk” role. Role executors are indicated in a special list “Role Performers”, which is maintained by the person responsible for regulatory and reference information.
3. Is there support for document versions? What level of version nesting is supported?
"1C:Document Flow 8" supports working with versions of files and documents:
- When you place a modified file in "1C: Document Management 8", its new version is automatically created. At the same time, the program records the author of the version, the date and time of its creation, and a brief description of the changes made. It is possible to work with any version of the file. Version comparison is supported for popular office file formats. The number of stored versions is unlimited. If necessary, you can disable storing versions for some files.
- When document details change, information about this event is recorded in a special log, which allows you to compare several versions.
4. Is it possible to link discussions, chats, comments and votes to a document and its versions?
In the standard "Document Flow" configuration this feature is not provided. However, these features are easy to add during implementation. Thanks to the capabilities of 1C:Enterprise 8, this can be done even without removing the configuration from support.
5. When creating a business process, is it possible to select executors using the hierarchical organizational structure of the organization?
To select business process executors, the following can be used:
- organizational structure of the organization;
- performer roles.
When creating business process templates, in addition to the listed options, it is possible to use autosubstitutions.
6. Where can I see examples of implementation of "1C: Document Flow 8", including those with a large number of users and a large volume of documents?
This information can be obtained in the directory of implemented solutions. The directory provides a search for implementations based on various conditions, one of which is the minimum number of users. It is necessary to distinguish between the number of active users and the total number of users working with "1C: Document Flow 8". Sometimes these numbers can differ significantly. For example, 500 people may be connected to a document management system, but during normal operation the number of active users of the system may not exceed 200 people.
It is important to note that program performance depends not only on the number of actively working users, but also on the volume and intensity of the data processed. In this regard, the delivery package of "1C: Document Flow 8" version 1.1.3 includes processing that allows you to conduct load testing and obtain an accurate performance assessment for a specific customer, taking into account his tasks and equipment.
7. How to correctly calculate the amount of required hardware/software to operate the required number of users?
To select equipment, you can focus on the system requirements of "1C:Enterprise 8.2".
The delivery set of "1C:Document Flow 8" version 1.1.3 includes processing for setting up and conducting load testing of the program on the customer's equipment using the "Test Center" component from the "1C:KIP" program. Using the proposed methodology, you can configure various test characteristics (for example, the number of users, the frequency of typical operations, the size of files) and conduct testing. The result of the test is a highly accurate assessment of the speed of performing typical operations of "1C: Document Flow 8" with given characteristics.
8. How fully is archival records management implemented?
"1C: Document Flow 8" provides both operational and archival storage of documents and files. This allows you to search and analyze documents that are not only in operational work, but also those that have already been archived. It is possible to restrict access to archived documents and files. For official documents, accounting is provided according to the nomenclature of files, registration of transfer of files to the archive and destruction of files.
9. Where are the files stored: in the DBMS or in the file system?
"1C: Document Flow 8" provides both file storage options:
- Directly in the information base (in the DBMS).
- In disk volumes (in file system folders).
10. By what means is the reliability and integrity of the storage of documents and files ensured?
The integrity of the information base is ensured by the 1C:Enterprise 8.2 platform used by the DBMS and its backup tools.
Files are stored in volumes on disk in such a way as to simplify the creation of cumulative backup copies of volumes as much as possible. To do this, separate file folders are created in volumes for each day of work.
11. How is constant availability and high fault tolerance of document storage achieved?
Fault tolerance of file storage is achieved through the use of operating system tools, for example, by combining disks into a RAID array.
12. What mechanisms and tools are provided to support document storage backup and recovery?
Backup is performed using the DBMS used. When organizing file storage in volumes, in addition to this, you should ensure that all volumes are backed up.
The cumulative and full backup scheme is selected by the customer’s specialists independently, depending on the task at hand and the available equipment.
13. By what means is scalability achieved in terms of the volume of stored data and the number of users?
Scalability is ensured by the following mechanisms:
- Server cluster.
- Distributed information base.
- Storing files in volumes on disk.
14. Is full-text search implemented in the system?
Yes, the program implements full-text search with extensive functionality. The search is performed using all details of all program data and the contents of files in popular formats (rtf, txt, html, doc, xls, ppt, odt, etc.). The program can automatically recognize images, and therefore the search is carried out using the texts of scanned documents too.
Full-text search of documents and files is performed using the 1C:Enterprise 8 platform. To speed up the search, a full-text index is used. The construction and updating of this index is performed automatically by the 1C:Enterprise server.
15. Is it possible to save searches?
In "1C: Document Flow 8" edition 1.1.3, it is possible to save customized search conditions for documents and files by details. Users can give their saved search terms meaningful names.
16. Is streaming document input with automatic information extraction and filling in document attributes supported in the system?
"1C: Document Flow 8" allows for streaming images downloading from a scanner or from a directory on a hard or network drive. Attaching images to document cards is performed based on the recognition of barcodes previously applied to scanned documents. Scanned images are automatically recognized and indexed for full-text search.
Automatic filling of card attributes based on scanned images is not provided in the standard configuration, but can be implemented when the system is implemented by customer specialists or 1C partners.
17. How is control over the execution of documents and instructions organized?
There are two types of control over the execution of documents and decisions made:
- control of execution on the merits;
- control of execution on time.
Performance monitoring is essentially an assessment of how correctly and completely the assigned task has been completed. Such control is usually carried out by an employee competent enough to assess the compliance of the achieved result with the task set in the assignment.
Time-based execution control consists of tracking the deadlines of active orders. Usually carried out in a large organization by a division of a preschool educational institution, in a small organization - by a secretariat or secretary.
The 1C: Document Flow 8 system allows you to perform both types of control.
To exercise substantive control over execution in the “Order” and “Execution” business processes, in addition to the fields for specifying performers, the “Inspector” field is provided.
If it is filled in, then after the executors complete their task, the reviewer is automatically given the “Check execution” task. As part of this task, the inspector evaluates the completeness and correctness of the result of the execution of the order. If the result of execution does not correspond to the assigned task, the inspector has the opportunity to return the order back to the contractor for revision.
By default, the "Reviewer" field is filled in by the author of the business process.
To monitor execution by deadline in the “Order” and “Execution” business processes, in addition to the fields for specifying performers, the “Controller” field is provided.
If it is filled, then simultaneously with the tasks for the controller, the task “Monitor execution” is formed.
Thus, the controller sees among his tasks the execution of which orders he needs to control.
When the execution deadline expires, the controller's task also becomes overdue, which signals the controller that the deadlines have been violated and the need for appropriate action.
As soon as the performers complete their tasks, the controller's task also ends automatically.
The program "1C: Document Flow 8" also provides consolidated control of orders using reports. For example, the “Certificate of Performance Discipline” report allows you to obtain for each employee the number of tasks completed on time, not completed on time, not completed and overdue.
18. How is information security organized in 1C:Enterprise 8.2 when connecting remotely to the database via the Internet or using web services? What technologies are used?
When connecting via the Internet to the 1C:Enterprise database via a web server (web client or thin client), the secure https protocol is supported. Work with web services can also be organized through a secure connection.
19. Are there inexpensive programs for working with digital signatures that can be used within an enterprise, and not for organizing legally significant document flow?
Inside the enterprise, you can use any crypto provider, for example, Microsoft Enhanced Cryptographic Provider v1.0 - it is included with Windows and does not need to be purchased separately. Certificates can be obtained using a Windows Server 2003 or 2008 domain controller (using the certmgr.msc utility, running the All tasks - Request new certificate command).
To use digital signature with other organizations, you need a crypto provider that supports GOST R 34.10-2001, for example, Crypto Pro. In addition, you will need to enter into an agreement with a certification center to obtain certificates.
When using Microsoft Enhanced Cryptographic Provider v1.0, by default a certificate is issued that does not require a password at the time of signing. You can configure (when obtaining a certificate through a domain controller) to require a password when signing. Below are screenshots of the settings.



20. How does “1C: Document Flow 8” comply with the requirements of the Law “On Personal Data” (No. 152-FZ of July 27, 2006)?
In accordance with the requirements of the Federal Law of the Russian Federation No. 152-FZ of July 27, 2006 “On Personal Data”, “1C: Document Flow 8” implements a mechanism for auditing access to data containing personal information, for which the appropriate program settings must be enabled.
We also note that the 1C company produces the 1C:Enterprise 8.2z software package containing a special edition of the 1C:Enterprise 8.2 technology platform.
This software package received a certificate of conformity to FSTEC No. 2137 (valid until July 20, 2013), which confirms that the 1C:Enterprise 8.2z software package is recognized as a general-purpose software with built-in means of protecting information from unauthorized access to information that does not contain information constituting a state secret. Based on the certification results, compliance with the requirements of the governing documents was confirmed:
- for protection against NSD - class 5;
- according to the level of control of the absence of non-advanced substances - according to the 4th level of control;
- the possibility of use for creating AS up to class 1G inclusive, as well as for protecting information in personal data information systems up to class K1 inclusive, has been confirmed.
21. Our organization is already a user of solutions on the 1C:Enterprise 8 platform, and we have licenses for 1C:Enterprise 8. Can we use them for users to work with "1C: Document Flow 8"?
Yes, if your organization already has the required number of client licenses, then in order for users to work with the 1C: Document Flow 8 program, you should purchase only the basic package of “1C: Document Flow 8”.
If you are using the client-server version of the infobase and you already have a license for the 1C:Enterprise 8 application server, then by purchasing only the main package of 1C:Document Flow 8, you can deploy the 1C:Document Flow 8 infobase on this application server.
The need to purchase additional DBMS licenses is determined by the licensing terms of the DBMS you are using.
22. Is text recognized when entering a new document or file into the system by scanning a paper document?
Yes, when entering new documents into the system from a scanner, it is possible to recognize the contents of these documents.
More information about setting up recognition is written in the built-in help "1C: Document Flow 8" and in the documentation.
23. Are scanned documents included in full-text search?
Yes, if a scanned document is recognized, it will participate in the full-text search. If a document is not recognized and is loaded into “1C: Document Management 8” as an image, then a full-text search will be carried out only by the contents of the document’s metadata (by its details).
24. Is there a demo version of "1C: Document Flow 8" for independent review?
Yes, it is possible to get acquainted with the 1C: Document Management 8 program yourself using a fully functional demonstration information base available online.
In addition, in the section of the official 1C website dedicated to 1C: Document Flow 8 you can find additional materials on the product.
25. Is it possible to combine business processes into chains? For example, to carry out such a process: the supplier sent us a draft contract (incoming document) by email. Based on the results of the agreement, it was decided to create a protocol of disagreements and send it to the customer (outgoing document).
Yes, you can use the base input mechanism to do this.
26. What documentation is there for “1C: Document Flow 8”?
Traditionally, all solutions, and “1C: Document Management 8” is no exception, are supplied with a configuration description containing instructions for installation and getting started in the system, as well as a description of the configuration mechanisms.
Built-in help will help users navigate the purpose of certain objects directly at the place of use. Some supporting materials can be found on the website.
Additional articles on the Document Flow configuration, along with documentation on the 1C:Enterprise 8 technology platform in electronic form and articles on other 1C solutions, are published and updated monthly on the Information Technology Support CDs and on the ITS-online website (http: //www.its.1c.ru), which can be accessed by any ITS subscriber.
27. How to correctly set the image format when scanning?
To select the optimal ratio of size and quality of scanned images, it is recommended to use the following settings:
- Set the resolution to 200 dpi.
- To scan monochrome images, select TIF, monochrome, LZW or RLE compression.
- To scan images in color, select the JPG format and set the compression level to 75 (this is the optimal compression level, combining fairly good image quality and a high compression ratio). The level of compression affects the quality of recognition, so after setting compression, it is recommended to scan several test documents and make sure that recognition works at the appropriate level of quality.
28. Where can I find out the name and type of crypto provider (to indicate in the cryptography settings dialog)?
Some of the most common crypto providers are listed below (name, name and type of crypto provider to specify in the Cryptography Settings dialog):
- CryptoPro CSP: "Crypto-Pro GOST R 34.10-2001 Cryptographic Service Provider" (type 75), Signal-COM CSP: "Signal-COM CPGOST Cryptographic Provider" (type 75),
- ViPNet CSP: "Infotecs Cryptographic Service Provider" (type 2),
- Microsoft CSP: "Microsoft Enhanced Cryptographic Provider v1.0" (type 1).
If your crypto provider is not on this list, you need to contact the manufacturer of the crypto provider and obtain the necessary information.
29. How to organize the loading of paper documents into the program, for example, an archive of contracts for the past year?
- Manually create internal document cards by filling in the following fields: Correspondent, Amount, validity period, etc.
- Then, for each card, print a barcode on a sticker (a barcode is automatically assigned by the system to each card) and stick it on the first page of each agreement (consisting of one or more sheets of paper). Or print the barcode on a blank sheet of paper and place such a sheet at the beginning of the stack of sheets of each contract.
- After this, perform stream scanning, in which scans of paper documents are automatically attached to pre-set cards.
Below is an approximate estimate of the benefits from using streaming scanning:
Initial data:
- 30 seconds - scanning a page on a flatbed scanner (including the time to put the sheet in the scanner and pick it up from there).
- 5 seconds - stream scanning of the page (medium stream scanner).
- 120 seconds - register an Incoming or Internal document and print a barcode, then add a sheet with a barcode to the sheets of the incoming or internal document.
- 8 hours a day working time (without lunches, breaks, etc.) 8*60*60= 28800 sec.
- During a working day, one clerk will have time to register 240 document cards.
- Let each document consist on average of 2 pages (i.e. a total of 480 sheets of paper).
- If you scan them manually, it will take another 4 hours.
- With stream scanning, this will take 40 minutes of scanner operation, i.e. the winnings per day will be 3 hours 20 minutes.
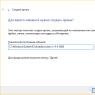
30. Is there an option to use digital signature on an enterprise server without installing cryptographic software on all client computers?
You can install cryptographic software only on the computers of those users who sign documents or files. In order for other users to be able to perform digital signature verification, it is necessary to configure digital signature verification on the server. To do this, you need to check the "Verify digital signature on the server" checkbox in the program settings, as shown in the figure.

Usage scenario:
- Some employees have the ability to apply digital signatures to documents and files. These employees have been issued digital signature certificates and have the appropriate cryptographic software installed.
- Other employees cannot apply digital signatures, but can check the established signatures. These employees do not need to install cryptographic software, but they do need to install it on each computer in the 1C:Enterprise server cluster. The procedure for licensing cryptographic software when installing it on a server should be clarified with the manufacturer of the corresponding software.
31. Files cannot be opened for viewing or editing in the web client. What could be the problem?
Check to see if you have a pop-up blocker in your browser. If a block is installed, disable it for the desired site.
32. Is it possible to transfer files from the database to volumes, and how to correctly specify the path in UNC format?
To transfer files from the infobase to volumes, follow these steps:
- Enable storage in volumes (Program settings - "Files" tab),
- Create one or more volumes:
- The path to the volume must be specified in UNC format, for example "\\server\folder",
- If the volume is located on the same computer on which the 1C:Enterprise server is running, then you need to configure shared access to the corresponding file system directory. For example, to use the directory "c:\volume1" as a volume:
- Configure shared access to the directory "c:\volume1" (Sharing tab in directory properties),
- Specify in the path to the volume the path to this directory "\\server\volume1" (it can be obtained by opening this computer through the network environment).
- Start the "Transfer to Volumes" processing from the "Administration Settings" section.
33. Is digital signature used when exchanging documents through MEDO?
When exchanging documents via MEDO, electronic digital signatures are not used. This is due to several reasons:
- GOST R 53898-2010, on the basis of which the functionality was developed, does not require the use of digital signatures. Instead, it is assumed that secure transmission transports will be used.
- The use of digital signatures by several exchange parties leads to the need to deploy a common certification center or use existing commercial certification centers. This is labor-intensive, difficult to set up and maintain, and when using commercial certification authorities, it also leads to additional financial costs.
- According to the law on electronic digital signatures, if the participants in the exchange of documents enter into an agreement that they recognize the fact of logging into the system as sufficient to identify the sender and recipient, then such an exchange of documents will be identical to the paper one.
34. When opening files, messages like “The file... was not found on the server. Should you delete it from the working directory?” How to get rid of these errors?
This message is issued if a file has been deleted in the infobase, but is still stored in the working directory on the user's personal computer.
When cleaning the working directory (for example, when opening a new file), the program checks all files stored in it and offers to delete those that are not found in the information database in order to free up space on the personal computer.
35. Are there any means in 1C:Document Flow for analyzing controversial situations when signing a document, for example, when an employee claims that he signed a completely different document card or did not sign this document at all.
- If an employee claims that he did not sign this document, then use the user logs and check the following:
- Open the document card.
- On the “EDS” tab, find the employee’s certificate (is there a certificate for this user among them).
- Follow the Work Protocols link (in the Navigation Panel) and find the "Signing of digital signature" event for this employee.
- If an employee claims that the document card was changed after he signed it:
- Open the document card.
- On the “EDS” tab, find the employee’s signature and check the EDS. If the signatures are correct, then the fields of the document card protected by the signature ("Name" and "Summary") are exactly those that were signed with the digital signature and were not changed after signing.
- Electronic digital signature verification can also be performed for files attached to the document and for approval visas.
36. What scanned file formats does 1C:Document Management support?
For single page images:
For multi-page images:
- pdf (with ImageMagick + Ghostscript installed).
Installing ImageMagick and Ghostscript is described in the Configuration Description book.
Scanning settings affect image size and the quality of barcode and text recognition.
Optimal scanning parameters (based on the ratio of recognition quality/file size):
- DPI: from 150 to 300.
- Color: color (i.e. not monochrome or grayscale image).
- Format: tif or png.
- 1. Corporate portals and document flow www.1c-kpd.ru+7 (495) 640-00-93 Stream scanning, barcoding and archiving in 1C: Document flow Master of 1C: Document flow Vladimir Lushnikov Corporate portals and document flow www.1c-kpd. ru+7 (495) 640-00-93
- 2. Corporate portals and document flow www.1c-kpd.ru+7 (495) 640-00-93 www.1c-kpd.ru+7 (495) 640-00-93 About the lecturer Vladimir Lushnikov Master of 1C: Document flow.
- Founder of 1C-KPD (1C-Corporate portals and document management).
- Teacher-methodologist for 1C: Document flow.
- Author and presenter of the courses “Possibilities of 1C: Document Flow”, “Implementation Technologies of 1C: Document Flow”, “Setup and Administration of 1C: Document Flow”.
- 6. Corporate portals and document flow www.1c-kpd.ru+7 (495) 640-00-93 www.1c-kpd.ru+7 (495) 640-00-93 Scanning and recognition work Scanning and recognition work is possible only under Windows.
- To set up image recognition on the server you need to: 1. Install the CuneiForm, ImageMagic and Ghostscript programs. 2. Set recognition parameters in the program settings and specify the path to the ImageMagic program.
- 8. Corporate portals and document flow www.1c-kpd.ru+7 (495) 640-00-93 www.1c-kpd.ru+7 (495) 640-00-93 Image recognition Texts can be extracted not only from text files , but also from graphic files and pdf formats with a graphic layer.
- The installation of the CuneiForm program in the file-server version should be done on the user’s computer under the user who will subsequently work with it, and in the client-server version on the 1C server - under the user under whom the 1C:Enterprise service is running.
- 10. Corporate portals and document flow www.1c-kpd.ru+7 (495) 640-00-93 www.1c-kpd.ru+7 (495) 640-00-93 Bar code Bar code (bar code) - graphic information , applied to the surface, marking or packaging of products, making it readable by technical means - a sequence of black and white stripes or other geometric shapes.
- 11. Corporate portals and document flow www.1c-kpd.ru+7 (495) 640-00-93 www.1c-kpd.ru+7 (495) 640-00-93 Logical structure of the barcode EAN-13 code from the point of view Product encodings can be divided into 5 zones: – Prefix of the national organization GS1 (3 digits); – Registration number of the product manufacturer (4-6 digits); – Product code (3-5 digits); – Check number (1 digit); – Additional field (optional barcode field, sometimes there is a “>” sign, “free zone indicator”).
- Codes starting with the number “2” (prefixes 200 to 299) are reserved separately. These are codes for internal use by businesses for their own purposes. Any enterprise in any region of the world, as well as individuals, can use them in any way they wish, at their own discretion, but exclusively for their internal purposes. Use of these codes outside of the company is prohibited.
- 12. Corporate portals and document flow www.1c-kpd.ru+7 (495) 640-00-93 www.1c-kpd.ru+7 (495) 640-00-93 Barcode symbol dimensions Nominal barcode dimensions: – Symbol width – 37.29 mm; – Symbol height – 25.93 mm;
- 14. Corporate portals and document flow www.1c-kpd.ru+7 (495) 640-00-93 www.1c-kpd.ru+7 (495) 640-00-93 Barcoding components When inserting a native barcode into, for example, doc format file, a specially prepared picture is inserted. The image is generated by the built-in component of the BarcodePrint Component (works in 32- and 64-bit Windows and Linux).
- To search for documents using a barcode received from a special scanner, the built-in Barcode Scanner Driver component is used (works in 32-bit and 64-bit Windows and Linux).
- To recognize barcodes, the Barcode Recognition Component component is used.
- 15. Corporate portals and document flow www.1c-kpd.ru+7 (495) 640-00-93 www.1c-kpd.ru+7 (495) 640-00-93 Uniqueness and unification of barcodes When assigning barcodes, it is necessary to ensure uniqueness internal barcodes in the information base. When using a distributed database, the uniqueness of barcode numbers allows you to provide a node prefix in the barcode, which is specified in each infobase.
- 18. Corporate portals and document flow www.1c-kpd.ru+7 (495) 640-00-93 www.1c-kpd.ru+7 (495) 640-00-93 Stream scanning Stream scanning consists of the following stages: 1 Receiving images from a scanner (or from a catalog) by scanning a stack of sheets directly into the program (to a network catalog); 2. Automatic recognition of barcodes and linking of recognized scans to document cards; 3. Checking the results and manually processing scans whose barcodes could not be determined (those images that the program could not recognize will need to be linked manually by the operator).
- 19. Corporate portals and document flow www.1c-kpd.ru+7 (495) 640-00-93 www.1c-kpd.ru+7 (495) 640-00-93 What is needed for streaming scanning? For streaming scanning to work, we need: Documents with barcodes or documents separated by blank sheets with barcodes;
- A scanner with automatic feed or a directory where scanned files are already located;
- Operator's workstation 1C: Document Flow, where GhostScript, ImageMagic and scanning and barcode recognition components are installed (built into 1C: Document Flow or ABBYY Recognition Server).
- 22. Corporate portals and document flow www.1c-kpd.ru+7 (495) 640-00-93 www.1c-kpd.ru+7 (495) 640-00-93 Archives
- 23. Corporate portals and document flow www.1c-kpd.ru+7 (495) 640-00-93 www.1c-kpd.ru+7 (495) 640-00-93 Nomenclature of cases Nomenclature of cases is a systematic list of names of cases entered into the organization’s records management, indicating their storage periods, in the prescribed form.
- After approval of the list of affairs of the organization, structural divisions receive extracts of its corresponding sections for use in their work.
- 25. Corporate portals and document flow www.1c-kpd.ru+7 (495) 640-00-93 www.1c-kpd.ru+7 (495) 640-00-93 Filling out the list of cases Deadlines and article numbers should be taken from document “List of standard management archival documents generated in the process of activities of state bodies, local governments and organizations, indicating storage periods.” Appendix to the order of the Ministry of Culture of the Russian Federation dated August 25, 2010 No. 558. The mark of the EPK (expert verification commission) is affixed to the paper cover of the case and means that some of the documents in this case cannot be destroyed without a preliminary examination.
- When printing a list of cases, if selection by division is enabled, then the head of the division will be substituted for the head of the organization.
- You can automatically fill out sections on the structure of the enterprise and copy the list of affairs for the next year.
- 28. Corporate portals and document flow www.1c-kpd.ru+7 (495) 640-00-93 www.1c-kpd.ru+7 (495) 640-00-93 Storage locations for paper documents Storage locations are indicated by premises and territories. But if room diagrams are not used, then the storage location directory will be linear.
- The person responsible for the master data has the rights to edit premises and territories.
- Clerks have rights to edit storage locations, and everyone else has rights to read.
- 29. Corporate portals and document flow www.1c-kpd.ru+7 (495) 640-00-93 www.1c-kpd.ru+7 (495) 640-00-93 Transfer log You can create a transfer log entry based on it immediately for multiple documents in the list. You can transfer the document either to an employee or to a contact person of the counterparty.
![[email protected]](/uploads/e51db64b6a5f2c0460e47b19d3ce3483.jpg)